The EU is often looked too as a global cybersecurity leader. And NIS2, a new EU policy in development, is just the latest in a series of steps to protect critical infrastructure and EU citizens from the risk of cyberattacks.
All EU member states are expected to comply with NIS2 by 2024. This means following specific cybersecurity strategies, establishing competent authorities, and implementing incident reporting mechanisms. NIS2 also requires EU member states to cooperate in the sharing of information to safeguard vital assets from cyberattacks.
Below we take a closer look at the EU’s updated directive and what it means for EU cybersecurity.
Go To Section
How has the EU managed cybersecurity to date?
The European Union Agency for Network and Information Security, or ENISA, was founded in 2004 to improve EU cybersecurity. Then, in 2016, the EU passed the NIS Directive, setting out guidelines for EU member states on how to improve their cybersecurity.
The NIS Directive has since been revised and replaced by the NIS2 Directive.
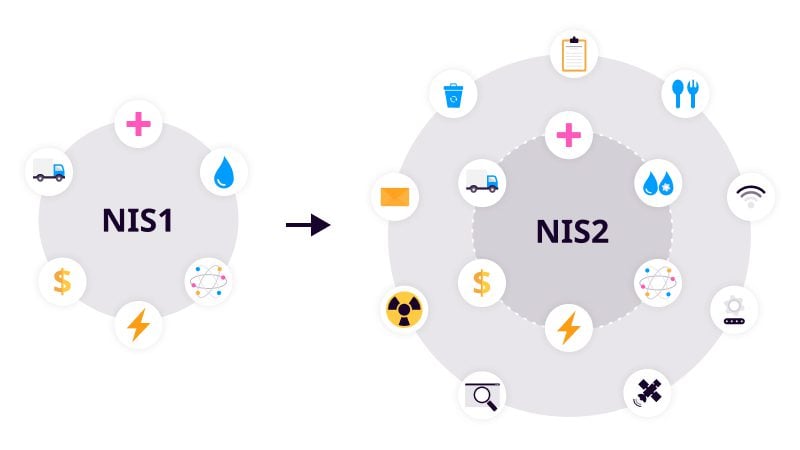
Image: How NIS2 has grown its coverage
What is NIS2?
NIS2 builds on the requirements of the original directive; it still aims to protect critical infrastructure and organizations within the EU from cyber threats and achieve a high level of common security across the EU.
To achieve this goal, NIS2 requires member states to take a number of additional measures, including:
- Establishing an incident response plan that coordinates with other member state plans
- Establishing a national Computer Emergency Response Team
- Strengthening cooperation between public and private sector entities
- Improving information sharing between member states
By working with member states to help them improve their defenses against cyberattacks, and by providing support and guidance to businesses and individuals, the EU is making sure that its citizens are protected from the growing risk of online threats.
Sectors that NIS2 will impact
The original NIS directive was brought in to protect:
- Healthcare
- Digital infrastructure
- Transport
- Water supply
- Digital service providers
- Banking and financial market infrastructure
- Energy
Additionally, the NIS2 directive now includes amongst many others:
- Providers of public electronic communications networks or services
- Wastewater and waste management
- Manufacturing of certain critical products (for example, pharmaceuticals, medical devices, and chemicals)
- Food
- Digital services such as social networking platforms and data center services
- Space and aerospace
- Postal and courier services
- Public administration
Image: Amongst other sectors NIS2 covers.
How NIS2 will change EU cybersecurity: The 4 main objectives
As mentioned previously, there will be increased cyber resilience across essential service providers. The scope of service providers that must comply with the NIS2 directive is greater than the scope of the original NIS directive, so by expanding the scope of the directive, the EU is making sure that all essential service providers are protected from cyber threats.
Strengthened security standards and penalties to streamline resilience
The original NIS directive permitted organizations to tailor their adherence to cybersecurity requirements. This flexibility ultimately led to vulnerabilities, as some organizations did not take the required measures to protect themselves from cyber threats.
NIS2 strengthens the security requirements and introduces penalties for organizations that do not comply with the directive.
Logpoint’s SAP Security and Compliance solution provides a comprehensive visualization of a business’s end-to-end security operations, enabling organizations to detect and respond to cyber threats in real time. It’s a NIS2-compliant tool to increase cybersecurity standards for every user and better protect business-critical systems.
Enhanced capacity to anticipate and respond to cyber attacks
By improving coordination and communication between member states, the EU will be better equipped to respond to cyberattacks. The EU has recognized that cybersecurity is a collective effort and by working together, EU and member state authorities can improve their defenses against cyber threats.
An EU-wide incident response plan
NIS2 also calls for compulsory incident reporting. Under the original NIS directive, organizations were only required to report incidents that had a significant impact on their operations. This meant that some organizations failed to report incidents — choosing not to admit that they had been impacted by an attack.
Under NIS2, all organizations must report any incidents that occur, regardless of whether or not they have a significant impact on their operations. This ensures that all incidents are tracked and monitored and that authorities can identify and respond to any potential threats.
The EU is committed to improving cybersecurity, and NIS2 is just one part of that effort. To find out what your business requires, visit the EU NIS2 website or contact a cybersecurity agency with experience in European Union regulations, like Logpoint.
Fines for NIS2 what can you expect for non-compliance
-
Consequences of Non-compliance:
- Non-financial: Orders to comply, direct instructions, security audit mandates, and risk alerts to clients.
- Financial: Fines differentiated for:
- Essential Entities (EE): Up to €10 million or 2% of annual global revenue, targeting sectors like transportation, finance, healthcare, etc.
- Important Entities (IE): Up to €7 million or 1.4% of annual global revenue, targeting industries like food production, digital services, chemicals, etc.
-
Management Accountability:
- NIS2 introduces provisions holding senior management accountable for major negligence during cyber incidents.
- Consequences include public disclosure of compliance violations, public announcements detailing those responsible, and potential temporary managerial bans for recurring violations in essential entities.
- Aim: Ensure management's dedication and responsibility in managing cybersecurity risks.
For more information on how non-compliance can impact your business, you can download the document below.







