Security in the Service and Hospitality Industry
The threat of cyber-crime is becoming an increasing issue for many organizations and businesses. This includes the service and hospitality industry, as new advances in computing systems have emerged, such as cloud computing, social media, and big data.
Hospitality Cybersecurity
Ensuring your guests’ security is a standard practice in accommodation services, but the focus has traditionally been around physical property. Guests rely on hotels to keep themselves and their possessions safe during their stays. When they leave valuable items in their rooms, they just put the lock on their doors or use the room safe – but what about hospitality cybersecurity?
Change of Focus
Guests may mistakenly assume the same level of security in the hospitality industry for physical property extends to the digital assets that reside on their laptops and smartphones when they use hotel Wi-Fi connections. Hotels need to be certain they are delivering a consistent level of security to guests and their possessions, whether they are physical or digital, putting hotel cybersecurity in focus.
At Risk on Several Levels
Accommodation services need to think about multiple endpoints and the remote connections they rely on to run operations. Electronic door locks, HVAC controls, alarms and a full range of Internet of Things (IoT) devices can fall under the control of cybercriminals aiming to disrupt normal operations.
The risk of hotels becoming a victim to cyber-crime is even higher, as most of the people in accommodation services who deal with computer systems (e.g., front office managers and accountants) are not IT experts and have only some familiarity with computer systems, making improvements to hospitality cybersecurity a necessity.
Threats to the Hospitality Industry
Ensuring Network Security
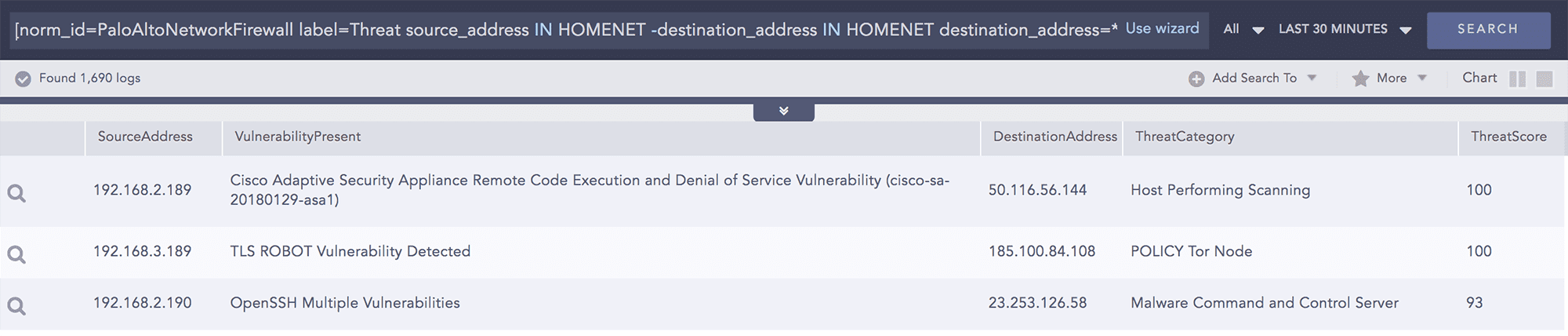
Logpoint integrates with a wide range of network and firewall devices. The data from these devices can be normalized, aggregated, enriched, and correlated to ensure security inside the network. Furthermore, Threat Intelligence feeds can be used to enrich the log data to understand if the network is being targeted by an external attacker. Logpoint can check various activities such as allowed and denied connections, usage of data and applications, connection to threat sources, or any other suspicious activities.
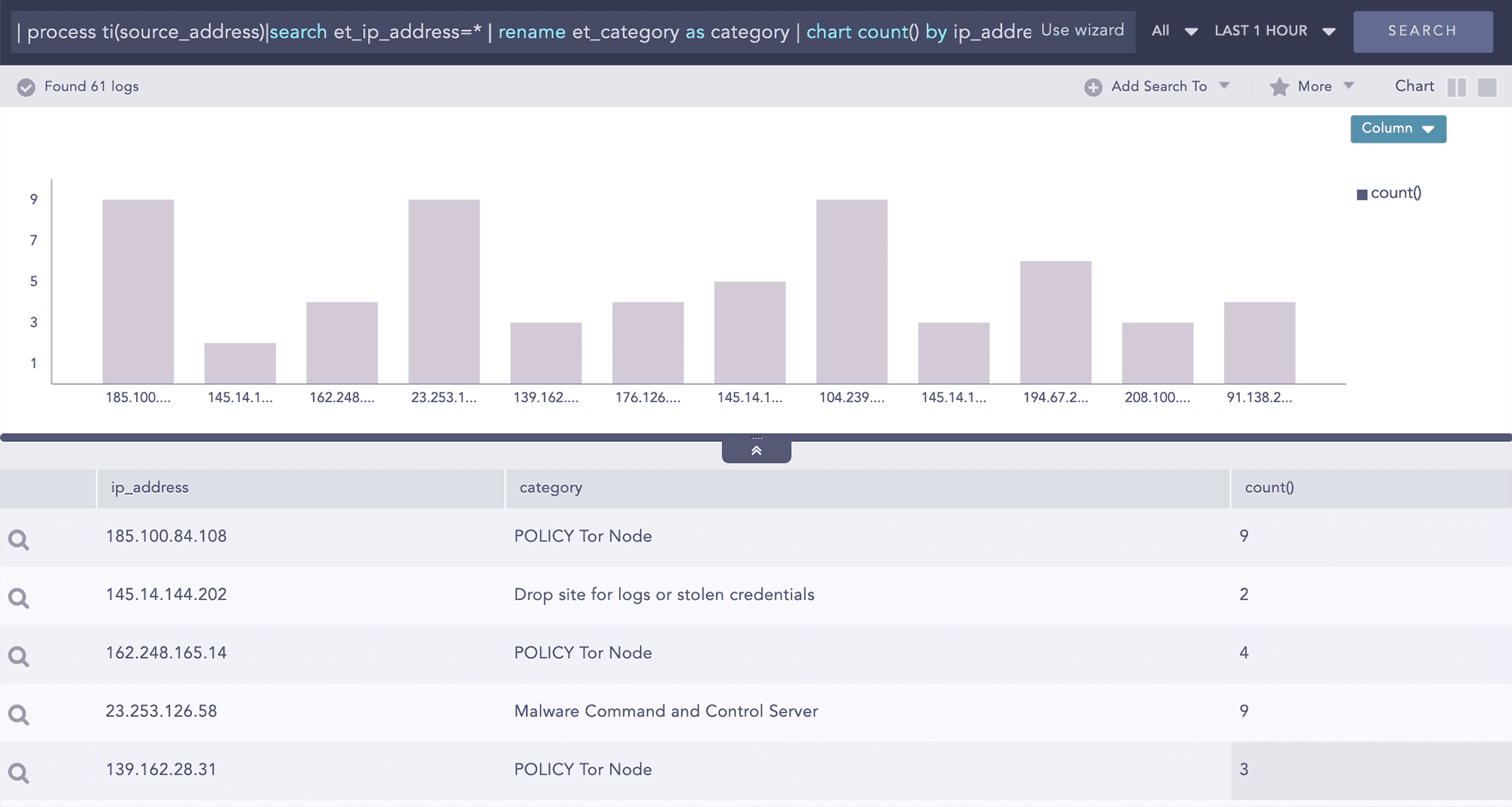
Identifying Threat Indicators While Working with Large Volumes of Logs
Analysts can use queries with generic commands for threat intelligence to filter out only critical threat indicators. In Logpoint, filtering can be generic, giving you all matches to the threat intelligence database or based on a certain threat category or threat score. With this approach, we enable your analysts to simplify the investigation process and focus on the actual threat.