By Nischal Khadgi, Swachchhanda Shrawan Poudel, and Anish Bogati – (Security Research Team)
Fast Facts
-
With over 500 million users worldwide, WinRAR is the world’s most popular compression tool!
-
CVE-2023-38831, named ‘RARLAB WinRAR Code Execution Vulnerability is an arbitrary code execution vulnerability on WinRAR, with a CVSS score of 7.8
-
CVE-2023-38831 vulnerability has been patched in the latest version of WinRAR and the vulnerability resides on versions prior to 6.23.
-
Threat Actors have been targeting this vulnerability to deliver malware such as Agent Tesla, GuLoader, Remcos, and Darkme.

Go To Section
Background
WinRAR, with its user-friendly design and broad accessibility, portrays simplicity and class in the world of compression software and it's rare to find someone in the digital world who hasn't used WinRAR. Consequently, Threat actors dedicate their efforts to identifying vulnerabilities in widely used programs like WinRAR.
On August 23, 2023, the National Institute of Standards and Technology (NIST) disclosed a high-severity Arbitrary Code Execution vulnerability in WinRAR, CVE-2023-38831 having a CVSS score of 7.8. Group IB initially identified this zero-day vulnerability during their research on the DarkMe malware spread on July 10, 2023. MITRE Corporation officially designated it on August 15, 2023. This vulnerability is present on WinRAR versions prior to 6.23.
Vulnerability Details
The first step in the infection chain involves the attacker crafting a ZIP archive comprising both malicious and benign files." Attackers can conceal the activation of malicious code within an archive masquerading file formats such as ".jpg", ".txt", ".pdf" or any other file format and craft a weaponized archive.
This vulnerability is exploited when WinRAR is used to extract a ZIP archive containing both a benign file and a folder sharing the same name as the benign file. When attempting to access the benign file, WinRAR inadvertently executes the file present within the folder. Threat actors can exploit this vulnerability by including malicious files inside a folder with the same name as a benign file. As a result, when the user, accesses the benign file, the malicious file gets executed leading to code execution.
Technical Analysis
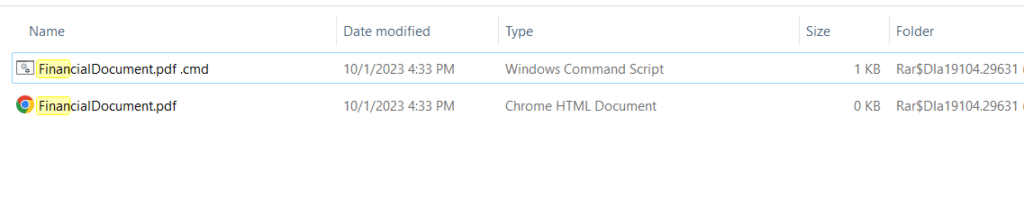
For our analysis, we have taken a benign pdf file with the name FinancialDocument.pdf and a folder with the same name as the benign file for example, ‘FinancialDocument.pdf’.
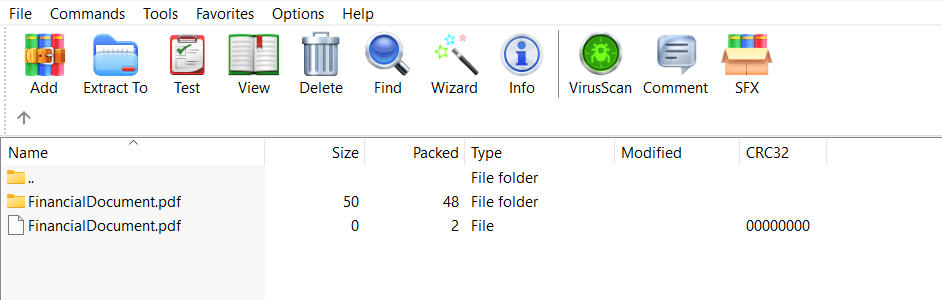
The folder with the same name as the benign file comprises a file named FinancialDocument.pdf.cmd which is masqueraded as pdf file format.
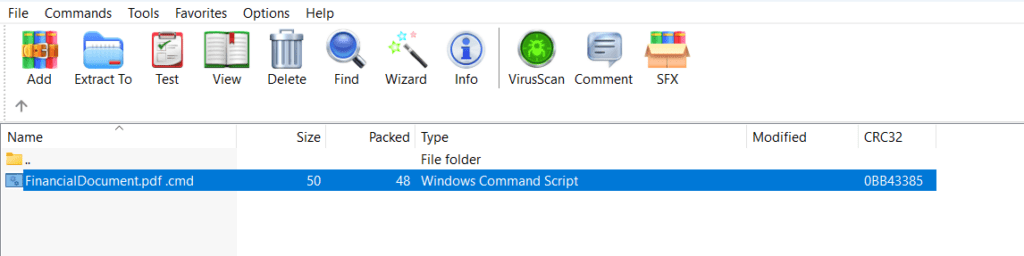
The batch file “FinancialDocument.pdf.cmd” contains a simple script when executed it first prints "Hello" in the Command Prompt, then opens PowerShell and it prints "Exploit Successful" within the PowerShell environment. The pause command is included so that the Command Prompt window remains open after executing the script.
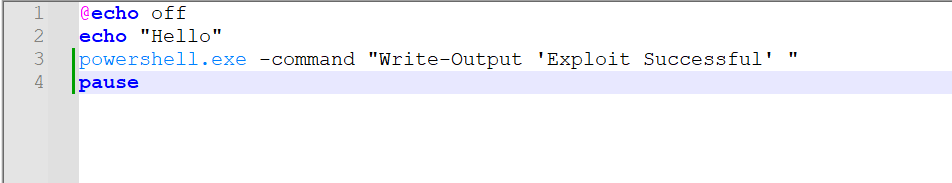
When this weaponized archive is delivered to the victim, they typically find a benign file and a folder with an identical name to the benign file. When the victim opens the benign file, it triggers the execution of a batch file present inside the folder instead.
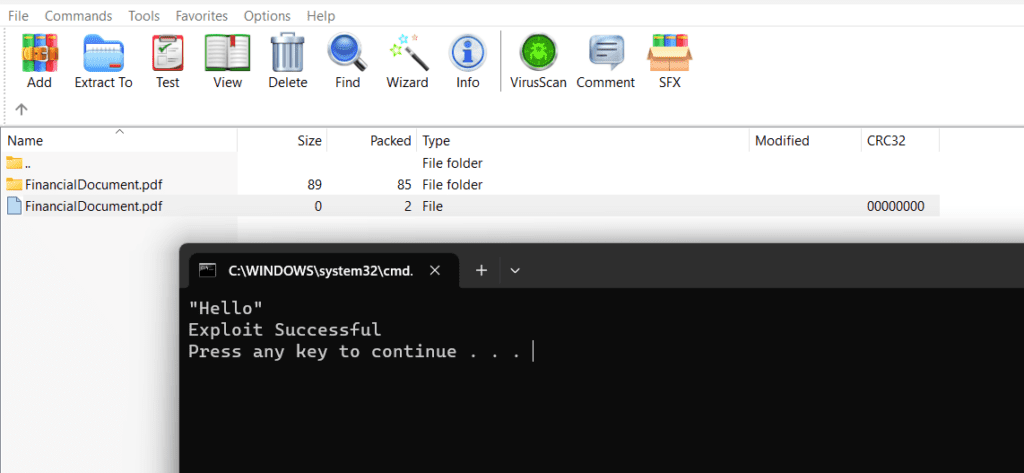
When extracting files using WinRAR, it requires a temporary location to store the extracted files before moving them to the intended destination folder. To accomplish this, WinRAR utilizes the %TEMP% or %RARTMPDIR% folders, which point to the system's designated temporary folder. When a legitimate ZIP file is extracted, only the intended files are created. However, in the case of a weaponized ZIP archive, the contents of a folder with the same name as the legitimate file are also extracted.
 Recent trends on CVE-2023-38831
Recent trends on CVE-2023-38831
The proof of concept (POC) for CVE-2023-38831 has been available for some time now, and threat actors are actively exploiting it in current campaigns. According to Group IB's report, threat actors behind a specific campaign targeted traders by posting malicious ZIP archives on public forums popular among traders for discussion and information sharing. These archives, which were typically attached to forum posts (as shown in Figure 1), contained malicious content. The malicious ZIP files were distributed in some cases via catbox.moe, highlighting the varied tactics employed by the attackers to disseminate their malicious payloads.
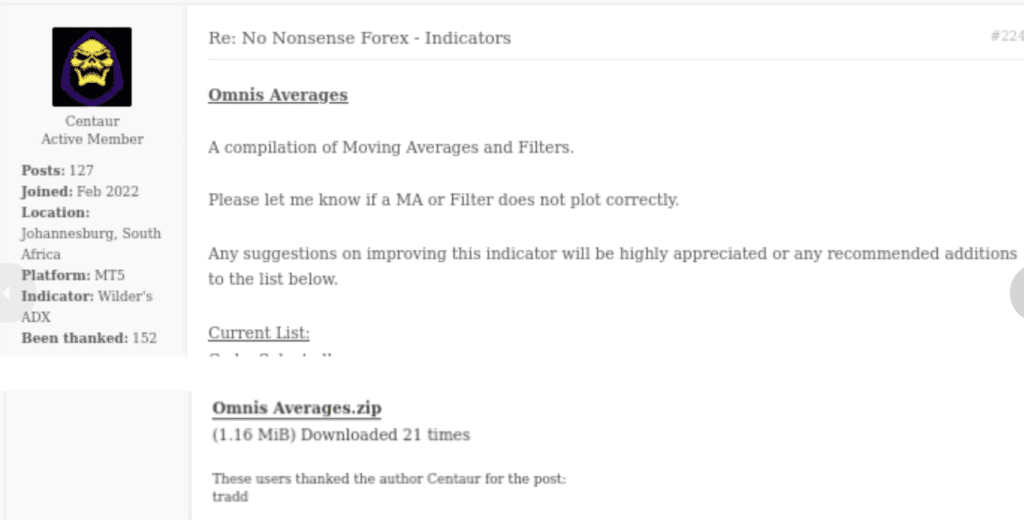
Example of Post made by Threat Actor, Group-IB
DarkMe Malware
In some cases, threat actors are exploiting the mentioned vulnerability to distribute the DarkMe Malware. Initially, the script mentioned earlier triggers the Cabinet Self-extractor file. This type of archive file, often referred to as an SFX CAB file, automatically extracts its contents upon execution. Within this archive are 5 files, with the 'cc.exe' file being the primary entry point. Once extracted, this file is launched.
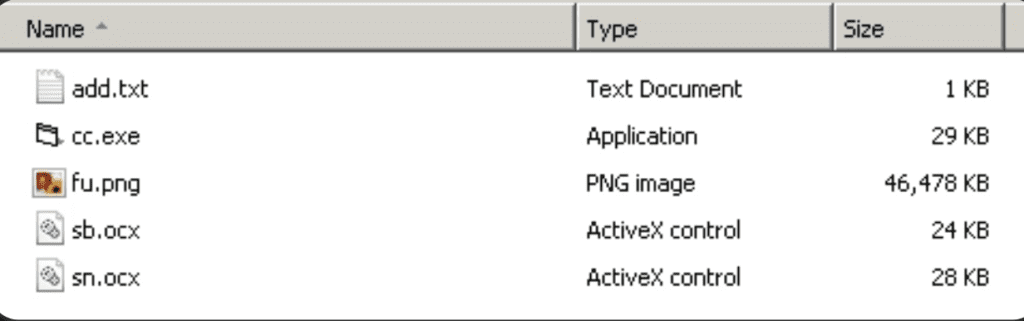
Agent Tesla
Threat actors have also been discovered exploiting CVE-2023-38831 to distribute the Agent Tesla malware. A CMD file was disguised as a PDF file within a folder that had the same name. After clicking on this file, the Agent Tesla malware within the folder gets executed.
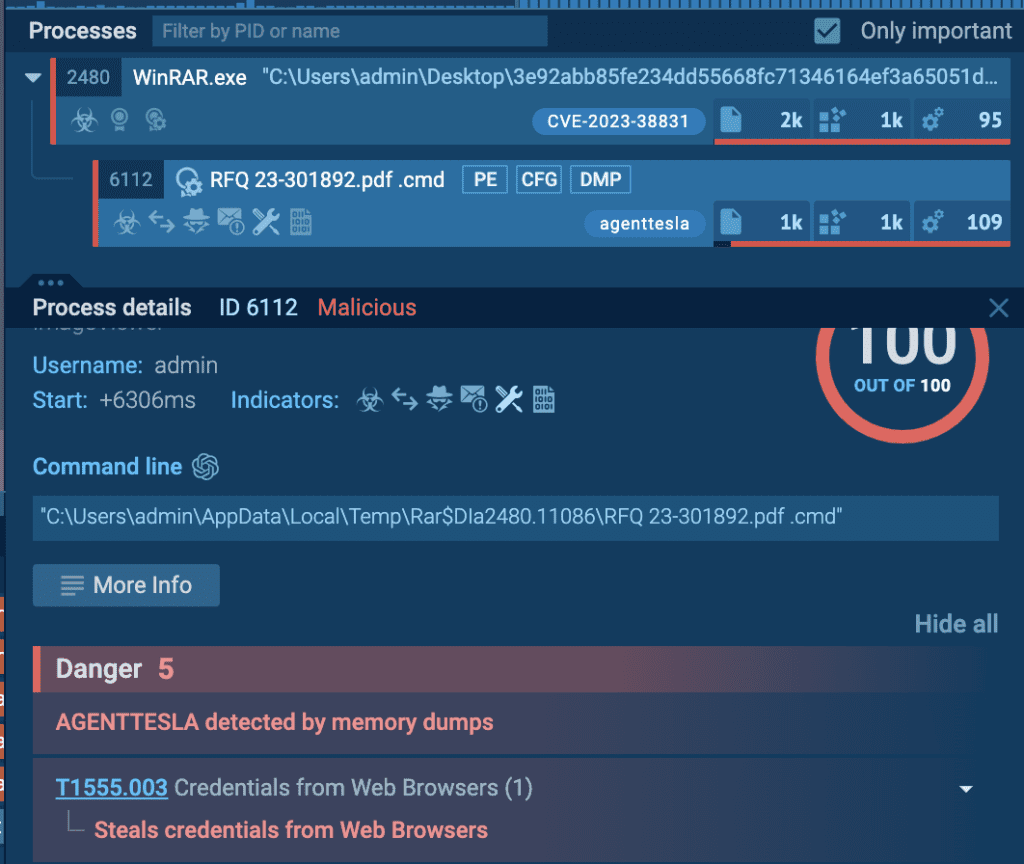
Detection
When it comes to strengthening your organization's security, dedicating sufficient time to patching is essential. Actively searching for indicators of attack and detecting any signs of exploitation attempts or intrusion is crucial. Logpoint Converged SIEM, coupled with the provided queries, will be a valuable asset in your arsenal, aiding in the vital task of detecting and mitigating vulnerability exploitations.
Required Log Sources
- Windows
- Process Creation with command-line auditing should be enabled - Windows Sysmon
Detection with Logpoint Converged SIEM
1. Possible Exploitation of CVE-2023-38331
As aforementioned, the creation of a double file extension by WinRAR is the peculiar character of this vulnerability.We can look for the creation of a file with a double extension and a space by WinRAR which could be a sign of exploitation of CVE-2023-38331.

2. Suspicious WinRAR Child Process
It is uncommon and suspicious for file compressor tools like WinRAR to spawn Windows command shells such as cmd, PowerShell, etc. as child processes. After successfully exploiting the vulnerability, the malicious payload may spawn these processes to execute arbitrary code like to download their second stage. We can look for suspicious child processes spawned by WinRAR.exe.
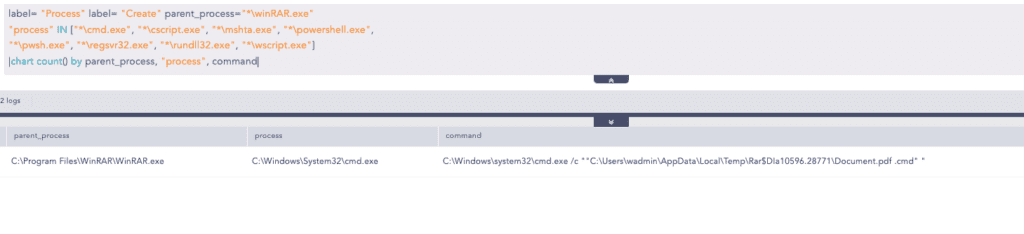
This is one of the techniques for initial access to the victim machines. Since people are still using the unpatched version of WinRar, Threat actors may trick the victim into downloading the crafted zip and possibly exploit the vulnerability. Once initial access is achieved, the actions of threat actors can vary significantly, depending on their objectives.
Here at Logpoint, we remain committed to creating new reports, and detection rules uncovering new cyber trends and emerging threats. We encourage you to also consult our Emerging Threat Report and blog posts to better understand potential Tactics, Techniques, and Procedures (TTPs) that may be employed by threat actors.
Recommendations and Best Practices
-
This vulnerability affects the winRAR version prior to 6.23. It is recommended to update WinRAR to the latest version. Regularly updating your software application, browsers, and devices is a crucial security practice that can help protect your systems from known vulnerabilities and cyber threats.
-
Always be cautious of any message that requests you to click a link or open an attachment.
-
Configure email security technologies such as SPF, DKIM, and DMARC to authenticate and verify the origin of incoming emails.
-
Conduct simulated attack scenarios to make sure that the employees are well aware of phishing and other risks, and also to make sure that they report the incident to the internal cybersecurity team.
-
The principle of least privilege involves restricting user access and permissions to only what is necessary for them to perform their job functions. Limiting user access can also prevent potential damage that can be caused by compromised user accounts.
-
Perform network segmentation to keep important systems and sensitive data apart from the rest of the network. This helps to confine possible breaches and minimize attacker lateral movement.
-
Regularly auditing privileged accounts and their activities is crucial because these accounts have elevated access and permissions that can potentially give malicious actors unauthorized access to sensitive data or critical systems. Without proper monitoring, privileged accounts may be misused, leading to data breaches, system failures, and other security incidents that can cause significant harm to an organization. Additionally, auditing privilege accounts can provide valuable insights into how these accounts are being used, allowing organizations to make informed decisions about access control, resource allocation, and risk management.
-
Having proper logging, visibility of assets, and monitoring of systems are essential components of a robust cybersecurity strategy. These measures provide an overview of the network and help to detect anomalies that may indicate a security threat.
-
Stay updated on new trends employed by attackers as this awareness is essential for recognizing potential risks.
-
Host-level security solutions like AgentX can help detect and prevent malware infections, including stealer malware. These solutions can provide an additional layer of protection to your devices, by monitoring the activity of processes and services running on your device and alerting you to any suspicious or malicious activity.
Conclusion
The vulnerability CVE-2023-38831 poses a significant threat, especially considering the widespread use of WinRAR. Adversaries can exploit this vulnerability for malicious purposes, making early detection even more crucial. Detecting and acting upon these attacks in their early stages can help minimize potential damage. Logpoint Converged SIEM offers a solution by providing early detection and mitigation capabilities. Our platform consolidates SIEM, SOAR, UEBA, and a native endpoint agent (AgentX) for rapid TDIR (Threat Detection, Investigation, and Response).
Logpoint Converged SIEM is a powerful platform that assists analysts in detecting and responding to security issues. It offers pre-defined alert rules encompassing Tactics, Techniques, and Procedures (TTPs) and detects unusual user behavior, enabling quick analysis. Logpoint SOAR orchestrates all software, hardware, and alerts from many sources and systems and speeds up the TDIR by automating the investigation and response to the incident. UEBA detects insider abnormal behavior to uncover insider threats. AgentX, the native endpoint agent, ensures real-time monitoring and responses, such as isolating compromised endpoints.
In combination with SIEM and SOAR, AgentX brings EDR capabilities to Converged SIEM. Such a security operations platform enables enterprises to detect and respond to various attacks quickly with out-of-the-box alerts, threat intelligence, and orchestration and automation actions that streamline manual processes and respond to and remediate incidents.
If you enjoyed this article and would like to check out more from our research team, you can read our latest Emerging Threats report on Akira. Simply click the link below.







