By Nils Krumrey, UK Presales Lead, LogPoint
Cyberattacks are getting increasingly sophisticated, and attackers can circumvent even the best security controls and policies. Once the adversaries gain access to a system, it is crucial to stop them as soon as possible to reduce the damage. The challenge is that security operations teams must manage thousands of indicators of compromise and multiple security tools with limited time, making it difficult to detect and respond to malicious activity. One effective solution is to prioritize indicators of compromise by enhancing your SIEM with the ATT&CK framework by the MITRE Corporation.
ATT&CK at the apex of the pyramid
The ATT&CK framework is an industry-standard classification of adversarial tactics and techniques based on real-world observations of different cyberattacks. The framework is vendor-agnostic and community-driven, providing a common classification across multiple products and users. ATT&CK is an acronym for Adversarial Tactics, Techniques & Common Knowledge, implying the different parts of the framework. Tactics are threat actors’ objectives or goals, and techniques are the specific methods they use to achieve them. Security analysts can use the framework to understand adversarial behavior and how attackers carry out attacks.
Security professional David Bianco introduced the pyramid of pain to describe the different indicators of compromise to spot malicious activity. The further up the pyramid you detect and respond, the more painful or challenging it is for the attacker to go through with an attack. Defenses based on indicators of compromise at the bottom half of the pyramid, hash values, IP addresses, and domain names, are simple for an attacker to circumvent and consequently not very valuable to analysts.
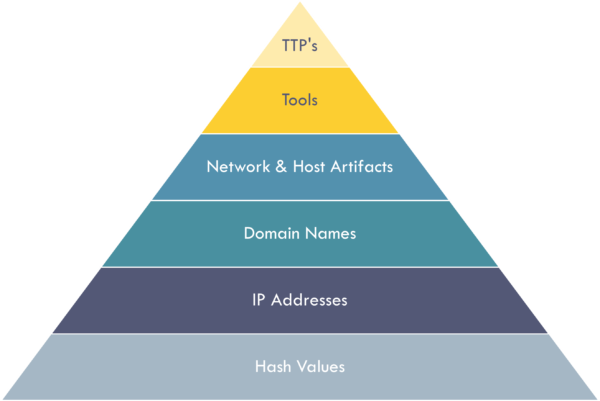
Instead, it helps to defend based on the indicators at the top half of the pyramid. Network and host artifacts, tools, and especially tactics, techniques and procedures (TTPs) pose a more significant challenge to attackers. The ATT&CK framework, in its nature, enables detection and response against TTPs, providing the most robust defense. Defending your network against TTPs prevents attackers from using their approach, forcing them to either spend a lot of time and effort developing new techniques or move on to the next target. The attackers will most likely choose the latter.
Enhancing your SIEM with the ATT&CK framework
The ATT&CK framework practically provides a playbook of possible cyberattacks, which works effectively with SIEM solutions. SIEMs provide monitoring, detection, and alerts of security events or incidents within an IT environment. Enhancing SIEM capabilities with the threat intelligence of the ATT&CK framework allows analysts to understand the specifics of an attack better.
When your SIEM solution generates an alert, you understand why it’s firing. Mapping it against the ATT&CK framework allows you to understand what it means. For example, analysts can see whether an alert correlates to a specific ATT&CK technique, a known threat group, or seemingly unrelated alerts to get a better picture.
For example, to identify if an event is a smokescreen for something else happening in the environment. Enhancing your SIEM with the ATT&CK framework offers stronger indicators so you can detect a threat faster and respond accordingly.
How LogPoint uses MITRE ATT&CK
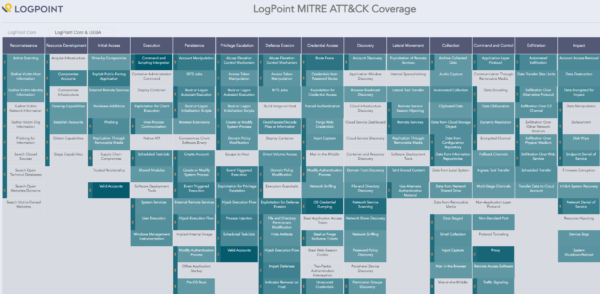
LogPoint’s SIEM solution covers a significant part of the ATT&CK framework’s use cases. For example, LogPoint maps all of its queries around the framework to make it easier for analysts to collect solid threat intelligence and identify indicators of compromise against TTPs. Another example of how LogPoint uses the ATT&CK framework is alert rules. The ATT&CK model assigns a unique ID to every adversarial tactic, and all enabled alert rules in LogPoint will return an alert with an ATT&CK ID attached. The ID makes it easy for an analyst to see whether disparate alerts match a single attack following an established sequence.
LogPoint’s UEBA module uses machine learning to detect suspicious user and entity behavior. The technology behind UEBA perfectly complements the detection capabilities with the tactical methods in the framework. Instead of rigid queries, searches, or other data constructs that typically come together with a SIEM, LogPoint UEBA matches the machine learning algorithms to actual practical scenarios rather than non-cohesive, singular items of interest.
Many SIEM providers offer a specific ATT&CK framework coverage, but few can put an exact number on the use cases covered. It’s easier to get a complete picture of the actual value of the SIEM solution when the number of use cases covered by ATT&CK is transparent. LogPoint offers full transparency about which tactics and techniques it covers with LogPoint ATT&CK Navigator.
You can read more about how to use MITRE ATTA&CK in LogPoint on our website.