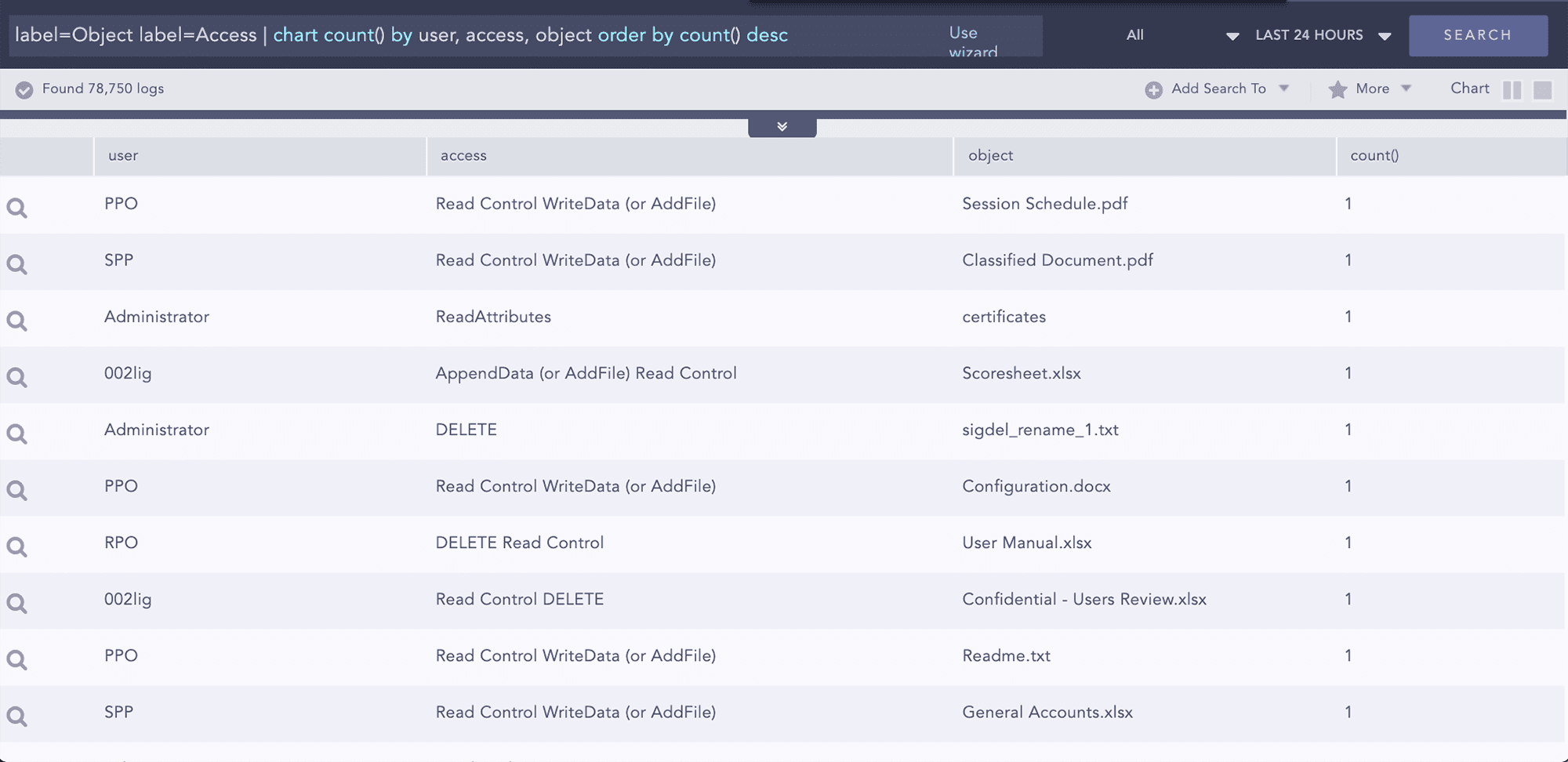
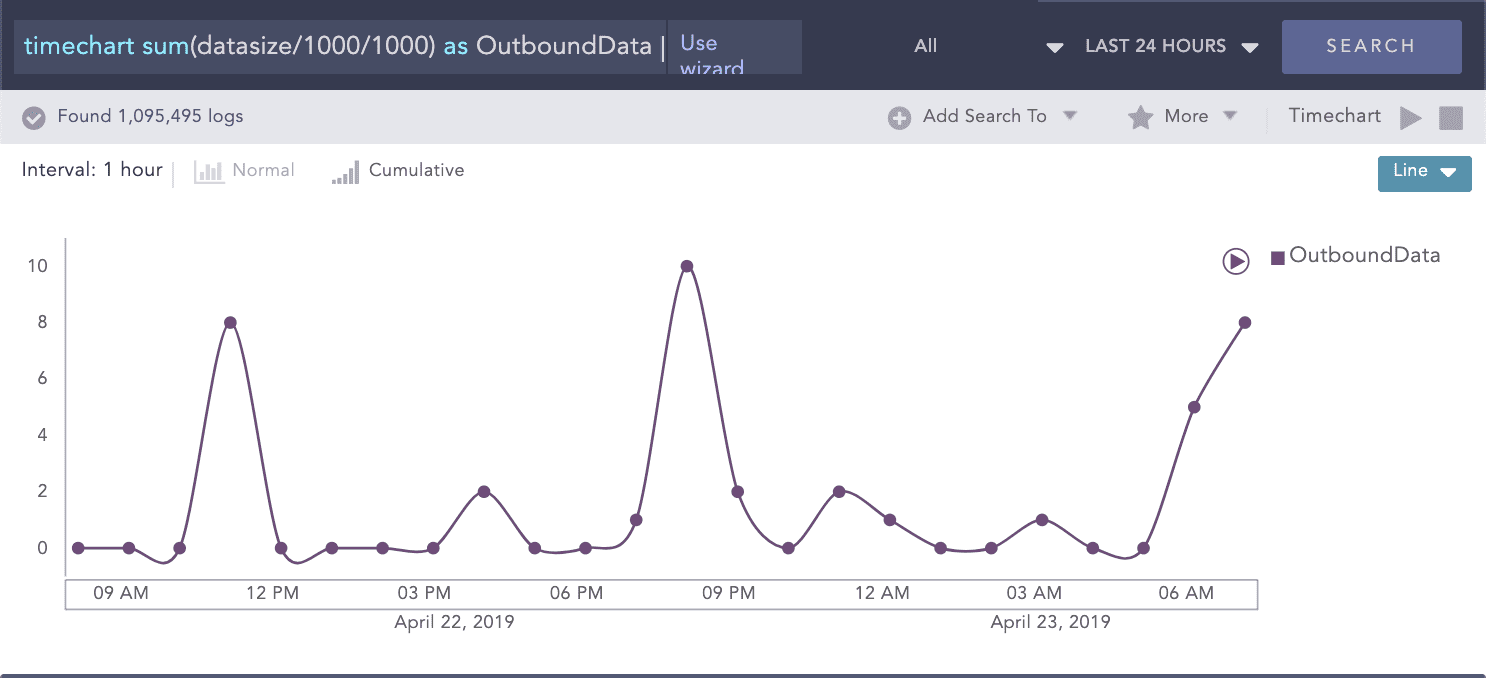
Cybersécurité pour le secteur de l’Éducation
Les violations de la sécurité dans les universités et les grandes écoles ont considérablement augmenté au cours des dernières années. La nature ouverte des systèmes informatiques des campus et la propriété intellectuelle dans ces institutions en ont fait une cible attrayante pour les attaques malveillantes. Les universités et les grandes écoles sont l’objet de piratages, d’attaques par logiciel malveillant, de courriels d’hameçonnage, d’attaques par DDoS et de piratages intentionnels ou accidentels par les étudiants.
Téléchargez notre brochure pour en savoir plus sur la mise en place de solutions SIEM et UEBA pour les établissements éducatifs :

Logpoint pour l’Université de Bedfordshire
Avec Logpoint, l’équipe informatique de l’Université du Bedfordshire a :
- simplifié la gestion des alertes réseau
- amélioré sa capacité à identifier les incidents nécessitant une intervention
- réduit ses coûts opérationnels
En convertissant les données en informations exploitables et en améliorant leur posture de cybersécurité, Logpoint a réduit les analyses fastidieuses des logs de sécurité tout en éliminant la majorité des faux positifs.

Protéger les informations à caractère personnel sensibles et la recherche avancée
Les établissements d’enseignement supérieur stockent de grandes quantités de renseignements personnels provenant des étudiants actuels, des professeurs, des candidats, du personnel administratif, des anciens élèves, des collaborateurs, des participants à la recherche et aux projets, des fournisseurs et des autres parties-prenantes. En outre, ces systèmes informatiques stockent des informations sur la recherche de pointe et des contenus de valeur relevant de la propriété intellectuelle. Malheureusement, les unités d’enseignement supérieur, en particulier les établissements publics, manquent souvent des ressources financières et humaines nécessaires pour mettre en place un plan complet de sécurité de l’information, ce qui compromet leurs objectifs.
Grâce à Logpoint, les établissements d’enseignement supérieur et les universités peuvent s’appuyer sur des analyses avancées, accélérées par l’apprentissage automatique, pour améliorer l’état de la cybersécurité et automatiser efficacement les réponses pertinentes aux menaces internes et externes.
Les menaces
Il existe de nombreux auteurs potentiels d’infractions numériques dans le secteur de l’éducation. Alors que les attaques ciblées n’ont rien d’étonnant, il est impossible d’écarter les étudiants eux-mêmes, qui parfois, parce qu’ils s’ennuient ou sont curieux, peuvent servir de catalyseur à une violation de sécurité. Que ce soit intentionnel ou accidentel, des mesures de protection doivent être mises en place pour empêcher que cela se produise.
Surveillance des activités des utilisateurs
Le monitoring des activités des utilisateurs est depuis longtemps la clé de voûte de toute stratégie de défense efficace. Logpoint est conçu pour fournir aux analystes un outil intuitif et puissant pour détecter les activités malveillantes, créer des alertes, des dashboards et des rapports – offrant une visibilité globale et une réponse immédiate. Principalement pour des raisons de confidentialité et de réglementation, le contrôle de l’activité des utilisateurs se concentre sur les activités liées à l’accès aux objets. Logpoint peut surveiller cela en utilisant des rapports d’audit natifs sur l’accès aux données. L’application FIM de Logpoint surveille tout type de tentative d’accès aux systèmes de partage de fichiers privilégiés et fournit des informations sur le type d’accès et les actions effectuées dans le fichier. De plus, les sommes de contrôle (checksums) d’origine et celles modifiées peuvent également être comparées pour mieux comprendre le comportement en termes d’accès.
Corrélation analytique avancée et reconnaissance de schémas
Logpoint est capable, par défaut, d’effectuer une corrélation avancée sur plusieurs sources de données – internes, externes ou structurées. Il peut s’agir d’une agrégation entre deux ou plusieurs groupes d’entités, tels que l’utilisateur et l’adresse source en cas d’échec de connexion, ou de la combinaison de données provenant de plusieurs sources de logs en utilisant les requêtes join et followed by. Les alertes sur les comportements à risque et les activités anormales vous sont fournies en temps réel. Avec Logpoint, les listes dynamiques peuvent également être utilisées pour effectuer des corrélations avancées de plusieurs façons, telles que la création d’une liste dynamique avec des adresses IP ou des noms d’hôte pour les postes de travail vulnérables afin d’identifier toute exploitation potentielle d’une vulnérabilité par une source de menace.
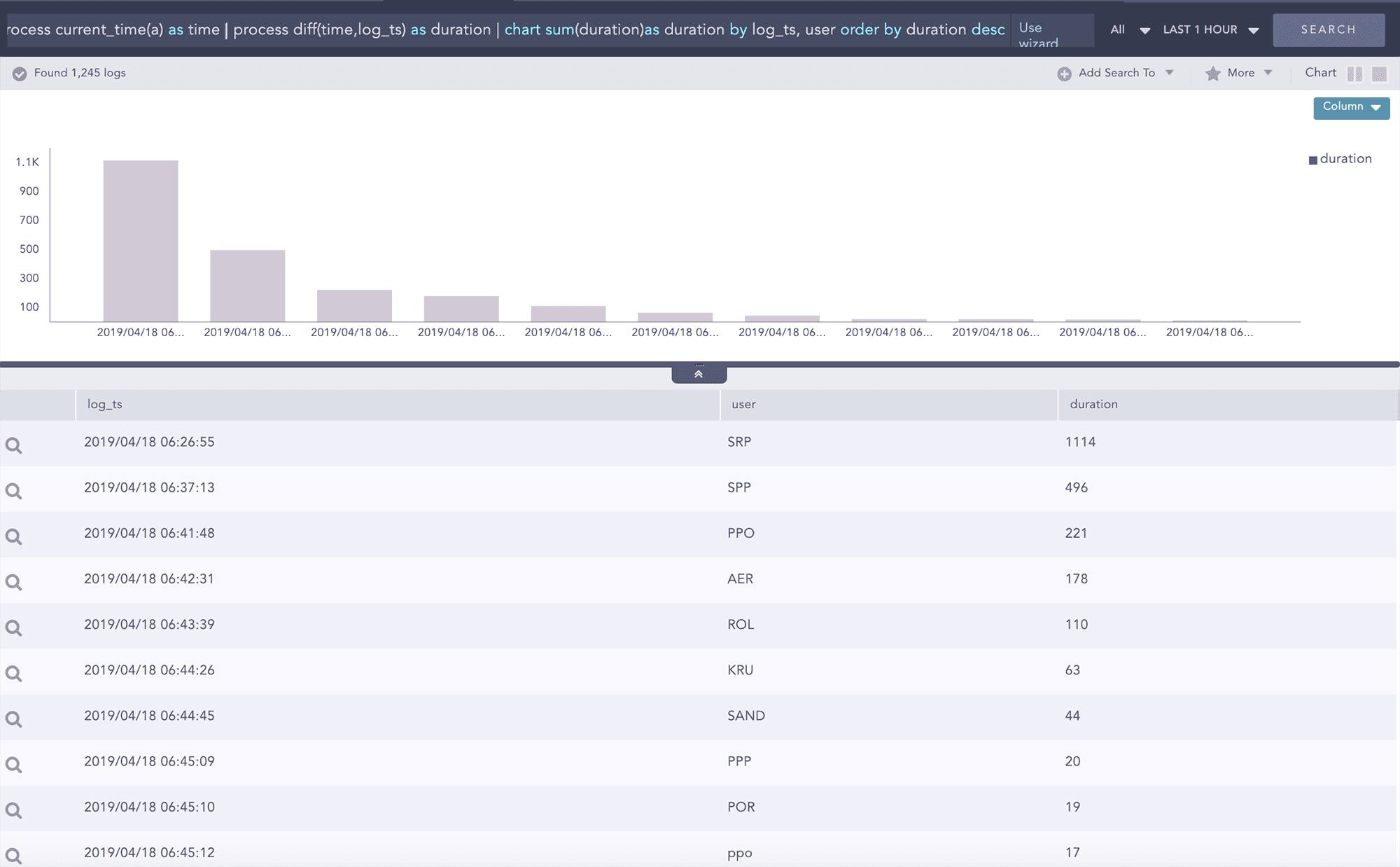
Détection du staging (stockage intermédiaire) et de l’exfiltration de données
Les comptes ou machines compromis tentent généralement de déplacer les données vers des zones de staging où elles pourront être facilement extraites du réseau de l’entreprise. Lors de la préparation des données à extraire, les attaquants utiliseront des outils tels que PSExec ou des outils de bureau à distance. Dans ce cas, l’UEBA détectera et mettra en évidence des opérations de staging et des mouvements latéraux anormaux, notamment des transferts de données importants entre postes de travail (très inhabituels), des combinaisons de protocoles/ports inhabituelles ainsi que des volumes inhabituellement élevés d’accès aux données.