In May 2019, Patch Tuesday – Microsoft addresses 79 vulnerabilities with 22 labeled as Critical. Out of the 22 Critical vulnerabilities, 18 relates to scripting engines and browsers while 4 are Remote Code Execution in Remote Desktop, Word, GDI+, and DHCP Server.
What is a Remote Code Execution Vulnerability?
Remote code execution allows attackers to access and make change on other’s computing devices regardless of the devices’ geo location.
When exploiting a Remote Code Execution Vulnerability, cyber criminals typically execute some type of malicious code allowing them to seize control of the targeted system, thus all privileges of the user. Once they succeed, they can move higher and higher up by increasing their privileges. To avoid this, users are advised to patch the holes/vulnerabilities on a regular basis preventing any cyber criminals to gain control. The purpose of Microsoft’s patch Tuesday is to address these vulnerabilities by releasing fixes on a monthly basis.
Remote Code Execution Vulnerability
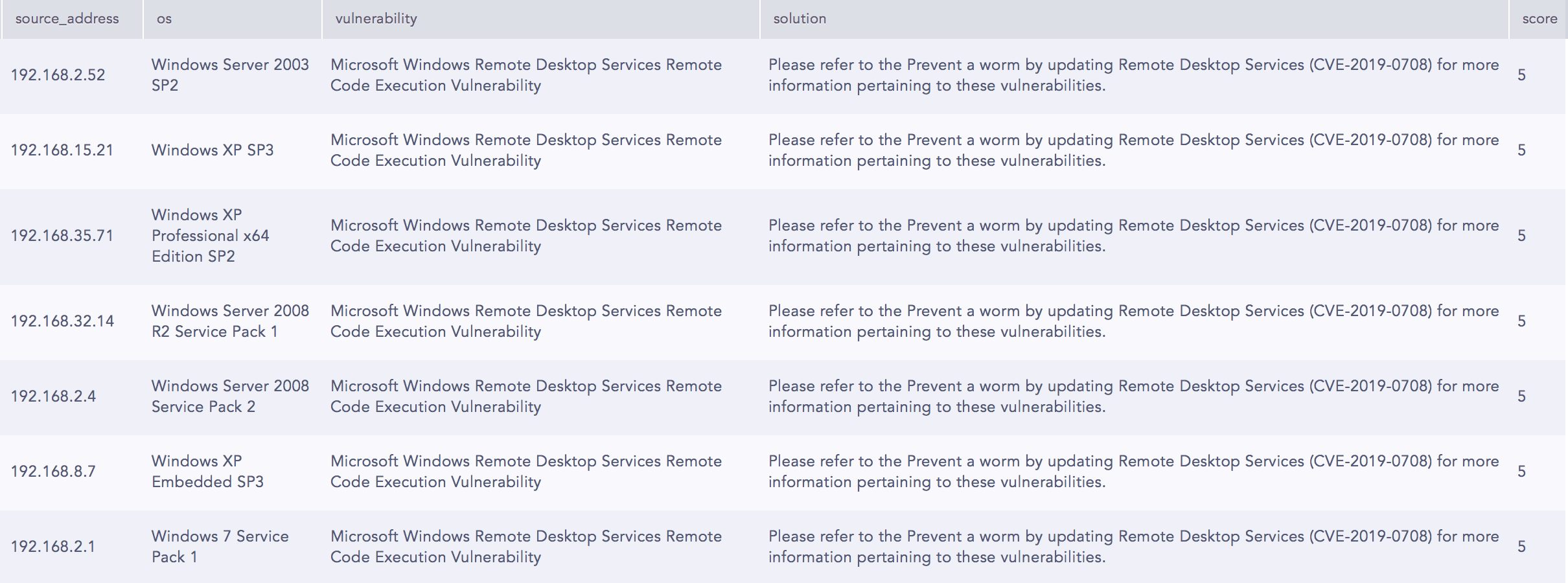
The Windows RDP Remote Code Execution Vulnerability aka BlueKeep (CVE-2019-0708) is included as a critical vulnerability that exists in Remote Desktop and impacts the Windows Servers 2003, 2008, 2008 R2, Windows XP, and Windows 7. Exploiting this vulnerability allows an unauthenticated attacker to execute an arbitrary code on the vulnerable system.
Due to the criticality of this vulnerability, Microsoft has not only released patches for Windows 7, Server 2008 & R2, but also for Windows XP and Server 2003. The PoC code might be publicly available very soon and may result in a “WannaCry-type” attack.
LogPoint query
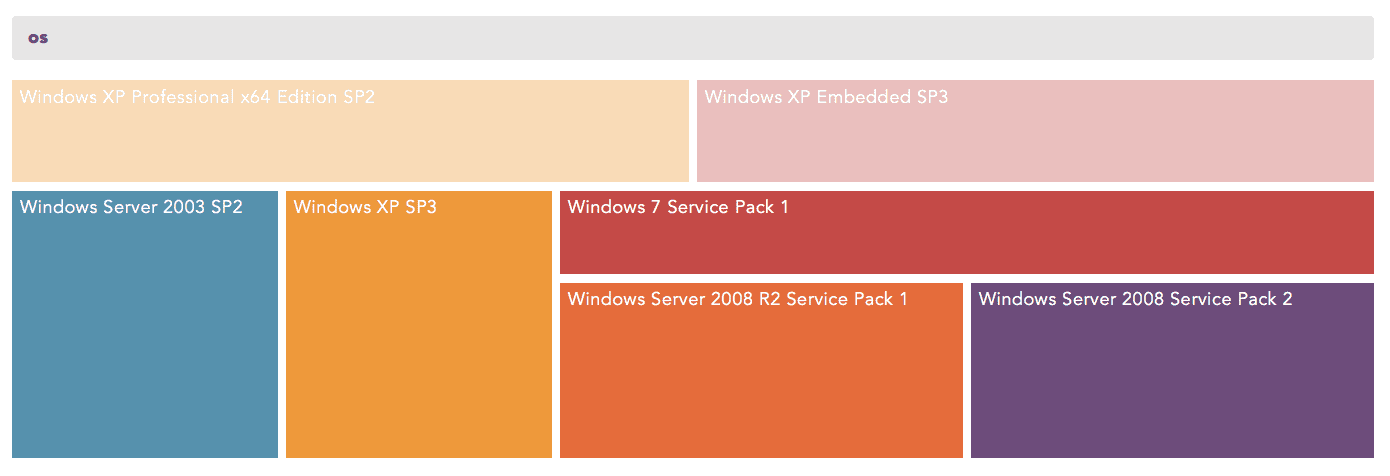
Top 10 OS with Remote Code Execution Vulnerabilities
(source_address=* OR host=*) cve_id="*CVE-2019-0708*" | rename operating_system as os, host as source_address | chart count() by os, source_address order by count() desc limit 10
Remote Code Execution Vulnerability Details
(source_address=* OR host=*) cve_id="*CVE-2019-0708*" | rename operating_system as os, host as source_address, title as vulnerability, severity as score, cvss as score | chart max(score) as score by source_address, os, vulnerability, solution
DHCP Server Remote Code Execution
Another critical vulnerability relates to a memory corruption in the Windows DHCP Server (CVE-2019-0725). An attacker can process specially crafted packets and run arbitrary code on an affected DHCP server. For any Windows DHCP implementations this patch needs to be prioritized.
LogPoint query
(source_address=* OR host=*) cve_id="*CVE-2019-0725*" | rename operating_system as os, host as source_address, title as vulnerability, severity as score, cvss as score | chart max(score) as score by source_address, os, vulnerability, solution
Privilege Escalation in Windows
Microsoft has also addressed a Windows Error Handling privilege escalation vulnerability (CVE-2019-0863) which has been exploited extensively by an attacker. This patch also needs to be prioritized for all supported versions of Windows.
LogPoint query
(source_address=* OR host=*) cve_id="*CVE-2019-0863*" | rename operating_system as os, host as source_address, title as vulnerability, severity as score, cvss as score | chart max(score) as score by source_address, os, vulnerability, solution
Workstation Patches
Finally, Scripting Engine, Browser, Word and GDI+ patches from Microsoft needs to be prioritized by the system administrator for all workstations that are used to access the Internet or email via a browser.
Log source requirement
- Vulnerability Management (Qualys/Nessus)