One of the big concerns at the moment in the world of IT security is Ransomware. It is a small piece of malware that will encrypt data on local hard drives as well as remote network shares. After the encryption is completed a ransom for the data is requested.
It is important to understand that no file integrity monitoring tools can prevent or eradicate a ransomware. The best way to avoid the malware is user awareness as well as updated mail and endpoint protection.
When dealing with ransomware, one of the most important aspects is the time used to detect it. The longer a ransomware is active in an enterprise, the larger the impact and costlier it is to recover.
As mentioned, no single tool – even SIEM – can prevent or eradicate a ransomware. The very nature of a SIEM installation is to collect logs for something that has already happened.
An appropriate and well configured SIEM installation with file integrity monitoring tools will greatly reduce the meantime to detect an outbreak, hence also reduce the costly meantime to recover. This is done by always having a clear baseline of your enterprise, as well as the possibility to actually see in near real-time what is going on in the enterprise.
Baseline
Baselining your enterprise is very important, this is the only way you can make an educated guess to determine if something is normal behavior or an abnormal activity. In the case of ransomware, the baseline for the utilization of a file system is very important. This will help to quickly identify any spike in file creation, renaming or deletions by a specific user or process. Depending on the log data available, both user name and source ip can quickly be identified as well as all files affected through file integrity monitoring.
Below are some of the most common ways of monitoring the file systems in an enterprise:
File Integrity Monitoring (FIM)
Pro: Will normally provide all the information needed.
Cons: Not real-time, requires a lot of resources.
Most file integrity monitoring tools will scan specific selected directories for changes. The monitoring is however (in most cases) not carried out in real time, but on scheduled intervals. During a scan a checksum of the files are compared with the values from the last scan. This way the file integrity monitoring tools can identify everything from creating a file, change, rename to deletion of files or folder.
Because file integrity monitoring is not running in real-time, it is not the best method to alert about a ransomware attack. File integrity monitoring can however be very useful when the attack has been contained in order to identify which files needs to be recovered.
Windows OS
Pro: Real-time, native part of the OS.
Cons: Object monitoring is very chatty, difficult to detect renames.
Object access monitoring must be activated either through a Global Policy object or through a local security policy on the server. Furthermore, it is necessary to enable monitoring for everybody on the folders in question. A comprehensive guide on this can be found on Microsoft Technet.
When enabled this will generate a lot of events in the server’s security log. The major event to look for is event ID “4663”. The key in this event to look for is the access mask, because this will reveal what kind of object access has been carried out. When the events have been identified, further investigation is needed in order to determine if a 4663 event is a delete or rename etc.
The search language in LogPoint’s SIEM solution makes it very simple to do this and build a dashboard like the following (remember when dealing with ransomware, it is the amount of activities in a directory that will be the counter):
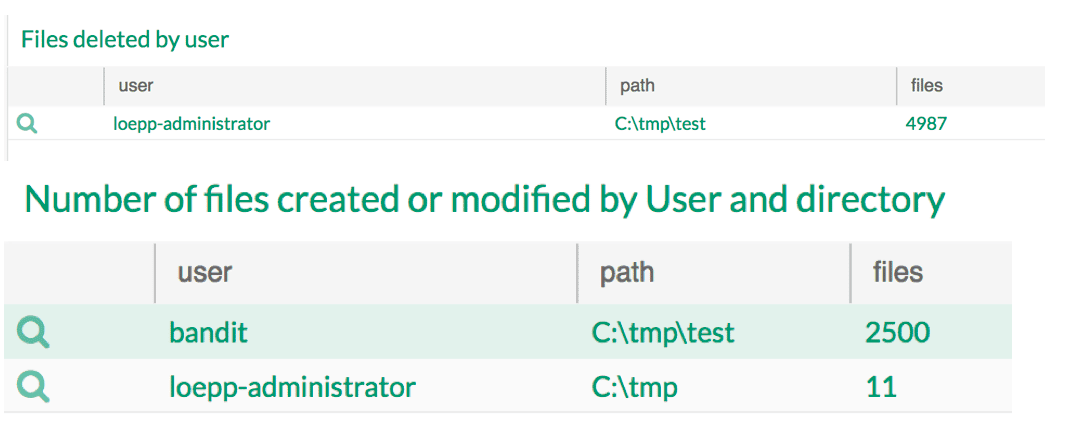
In the latter case, over the last 10 minutes Bandit has created 2500 files in the c:\tmp\test directory, which will be considered abnormal. Again, when a baseline has been established for the enterprise, the search from the dashboard can be reused to create near real-time alarms.
Furthermore, with a small change the search can provide a full list of files that has been changed/deleted etc. by a specific user. The list can be exported and reused as input for a backup software to start a restore of the affected files. In this way, LogPoint facilitates recovery, which can be started within minutes.
Hardware
Pro: Real-time, native part of storage system.
Cons: Enrichment of the logs may be needed.
In a lot of enterprises users connect directly to the storage environment. In these cases, the audit log has to come directly from the storage devices (LogPoint supports most of the major storage systems).
Audit for malware activities has to be carried out more or less in the same way as with the Windows OS. The storage logs are normally much less chatty than an OS log and more precise on what has happened on the system.
Depending on the type of access to the storage system used, the audit log may not contain everything needed, i.e. the individual event may contain file name, ip-address and the type of access, but no username. Here, LogPoint’s ability to enrich the log files can be a big help. An ip-address can be translated to a device name, and a device name can be converted to a specific user in one query. In this simple way, LogPoint is able to identify a person who is doing something out of the ordinary, so action can be taken at once.
The Human Factor
Even though LogPoint file integrity monitoring tools can help to quickly identify behavior that is out of the ordinary and can be an indicator for ransomware, human intervention is still needed in order to stop and contain the processes as well as start the recovery. Unfortunately, this last part is greatly overlooked, hence the cost and meantime to recover becomes greater than needed. It is therefore an absolute must to test the procedures needed when LogPoint alerts you on Ransomware.
LogPoint customers are already experiencing great value of this feature and one has more than 50,000 employees and claim the ability to detect and react to any ransomware attack across their massive IT infrastructure in less than 5 minutes…. Want to know more…?






