by Sükrü ilkel Birakoglu, Senior Director
In all common programming languages, faults during development may lead to immense security vulnerabilities in production systems. ABAP/4,-(Advanced Business Application Programming/4th generation language) which is the programming language of SAP Applications is no exception to that. The steep rise in the number of SAP Security Notes in the past few years related to ABAP/4 Code Security shows the need for further action to check code security in SAP Applications.
Which dangers arise from security flaws in the ABAP/4 code?
The risks due to insecure programming can be classified into different areas. They describe the respective impact of security defects on compliance and the legal rights that are violated if insecure code finds its way into a production system. Insecure programming can lead to unauthorized execution of business logic, unauthorized read access to business and configuration data, unauthorized modification of business and configuration data, repudiation of business processes or identity theft.
Though SAP Systems have a built-in tool called SAP CVA (Code Vulnerability Analyzer) to detect security flaws in ABAP Codes, this tool is subject to separate licensing and is integrated into ABAP Test Cockpit. SAP CVA checks ABAP Security Flaws in code for which it is configured.
What vulnerabilities are ABAP/4 coded in your SAP system?
The complex nature of SAP Systems obligates development of in-house applications or enhancements in standard ABAP/4 Code delivered by SAP. As far as application security is concerned, the first important thing to understand is that the risk comes not only from specific transactions but also from special ABAP/4 commands in developed code.
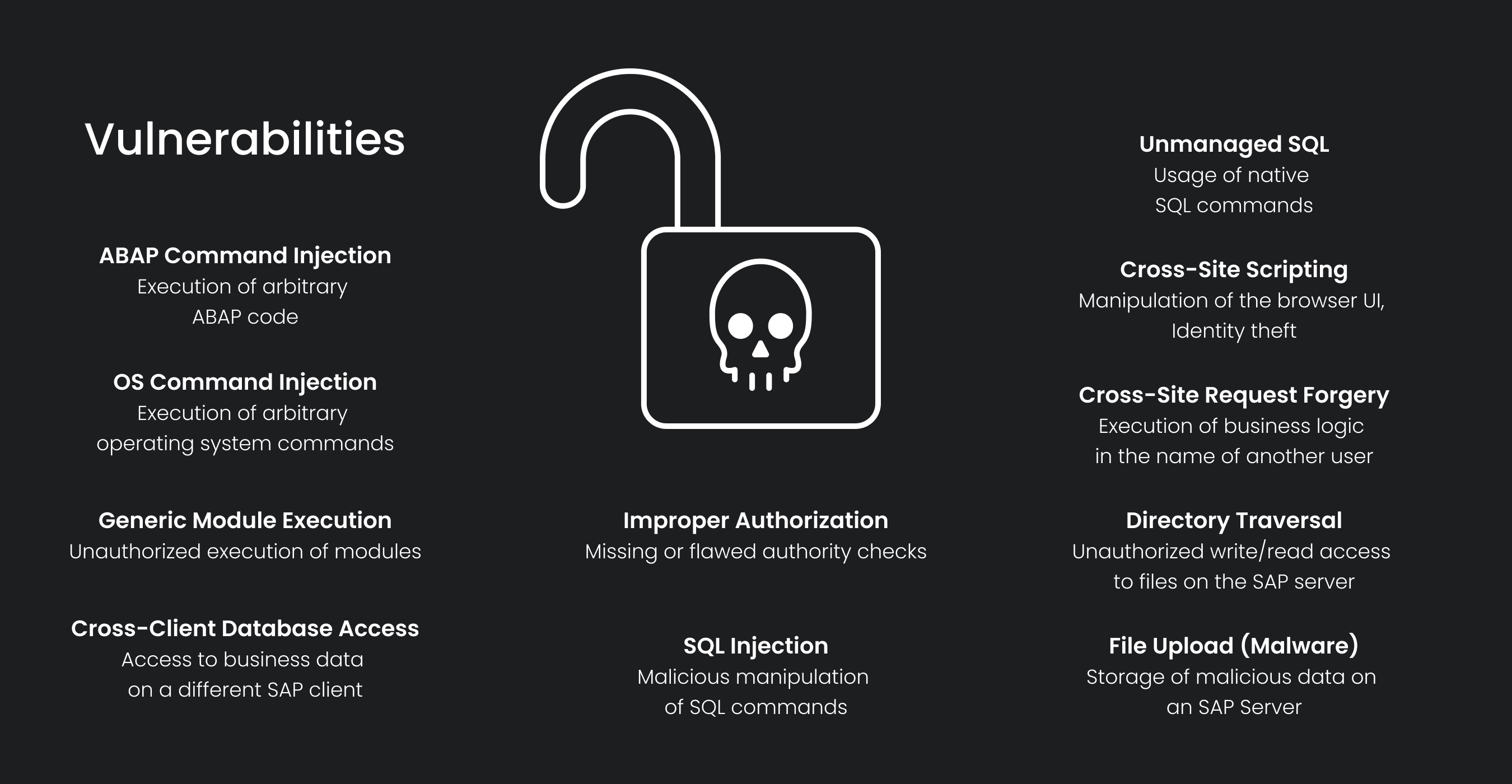
There are many different types of vulnerabilities that could arise from ABAP/4 code. The most obvious security problem in ABAP/4 code is presented by missing or technically faulty authorization checks. Since ABAP/4 has an explicit authorization concept, any program executing authorization-relevant actions must also explicitly check the appropriate authorization objects itself. If this check in the code is missing or faulty, the program will execute the action even though the user does not have the required authorization, and this will lead to security breaches in SAP Systems.
Another fundamental but less obvious problem is the injection vulnerabilities. Through them, malicious users can manipulate certain dynamically programmed ABAP/4 commands to make them behave in unexpected and unforeseen ways. This manipulation of dynamic ABAP/4 commands works even if correct authorization checks are performed. Very often, developers do not know which risks occur with the use of dynamic programming techniques and unintentionally open the door to hackers.
The most common ABAP/4 Security Issues and the corresponding risks connected with them
First off here are some samples of vulnerabilities and their descriptions in the table below.
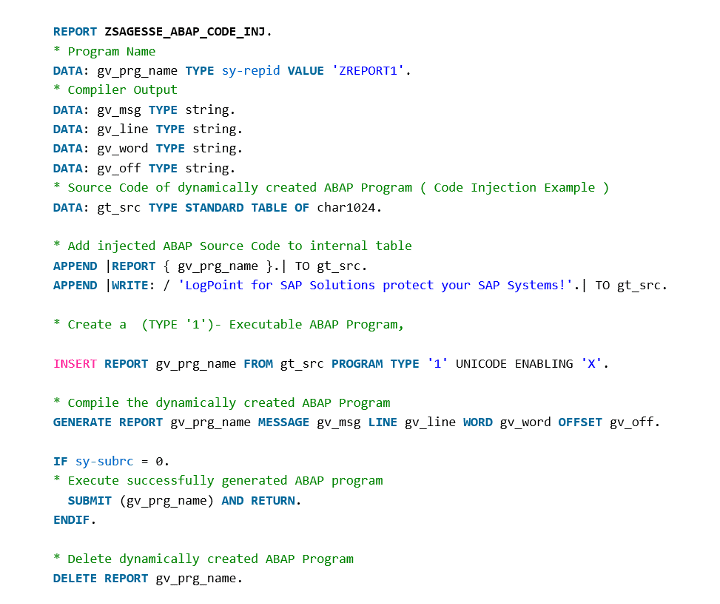
Let’s see in an example, how ABAP Command Injection would be applied in an SAP System using dynamic programming techniques.
If the code is examined, an ABAP/4 programmer can immediately see the dynamically generated code. The source code of dynamically generated program is built with commands below:
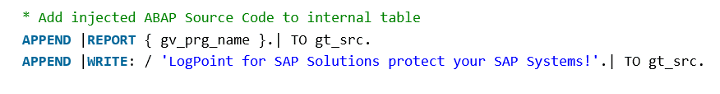
This code snippet is harmless and just prints the text ‘Logpoint for SAP Solutions protect your SAP Systems!’ on the screen (Note: Logpoint for SAP, is now BCS for SAP). An attacker, who can also be an internal employee, a software vendor or a contractor, can inject any arbitrary code instead of this harmless piece of code and execute this by bypassing any authorization checks and delete the generated code automatically like in the example program. It would not take 15 minutes for an average ABAP programmer to write dynamic ABAP/4 code to delete all customer master data, change financial journal entries or download HR related data like salary information of employees from system.
How you can leverage Logpoint BCS for SAP to keep your business-critical data in the right hands.
At Logpoint, we have our portfolio of SAP Security Monitoring Solutions (BCS for SAP) and ABAP/4 Code Security is also checked. If a transport request (a bundle of ABAP/4 Programs / Objects) is imported into a production system, our extractor installed on the SAP System executes the SAP Code Inspector and SAP CVA automatically and sends the results to our Logpoint SIEM Solution.
Displaying ABAP Security Flaws in our SIEM Solution is just one part of the solution we deliver. You can need more information about the risky code imported like how many times it has been executed and by whom, or if it has been executed by someone whose user behaviour is out of normal behaviour. Here our other SAP Log Extractors and our UEBA (User and Entity Behaviour Analytics) solution comes into play.
Let’s go one step further and think of a scenario wherby your SOC employee detects execution of a highly risky code in a production system, and they would like to lock the user(s) executing the code or create a ticket with very high priority for the SAP Basis Team in the IT Service Management Tool of company e.g., in ServiceNow. In these cases, our SOAR offering and its predefined playbooks for SAP related security incidents would handle the situation – no questions asked.
You can get more information about our SAP Security Monitoring Solutions on our website Here: Logpoint BCS for SAP
If you would like to discuss any of this further, then please contact us at the button.