by Bhabesh Raj Rai, Associate Security Analytics Engineer
On July 19, 2021, security researcher Lionel Gilles released technical details and a PoC tool for a vulnerability named PetitPotam. The vulnerability allows a domain user to coerce a domain controller to authenticate against a remote server using the Microsoft encrypting file system remote protocol (MS-EFSRPC) interface revealing its authentication hash in the process.
What makes the flaw very dangerous is that attackers can chain it with a relay vulnerability in the Active Directory Certificate Services (AD CS) server recently discovered by Specterops researchers. Effectively, adversaries can relay the obtained hash of an entity to an AD CS server and obtain that entity’s certificate. Using that certificate, adversaries can impersonate that entity and effectively request the ticket-granting-ticket (TGT) on their behalf. In essence, adversaries can fully compromise the domain through the AD CS server without any authentication.
Like any other relay attack, adversaries must have their machine in the same LAN segment or have elevated privileges in the domain. AD CS servers with either Certificate Authority Web Enrollment or Certificate Enrollment Web Service enabled are vulnerable.
Microsoft has released guidance on mitigating PetitPotam, and they classify the vulnerability as a classic NTLM relay attack. Microsoft recommends that administrators enable Extended Protection for Authentication (EPA) and disable HTTP on AD CS servers. Apart from this, Microsoft has also outlined additional mitigations like disabling NTLM authentication where possible and enforcing SMB signing. System administrators should keep in mind that disabling MS-EFSRPC does not mitigate the vulnerability.
Detecting the PetitPotam attack chain in LogPoint
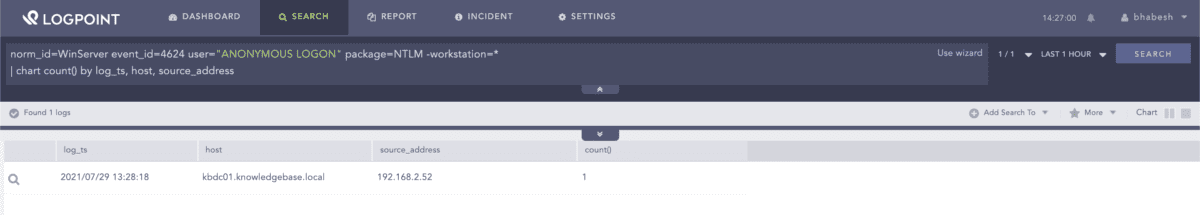
PetitPotam does not require any authentication, which means we can look for anonymous NTLM logins to servers, especially domain controllers. We have found that adversaries using their machine for the attack generate Event ID 4624 with a null workstation field which we can use to filter out false positives.
norm_id=WinServer event_id=4624 user="ANONYMOUS LOGON" package=NTLM
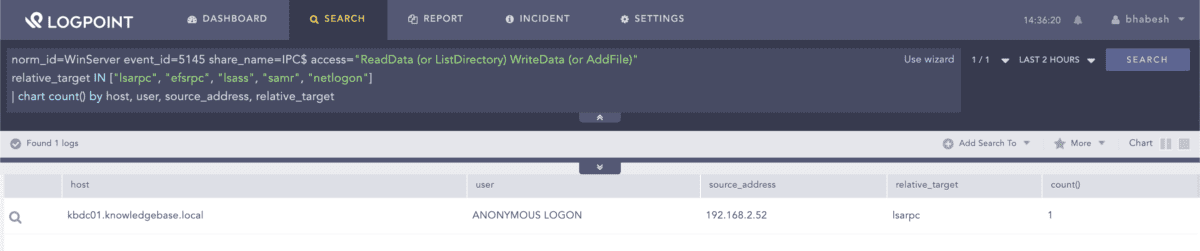
We can also hunt for PetitPotam artifacts in file share auditing event logs. Administrators should verify that they have enabled detailed file share auditing for the query to work.
norm_id=WinServer event_id=5145 share_name=IPC$ access="ReadData (or ListDirectory) WriteData (or AddFile)" relative_target IN ["lsarpc", "efsrpc", "lsass", "samr", "netlogon"] | chart count() by host, user, source_address, relative_target
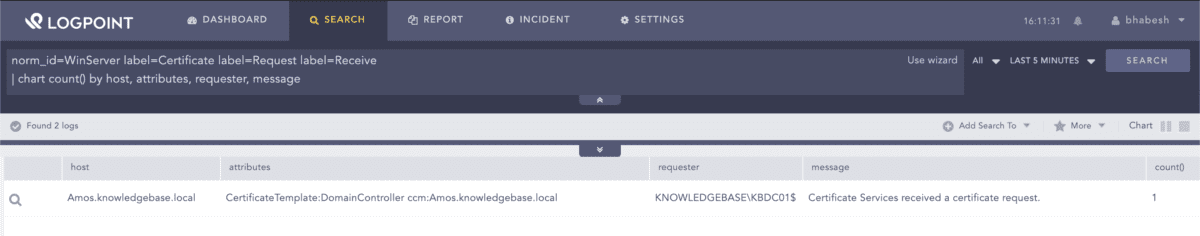
To help in correlation, administrators can look for certificate request events generated by the AD CS server and zoom in on certificate requests by domain controllers around the timeframe of PetitPotam artifacts. Administrators should enable “Issue and manage certificate requests” auditing in the AD CS server to generate the corresponding logs because the auditing is disabled by default.
norm_id=WinServer label=Certificate label=Request label=Receive | chart count() by host, attributes, requester, message
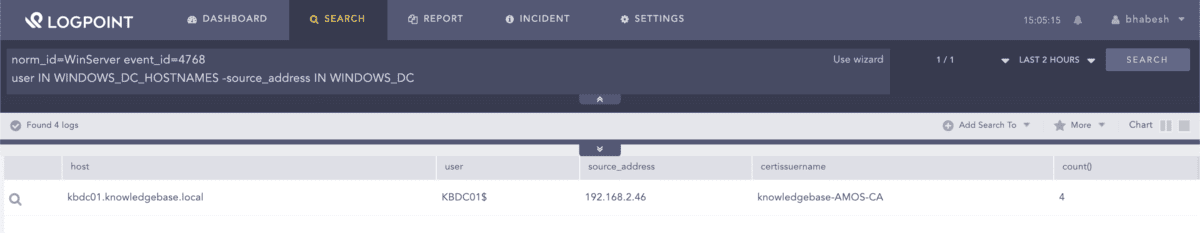
At last, adversaries will fetch a TGT from a domain controller using the previously obtained certificate and cache the ticket in memory. To catch this, we need to look for TGT request events where the domain controller is a user (as the certificate belongs to the domain controller), but the source address field has the IP address of the adversary-controlled machine. In everyday use, the domain controller machine account will always request a TGT from its own machine, and thus the source address field should always be its own IP address.
norm_id=WinServer event_id=4768 user IN WINDOWS_DC_HOSTNAMES -source_address IN WINDOWS_DC
WINDOWS_DC_HOSTNAMES is a list that contains the username of all domain controller accounts like DC01, DC02, and so on, while WINDOWS_DC includes the IP addresses of all domain controllers.
Deploy the mitigations as soon as possible
In conclusion, system administrators should promptly follow the mitigations provided by Microsoft if they have deployed AD CS servers in their environment. If admins postpone the deployment of mitigations to a later date due to various circumstances, they should place necessary detections to catch exploitation attempts. Since complete domain compromise is possible without any authentication, the flaw will likely seduce threat actors of all, which Microsoft will not fix.