Executive Summary
- Multiple vulnerabilities in MOVEit Transfer tracked as CVE-2023-34362, CVE-2023-35036, and CVE-2023-35708 were found.
- Mentioned vulnerabilities are SQL injections allowing unauthorized access to the MOVEit Transfer database, affecting all MOVEit Transfer Web versions.
- During the initial analysis, the first attempt of exploitation was detected as early as May 27th, 2023 but the first trace of exploitation goes back to July 2021.
- 2500+ public-facing MOVEit servers are detected via Shodan as of June 13th, 2023.
- After exploiting vulnerability data exfiltration attempts are performed.
Go To Section
Background
Progress issued an advisory on May 31st about a vulnerability in MOVEit Transfer that, if exploited, allows unauthorized access to the system aiding the escalation of privileges. MOVEit, a Managed File Transfer (MFT) application developed by Progress (previously Ipswitch), offers flexible deployment options and ensures secure data transfer. The vulnerability, known as SQL injection (CVE-2023-34362), resides in the MOVEit Transfer web application and permits unauthenticated attackers to gain unauthorized entry into the MOVEit Transfer database. Progress has stated that the exploitation of this vulnerability commenced in May 2023. The Clop ransomware group has informed BleepingComputer that they are responsible for the data breaches involving MOVEit Transfer that have occurred in the wild, as of June 6th.
Development Until Now
According to Microsoft, they have observed the exploitation of the MOVEit Transfer vulnerabilities from May 27, 2023. Additionally, the exploitation campaign has been attributed to Lace Tempest (DEV-0950) who is responsible for running Clop ransomware extortion site. Upon successful exploitation of the vulnerability, a custom web shell that has data exfiltration capabilities gets deployed on the server. In some cases, Lace Tempest has immediately performed data exfiltration after successfully exploiting the vulnerability.
Mandiant has discovered that the web shell dropped after exploitation of the vulnerability is the LEMURLOOT web shell which masquerades as a legitimate component of MOVEit as it is named “human2.aspx” and “_human2.aspx”. LEMURLOOT can enumerate files and folders, retrieve configuration information, and has a hard-coded username to delete if it exists and to create a new user. The web shell also utilizes an authentication method as the “human2.aspx” or the dropped web shell page loads, and a request header named X-siLock-Comment will be checked against a hard-coded password.
Huntress has provided a POC where they were able to chain the underlying SQLi to gain arbitrary code execution with a local administrator privilege. Additionally, they demonstrated how adversaries, upon exploiting this vulnerability, can perform malicious actions such as data exfiltration or ransomware deployment. They were able to identify another SQLi in the MOVEit Transfer that has been assigned a new CVE CVE-2023-35036 as of June 12.
Kroll's initial analysis of its impacted customer revealed that the exploitation attempts of the MOVEit Transfer vulnerability were first detected on May 27, 2023. According to them, the activities detected in May appeared to be an automated exploitation that resulted in the deployment of the LEMURLOOT. After studying the IIS logs of the affected clients, Kroll discovered evidence of similar activity in several client environments, dating back as far as July 2021 and continuing through April and May 2022. Those activities indicate that actors were testing access to organizations and pulling back information to identify its victim organization as they were trying to retrieve Organization ID, a unique identifier among MOVEit Transfer users on May 22, 2023. Such activity was performed around July 2021, and April 27, 2022. According to them, the adversaries were manually testing out commands during earlier exploitation attempts.
Affected Versions
The following MOVEit versions are affected by the vulnerabilities:
|
Affected Version |
|
MOVEit Transfer 2023.0.0 (15.0) |
|
MOVEit Transfer 2022.1.x (14.1) |
|
MOVEit Transfer 2022.0.x (14.0) |
|
MOVEit Transfer 2021.1.x (13.1) |
|
MOVEit Transfer 2021.0.x (13.0) |
|
MOVEit Transfer 2020.1.x (12.1) |
|
MOVEit Transfer 2020.0.x (12.0) or older |
|
MOVEit Cloud |
Visit this page, to get information on available patch versions.
Detection of MOVEit Exploitation & Post-Exploitation with Logpoint
When it comes to patching your organization’s security infrastructure, it is important to devote ample time to the task. This makes it crucial to actively search for indicators of attack and detect any traces of exploitation attempts or intrusion.
Logpoint Converged SIEM, along with the provided queries, can serve as a valuable tool in your arsenal for the task of detecting vulnerability exploitations.
Required Log Sources
-
Windows
-
Process Creation with Command Line Auditing should be enabled
-
-
Windows Sysmon
-
Windows Event Logging for MOVEit should be enabled
-
Firewall
-
IDS/IPS
Detecting IOCs
The IOCs list provided by Progress has been utilized to create queries for detecting the exploitation of CVE-2023-34362 and hunting for post-exploitation activities.
A web shell is dropped into the MOVEit subdirectory, masquerading as MOVEit’s file.
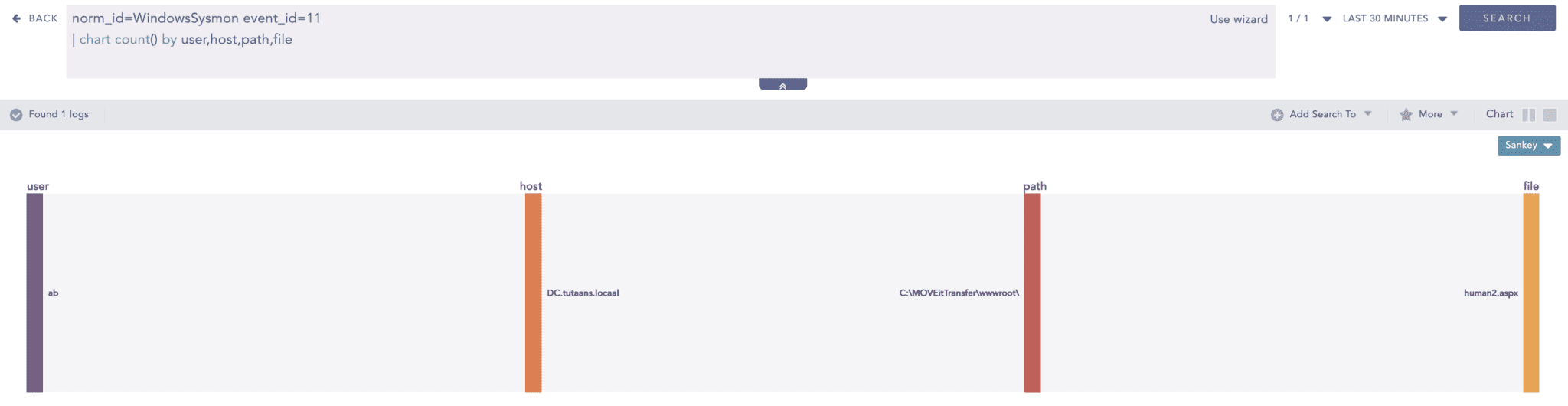
Besides the human2 file, adversaries can utilize any file name so, it is crucial to look for file creation events in the MOVEitTransfer folder. The query can show many events which must be filtered out to reduce false positives for detecting web shells.
Note!: Use of “.aspx.lnk” file name was detected.
As Mandiant and Huntress observed HTTP requests to the following files, the below query can be utilized to detect suspicious web requests before the execution of the web shell.
According to Kostastsale, in the victim hosts csc.exe is executed via the w3wp.exe process to compile malicious DLL files.
As observed by Huntress, the newly compiled DLL is dropped under C:\Windows\Microsoft.net\Framework64\v4.0.30319\Temporary ASP.NET Files\root\9a11d1d0\5debd404 folder which can be detected using the following query:
Note: While installing the application an App_Web_*.dll file is created so, watch out for the creation of a file in the provided format.
Florian Roth and Nasreddine Bencherchali have written a Sigma rule to detect events where files with suspicious extensions are created under the Moveit web root folder.
After reviewing the Web Shell file provided by Huntress, the payload contains code to delete an existing user “Health Check Service”.

After deleting the existing user, they created another user with the same name.

Besides the addition and deletion of the specific user, it is very crucial to look for any user add and delete events.
Crowdstrike observed in the IIS logs that during data exfiltration, the "referer" field contains IP addresses instead of domain names.
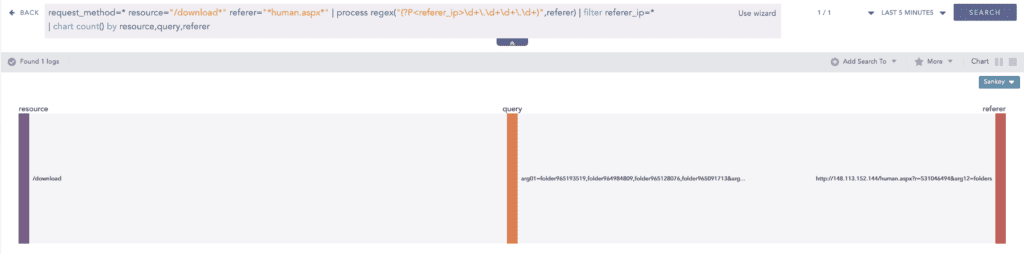
Searching for known user-agent of adversaries.
To detect the hash provided by Progress.
Searching for communication events with the domain mentioned by Progress in the IOC list.
In the IOC list creation of .cmdline was mentioned, to detect such events below query can be utilized:
As mentioned by Kroll, threat actors attempted to retrieve the organization ID, which can be detected using the below query:
According to Kroll, adversaries access the victim environment around 2021 and 2022 using some specific IP address, below query can be utilized to search for communication to those IP addresses.
Incident response with Logpoint SOAR and AgentX
Logpoint Converged SIEM recently got even better with the addition of EDR capabilities via AgentX! This native endpoint agent allows for the detection, investigation, and response to security incidents in the endpoints and enables faster threat detection through Logpoint SOAR. As AgentX comes with built-in telemetry enrichment of SIEM+SOAR events and adds further context through MITRE TTPs, it provides SOC teams with actionable threat and operational information, reducing the time to respond to an incident.
AgentX comes with more than 20 out-of-the-box playbooks that help reduce alert fatigue and improve the meantime response - Logpoint AgentX is available now: Contact your representative.
The playbook "Malicious File Investigation and Containment" enables the querying of files in threat intelligence platforms to verify their legitimacy and offer an automated response.
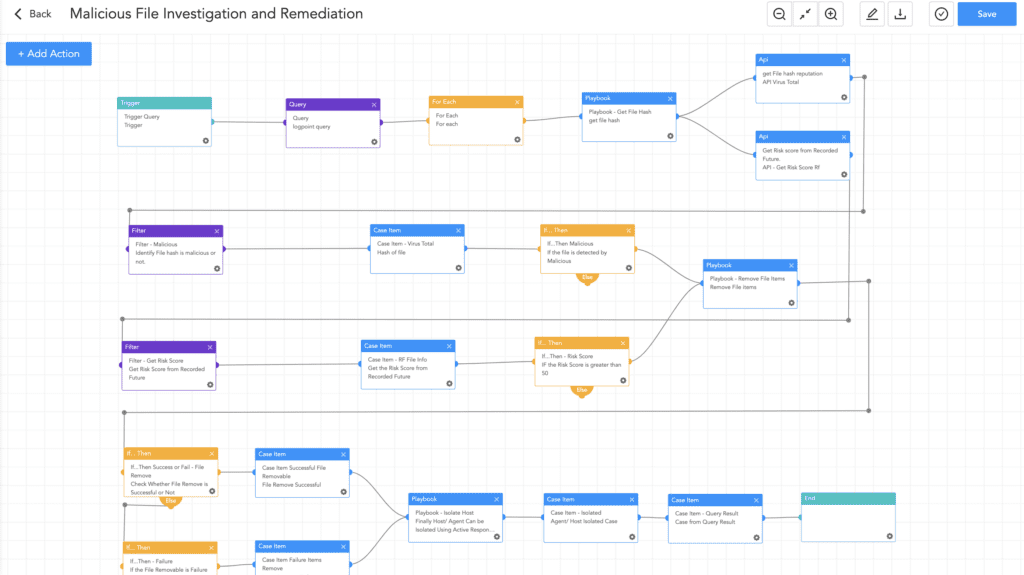
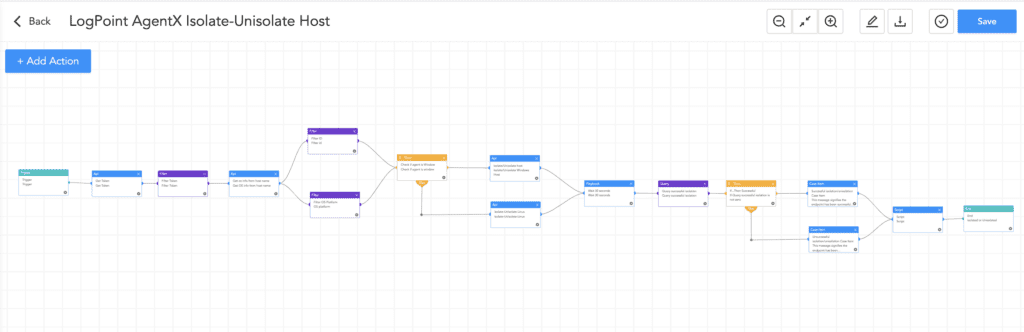
After detecting any IOC administrator can utilize the “Logpoint AgentX Isolate-Unisolate Host” playbook to isolate the host to prevent ransomware infection or lateral movement.
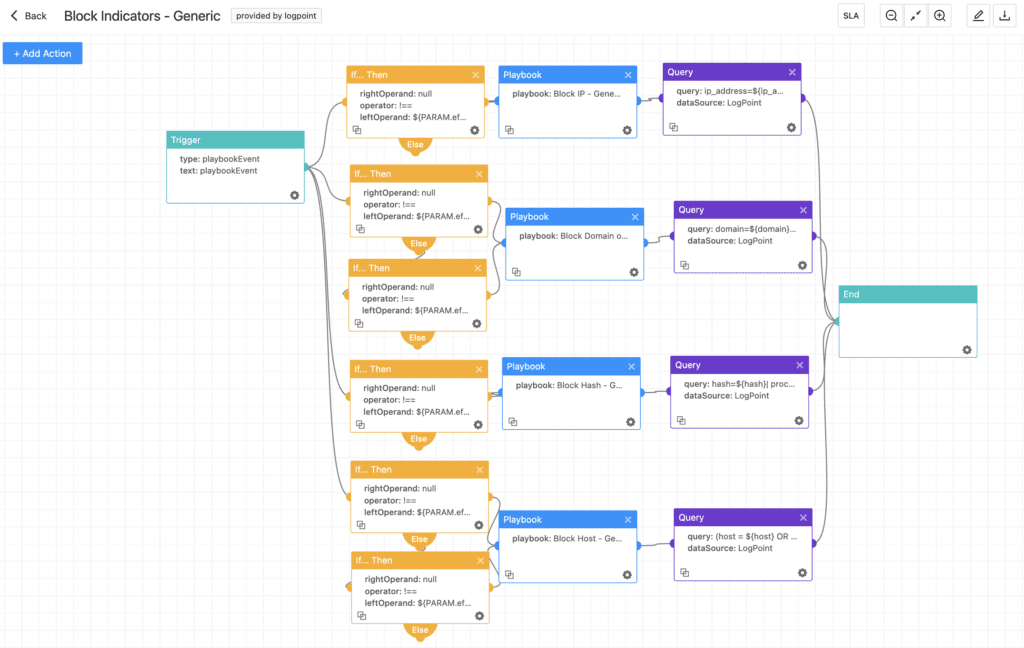
The Block Indicators - Generic playbook can be utilized to block malicious IP addresses, domains, files, and hosts. Block IP and other sub-playbooks work on a fixed number of products.
Conclusion
Adversaries are always looking for opportunities to exploit vulnerable and unpatched systems. By exploiting vulnerabilities such as CVE-2023-34362, adversaries can gain access to a system, conduct data exfiltration, and deploy ransomware that compromises the security of organizations and infringes upon the privacy of the organization and its customers. Therefore, it is highly recommended to promptly update the system as soon as a patch becomes available. In cases where patches are unavailable or not feasible, it is advisable to implement any mitigation or preventive measures provided by the affected product vendor and other security vendors. By taking these steps, organizations can enhance their defense against potential threats.






