Despite the continuous evolution of cybersecurity, there is always a strong human factor in play, such as SOC teams. They are usually formed by individuals who monitor and respond to incidents and often involve employees. This human element also happens even on the other side of the fence.
Attackers are often human, and when they aren’t, as with generative AI (GenAi) cyber threats, there’s the planning and creation of these attacks which is often carried out by humans.
Go To Section
According to the ISC2 Cybersecurity Workforce Study, “staff/skill shortages impede the ability of cybersecurity teams to properly secure their organizations.” This study shows that only 52% of organizations believe they have the tools and people necessary to respond to cyber incidents over the next two to three years.
With this lack of resources, it’s important to optimize the existing ones – and that is exactly what we have done with this new release, from improved memory management to save-timing features.
More memory and less manual work
During resource-intensive operations, an inadequate heap memory allocation can make any software unresponsive and create service disruptions. But this thought is more ominous if we talk about SIEM solutions, where this leads to failure in log collection or unavailability of alerts and searches. Another consequence of running out of memory is the lack of scalability of your SIEM to expand your visibility.
To prevent all of this from happening, Converged SIEM comes with an upgraded AutoTuner, which optimizes memory usage automatically, and a new garbage collector, which continuously releases memory back.
No more manual memory tuning, saving time and effort, but more memory if you want to add more log sources to expand your visibility.
Detect and investigate incidents using fewer resources
With too many alerts to look at and too many incidents to investigate, the concept of a full-time threat hunter is blurry or almost non-existent in many SOC teams.
While we can’t add more resources to your organization, we can free up resources by easing processes like updating and populating lists of IoC, malicious domains, IPs, etc. By allowing you to add lists in .TXT and .CSV files, this process becomes more flexible than before and facilitates the analyst’s job of keeping threat detection up to date.
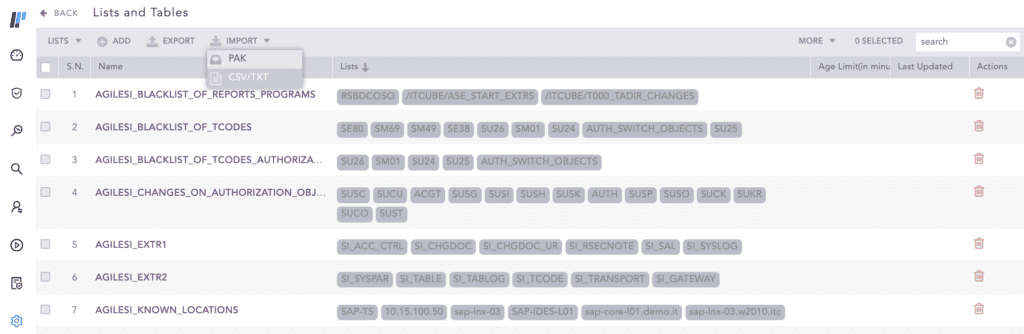
The work put in during the last months to increase efficiency and reduce effort in daily tasks for threat detection also shows in the new and improved interface for alert set-up. With one single window and fewer clicks to configure or modify an alert, SOC team members will save time in this type of operations
In addition to this, Converged SIEM has improved how incident responders investigate cases. By including the option of searching the logs that trigger a playbook directly from the case and bringing the results back to it, they don’t have to go back and forth between the search page and the case manager
To free up precious resources like time, Converged SIEM can now extract incident artifacts into cases automatically. The user can add a new playbook action that will read the incidents and add all the extractable data from it as artifacts and put them in the case, optimizing resources for the analyst, who otherwise would have added them manually.
Ease of work for MSSP and those working with distributed environments
With the latest release, Logpoint brings improvements to log management and automation specifically tailored to those in distributed environments.
To start with, they can now forward raw logs from on-prem sources to remote servers to cover different use cases like compliance. Search results are now much more complete as users can connect their LDAP server with the collector, fetching user information and enriching the search results.
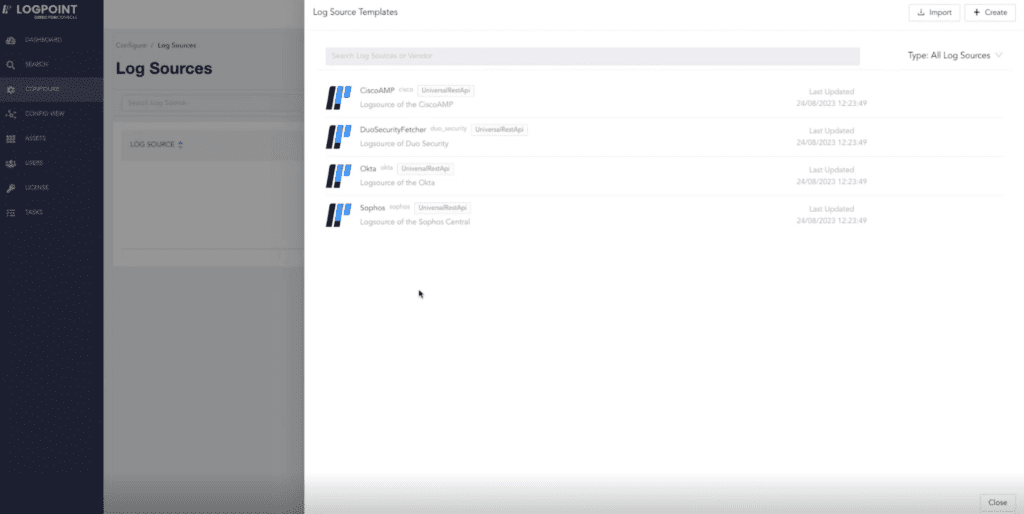
Repetitive tasks should be automated or simplified to avoid consuming vast resources. This idea has been applied to log source configuration in Director. With one centralized platform to create and manage log sources, MSSPs can now use preconfigured templates to reduce the complexity of setting up log sources across tenants
Ease of work for multitenancy also goes for the update and distribution of playbooks. Now, SOC members can cut down on costs and reduce errors when shipping playbooks to their customers thanks to out-of-the-box generic playbooks that are integration agnostic. This way, they can update a playbook once and affect all tenants without worrying about the different integrations their customers can have.
Mastering automation that doesn’t cost extra resources
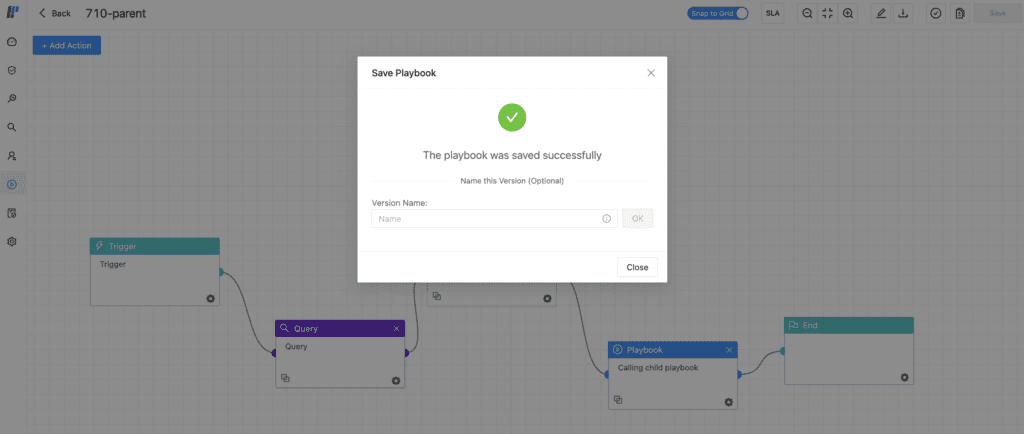
When updating how playbooks behave in Converged SIEM, we also put an emphasis on the human factor. People make mistakes, so let’s give analysts the possibility of restoring a playbook to a saved version instead of having to correct it or build it from scratch – and, in doing so, reducing a considerable amount of work.
With this idea of removing unnecessary workload, now it’s possible to save scripts. This way, if your team works with playbooks that contain similar data, they don’t have to write the script from the beginning. Instead, they can edit the Python code according to their needs, for example, by changing the username.
But that’s not all because different enhancements in the playbook canvas provide users with more ease of work. Another update is the ability to save scripts. From small visual improvements such as snap to grid for building blocks to string manipulation testing to verify everything works before running an action in a playbook, each improvement facilitates how analysts work with playbooks.
We expect these updates will allow SOC teams to free up resources to focus on what matters the most, like securing their organization. If you want to know more about all these updates in Converged SIEM and Director, you can contact your sales representative.






