A year on since the first attack on Ukrainian territory and the unofficial beginning of the cyber war, the Secretary of Ukraine’s National Security and Defense Council, Oleksiy Danilov, has issued a warning that Russia could conduct a large-scale cyberattack as part of its renewed aggression.
Danilov has stated that the Ukrainian government must be prepared to retaliate against such a potential attack. To date, Ukraine has fortified its cyber security system, increased its military’s technical equipment, and is prepared to defend against a renewed cyber attack by Russia.

Go To Section
A year on since the first attack on Ukrainian territory and the unofficial beginning of the cyber war, the Secretary of Ukraine's National Security and Defense Council, Oleksiy Danilov, has issued a warning that Russia could conduct a large-scale cyberattack as part of its renewed aggression.
Danilov has stated that the Ukrainian government must be prepared to retaliate against such a potential attack. To date, Ukraine has fortified its cyber security system, increased its military's technical equipment, and is prepared to defend against a renewed cyber attack by Russia.
What has happened?
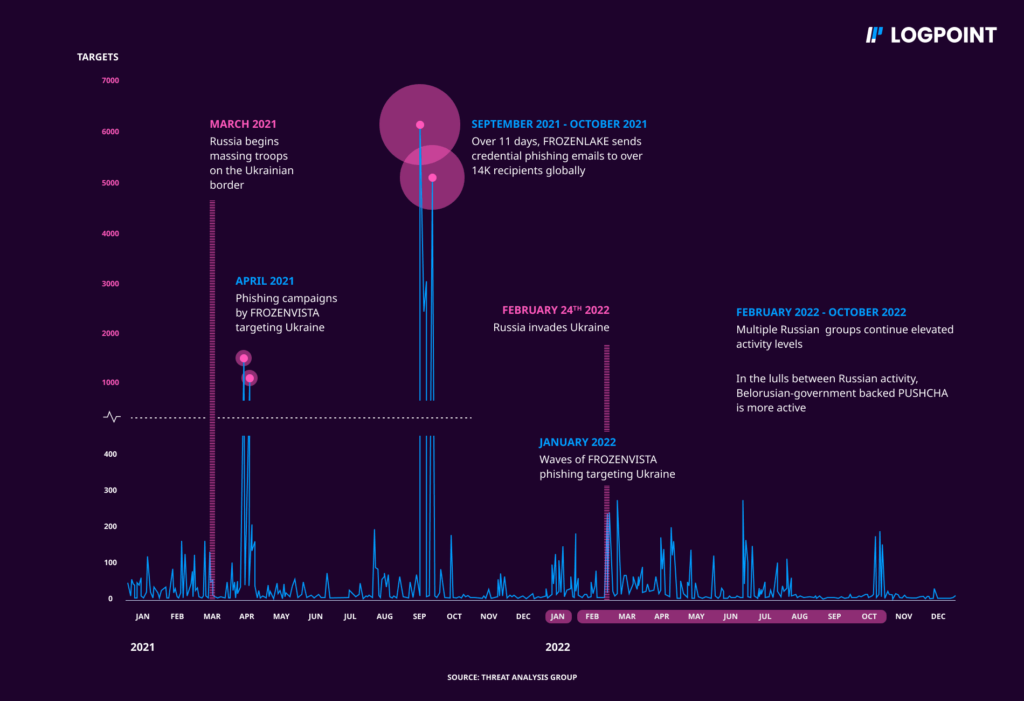
Over the last year, Russian cyberattacks on Ukraine have nearly tripled, targeting government databases, logistics, and military facilities. In addition, energy infrastructure has also been systematically attacked by Russia. Ukraine's Defense Minister, Oleksii Reznikov, has expressed concern that Russia may renew its offensive against Ukraine to coincide with the first anniversary of the all-out war.
These campaigns are suspected to be supported by the Russian government and have attempted to gain an advantage during wartime, using various tactics with varying degrees of success. The focus of several groups has shifted towards Ukraine resulting in increasingly destructive attacks on their government, military, and civilian infrastructure. Additionally, spear-phishing activity targeting NATO countries has risen, and there has been an increase in cyber operations designed to advance Russian objectives.
Approximately, from 2021 onwards Russian government-affiliated attackers intensified their cyber operations in preparation for the attacks. In 2022, these attackers increased their targeting of Ukrainian internet users by 250% compared to 2020, and targeting of NATO country users increased by over 300% in the same period. Ukraine was the most targeted country in 2022. While these attackers primarily focused on the Ukrainian government and military entities, they also targeted critical infrastructure, utilities, public services, and media and information outlets in campaigns that we disrupted. The situation is expected to get worse in round two.
Anticipating the anniversary
Ukrainian CERT has released reports stating UAC-0010, a Russian threat actor better known as Gamaredon, ACTINIUM, BlueAlpha, Trident Ursa, or Primitive Bear based on which naming convention to follow, has been actively renewing their attack efforts. According to the report released by the Ukrainian government, the Russian-sponsored hacker group is still actively attacking Ukrainian organizations and remains one of the "key cyber threats" to Ukraine's cyberspace. This is a cause for concern as the group has been operating for almost a decade and is known for its aggressive and persistent tactics. The Ukrainian government alleges that Gamaredon operates from Sevastopol, a city in the Russian-occupied Crimea, but follows the instructions of the FSB Center for Information Security in Moscow.
Gamaredon: Who are they?
The group began its operations in June 2013, a few months before Russia forcibly annexed the Crimean Peninsula from Ukraine. Since then, Gamaredon has carried out several cyberattacks against Ukraine, ranging from government services to critical infrastructure. The group's primary focus is on stealing sensitive information and disrupting Ukraine's operations. The government of Ukraine has identified the group as one of the primary cybersecurity threats to the country's sovereignty.
In recent years, Gamaredon has utilized various malware strains to execute its cyberattacks. The group has been observed using PowerShell info-stealer malware called GammaLoad and GammaSteel. These malware variants are custom-made information-stealing implants that can exfiltrate files of specific extensions, steal user credentials, and take screenshots of the victim's computer. The Ukrainian State Cyber Protection Centre has warned that the use of these malware strains has been on the rise in recent Gamaredon attacks against Ukraine.
The impact of these malware strains?
The use of these malware strains is particularly concerning as they are specifically designed to evade detection and exfiltrate sensitive information, including classified government data. Gamaredon's persistent and aggressive tactics suggest that the group is determined to continue its cyberattacks against Ukraine. However, the Ukrainian government has made efforts to protect itself from these attacks.
The State Cyber Protection Centre has launched several initiatives to combat cyber threats, and the Ukrainian government has prioritized improving its cybersecurity infrastructure and technical capabilities to counter these cyberattacks.
However, the use of these sophisticated malware strains highlights the importance of continued vigilance and effective measures to protect Ukraine's sovereignty and critical infrastructure.
Through this updated edition of the Russia-Ukraine war, we look deeper into its execution, techniques they have deployed, the variations, and how we can utilize the capabilities of Logpoint Converged SIEM to detect, prevent and respond to attacks from Gamaredon and their new “Gamma“ edition of malware TTPS.