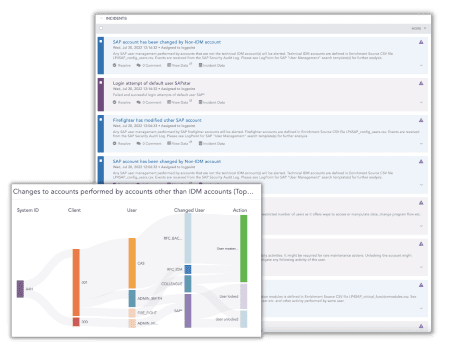
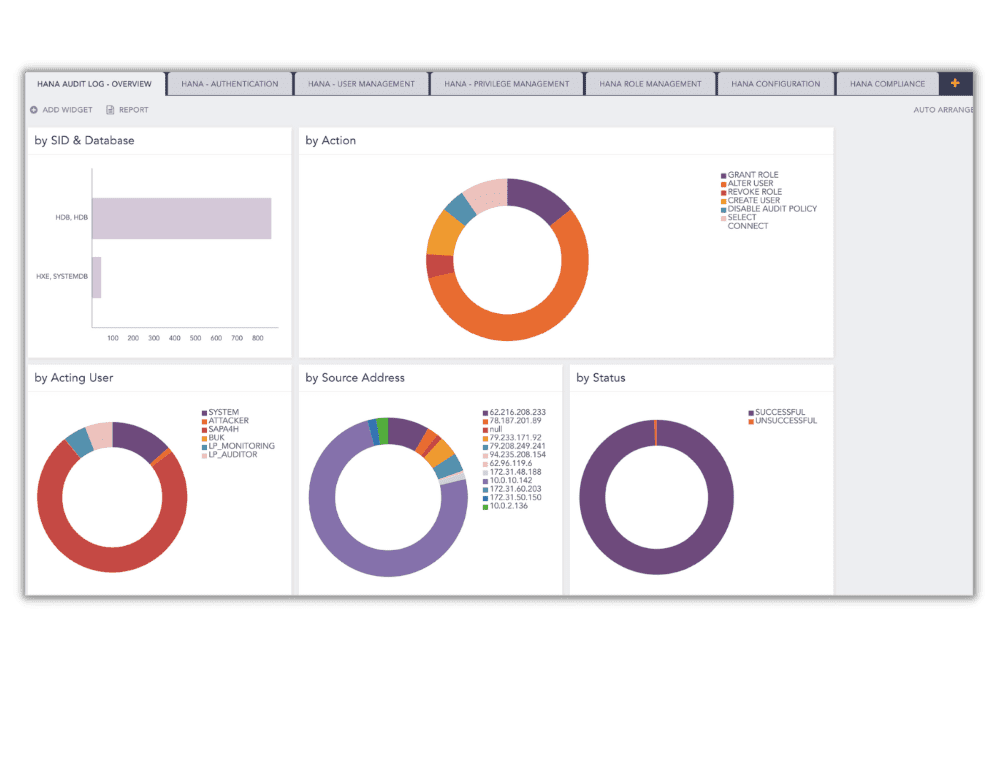
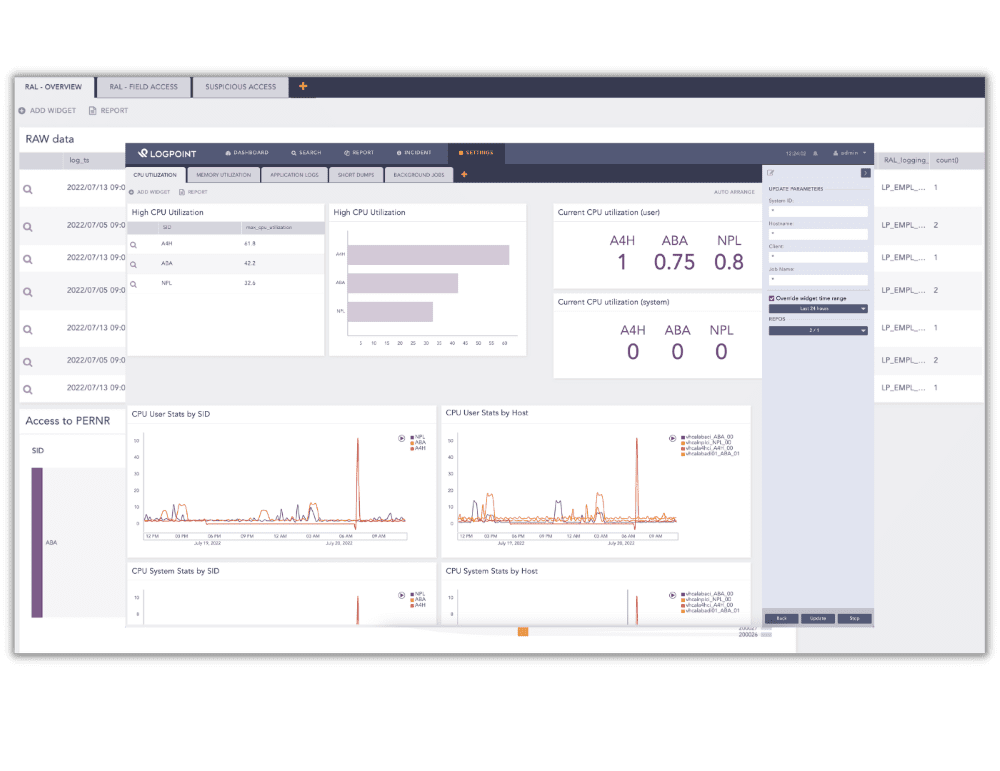
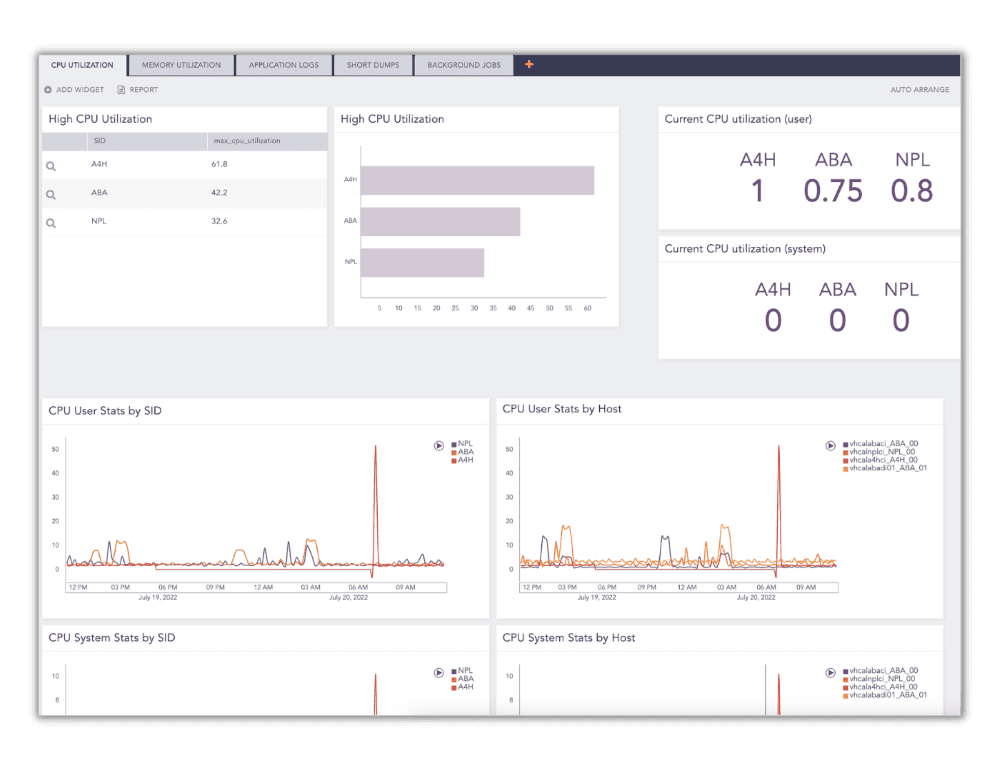
Mehr als 1.000 Organisationen in über 70 Ländern nutzen Logpoint SIEM
Replace your existing cybersecurity solution
with Logpoint
with Logpoint
Up and
running fast
Our onboarding and implementation process makes cybersecurity available to you in a matter of days.
Continuous
improvements
Stay agile with updates to solution capabilities, detection, and response. Keeping you future-proofed against emerging threats.
Compliant
and secure
Logpoint is compliant with the strictest data privacy regulations, including GDPR, CCPA and SCHREMS-2.
Onapsis vs. Logpoint
Compare directly, like for like!
Why our customers choose Logpoint
G2 peer-to-peer reviews

Gartner Peer Insights 2021