By Roshan Pokhrel, Associate Engineering Manager, LogPoint
After rearing its ugly head in early 2019 by attacking French consulting firm Altran Technologies, LockerGoga ransomware strikes again! This time the unfortunate victim is Norsk Hydro, Scandinavia’s largest and internationally renowned producer of aluminium.
Eivind Kallevik, CFO of Norsk Hydro, stated that internal IT detected the attack had affected computer systems in multiple business areas at around 12AM CET on Monday. He also went on to assure the public that despite the disruption, Norsk Hydro employees and civilians were not targeted in anyway by this attack.
LockerGoga shows similarities to other recent large scale ransomware attacks such as CottleAkela or Gorgon. These malware are designed to access and encrypt sensitive user data on infected devices by either sending out malicious emails or using other forms of social engineering to trick victims into downloading a malicious file or accessing a link prompting the automatic download of said file and/or using exploit kits.
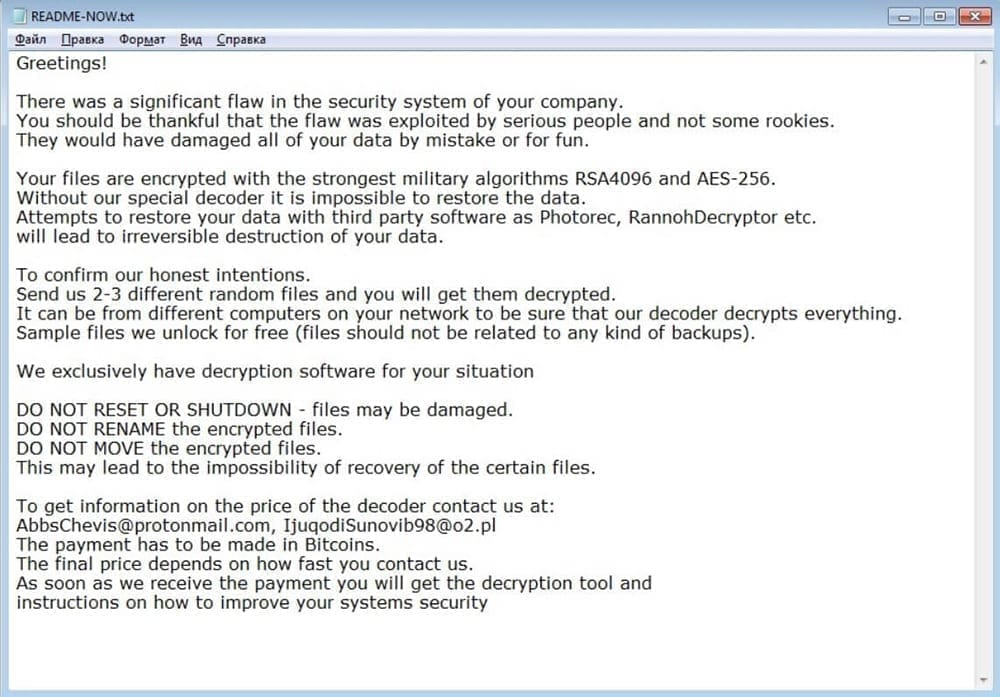
Once the victim is lured into opening the malicious attachment, the ransomware encrypts the files by using AES or a similar algorithm. In the case of LockerGoga, the attackers used the RSA- 4096 and AES-256 cryptography algorithms with the following attachment:
- .locked!?”
- “.locked”
A README-NOW.txt noted:
In the case of LockerGoga, the targeted file extensions included: pdf, .ppt, .pot, .potx, .ppsx, .sldx, .doc, .dot, .dotx, .docb, .xlm, .xlsx, .xltx, .pps, .pptx, .xlsb, .xlw, and .wbk.
How does LogPoint SIEM detect ransomware?
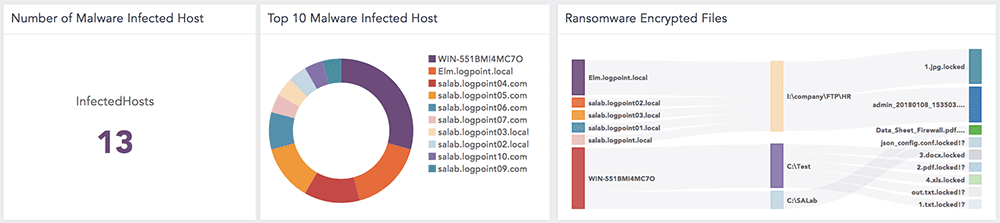
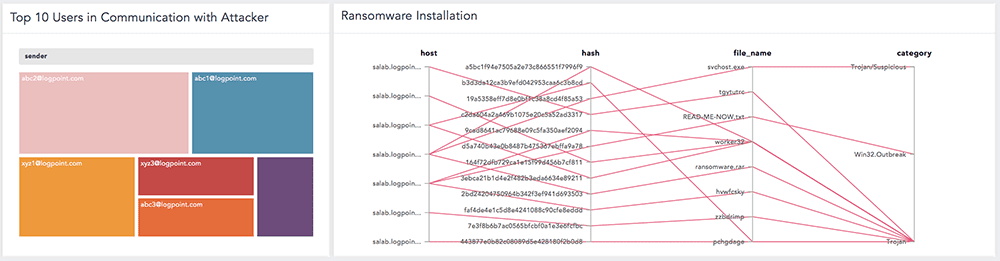
LogPoint LockerGoga malware application provides you with a comprehensive package to detect any malware infection in just a few simple steps. The list of updated IoC’s required to run the application are as follows:
Indicator of Compromise
The red flags indicating that your system might have been compromised.
Hash
| MD5 | SHA1 | SHA256 | File Name | Malware Category | |
|---|---|---|---|---|---|
| 1 | 2bd24204750964b342f3ef941d693503 | d1c0138baa345a8d912cc4519d10e0bde3f1d059 | 0e874661b6bc116f18230dd6b50f792a944f4ba8e3f58edf1f128517ce8d44ee | ransomware.rar | Trojan |
| 2 | a5bc1f94e7505a2e73c866551f7996f9 | 7dea7ff735023418b902d093964028aefbc486a5 | 14e8a8095426245633cd6c3440afc5b29d0c8cd4acefd10e16f82eb3295077ca | worker32 | Trojan |
| 3 | d5a740b43e0b8487b475367ebffa9a78 | d7760deb9b0b5647b3b297cda7533b7c3f0fd035 | 39e298627215ed3bed76686f52eb741335195c2cd09b69181892b4fa9f53f514 | READ-ME-NOW.txt | Win32.Outbreak |
| 4 | faf4de4e1c5d8e4241088c90cfe8eddd | fcd241fdcd462199f2907ca34c73ce9c89b03e5f | 47f5a231f7cd0e36508ca6ff8c21c08a7248f0f2bd79c1e772b73443597b09b4 | hvwfcsky | Trojan |
| 5 | 9cad8641ac79688e09c5fa350aef2094 | 3da0a217bbda09561780f52f163a6aafeb721d60 | 5b0b972713cd8611b04e4673676cdff70345ac7301b2c23173cdfeaff564225c | worker32 | Trojan |
| 6 | 3ebca21b1d4e2f482b3eda6634e89211 | 37cdd1e3225f8da596dc13779e902d8d13637360 | 6e69548b1ae61d951452b65db15716a5ee2f9373be05011e897c61118c239a77 | worker32 | Trojan |
| 7 | b3d3da12ca3b9efd042953caa6c3b8cd | 34fb03a35e723d27e99776ed3e81967229b3afe1 | 7852b47e7a9e3f792755395584c64dd81b68ab3cbcdf82f60e50dc5fa7385125 | pchgdage | Trojan |
| 8 | 443877e0b82c08089d5e428180f2b0d8 | 26d96eb7390fc9565a3016e907840e263380b301 | 7a059301a1c6198bb3a2cb2ae8cd358486f806ea1b202c4ca8613846a9c3cc64 | pchgdage | Trojan |
| 9 | 7e3f8b6b7ac0565bfcbf0a1e3e6fcfbc | b2a701225c8c7f839be3c5009d52b4421063d93e | 7bcd69b3085126f7e97406889f78ab74e87230c11812b79406d723a80c08dd26 | zzbdrimp | Trojan |
| 10 | c2da604a2a469b1075e20c5a52ad3317 | 442ed0cac2abe062d8e630f3ece803af687751db | 88d149f3e47dc337695d76da52b25660e3a454768af0d7e59c913995af496a0f | tgytutrc | Trojan |
| 11 | 164f72dfb729ca1e15f99d456b7cf811 | f92339e73c7e901c0c852d8e65615cfb588a4ff6 | 8cfbd38855d2d6033847142fdfa74710b796daf465ab94216fbbbe85971aee29 | worker32 | Trojan |
| 12 | 19a5358eff7d8e0bf1c38a8cd4f85a53 | baa9f65be5177d1af5c5e8e822d756c799bb03ae | 9128e1c56463b3ce7d4578ef14ccdfdba15ccc2d73545cb541ea3e80344b173c | svchost.exe | Trojan/Suspicious |
| 13 | a52f26575556d3c4eccd3b51265cb4e6 | 61fdebb3c9dfa880b54e82579256acfcd4d6d406 | 97a2ab7a94148d605f3c0a1146a70ba5c436a438b23298a1f02f71866f420c43 | CryptoLocker | Trojan |
| 14 | ba53d8910ec3e46864c3c86ebd628796 | d1c2dfedc602f5d5f2036b0ba5541cac8f8b4b95 | a84171501074bac584348f2942964c8550374c39247ec6af0f4a69756ea9fc7a | CryptoLocker | Trojan |
| 15 | cf3282d6ad1dce954e472722979f3bde | a2a9501fe1c525702ec428b8c4aa35be954424b6 | b686c88bce6629088ce1044b30ad1d5b978fd754601b8b463bc1f611b01d05d7 | CryptoLocker | Trojan |
| 16 | 2e2e4988a49f8b22d5909cf1964851cb | cd3f6121705a3df9156d823b7da34c4745588ac5 | b8dedd74f8f474c97d53d313eb5a61d09fc020e91aa09c36711bac5cc123b6d7 | README-NOW.txt | Trojan-Ransom.LockerGoga |
| 17 | 2e2e4988a49f8b22d5909cf1964851cb | cd3f6121705a3df9156d823b7da34c4745588ac5 | b8dedd74f8f474c97d53d313eb5a61d09fc020e91aa09c36711bac5cc123b6d7 | README-NOW.txt | Trojan-Ransom.LockerGoga |
| 18 | 52340664fe59e030790c48b66924b5bd | 73171ffa6dfee5f9264e3d20a1b6926ec1b60897 | bdf36127817413f625d2625d3133760af724d6ad2410bea7297ddc116abc268f | worker32 | Trojan |
| 19 | 4da135516f3da1c6ca04d17f83b99e65 | 127b2c4403995d35622487bd250d673d74b613b9 | bef41d3c76aa98e774ca0185eb5d37da7bf128e3d855ebc699fed90f3988c7d3 | svch0st.4553.7z | Trojan |
| 20 | a1d732aa27e1ca2ae45a189451419ed5 | 50f5a5ec13d21d4df119140547d63bc40f93b079 | c3d334cb7f6007c9ebee1a68c4f3f72eac9b3c102461d39f2a0a4b32a053843a | – | Trojan |
| 21 | 174e3d9c7b0380dd7576187c715c4681 | 31fbfe814628db3b459ddc87bf5ed538700db17a | c7a69dcfb6a3fe433a52a71d85a7e90df25b1db1bc843a541eb08ea2fd1052a4 | CryptoLocker | Trojan |
| 22 | e11502659f6b5c5bd9f78f534bc38fea | b5fd5c913de8cbb8565d3c7c67c0fbaa4090122b | c97d9bbc80b573bdeeda3812f4d00e5183493dd0d5805e2508728f65977dda15 | tgytutrc | Trojan |
| 23 | 52d43618b1d9f660d446163c050eccfb | 6ee0e829659d4746bdfba803ecabbe75707e9b88 | ec52b27743056ef6182bc58d639f477f9aab645722f8707300231fd13a4aa51f | tgytutrc7290.zip | Trojan |
| 24 | 16bcc3b7f32c41e7c7222bf37fe39fe6 | a25bc5442c86bdeb0dec6583f0e80e241745fb73 | eda26a1cd80aac1c42cdbba9af813d9c4bc81f6052080bc33435d1e076e75aa0 | yxugwjud | Trojan |
| 25 | e8c7c902bcb2191630e10a80ddf9d5de | e00ec019409a078e9819e09d0f3915cb41fc131f | f3c58f6de17d2ef3e894c09bc68c0afcce23254916c182e44056db3cad710192 | worker32 | Trojan |
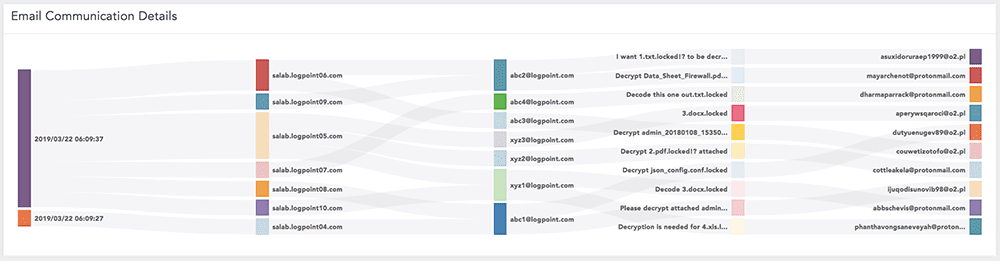
Emails
For further information about the danger and threat behavior of trojans, read our blogpost here.
Log Source Requirements
Sysmon/Windows Server/Integrity Scanner
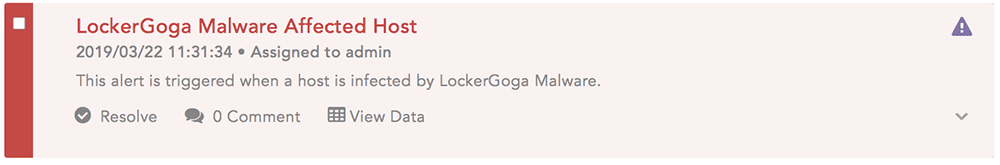
- It detects malicious file installation and malware-infected hosts.
Mail Server
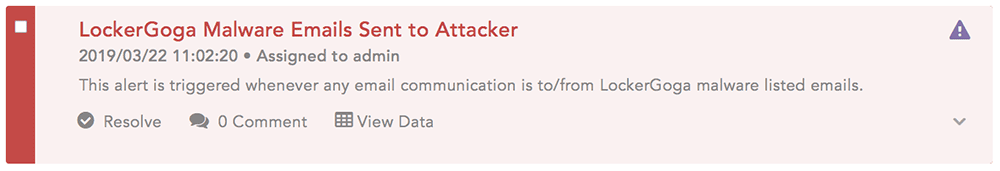
- It detects any emails sent to the malicious address.
Screenshots
LogPoint customers can download the application directly from the Help Center.
For more information, contact LogPoint.