By Santosh Nepal and Anish Bogati; Security Research
Updated on 21st April
Quick Digest:
When a new application is downloaded, most users assume it’s a safe file and has retrieved what is expected. However, what if an application had been tampered with? Instead of a legitimate application, what if the downloaded binary is a trojan that is designed to steal personal information and perform other unwanted actions? This is the reality of trojanized desktop applications, a form of malware.
In this blog, we’ll explore the tactics used by attackers to distribute trojanized 3CX desktop applications.

Go To Section
According to CrowdStrike, they observed an anomaly from the signed binary, 3CXDesktopApp — unified communication with integrated CRM and videoconferencing facilities. The 3CX application is being used by a large number of customers which include well-established companies like American Express, Coca-Cola, Pepsi, Honda, McDonald's, and Toyota. The issue in question has been allocated a CVE (Common Vulnerabilities and Exposures) identification number, specifically tracked as CVE-2023-29059.
The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on keyboard activity. The campaign has been attributed to LABYRINTH CHOLLIMA aka Lazarus Group (G0032), which is linked with the alleged cyber-warfare unit of North Korea's intelligence agency. One of the factors for attribution to the threat actor is the use of hard-coded RC4 decryption key 3jB(2bsG#@c7.
The malicious attribute of the application binary was flagged by various EDRs such as CrowdStrike, PaloAlto Networks, Sentinel One, and Eset and pointed out by various customers since March 2022, in response to which 3CX reportedly dismissed the concern with a verdict that those detections were wrong. Now, as the claims made from next-generation defense EDRs have proven to be correct and the supply chain attack has struck hard, with more than 200 thousand devices impacted, 3CX has appointed Google subsidiary, Mandiant, as an independent reviewer in an attempt to uncover details and review the security incident.
The intrusion overview
Disclaimer - The 3CX supply chain attack was not just a standalone incident but a part of a sophisticated double supply chain attack.
North Korean nation-sponsored threat actors had been targeting crypto trading sites either by creating a phishing website or compromising the websites to distribute their malware. One such site which was compromised by the adversaries was tradingtechnologies[.]com. The threat actor utilized techniques such as Drive-by Compromise [T1189] where they exploited the vulnerabilities in the websites and hosted hidden iframes to serve the payloads to visitors.
According to 3CX, one of their employees downloaded and installed the Trading Technologies X_TRADER software on the system. Like 3CX Desktop Application, the X_TRADER installation software was trojanized, and contained VEILEDSIGNAL malware, enabling the threat actor to access the system and maintain persistence. After gaining access, threat actors were successful in retrieving credentials from the employee's system. Among the credentials, adversaries were able to retrieve the 3CX organization VPN credentials of the employee. In two days of infecting the employee system, adversaries were able to organization’s network through VPN.
The threat actors utilized Fast Reverse Proxy tool to move laterally within the 3CX environment. The tool was masquerading as MsMpEng.exe and was dropped in the C:\Windows\System32 directory.
According to Mandiant, after gaining access to the organization system, to move laterally they performed credentials harvesting. The attacker succeeded in compromising the Windows and macOS build environments. In the Windows build environment, the attacker installed a TAXHAUL launcher and COLDCAT downloader which persisted by DLL side-loading through the IKEEXT service and operated with LocalSystem privileges. On the other hand, the macOS build server was infiltrated using a POOLRAT backdoor, leveraging Launch Daemons as a persistence mechanism.
Am I Affected?
Currently, some versions of the application for MacOS and Windows are only found to be used in malicious campaigns as per the release from 3CX, whereby the users are urged to immediately uninstall the application. Meanwhile, no news on mobile apps for Android and iOS/Apple has been reported.
| OS | Version |
|---|---|
| Windows |
|
| Mac |
|
However, other versions can be also modified to include payload by adversaries.
Attack Chain
At the time of publication, a total of 244,175 has been observed in Shodan(click for latest update), with the most exposed devices have been recorded in USA. with 53K followed by Germany and France with 37k and 24k counts respectively.
The attack shows some relation to breaches at SolarWinds back in 2020. This comes on the back to the fact that similar to SolarWinds, some security vendors have identified this attack to be possible after attackers had access to the 3cxs development or build environment. Forensics on GitHub suggests that the Windows variant was activated on December 7, 2022. The domain and web infrastructure were registered around early November. The application was weaponized when the company’s signed certificate was obtained, modified, and delivered to a legitimate update channel on the server, which ultimately led to a malicious version of the software being distributed.
Guided by behavioral detections, abuse of 3CXDesktopApp was detected leading the trojan-laden installers to be quarantined with immediate effect. The application with the update process led to malicious behavior observed with C2 communication to various external servers.
This application is in itself just the first stage of a multi-stage attack chain. As per the publication on Unit42 of Palo Alto, once on the system, the MSI installer runs the executable and loads a ffmeg.dll malicious library file. This is followed by extraction of d3dcompiler_47.dll, a portion of which is decrypted, using RC4 and key 3jB(2bsG#@c7, and loads embedded DLL.
After their execution, a random date of 1-4 weeks is selected. With the time-based logic bomb against the current machine time, it gets triggered at the designated time. this allows successful obfuscation of malware within the system for the hibernation period. It follows the malicious DLL file cloning icon (*.ICO files) with base64 data(encryption with AES-GCM encryption algorithm) appended from the GitHub repo. This sets up for final stage of infection that involves the decryption of .ico files to extract the URL, which is subsequently used for HTTPS GET request, expecting a key named “meta” from the response JSON. The value corresponding to the key is parsed and as with the previous decryption, the same process is run to decrypt the final data which runs on the target machine.
On the mac variant, in place of obtaining C2 Url from a .ico file. a list of 15 hardcoded URLs is present that will communicate with the C2 server.
The attack chain begins with the ECX Electron application update which drops multiple payloads in the system in the process. While the 3CXDesktopApp.exe binary update gets started it loads the ffmpeg.dll which contains the malicious payload. Then ffmpeg.dll drops another payload to the system. ffmpeg.dll and d3dcompiler_47.dll are not malware in themselves but are legitimate files that are trojanized by adversaries. d3compiler_47.dll is a DLL file signed by Microsoft but contains an embedded secondary encrypted payload.
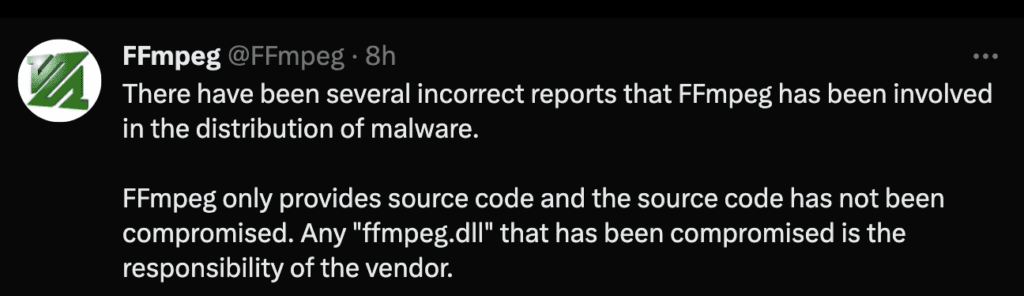
Source - FFmpeg
As mentioned above after the selected sleep time, the payload is activated. It then attempts to access the GitHub file hosting page and downloads other stages of payloads. In the final stage, an information stealer malware is dropped into the system which has mainly targeted sensitive data stored by browsers such as Chrome, Edge, Brave, and Firefox web browsers.
According to an update from Crowdstrike(31st March), the first beaconing activity was detected on March 7th, where the beacon structure and encryption key matched with other campaigns by Labyrinth Chollima.
As published on April 3, 2023, on further analysis by Securilist, telemetry review on one of machine observed guard64.dll file loaded into 3CXDesktopApp.exe process, and the same file name. While. was found in recent backdoor deployment on “Gopuram”. This file has been around in cybersecurity space for 3 years and Gopurum was found coexisting on victim machine with another backdoor, AppleJeus, attributed to Lazarus, as seen at SouthEast Asia cryptocurrency company infection. This consolidates the claim made by several vendors, that the notorious Lazarus group is associated to 3CX task. It was also observed that attackers dropped malicious wlbsctrl.dll and encrypted shell payload(.TxR.0.regtrans-ms) on systems impacted.
How to detect the trojanized version of 3CXDesktopApp using Logpoint
Even though appropriate mitigation and prevention mechanism has been implemented, it is highly advisable to look for indicators of attacks and detect traces of the trojan and intrusion artifacts. For detecting the incidents users can utilize available alert rules and provided queries in the Logpoint Converged SIEM platform.
Log Source Needed
-
Windows
-
Windows Sysmon
-
Firewall
-
IDS/IPS
-
Proxy
-
Process Creation with Command Line Auditing should be enabled
-
Registry Auditing should be enabled
-
File System Auditing should be enabled
Detecting IOC
Since the campaigns were initiated in March 2022, it is imperative to employ the detection query below to search for events from March 21 onwards. By taking into account the specified date, we can prioritize the detection of the given indicator of compromise.
Below query can be utilized to discover the connection to the known C2 server.
Also, users can utilize the query provided below to search for the known hash of the malicious files from the campaign.
For communication to the C2 server adversaries have hard-coded the user-agent header’s value, so the below query can be utilized to detect a remote connection to the C2 server utilizing the header
As for downloading other stages of payload, the dropper connects to a GitHub repository. The below query can be used to detect such events:
Detecting Malicious Version of the 3CX app
A certain version of 3CXDesktopApp.exe was found to be trojanized. By using WindowsSysmon logs we can look for the versions that are used in malware distribution campaigns.
Fortunately, if you have not set up Sysmon you can use the below query to detect the host running the application by utilizing Native Windows logs. As the native windows log doesn’t have OriginalFileName, product name, file version, etc. fields in the log.
Browser Credential Files Accessed
As per the SentinelOne report, in the final stage of the attack adversaries have deployed an information stealer in the form of DLL that retrieves credentials from browsers such as Chrome, Edge, Brave, and Firefox browsers.
Detecting Connection to Suspicious IP address and Domain
Once the application has been installed, additional payloads are deployed into the system and establish communication with the C2 server. Through the utilization of the threat intelligence (TI) plugin, we can identify IP addresses that have been flagged by numerous threat intelligence platforms.
We can also do the same for domains:
Network Connection to Suspicious Server
From a case, the payload tries to connect to the GitHub hosting server for downloading later stages of the payload. Currently, the user is taken down but adversaries can utilize other freely available hosting sites. By using this alert we can detect events where connection to some of the commonly used file-sharing sites by adversaries is detected.
Post-Detection Activities
After detecting the indicator of attacks, it is necessary to detect backdoors or any persistence methods utilized by adversaries. Lazarus group has utilized techniques such as Account Manipulation, Registry Run Keys / Startup Folder, Shortcut Modification, Windows Service, Schedule Task/Job, BootKit, and Valid Accounts for persistence.
To verify some of the persistence techniques below alerts and queries can be utilized:
Adversaries have dropped multiple files in the system which can be scheduled to run at a certain time or in a time interval. This alert helps to detect the scheduling of new tasks.
Note: Registry auditing for the Key should be enabled.
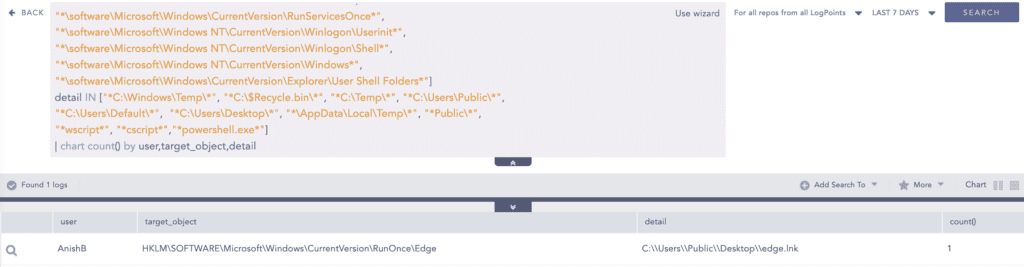
Also, in many incidents adversaries have modified Autorun registry keys to include their malicious payload to be executed during system boot-up or when the user logins to the system. This alert can help to detect such events.
Note: Registry auditing for the Key should be enabled.
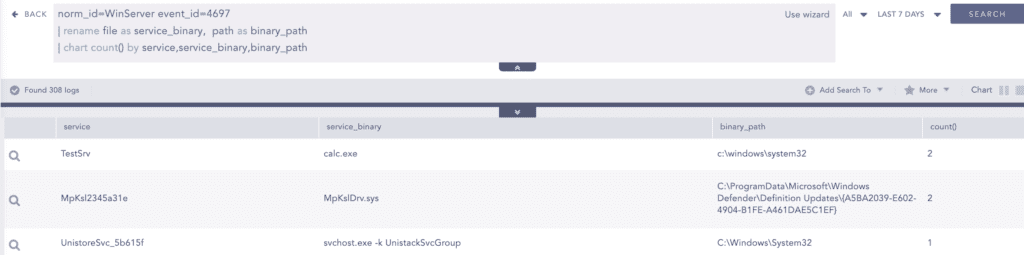
Also, it is important to search for any new service creation events. To do so below query can be utilized
In the above query service name and file are renamed to have better visualization.
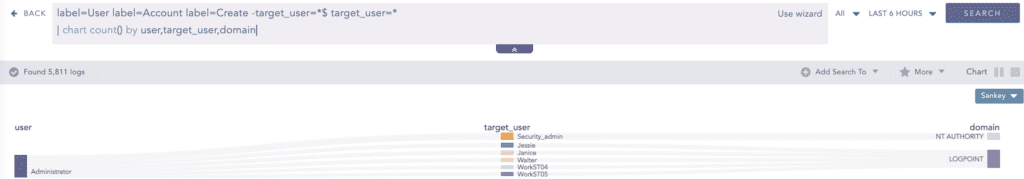
And in other cases adversaries can create a new user account for persistence and below is the query to detect such events:
Incident response with Logpoint SOAR and AgentX
Logpoint has integrated AgentX, an advanced security solution that enables the detection, investigation, and response to endpoint security incidents powered by the Logpoint Converged SIEM platform, as well as faster threat detection using SOAR. Thanks to built-in log and telemetry enrichment of SIEM and SOAR events, AgentX not only collects logs and telemetry from endpoints but also provides additional context through MITRE TTP to reduce MTTR.
Logpoint AgentX is available now: Contact your representative.
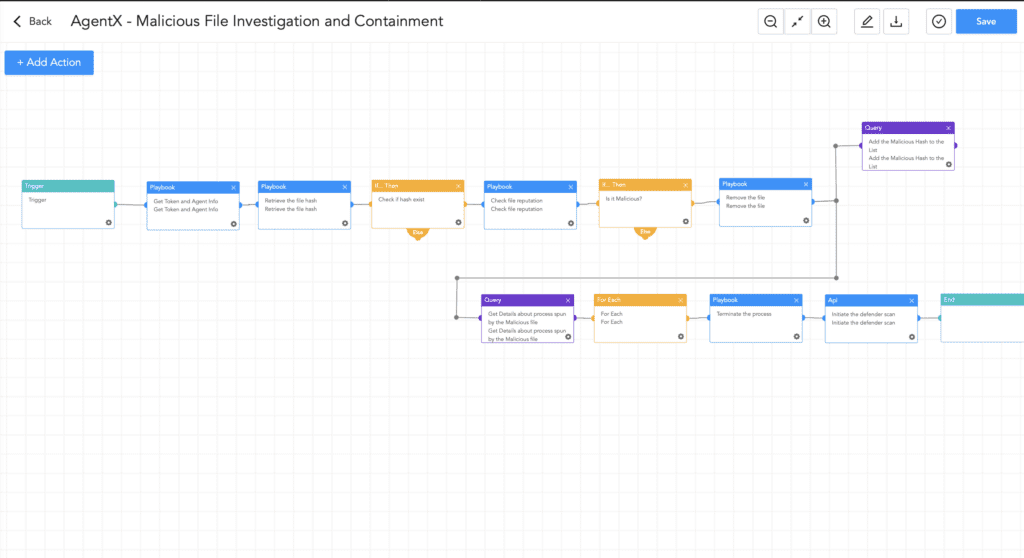
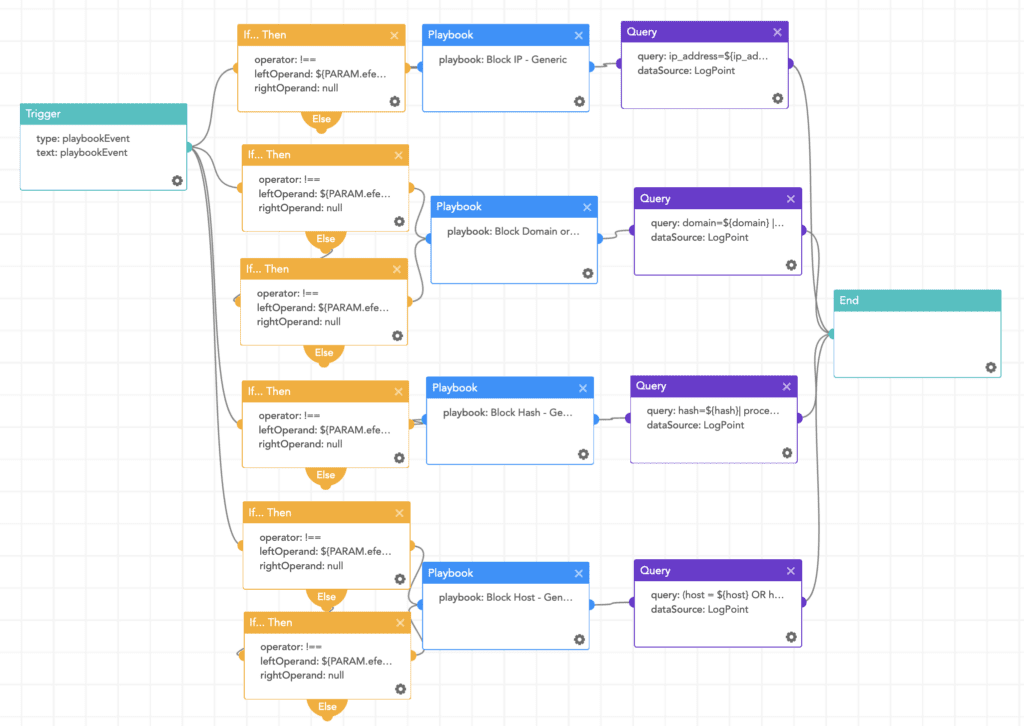
By utilizing AgentX - Malicious File Investigation and Containment playbook we can query files in threat intelligence sites to check the legitimacy of the file and provide an automatic response.
Besides using the Malicious File Investigation and Containment Playbook, analysts can utilize the Block Indicators - Generic playbook to block malicious IP addresses, domains, and files. This playbook can also be utilized to quarantine the infected host.
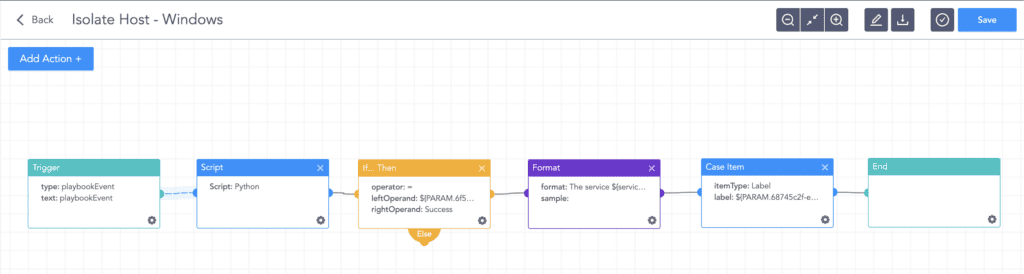
After verifying that a windows host has been infected, the Logpoint AgentX Isolate-Unisolate Host playbook can be utilized to isolate the host from the network.
Mitigation
As currently no patch is available, 3CX and we also recommended the customer uninstall the desktop application client for Windows and MacOS. The vendors have also urged the customer to use the web app instead.
Conclusion
After analyzing the distribution of trojanized versions of legitimate applications and the tactics, techniques, and procedures (TTP) utilized by threat actors, it is clear that this is not a noble technique. The SolarWinds and Kaseya incidents are a stark reminder of the potential damage that such attacks can cause. However, with the implementation of appropriate security solutions, early detection of threats is possible. It is essential to ensure that organizational online assets are continuously monitored to identify any signs of anomalous behavior. To this end, we have gathered information from various vendors and conducted our intelligence analysis, resulting in the development of detection rules for 3CX events and other stages of attacks. By implementing these rules, organizations can effectively mitigate the risk of such attacks and protect their systems from malicious actors.