Updated July 18, 2023
Fast Facts
- CVE-2023-36884 is an Office and Windows HTML Remote Code Execution Vulnerability.
- No patch is available for this zero-day as of 13 July 2023.
- Microsoft is still investigating reports of a series of remote code execution vulnerabilities impacting Windows and Office products.
- Users of Microsoft Defender for Office 365 and Microsoft 365 Apps users (Versions 2302 and later) are protected against vulnerability exploitation through Office.
- Storm-0978 has exploited CVE-2023-36884 to conduct a targeted phishing campaign against individuals and countries supporting Ukraine, particularly during the Ukrainian World Congress NATO Summit.
Go To Section
Background
On June 11, Microsoft issued an advisory about a fresh zero-day vulnerability (CVE-2023-36884), which was exploited by a threat actor known as Storm-0978 (also called RomCom). The adversary was found abusing this vulnerability in their phishing campaigns targeted against defense and government entities in Europe and North America notably targeting upcoming NATO Summit guests who may also be providing support to Ukraine as reported by Blackberry in their article published on July 7. According to Microsoft, the vulnerability resides in Office products and can be exploited for remote code execution with a CVSS score of CVSS:3.1 8.3 / 8.1
Technical Analysis
Nato Summit got held on 11-12 July 2023 in Vilnius, Lithuania. One of the topics was about Ukraine joining NATO. According to the BlackBerry Threat Research and Intelligence team, to take advantage of the event, adversaries create crafted Word documents with alluring messages and send them to target individuals who were participating in the event.

source: Microsoft
They also found another masqueraded malicious document from the same threat actor, which they believed to be a lure based on the upcoming NATO Summit in support of Ukraine.

Source: Microsoft
As soon as the target downloads and opens that malicious document, it starts making outbound connections with the attacker’s machine, allowing the attacker remote control over the victim’s machine.
Infection Chain
Microsoft has reported that Storm-0978 executed a phishing operation targeting defense and government organizations in Europe and North America, employing a counterfeit OneDrive loader to distribute a backdoor resembling RomCom. The phishing emails, centered around the Ukrainian World Congress, exploited the CVE-2023-36884 vulnerability. On the contrary, Threar Intel at Blackberry states, the threat actor likely relied on spear-phishing techniques, engaging their victims to click on a specially crafted replica of the Ukrainian World Congress website. They typosquatted the real domain of the Ukrainian World Congress website ukrainianworldcongress[.]org with a fake domain ukrainianworldcongress[.]info.
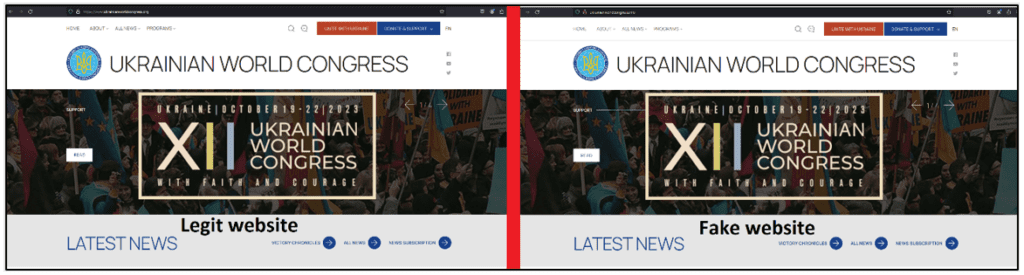
Source: Blackberry
According to Microsoft, in addition to the CVE-2023-36884 vulnerability, threat actors were found leveraging additional vulnerabilities on the target machine such as Follina (CVE-2022-30190). They also use 'trojanized' software to disseminate the RomCom backdoor, such as Adobe products and Signal. They use malicious domains that seem like real software names and carry out financially driven assaults utilizing the ransomware Industrial Spy, Underground, and Trigona.
Storm-0978 has used a variety of tactics to obtain unauthorized access during ransomware assaults. One approach is to extract password hashes from the Security Account Manager (SAM) by modifying the Windows registry, which requires SYSTEM-level access. Microsoft Defender for Endpoints generates alarms when this action occurs, particularly when the SAM registry hive is exported.
Following the credential acquisition, Storm-0978 employs the Impacket framework's SMBExec and WMIExec features to assist lateral movement inside the infiltrated network. These strategies enable the attacker to move between computers and expand their reach inside the targeted environment.
Detection Using Logpoint Converged SIEM
Required Log Sources
-
Windows
-
Process Creation with Command Line Auditing should be enabled
-
Microsoft-Windows-Windows Defender/Operational
-
Microsoft-Windows-Windows Defender/WHC
-
-
Windows Sysmon
Detection
1. Microsft office365 Child Processes
When a phishing document is suspected to be the initial access point for cyber attacks, it becomes crucial to prioritize the hunting and investigation of child processes spawned by office applications. Analysts can use the following targeted query to look for child processes of office apps.
-
Microsoft Office Product Spawning Windows Shell
For a more focused search, Analysts should carefully filter for child processes created by Microsoft Office programs that interact with the Windows shell. Because these processes may execute commands and scripts, they are an important subject for analysis in order to uncover any potentially harmful activity linked with the ransomware assault.
-
Attack Surface Reduction (ASR)
Administrators can configure Microsoft Defender’s Attack Surface Reduction (ASR) rules to detect suspicious Office activities, such as an Office application creating executable files.
-
A suspicious file dropped during Potential CVE-2023-36884 Exploitation
During the alleged exploitation of CVE-2023-36884, a new file, especially a file with a ".url" extension was seen being dropped. The query below is intended to identify the creation of a certain file in Office's recent folder.
-
Potential CVE-2023-36884 Exploitation - File Downloads
During the campaign, Romcom was spotted requesting and downloading several files, perhaps abusing CVE-2023-36884. This sigma rule can be used to hunt such requests through network logs.
Mitigations
Here are official recommendations for mitigations of CVE-2023-36884 provided by Microsoft themselves.
- Customers who use Microsoft Defender for Office are protected from attachments that attempt to exploit this vulnerability.
- In current attack chains, the use of the Block all Office applications from creating child processes Attack Surface Reduction Rule will prevent the vulnerability from being exploited.
- Organizations that cannot take advantage of these protections can set the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key to avoid exploitation. No OS restart is required, but restarting the applications that have had the registry key added for them is recommended in case the value was already queried and is cached. Please note that while these registry settings would mitigate exploitation of this issue, they could affect regular functionality for certain use cases related to these applications. For this reason, we suggest testing. To disable the mitigation, delete the registry key or set it to “0”.
- Add the following application names to this registry key as values of type REG_DWORD with data 1.:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
-
Excel.exe
-
Graph.exe
-
MSAccess.exe
-
MSPub.exe
-
Powerpnt.exe
-
Visio.exe
-
WinProj.exe
-
WinWord.exe
-
Wordpad.exe
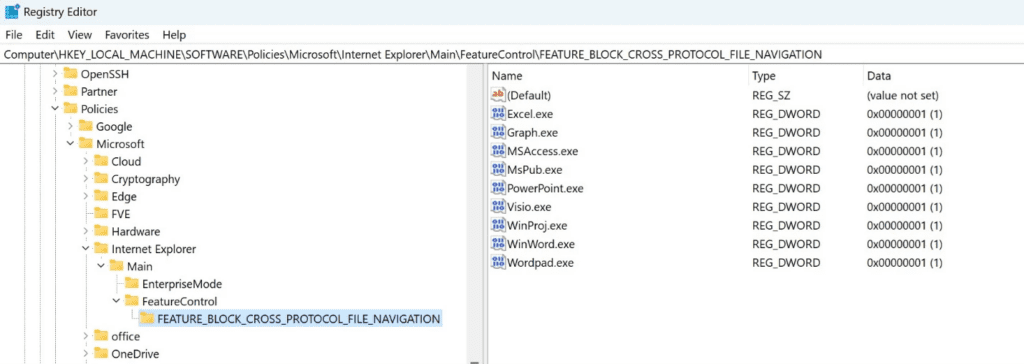
Source: Microsoft
Recommendation
-
Conduct simulated attack scenarios to make sure that the employees are well aware of phishing and other risks, and also to make sure that they report the incident to the internal cybersecurity team
-
Always be suspicious of any message that requests you to click a link or open an attachment.
-
Configure email security technologies such as SPF, DKIM, and DMARC to authenticate and verify the origin of incoming emails.
-
Utilize phishing-resistant multi-factor authentication whenever possible. Require all accounts with password logins to have strong, unique passwords, and change passwords immediately if there are indications that a password may have been compromised.
-
Update and patch systems regularly whenever possible.
-
Regularly review the security posture of third-party vendors interconnected with the organization.
-
Continuously monitor critical organizational assets with a combination of tools such as Sysmon and the Logpoint Converged SIEM platform.
Final Thoughts
CVE-2023-36884 as an n-day can be exploited by adversaries for their malicious purposes. So, it’s vital to detect such activity in the early phases of their attack lifecycle if possible. If the attack’s traits are detected early, then the possible damage can be contained. Early detection and mitigation are possible with Logpoint Converged SIEM. Our end-to-end security operations platform helps you detect, investigate, and remediate attacks like the one by Storm-0978. Converged SIEM consolidates SIEM, SOAR, UEBA, and a native endpoint agent capable of remediation actions (AgentX) for faster TDIR of all sorts of attacks, including but not limited to ransomware, spyware, and botnet.
Logpoint Converged SIEM is a robust platform that assists analysts in effectively detecting and responding to security problems. It includes pre-defined alert rules that include Tactics, Techniques, and Procedures (TTPs), as well as behavior and pattern indications of suspicious acts that differ from regular user behavior, allowing analysts to efficiently prioritize and analyze possible security issues. Logpoint's SOAR features automate repetitive operations, organize incident response workflows, and optimize issue management procedures, resulting in faster reaction times and less manual labor. User And Entity Behavior Analytics Analytics (UEBA) feature in the system analyzes irregularities in user and object activity, recognizing potential insider threats and compromised accounts. The native agent of Logpoint, AgentX, enables real-time reaction measures such as isolating compromised endpoints and preventing communication with malicious domains. Overall, Logpoint Converged SIEM equips enterprises to detect, investigate, and remediate a wide range of attacks, including n-day vulnerabilities, through its OOTB alerts, SOAR capabilities, UEBA functionality, and AgentX.
IP addresses
104[.]234.239.26
138[.]124.183.8
45[.]9.148.118
45[.]9.148.219
45[.]9.148.123
74[.]50.94.156
209[.]159.147.170
66[.]23.226.102
209[.]127.116.190
65[.]21.27.250
Domain
bentaxworld[.]com
penofach[.]com
altimata[.]org
finformservice[.]com
URL
hxxp://finformservice[.]com:80/api/v1.5/
subscriptiontoken=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
eyJpZCI6MTIzNDU2Nzg5LCJuYW1lIjoiSm9zZXBoIn0.
OpOSSw7e485LOP5PrzScxHb7SR6sAOMRckfFwi4rp7o
hxxp://65.21.27[.2]50:8080/mds/O--------------------------
hxxp://finformservicecom:8080/mds/S--------------------------






