Ensuring the security and reliability of an organization’s IT infrastructure is paramount. SAP systems, which are at the heart of many companies, have come under scrutiny recently due to the discovery of critical vulnerabilities that could severely compromise system integrity and security. These vulnerabilities not only pose significant risks to data integrity and privacy but also threaten the overall stability and availability of business-critical systems.
The recent patches released by SAP underscore the urgency of the situation. The vulnerabilities in the SAP Web Dispatcher and SAP Message Server are particularly concerning, given their central roles in many SAP architectures. Immediate action is required to address these threats and ensure the continuous, secure operation of SAP systems.

Go To Section
What’s new in the update?
In July and August, SAP published two critical patches relating to the security of the SAP systems:
- CVE-2023-35871: SAP Web Dispatcher Memory Corruption
- CVE-2023-37491: Authorization Check Vulnerability in SAP Message Server
The SAP Web Dispatcher is a critical component in many architectures. It contains critical vulnerabilities that can lead to memory corruption and cause information disclosure and even system crashes. This can greatly impact the system availability and put the reputation and integrity of an entire company at risk.
The message server is a central communication component in the SAP network as it facilitates communication between the application and the server. To ensure safety, it is crucial that it is protected against unwanted and external access. The vulnerability in the authorization check of the SAP Message Server can potentially allow malicious users to gain access to the network, granting them the ability to read/write data and even rendering the system unavailable.
SAP Recommendation
To remediate these vulnerabilities, SAP has released the following recommendations:
Option 1: Install Kernel Patch Implementing a Kernel Patch is generally a complex task for companies. It involves extensive testing and quality assurance procedures
Option 2 (Workaround): Adjust SAP Profile Parameters Here are the specific SAP profile parameter settings:
- Set icm/HTTP/support_http2 to FALSE
- Set system/secure_communication to OFF
Since these vulnerabilities affect the HTTP/2 implementation of the ICM, applications that do not have HTTP/2 enabled are considered not vulnerable to CVE-2023-35871.
Because of this, a workaround solution to mitigate these vulnerabilities is to simply disable the support for HTTP/2 in the affected applications. This may have a performance impact but should remain functionally equivalent to HTTP/2.
To disable the support for HTTP/2, the profile parameter icm/HTTP/support_http2 should be set to FALSE. The location of this configuration will depend on the affected product (i.e., for the ICM in the SAP NetWeaver ABAP, it should be configured in the DEFAULT profile).
What else can you do to secure your SAP systems?
Ensuring the security of your SAP system involves both proactive measures, like adjusting profile parameters, and reactive measures, such as implementing kernel patches. Choosing the most suitable approach depends on your organization's resources, requirements, and risk assessment.
If the system/secure_communication parameter is ON, then the ACL (Access Control Lists)are bypassed during the communication between Message Servers. If this parameter is set to OFF, then the ACLs must be maintained accordingly and the authorization problems during accessing Message Servers will not take place.
Monitoring of the Profile Parameters by Logpoint
The above-mentioned vulnerabilities can in the meantime be monitored with Logpoint BCS for SAP. We have a specific solution for monitoring the SAP Profile Parameters, which consists of a set of configuration parameters that define how the SAP system should operate and control aspects of the system’s functionality, such as memory usage, database access, network connectivity, and other settings.
BCS for SAP automatically monitors the profile parameters' settings, transmits the log entries directly to SIEM, and incorporates the configuration settings from SAP ABAP.
Extended/Enterprise SAP Connectors by Logpoint can be configured to bring to SIEM not only log entries but also configuration settings of SAP ABAP systems. As an illustration, a sample Extended Profile Parameter configuration policy for icm/HTTP/support_http2 is provided
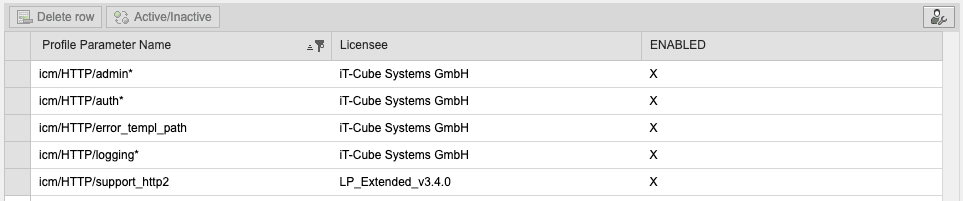
In SIEM you can easily find related events using elementary filter (SI_SIGID=”icm/HTTP/support_http2” or SI_SIGID=”system/secure_communication”):
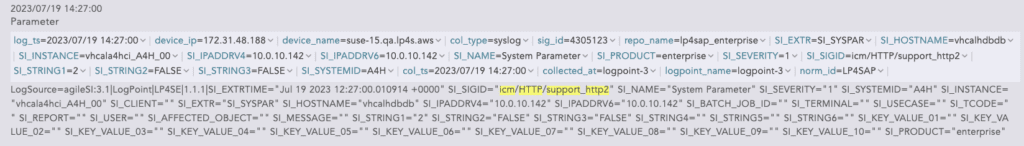
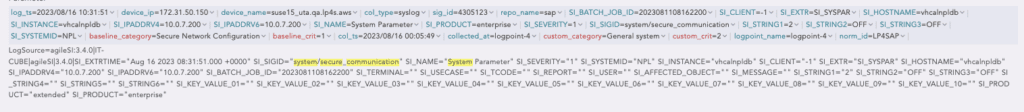
Event Example in Logpoint SIEM
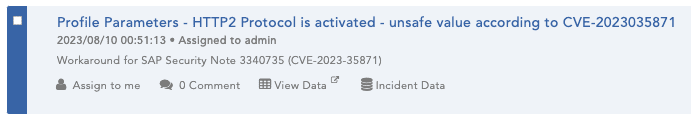
On the SIEM side of things, a special Alert Rule was created by our SAP experts to exclude unsafe profile parameter values. It’s triggered each time whenever profile parameter icm/HTTP/support_http2 set to TRUE (unsafe value according to note 3340735).
Below you can see an example of a triggered alert in Logpoint SIEM:
Logpoint Convereged SIEM
Logpoint Converged SIEM offers pre-configured, out-of-the-box dashboards, delivering you a complete overview of deviations or violations detected within profile parameters. This intuitive approach empowers you with insights into potential issues and anomalies, enabling swift and informed decision-making regarding the security and performance of your SAP system.
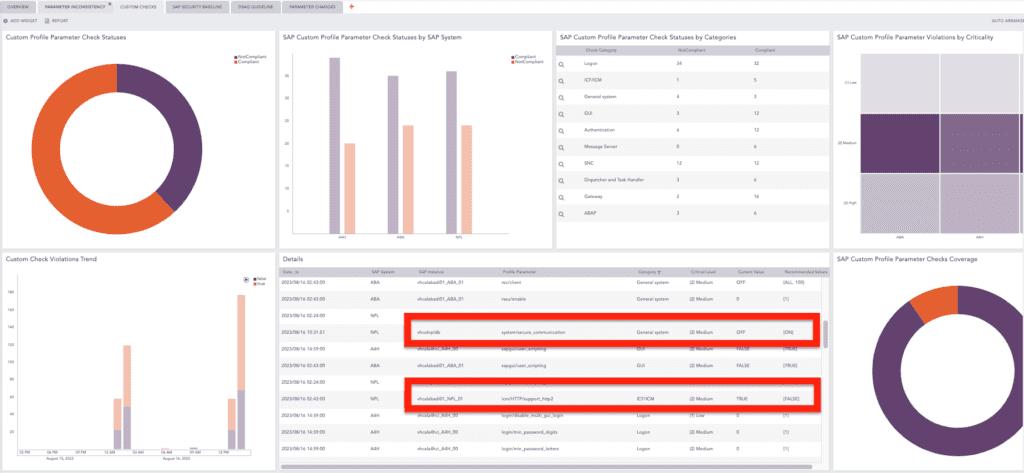
Profile Parameter Custom Checks Dashboard
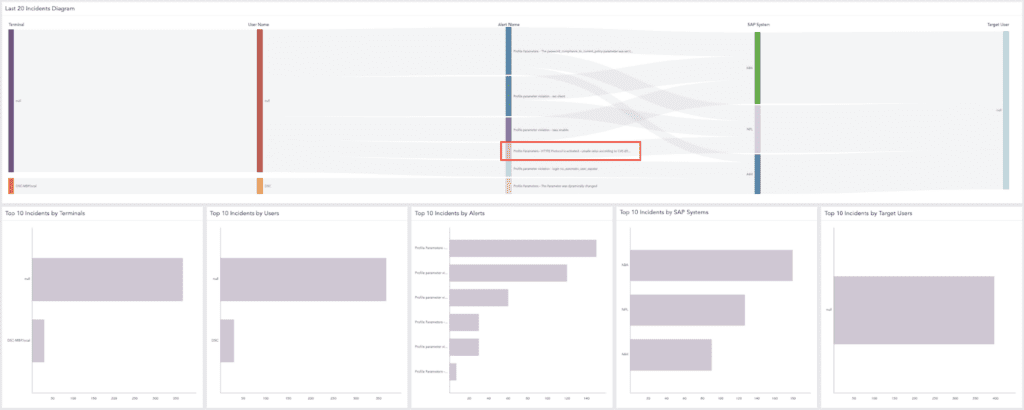
SAP Incident Dashboard






