Executive Summary
Starting in 2022, Logpoint Security Research Team has set out on a mission. We examined millions of logs and attack patterns prevalent in our customers to identify the tactics, techniques, and procedures (TTPs) used by adversaries in these malicious attacks by compiling a curated list of the most prevalent attacks that took place in the previous year. Using the MITRE ATT&CK® framework, the Logpoint Security Research team categorized each discovered TTP (v12). The current study identified the top 10 most frequent attack tactics by mapping known TTPs recorded in the previous year to ATT&CK.
The research depicted Command and Scripting Interpreter as the most common technique, whereas Execution and Defense Evasion dominated the detected tactics in 2022. By showing the most common attack techniques, threat actors deploying them, and red and blue team exercises for them, the research’s findings give insights for better-prioritizing risks and security operations.

Key Findings
-
The most common technique was T1059 Command and Scripting Interpreter which allows for the execution of various commands that directly or indirectly lead to almost every tactic in the list. A whopping 38.12% of incidents we detected were making use of the Command and Scripting technique.
-
Windows command lines and scripting tools, such as PowerShell, cmd.exe, and VBScript, were frequently used by attackers to perform complex actions and bypass security controls, and as sub-techniques for the T1059, made up the high percentage/
-
As the third most common technique, adversaries used Proxy T1090 to disguise their identity and evade detection by security controls that may be monitoring for known malicious IP addresses or domains. We did see a gradual decrease in the technique over the end of the year, however, even with the decline it still managed to reach third.
MITRE ATT&CK Framework
The MITRE ATT&CK® framework is a structured methodology for characterizing and describing cyber threats, based on observed attacker behavior during various stages of an attack. It organizes attacker behavior into tactics, such as initial access, persistence, and exfiltration, and then further breaks down these tactics into specific techniques that attackers use to accomplish their objectives. The framework is a valuable resource for cybersecurity professionals, providing a common language and structure for communicating about attacks, as well as a guide for developing and testing detection and mitigation strategies. It is continuously updated and expanded to stay current with emerging threats and new techniques used by attackers. The MITRE ATT&CK® framework is widely recognized as a leading methodology for threat intelligence, providing a systematic approach to understanding and defending against advanced persistent threats.
Methodology
Firstly, Logpoint collected alert fire rates from managed customers which were then used to generate an anonymized report. This provided a base for real-world data used to create this report.
To develop attack scenarios, we performed adversarial simulations and malware detonations in our labs and sandboxes to observe activities. References from external/online sources like blogs, forums, and sandboxes helped understand threat actors' techniques. Internal tools and open-source/paid sandboxes were used to analyze attacks, with some of the data sources collected from forums, sandboxes, blogs, white papers, and threat intelligence services.
Following the observation of the adversary's attack chain and collection of intrusion data, we then proceeded to develop relevant analytics and created a playbook for investigation and automated response. Analysts created actionable prevention signatures and detection rules by analyzing the effects of these malicious behaviors on security controls and endpoints. Each malicious activity was mapped to a technique of the MITRE ATT&CK framework, providing a common taxonomy for the building blocks of attack scenarios.
Throughout 2022, with multiple iterations, Logpoint analyzed hundreds of unique cases. Attack cases were extracted from them and then sorted based on the frequency at which they were observed. We published most of the data with our End-of-the-Year Report. However, the purpose of this report in particular is to understand the top ten techniques used by ransomware gangs most frequently to be better prepared against them and enforce additional security where required.
These data correspond to enterprise-level threats and are different from specific attacks like ransomware or cyber espionage. The data is supposed to be a representation of what users of Logpoint might face and we have tried our best to remain unbiased to provide a strictly educational report based purely on the data. However, we understand there may be some unconscious biases in our hypothesis or the data collection that might be reflected in some portions.
Logpoint Top 10 Critical MITRE ATT&CK Techniques 
In the Act
T1059 Command and Scripting Interpreter | Tactic: Execution | 38.12%
The most common technique in the Top 10 list this year is Command and Scripting Interpreter (T1059). It falls under the execution tactic, which means that adversaries use it to execute commands and scripts on a victim's machine. It is often used to gain a foothold on a system or escalate privileges. Adversaries have been found using legitimate interpreters like PowerShell or cmd.exe to evade detection and carry out their malicious activities.
Out of all the triggered alerts, we noted that sub-techniques such as Powershell (20%), Windows Command Shell (12%), Visual Basic (4.12%), and Python (2%) were the techniques mostly covered.
As for Powershell and Windows Command Shell below are some of the procedures that triggered the related alerts respectively.
T1003 OS Credential Dumping | Tactic: Credential Access | 34.52%
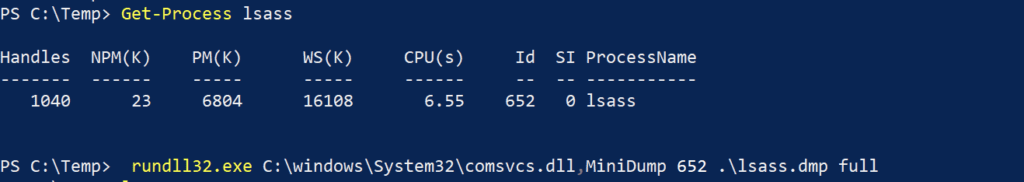
OS Credential Dumping(T1003) technique covers methodology utilized by adversaries to retrieve credentials from a system. It is the second most common technique on the list. This technique falls under the Credential Access tactic. This tactic covers all the techniques that can be utilized to retrieve credentials. Credential dumping is performed to gain access to users with higher privilege, access resources or perform lateral movement OS Credential Dumping technique includes methodology utilized by adversaries to retrieve credentials from a system. Here is a procedure on how adversaries have performed the OS Credential Dumping technique by utilizing rundll32.exe a LOLBins with comsvcs.dll to dump the LSASS.
Also, to dump ntds.dit file which contains sensitive data of Active Directory, adversaries have utilized Windows Server utility ntdsutil. Adversaries have utilized the acronym of "activate instance ntds" to evade detection based on command line execution.
In Linux to dump credential files adversaries have utilized the Linux utility unshadow to leave the encrypted credentials and later use various password-cracking tools to retrieve credentials.
T1090 Proxy | Tactic: Command and Control | 28.78%
Another common technique in the Top 10 list this year is Proxy (T1090) which falls under the Command and Control tactic. This tactic cover all the techniques utilized by adversaries to establish communication between the victim system and their C2 server. The Proxy technique can be used to mask the original C2 server address or bypass network restrictions by first sending traffic to a proxy server and then forwarding the connection to the intended server. Also, adversaries have utilized multiple proxy servers to redirect traffic to and from the victim systems and C2 server. Below is the procedure on how adversaries have utilized ngrok utility to expose a local port of a system inside the organization network to the internet.
T1055 Process Injection | Tactics: Defense Evasion, Privilege Escalation | 25.1%
The process Injection (T1055) technique involves replacing the code of a running process with code from another program. The technique falls under multiple tactics such as Defense Evasion, and Privilege Escalation as it allows adversaries to evade defense as the malicious payload is running under an existing process. It can also be utilized to gain privilege escalation by injecting code into a process having a higher integrity level. Among its sub-techniques, alerts related to Dynamic-link Library Injection (18%), Process Hollowing (5%), and Portable Executable Injection (2.1%) were triggered the most. Most of the triggered alerts were due to the detection of remote thread creation and process access events.
For DLL injection, windows internal binary Mavinject was utilized to inject a DLL into a process.
T1036 Masquerading | Tactic: Defense Evasion | 22.92%
Fifth in the Top 10 list this year is Masquerading (T1036) technique which falls under the Defense Evasion tactic. Adversaries use this technique to evade defenses by masquerading as an existing system process, binary, and services. Adversaries have been found utilizing this technique to drop payload masquerading as legitimate windows binaries such as Skype.exe and Svchost.exe. Most of the binary masquerading as legitimate processes were executed from the folder mentioned below but are not limited to it as directories such as Temp and other publicly writable folders were also utilized.
T1078 Valid Accounts | Tactics: Defense Evasion, Persistence, Privilege Escalation, Initial Access | 18.92%
The valid Accounts (T1078) technique indicates the use of existing system accounts or network users' credentials to access a system or resources. Like Process Injection, this technique also falls under multiple tactics such as Defense Evasion, Persistence, Privilege Escalation, and Initial Access. By utilizing compromised credentials, adversaries have gained access to the victim network, evade defense as it is a valid user, and escalate privilege by utilizing compromised admin credentials. Some of the triggered alerts were related to user login from suspicious locations. Other incidents were related to the activation of the guest account, setting a password for the account, and adding it to the local group. Below are some commands utilized to perform mentioned actions:
T1190 Exploit Public-Facing Application | Tactic: Initial Access | 15.44%
The Exploit Public-Facing Application (T1190) technique falls under the Initial Access tactic as it allows adversaries to gain access to a network. Adversaries can exploit vulnerabilities in an organization’s internet-facing services such as web servers, SSH, or SQL services. Threat actors have utilized this technique to exploit various unpatched vulnerabilities and zero days at the time such as Log4j, ProxyShell, and ProxyNotShell to gain access to a network.
T1112 Modify Registry | Tactic: Defense Evasion | 13.21%
Modify Registry (T1112) ranked quite low considering how rampant the ransomware was in the last year. This technique falls under the Defense Evasion tactic, as the technique allows adversaries to evade defenses by the modifying system and software components. Adversaries have been found modifying the registry value of security components such as antivirus products, and auditing registry keys by utilizing windows binary such as reg.exe and regedit.exe. A technique utilized to evade defense by modifying the registry is the use of reg.exe binary to disable Windows Defender and below is the procedure on how adversaries have performed the task.
T1053 Scheduled Task/Job | Tactics: Execution, Persistence, Privilege Escalation | 12.22%
Schedule Task/Job (T1053) technique is employed by attackers to maintain persistence on a victim's system. By scheduling a payload to execute at a specific time interval, an attacker can ensure that their malicious code remains active even if the connection to the Command and Control (C2) server is lost. It can also be utilized to escalate privilege by executing the payload as a user with higher privilege. Adversaries have utilized the windows internal binary schtask.exe to schedule their payload execution. Below is the procedure of the aforementioned technique:
T1562 Impair Defenses | Tactic: Defense Evasion | 9.2%
Last but not least Impair Defenses (T1562) is in the 10th position on our list which falls under the Defense Evasion tactic. Adversaries employ this technique to circumvent existing defense mechanisms by disabling security software and services and logging solutions to evade detection. This approach prevents malware or adversary activities from being detected and removes any evidence of intrusion. Here are some of the commands that were used to disable Windows Defender:
Comparison with Other Top ATT&CK Techniques Lists
In addition to our report, there are many other insightful studies on the best ATT&CK methods.
The top 10 lists created by Picus, CrowdStrike, Recorded Future, and Red Canary are shown in the table below, along with the methodologies used in each list. Different techniques are listed differently, although variety does not imply inaccuracy or incompleteness.
Limitations
This is the first edition of Logpoint’s Top 10 attack techniques. Keeping this in mind it should be disclosed that the research outcomes are based on attacks detected and reported alerts fired in 365 days on customers and Logpoint’s test network. The research largely incorporates many of the attack vectors. Given the nature of the data collected, this outcome varies and is largely dependent on activated alerts and/or created.
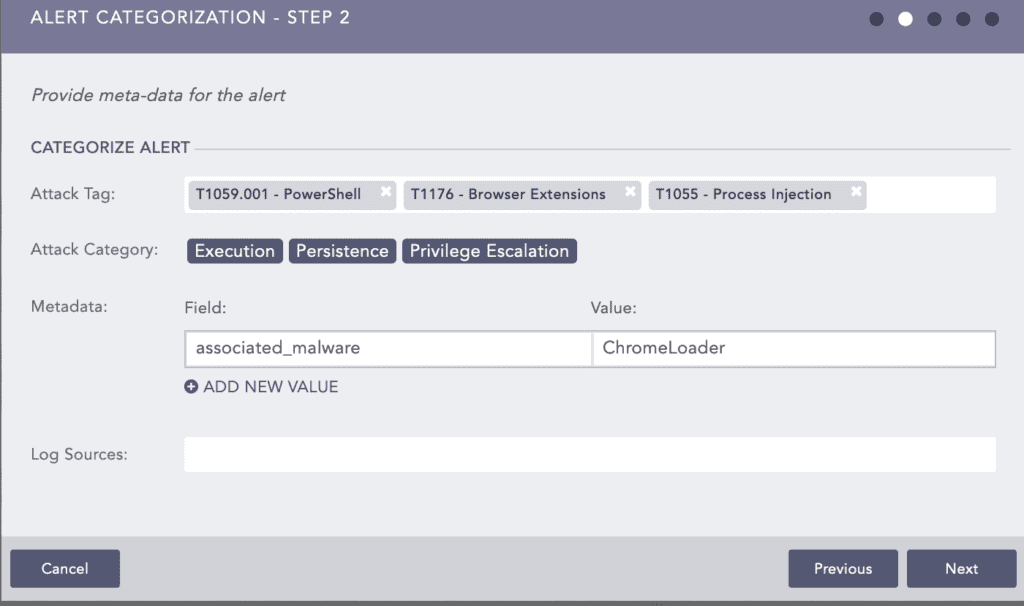
Also due to the design of the MITRE ATT&CK framework, an action may be mapped to multiple techniques with some techniques overlapping. For example, in a recent attack, Chromeloader uses Cross-Process Injection to Load Extention. We have mapped this attack in our Logpoint SIEM to Execution, Persistence, and Privilege Execution.
According to our methodology, a single instance of this attack adds one count to every three techniques.
The Bottom Line
This report aims to clarify that detecting threats at an early stage of the intrusion lifecycle can prevent significant cyber intrusions. It is also important to remember that appropriate processes for incident response and management can help reduce regulatory fines, cyber insurance premiums, potential revenue loss, and the impact on business operations. Often analysts and SOC teams can be overwhelmed with things they have to look out for. Knowing how and when to prioritize could be a definite game changer. Our experience has shown that this principle has helped many of our customers avoid significant harm over the years.
In most cases, we detect adversaries in the initial stages of their intrusion, when they are laying the groundwork for more damaging actions. We identify attempts to use operating system utilities to execute code or bring in custom tools, privilege escalation to gain deeper access to compromised systems, and establish persistence to maintain their presence. We also catch them manipulating our customers' defensive controls to evade detection or prevention. While these actions may be necessary means to an end, such as conducting espionage or a ransomware attack, disrupting these means can prevent their ultimate goals from being achieved.
Conclusion
The findings indicate that the most commonly used techniques by attackers fall under Defense Evasion and Execution tactics, with seven of the top ten ATT&CK strategies falling under these categories. Adversaries frequently employ legitimate software and techniques to avoid being detected and stopped by security controls. This highlights the need for organizations to continuously monitor and test their security controls to identify vulnerabilities and gaps that attackers could exploit.
To improve their security posture, organizations must prioritize measures such as regular security assessments, employee training, network segmentation, and multi-factor authentication. They must also monitor and analyze suspicious activity to detect and prevent attacks. Security professionals must remain vigilant and stay up-to-date with the latest techniques and tools used by attackers to ensure that their defense is effective.
In conclusion, by adopting a proactive and holistic approach to cybersecurity, organizations can improve their resilience and effectively mitigate the risks posed by cyber threats. All the detection rules in the Logpoint Converged SIEM platform are mapped with the MITRE ATT&CK framework. With the help of advanced security solutions such as Logpoint, companies can prevent and detect adversary TTPs, quantify their risks, and improve their overall security posture. With thousands of actual attack approaches, the Logpoint platform continuously tests your security controls in use and finds holes in your security stack.