Today we have released our application to detect the KRACK attacks. For detailed information about the attack please refer to https://www.krackattacks.com/.
Since the attack can target both infrastructure and endpoints, patching the infrastructure alone will not be sufficient to protect against the attacks. Patching endpoints will be a tedious process for large organizations, especially if they operate IOT, OT or embedded devices relying on WIFI.
Since the vulnerable devices can survive for longer periods of time in the network, it is important to implement active monitoring of potential attacks.
LogPoint has released an application that picks up logs from your wireless controllers if they detect the two primary approaches to exploiting the vulnerabilities:
- Faking an infrastructure AP (evil twin/rogue AP)
- Injecting frames in existing communication streams (null-key attacks and re-use of initialization vectors)
With this application, you will be able to identify possible attempts to exploit the KRACK vulnerability.
Configuring your WIFI infrastructure
Depending on your WIFI infrastructure, configuring the controllers to detect and log these things varies. We have included a guide on how to configure your Cisco Wireless Lan Controller.
Step 1. Make sure rogue detection is enabled
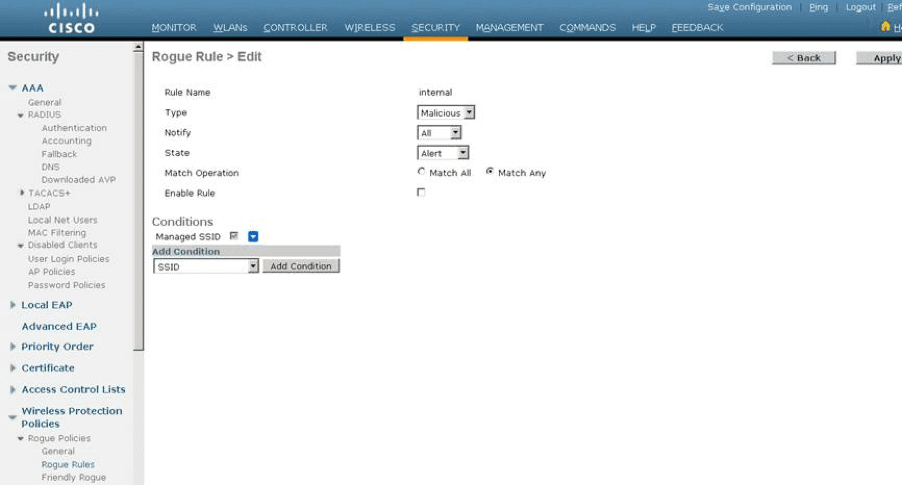
Step 2. Create a rule to flag rogue APs using “managed SSIDs” as malicious
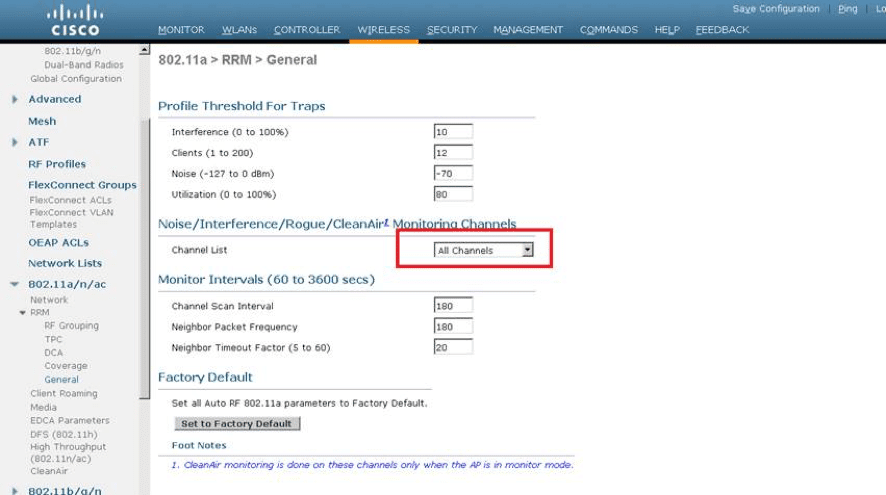
For more details on configuring your Cisco WIFI infrastructure, please refer to WLC documentation:
Configuring KRACK analytics in LogPoint
Step 1. Download the application from LogPoint Help Center and install it on your system
https://servicedesk.logpoint.com/hc/en-us/articles/115005424025-KRACK
Step 2. Activate the dashboard on your system
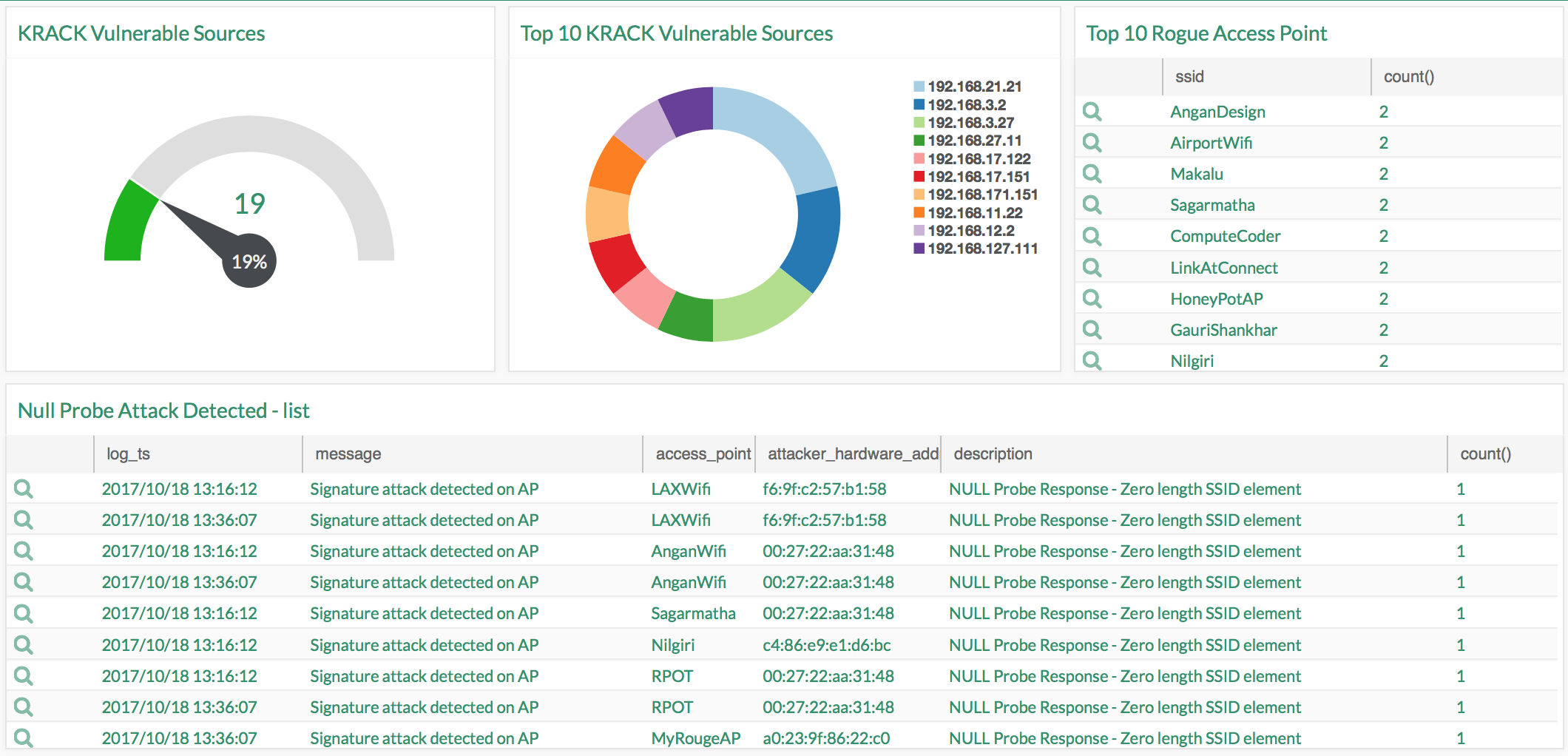
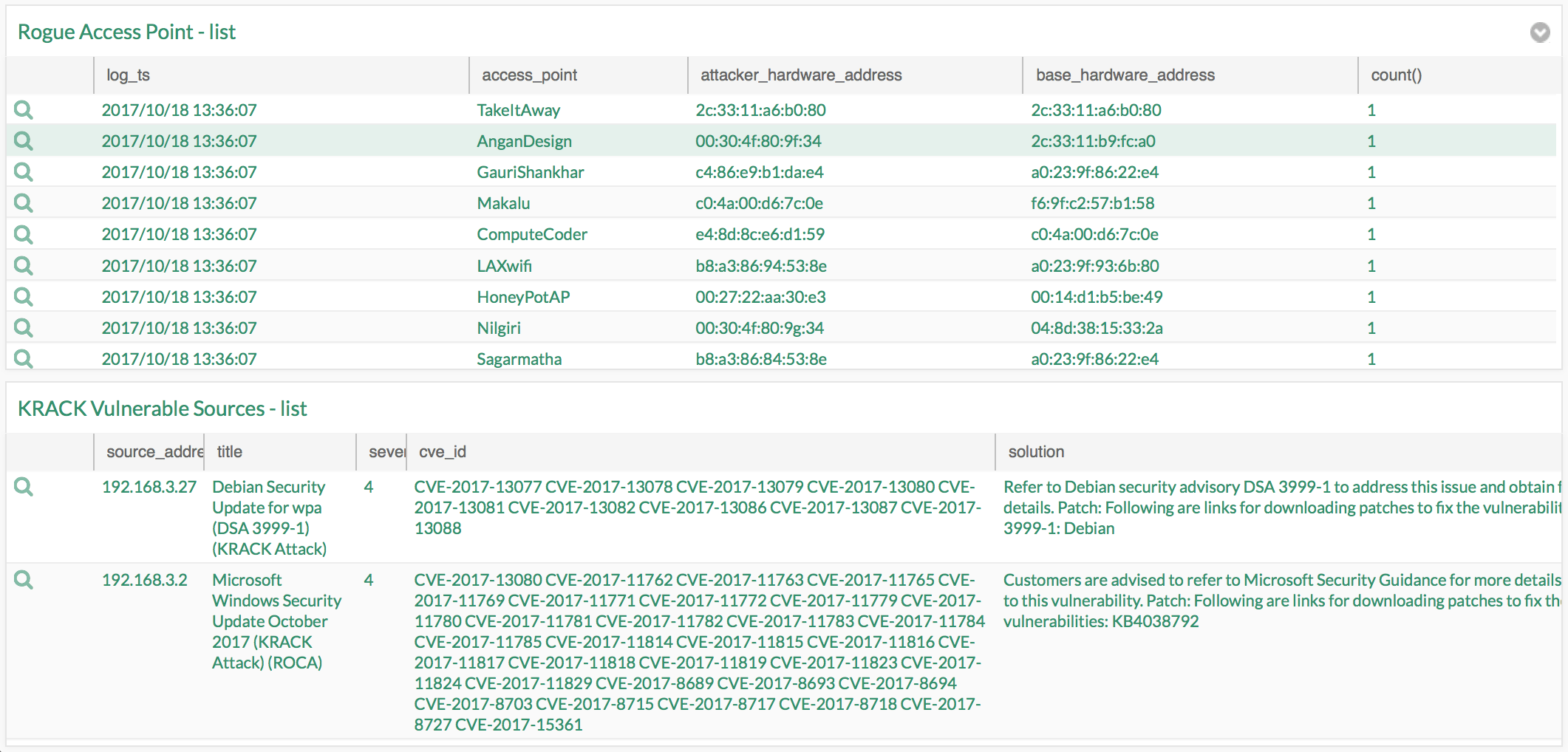
Step 3. Happy hunting!
Content included in the application
- Vulnerability Scan: Identifying vulnerable devices. Look for various CVE ID for KRACK Attacks
- Null Probe Response Attacks
- Rogue Access Point Detection
For more information visit us at https://www.logpoint.com or contact us at [email protected]






