It’s easy to integrate threat intelligence sources with LogPoint to help your organization understand its vulnerabilities and prioritize threats. There are numerous free and paid threat intelligence platforms and feeds you can use, one of which is MISP. An open-source platform, MISP, collects, shares and correlates threat information like vulnerabilities, indicators of compromise of targeted attacks, and financial fraud. You can integrate threat platforms and feeds, like MISP, as a source in the LogPoint Threat Intelligence application to fetch and analyze the logs. Analysts can use the fetched information to predict data breaches, vulnerability to attacks, and any evidence of pre-planned attacks or threats to their resources.
Follow the guide below to learn how easy it is to get started with threat intelligence, using MISP feeds as an example.
Get the Threat Intelligence application
Go to the LogPoint Help Center to access the Threat Intelligence application.
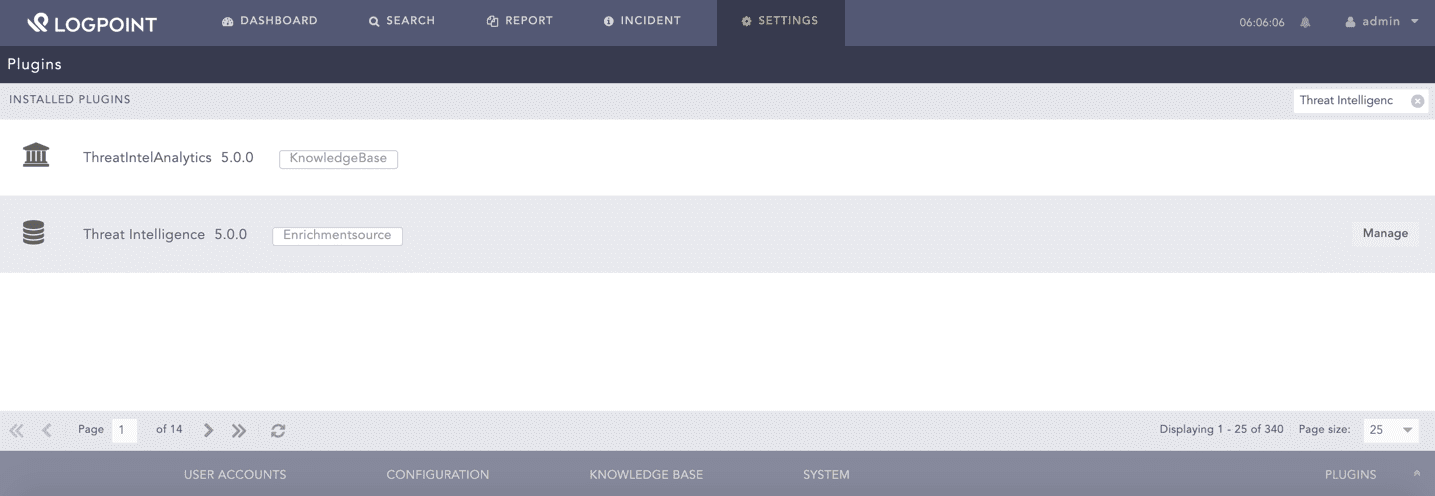
After downloading and installing the application, you can manage the application from the Plugins page.
You can see all of your integrations from the Plugins page.
Configure the Threat Intelligence platform
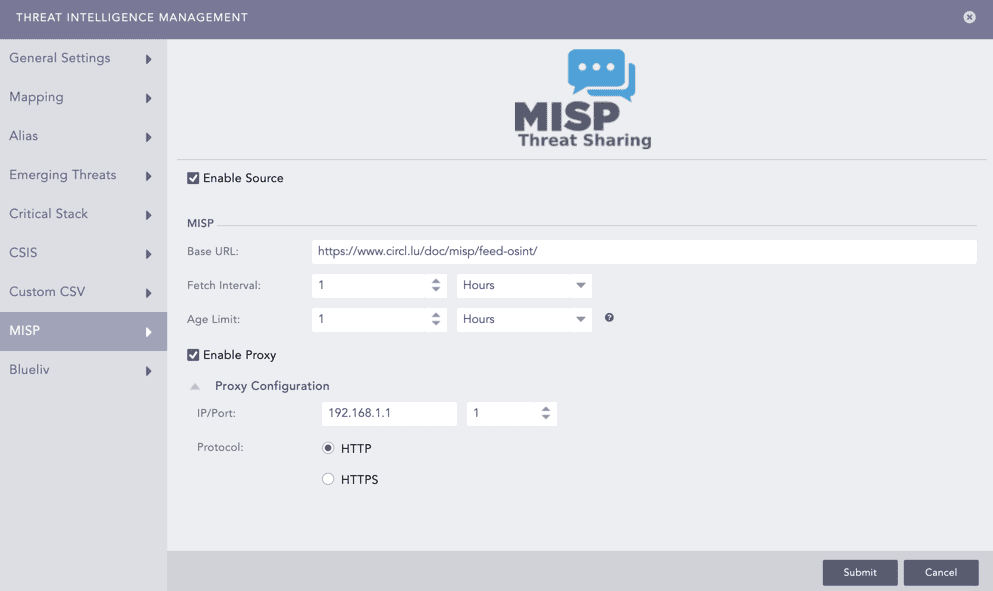
Select MISP from the Threat Intelligence Management panel. The Enable Source option is activated by default.
Select the Enable Proxy option to connect the MISP source via a proxy server. Enter the IP Address and the Port number of the proxy server, and select the HTTP or HTTPS protocol as required. Then, click Submit.
In the Management panel, you can see all of your connected Threat Intelligence feeds.
Search for threat intel results
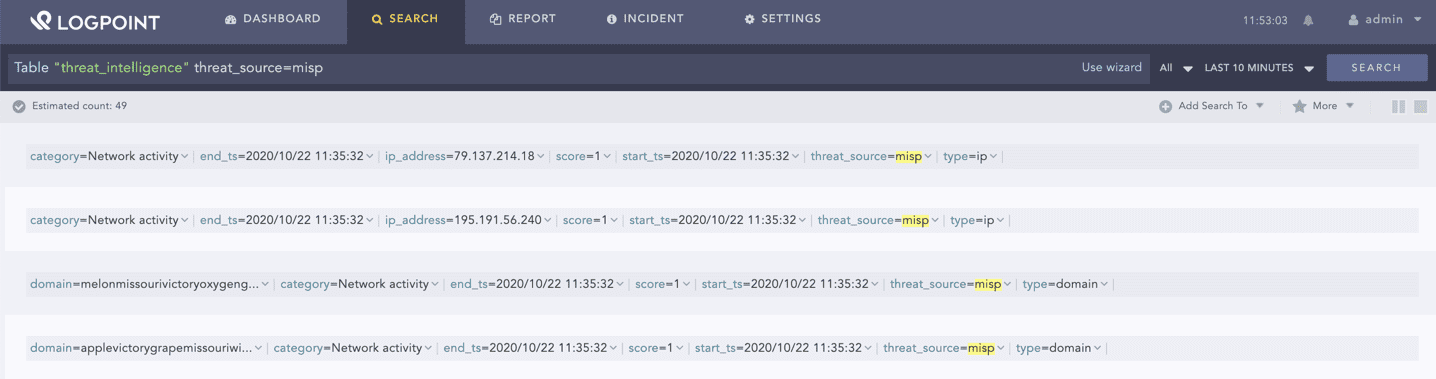
After configuring, you can search for MISP logs in the threat intelligence table.
Enter the following query to search for the logs:
Table "threat_intelligence" threat_source=misp
You can search for logs from specific sources.
Enrich logs with threat intelligence
The following examples show how a threat intelligence feed like MISP enriches your logs with contextual information to transform raw data into meaningful insights. Context from feeds helps analysts filter out noise and prioritize high-risk threats.
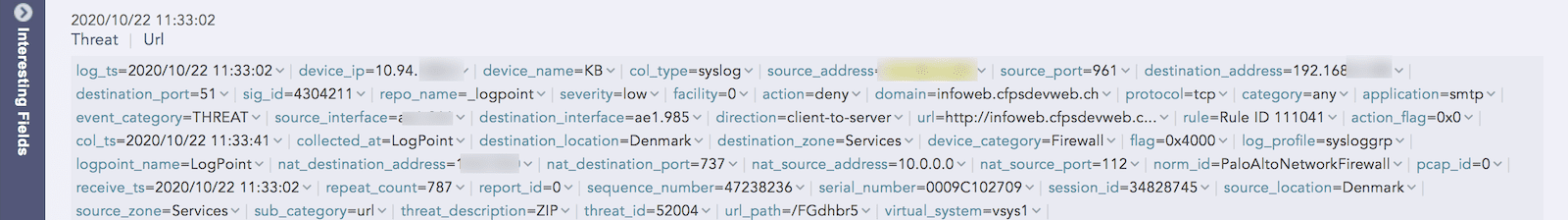
When logs aren’t enriched, it’s difficult for analysts to know how to prioritize the threat.
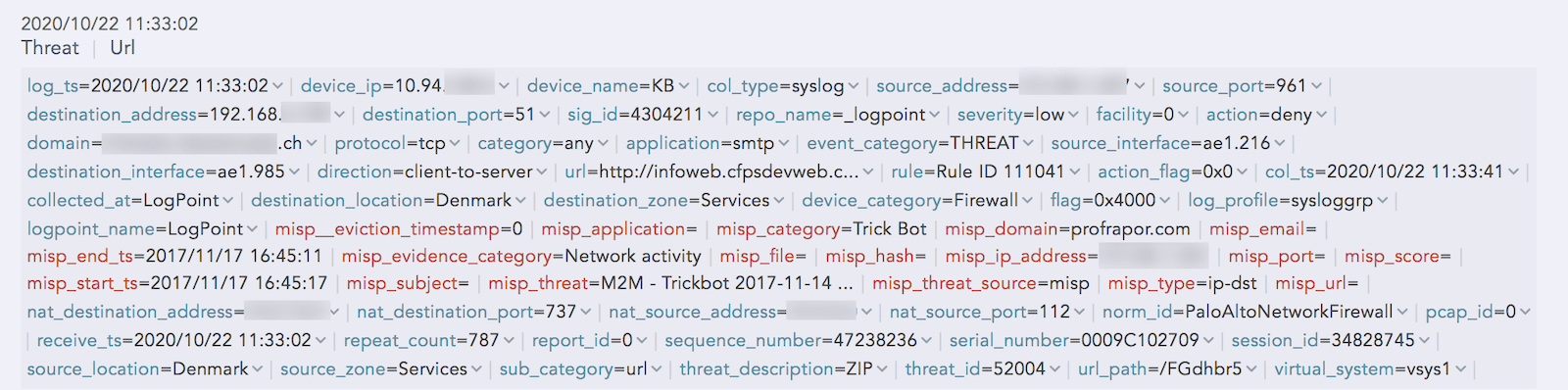
An example of a log from the Threat Intelligence application without enriched data.
Enrichment adds contextual information to the log, giving analysts more information to help investigate. A threat intelligence feed provides analysts with information about the threat type and score, so analysts can better evaluate the severity of the threat.
LogPoint shows the enriched log data as red text.
Get an overview of all threat intelligence
The LogPoint Threat Intelligence application comes with a ready-to-use Threat Intel Analytics package that includes general-purpose vendor alerts, rules and dashboards for threat intelligence. An overview helps analysts identify the most critical threats and know where to focus their resources.
Alerts
LogPoint provides the following alert packages, which merge a wealth of feeds into a single database for easy analysis.
- Threat intel connections with suspicious domains – Domains that the intel feeds label suspicious are integrated into LogPoint
- Threat intel internal machine connecting to multiple IOCs – An internal machine connecting to a number of suspicious resources on the web, such as IPs, URLs or specific resources like files hosted on popular services
- Threat intel excessive denied connections attempt from IOC – Sends an alert when the threat intel feed detects multiple denied connection attempts
- Threat intel allowed connections from suspicious sources – Sends an alert when the threat intel feed detects multiple allowed connection attempts
- Threat intel IOC connecting to multiple internal machines – Sends an alert if the threat intel feed marks an item as suspicious
Dashboards
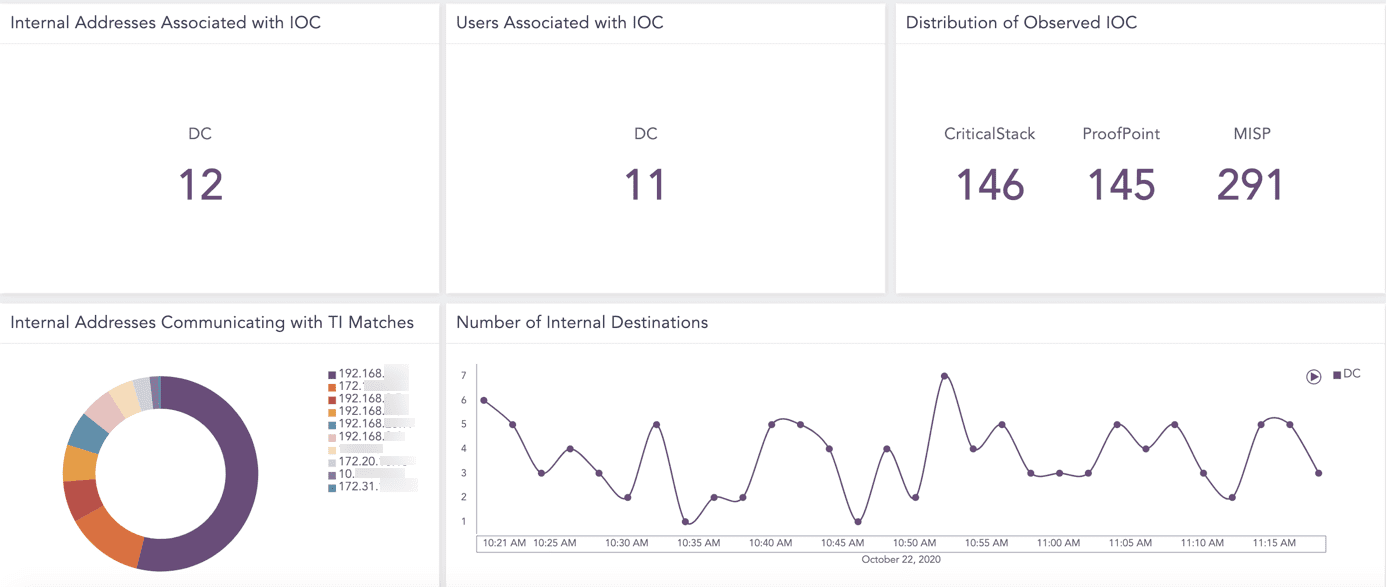
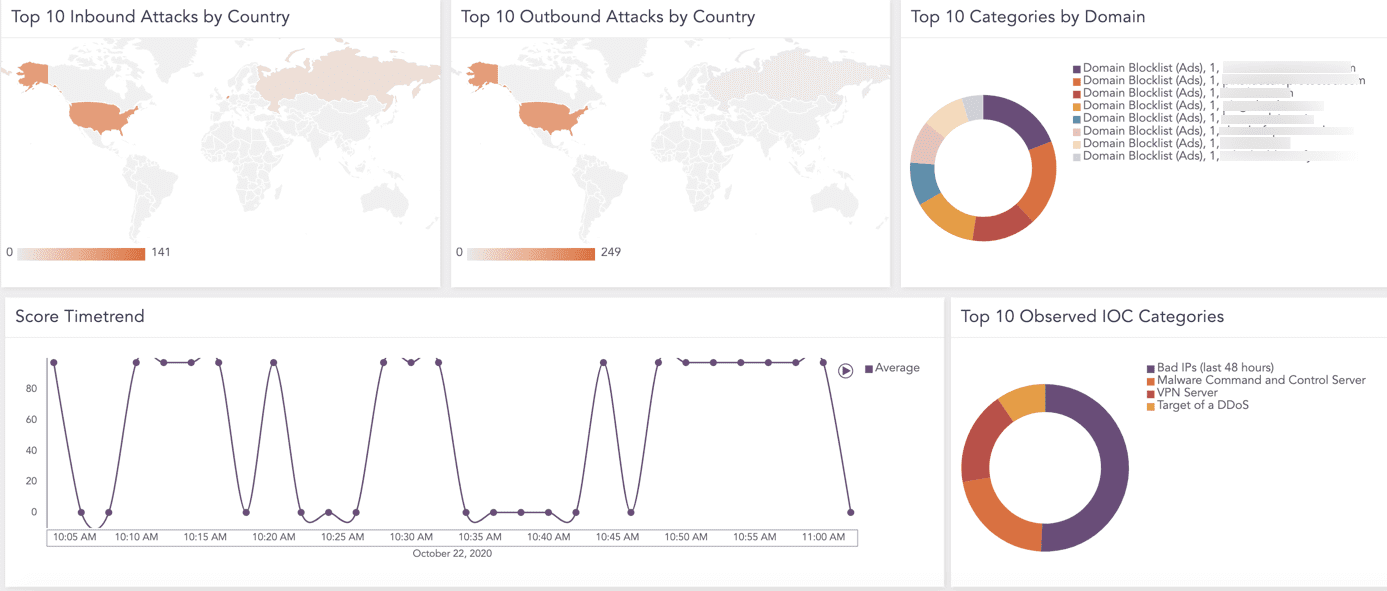
Analysts can get an overview of all integrated threat intelligence with the following dashboard widgets.
- Top 10 inbound attack alerts by country
- Top 10 outbound attack alerts by country
- Top 10 categories by domain
- Score time trend
- Top 10 observed IOC categories
- Internal addresses associated with IOC
- Users sssociated with IOC
- Distribution of observed IOC
- Internal addresses communicating with TI matches
- Number of internal destinations
Dashboard widgets give analysts a visual overview of threats.
Want to learn more?
If you have additional questions about integrating threat intelligence with LogPoint, reach out to your local LogPoint representative or contact us.