Die Top 10 SIEM-Use-Cases für Ihre Implementierung
LogPoint ist eine Lösung für das Security Information and Event Management (SIEM), die die Logdaten der gesamten IT-Infrastruktur sammelt, speichert und analysiert, um verdächtige Aktivitäten erkennen und auf Bedrohungen reagieren zu können. Obwohl SIEM-Tools in erster Linie der Unternehmenssicherheit dienen, gibt es dennoch eine Reihe weiterer Use-Cases, die jedes Unternehmen kennen sollte, wie beispielsweise automatisiertes Compliance-Management, die Überwachung der operativen Leistung oder das Logdaten-Management.
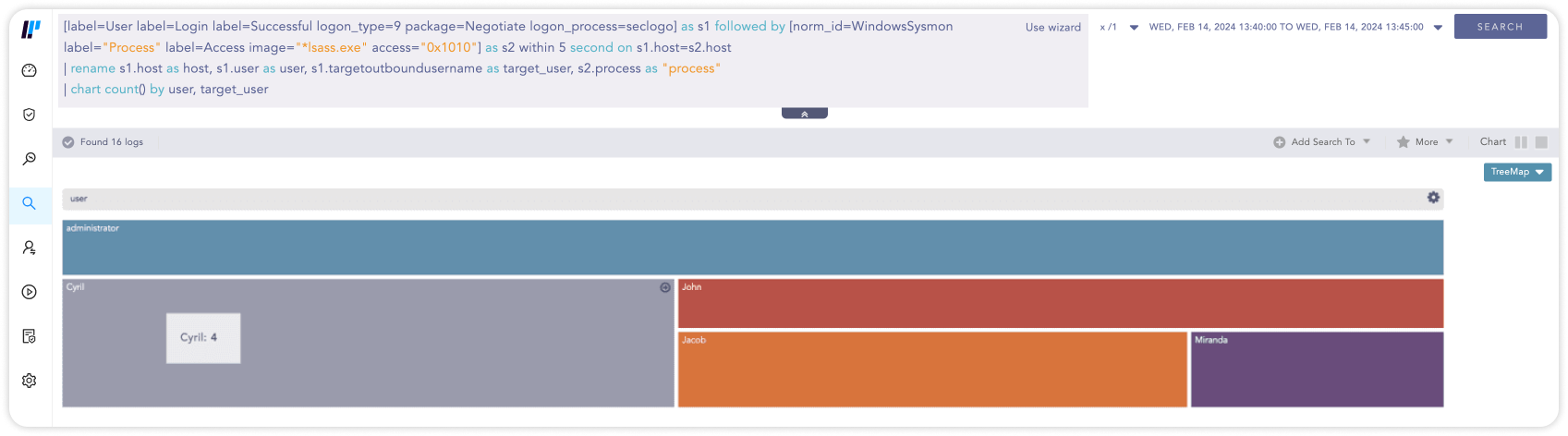
01Erkennung von kompromittierten Benutzer-Anmeldedaten
Stellen Sie sicher, dass ein Anwendungsfall und ein Arbeitsablauf vorhanden sind, um alle Versuche zu erkennen, die Anmeldedaten von Benutzern durch Brute Force, Pass the Hash, Golden Ticket oder andere Methoden zu kompromittieren. Im Falle einer erfolgreichen Kompromittierung ist es wichtig, die betroffenen Benutzer und Einrichtungen zu identifizieren, um die Auswirkungen zu untersuchen und weiteren Schaden zu verhindern.
[label=User label=Login label=Successful logon_type=9 package=Negotiate logon_process=seclogo] as s1 followed by [norm_id=WindowsSysmon label="Process" label=Access image="*\lsass.exe" access="0x1010"] as s2 within 5 second on s1.host=s2.host
| rename s1.host as host, s1.user as user, s1.targetoutboundusername as target_user, s2.process as "process"
| chart count() by user, target_user
02Nachverfolgung von Systemänderungen
Legen Sie geeignete Regeln für die Kennzeichnung kritischer Events fest, beispielsweise unbefugte Änderungen an Konfigurationen oder die Löschung von Audit-Trails. Diese Änderungen sollten sofort eskaliert werden, um Schaden abzuwenden und weitere Risiken zu minimieren, da beispielsweise die Manipulation von Audit-Protokollen immer ein Warnsignal ist.
label=Log label=Clear
| chart count() by log_ts, host, user, target_channel03 Erkennung von ungewöhnlichem Verhalten bei privilegierten Konten
Privilegierte Benutzer, wie beispielsweise System- oder Datenbank-Administratoren, haben erweiterte Zugriffsrechte. Dies macht sie zu einem attraktiven Ziel für Hacker. Mit einer SIEM-Lösung können Analysten alle Aktionen dieser privilegierten Benutzer genau im Auge behalten und nach ungewöhnlichem Verhalten suchen, das auf eine Bedrohung oder eine Kompromittierung hinweisen könnte.
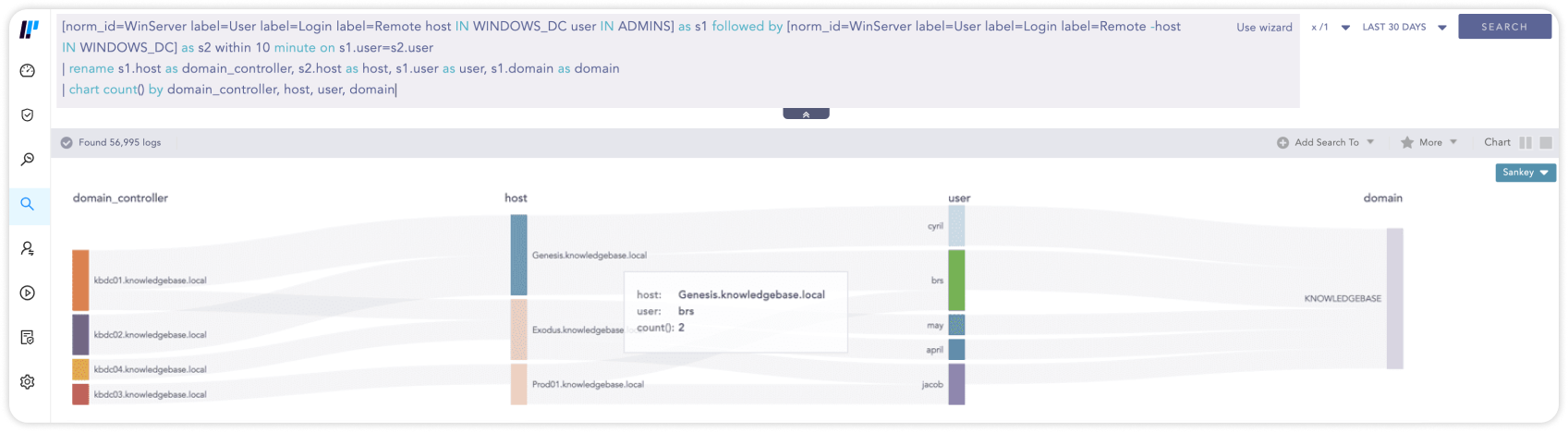
RDP-Anmeldung an einem Domain-Controller, gefolgt von einer RDP-Anmeldung an einer anderen Workstation
[norm_id=WinServer label=User label=Login label=Remote host IN WINDOWS_DC user IN ADMINS] as s1 followed by [norm_id=WinServer label=User label=Login label=Remote -host IN WINDOWS_DC] as s2 within 10 minute on s1.user=s2.user
| rename s1.host as domain_controller, s2.host as host, s1.user as user, s1.domain as domain
| chart count() by domain_controller, host, user, domain04Sicherheit für cloudbasierte Anwendungen
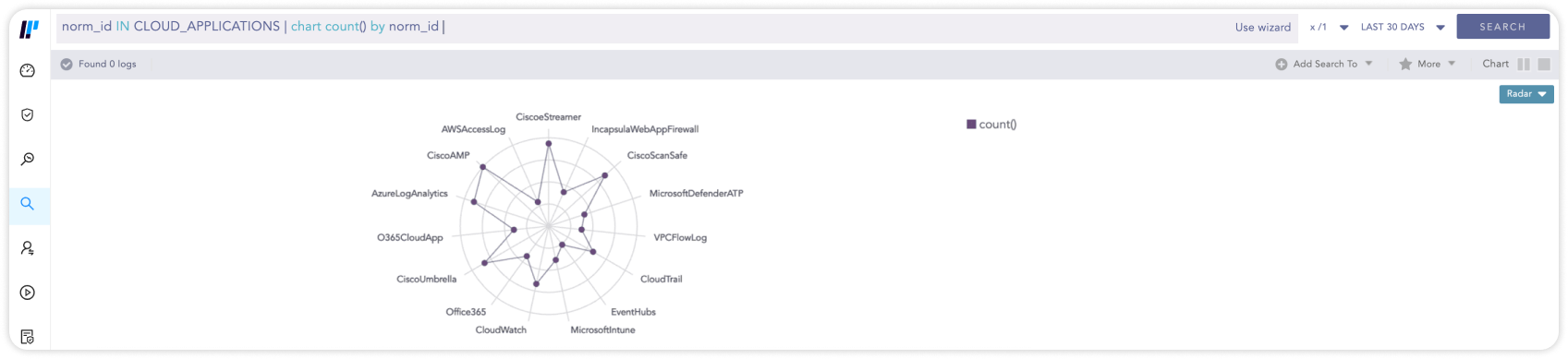
Cloud Computing bietet zahlreiche Vorteile, bringt jedoch auch einige Herausforderungen mit sich: die Erfüllung neuer Compliance-Anforderungen, die Verbesserung der Benutzer-Überwachung sowie der Zugriffskontrolle, oder die Prävention möglicher Malware-Infektionen und Datenschutz-Verletzungen. Eine SIEM-Lösung sollte auch cloudbasierte Anwendungen als Logdaten-Quellen unterstützen, beispielsweise Salesforce, Office365 oder AWS, um die Compliance-Überwachung sowie die Erkennung von Bedrohungen auf die Cloud-Umgebung ausdehnen zu können.
norm_id IN CLOUD_APPLICATIONS | chart count() by norm_id05Erkennung von Phishing-Angriffen
Phishing ist ein Versuch, an sensible Informationen zu gelangen, die für Identitätsbetrug und Identitätsmissbrauch verwendet werden. Dazu gehören Versuche, an persönliche Daten wie Sozialversicherungsnummern, Bankverbindungen, PIN-Codes oder Passwörter zu gelangen. Unternehmen müssen unter allen Umständen sicherstellen, dass diese vertraulichen Informationen in der gesamten Organisation geschützt sind. Phishing, insbesondere Spear-Phishing, wird häufig eingesetzt, um sich einen ersten Zugang zu einem Netzwerk zu verschaffen.
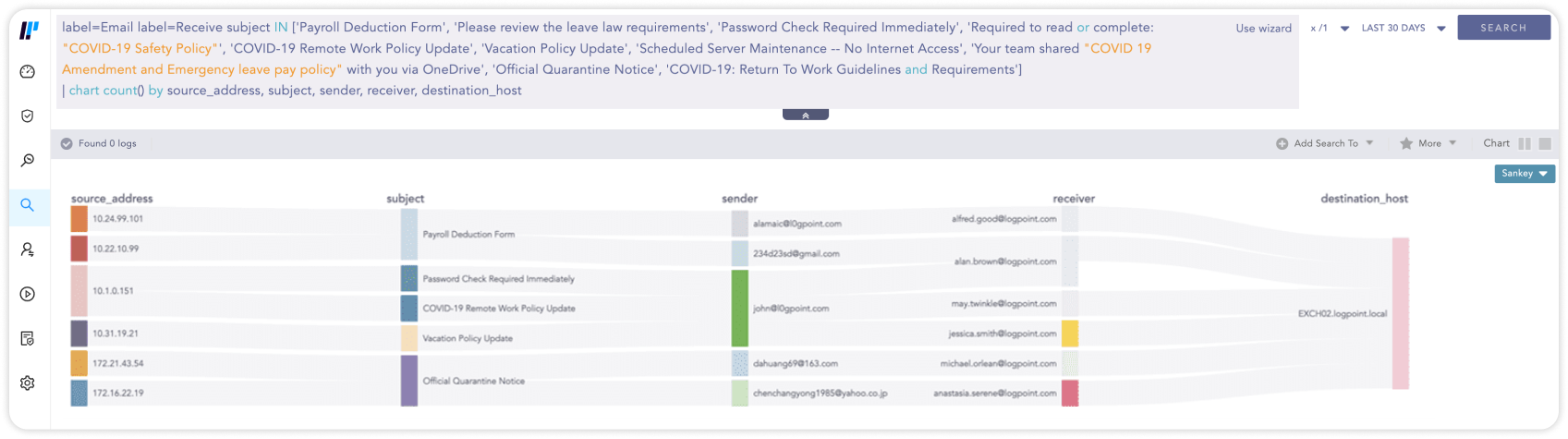
Bei Erhalt von Phishing-E-Mails können Analysten mithilfe von SIEM nachverfolgen, wer diese empfangen, auf darin enthaltene Links geklickt oder auf die E-Mails geantwortet hat, sodass sie sofort Maßnahmen ergreifen können, um den Schaden zu minimieren.
Die Suche nach den am häufigsten angeklickten, allgemeinen E-Mail-Betreffzeilen:
label=Email label=Receive subject IN ['Payroll Deduction Form', 'Please review the leave law requirements', 'Password Check Required Immediately', 'Required to read or complete: "COVID-19 Safety Policy"', 'COVID-19 Remote Work Policy Update', 'Vacation Policy Update', 'Scheduled Server Maintenance -- No Internet Access', 'Your team shared "COVID 19 Amendment and Emergency leave pay policy" with you via OneDrive', 'Official Quarantine Notice', 'COVID-19: Return To Work Guidelines and Requirements']
| chart count() by source_address, subject, sender, receiver, destination_host06Überwachung der Auslastung und der Verfügbarkeit
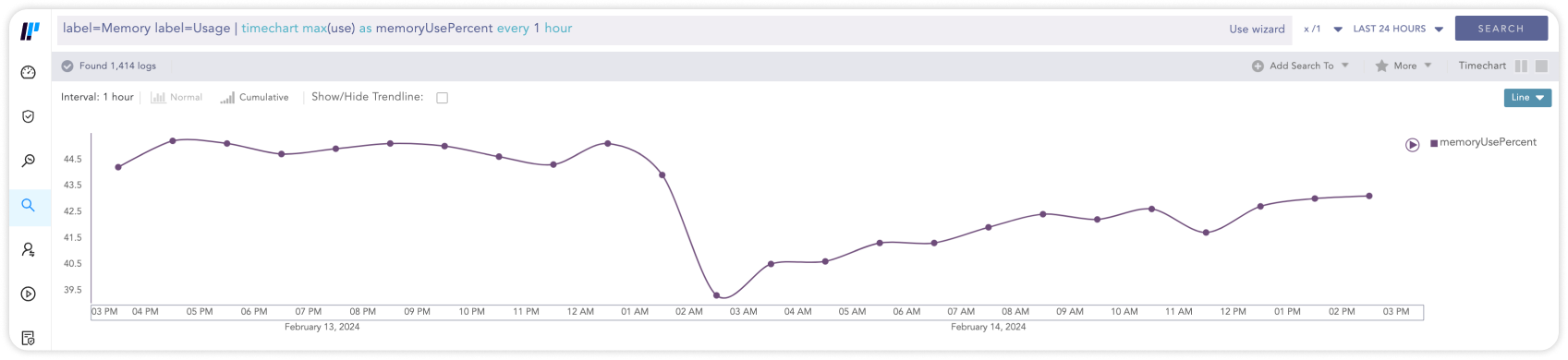
Mit einem SIEM-System, den passenden Korrelationsregeln sowie Warnmeldungen, ist es möglich, die Auslastung, die Verfügbarkeit sowie die Reaktionszeiten verschiedener Server und Dienste kontinuierlich zu überwachen. Störungen und Überlastungen lassen sich so frühzeitig erkennen, Stillstandzeiten sowie die damit verbundenen Kosten vermeiden.
label=Memory label=Usage | timechart max(use) as memoryUsePercent every 1 hour07Logdaten-Management
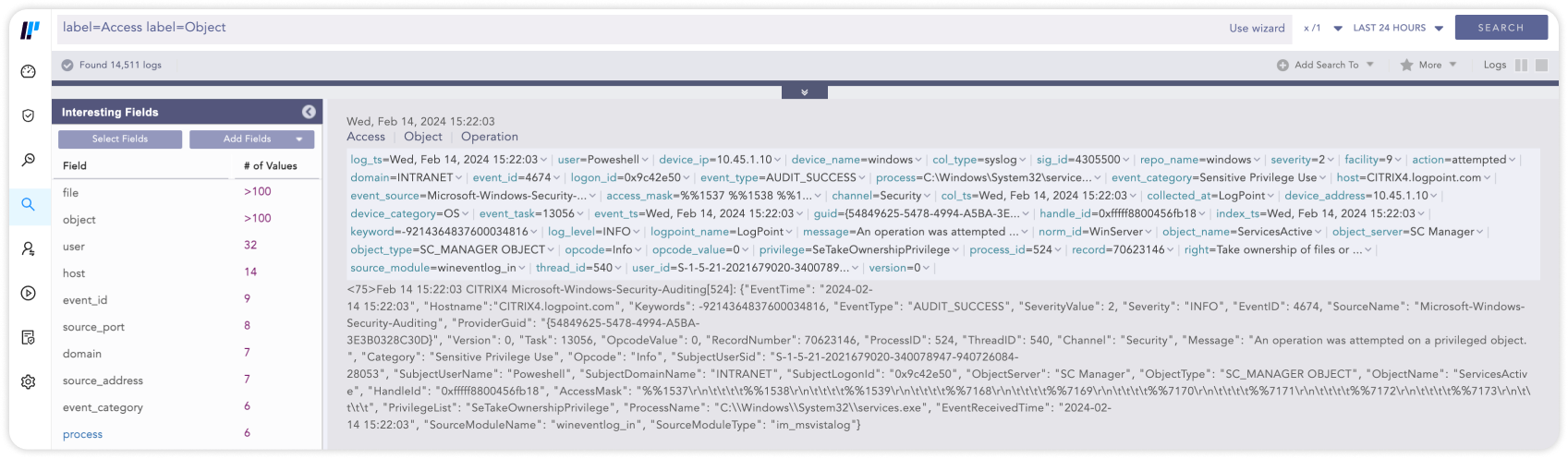
Datenbanken, Anwendungen, Benutzer und Server erzeugen große Mengen an Logdaten. Ein SIEM-Tool kann die Sammlung von Logdaten normalisieren und zentralisieren. Dies ermöglicht eine reibungslose Analyse und Korrelation der sicherheitsrelevanten Ereignisse, und erlaubt es dem IT-Security-Team, die Daten nach bestimmten Schlüsselwörtern oder Werten zu durchsuchen.
label=Access label=Object08SIEM für die GDPR-, HIPAA- oder PCI-Compliance
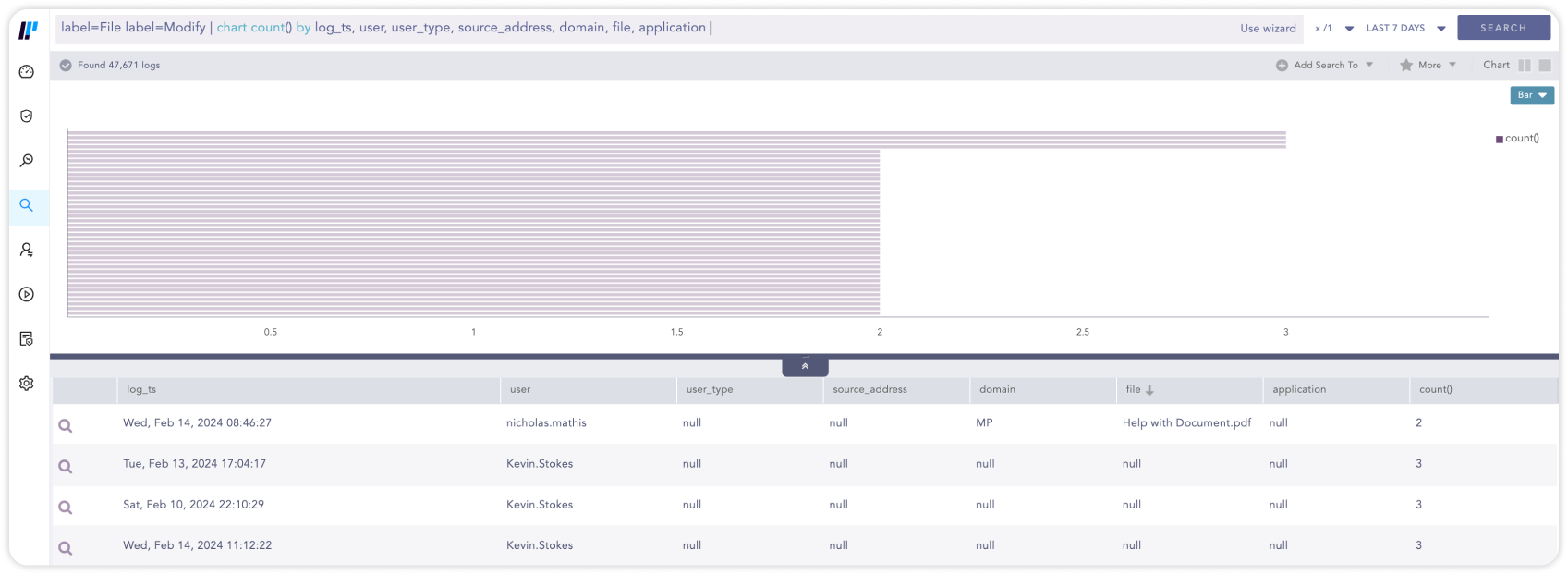
Unternehmen unterliegen einer Vielzahl von Compliance-Vorschriften, beispielsweise GDPR, HIPAA oder PCI. Mit einem SIEM-System können Sie dokumentieren, wann und von wem auf welche Daten zugegriffen wurde, diese gelesen oder kopiert wurden, um die Compliance-Anforderungen zu erfüllen und Verstöße zu verhindern.
label=File label=Modify | chart count() by log_ts, user, user_type, source_address, domain, file, application09Die Suche nach Bedrohungen
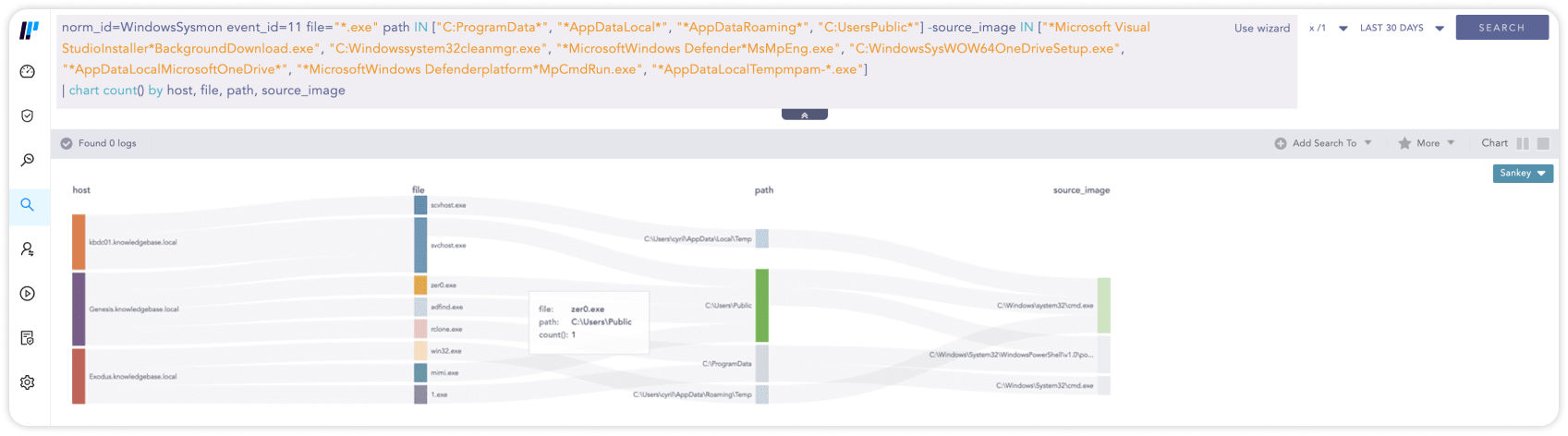
Der Prozess der aktiven Suche nach Cyberrisiken in einem Unternehmen oder Netzwerk wird als „Threat Hunting“ bezeichnet. Diese Suche nach Bedrohungen kann als Reaktion auf ein Sicherheitsproblem oder zur Erkennung neuer und unbekannter Angriffe oder Sicherheitsverletzungen ausgeführt werden. „Threat Hunting“ erfordert den Zugriff auf Sicherheitsinformationen aus allen Bereichen eines Unternehmens. Eine SIEM-Lösung kann diese bereitstellen.
Die Suche nach File-Droppings (EXE-Dateien) an verdächtigen Stellen:
norm_id=WindowsSysmon event_id=11 file="*.exe" path IN ["C:\ProgramData*", "*\AppData\Local\*", "*\AppData\Roaming\*", "C:\Users\Public*"] -source_image IN ["*\Microsoft Visual Studio\Installer\*\BackgroundDownload.exe", "C:\Windows\system32\cleanmgr.exe", "*\Microsoft\Windows Defender\*\MsMpEng.exe", "C:\Windows\SysWOW64\OneDriveSetup.exe", "*\AppData\Local\Microsoft\OneDrive\*", "*\Microsoft\Windows Defender\platform\*\MpCmdRun.exe", "*\AppData\Local\Temp\mpam-*.exe"]
| chart count() by host, file, path, source_image10SIEM für die Automatisierung
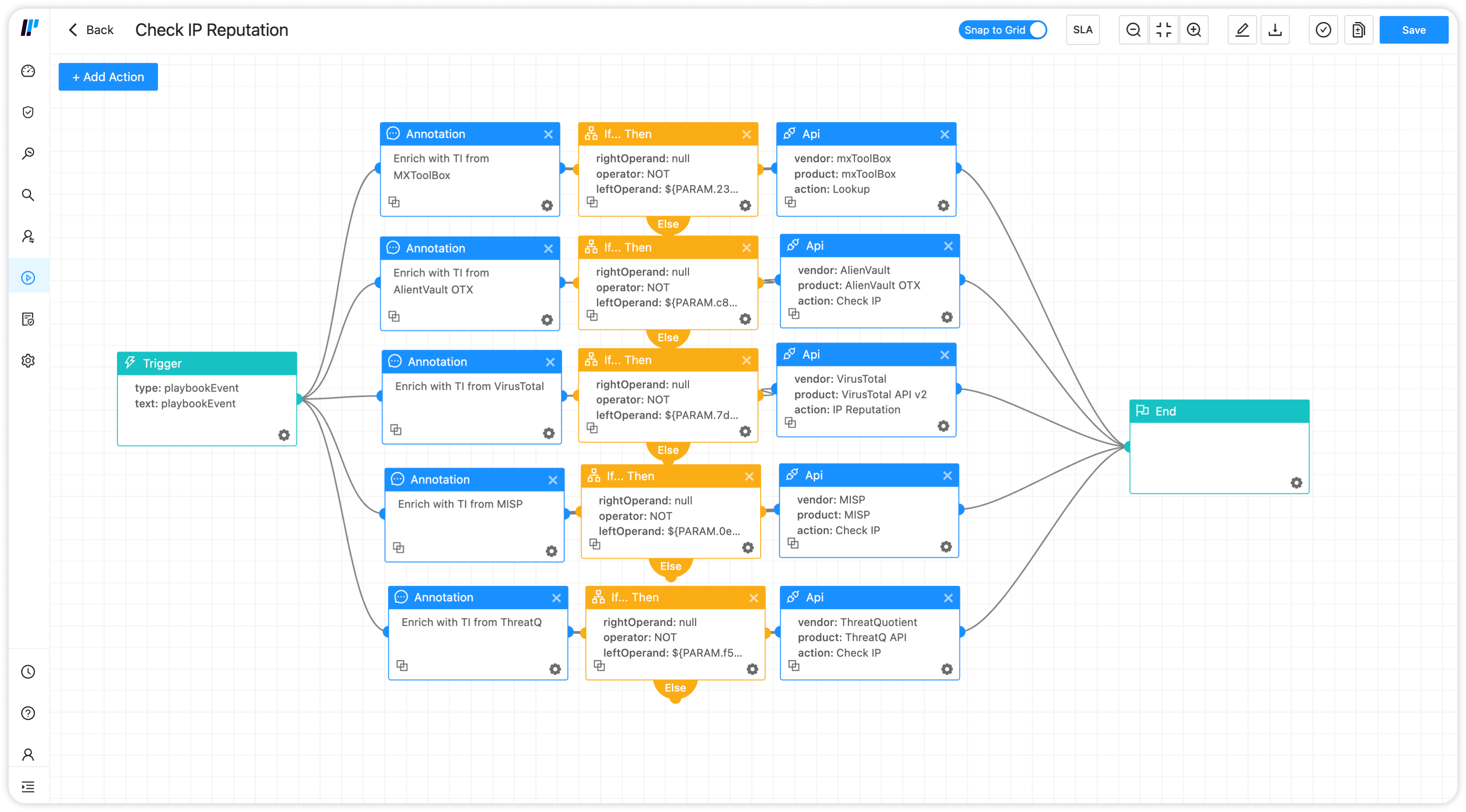
Eine SIEM-Lösung automatisiert die Aktivitäten zur Erkennung von Bedrohungen und bildet die Grundlage für eine automatisierte Reaktion auf sicherheitsrelevante Vorfälle. Die Weiterleitung von Sicherheitswarnungen und Security-Events an LogPoint SOAR ermöglicht eine noch schnellere Reaktion auf sicherheitsrelevante Vorfälle, da manuelle Aufgaben automatisiert werden. Dies steigert nicht nur die Produktivität des SOCs, sondern senkt auch die Kosten. Nutzen Sie jetzt LogPoint SOAR für einen Analysten kostenfrei als Teil Ihrer SIEM-Lizenz.
Playbook in Logpoint SOAR
Überzeugen Sie sich von den Vorteilen der LogPoint-Lösung für SIEM,
UEBA und SOAR
Falls Sie mehr über die Vorteile unserer Lösung für SIEM, UEBA und SOAR sowie die verschiedenen Download-Optionen erfahren möchten, vereinbaren Sie bitte einen persönlichen Demo-Termin.