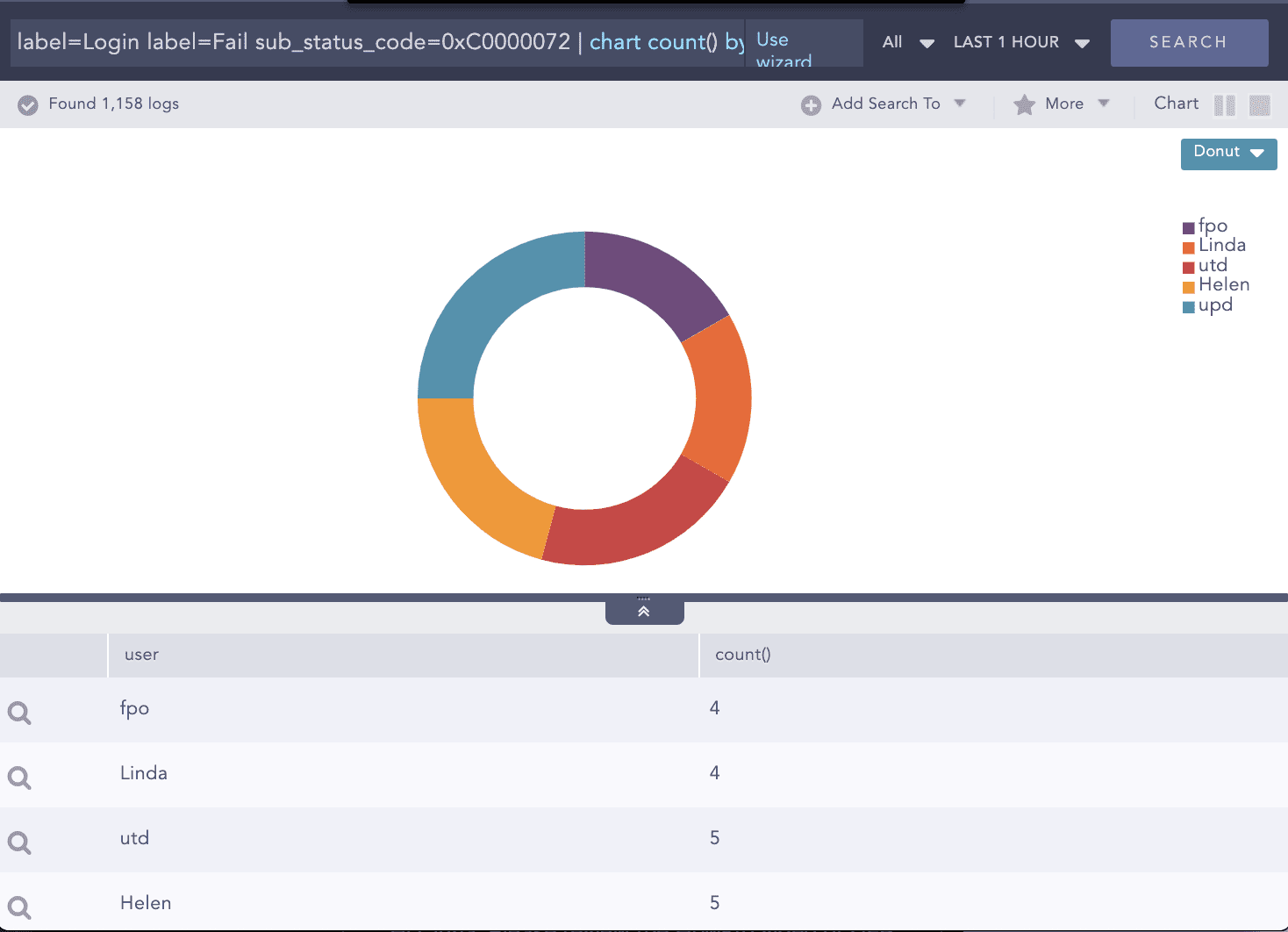
Cybersécurité dans l’administration publique
Pour les organismes publics opérant à grande échelle, accroître l’efficacité est une exigence constante motivée par une demande politique.
Téléchargez la présentation de notre solution pour découvrir plus en détail comment bien démarrer avec le SIEM et l’UEBA appliqués au secteur public :

Les institutions publiques sont confrontées à un certain nombre de défis, notamment :
- Des exigences en matière de conformité de plus en plus difficiles à respecter (RGPD, ISO, NIS etc.).
- Une complexité accrue au niveau de l’infrastructure qui rend difficile l’obtention d’une analyse centralisée, quel que soit l’organisme concerné.
- Une difficulté pour détecter les menaces persistantes avancées (APT : Advanced Persistent Threats), les pertes de données et les menaces internes.·
- Des exigences accrues en matière de confidentialité qui doivent être respectées tout en maintenant le bon fonctionnement des opérations IT et la sécurité des données des citoyens.
- Une augmentation des quantités de données qui implique des opérations de cybersécurité et d’analyse plus coûteuses.
De nombreuses organisations publiques chargées de sécuriser les données ne disposent peut-être pas de la bonne solution pour mener à bien leur mission. C’est un véritable problème, mais il a une solution. Cette solution ? C’est le SIEM. Les rapports transparents et rapides de Logpoint sur les comportements inhabituels au sein du réseau s’adaptent facilement aux exigences en matière de conformité spécifiques à votre agence ou institution. En observant tous les évènements se produisant sur votre réseau, Logpoint vous permet de traiter rapidement une éventuelle violation, limitant ainsi les dommages potentiels.
Logpoint pour Durham County Council
En choisissant Logpoint, le County Council de Durham a immédiatement économisé 50% au niveau de ses coûts par rapport à son fournisseur précédent. De plus, l’organisation a amélioré ses capacités SIEM :
- En faisant en sorte que les exigences en matière de conformité et d’accréditation soient pleinement respectées.
- Grâce à la structure simple de tarification par nœud, le SIEM peut être largement déployé et davantage de données peuvent être ingérées.
- Grâce à la facilité d’obtention des droits permettant, par exemple au Service Desk, d’effectuer ses propres recherches et de résoudre plus efficacement les cas.
Informations détaillées
Informations détaillées
Alors que les vulnérabilités des logiciels et des systèmes d’exploitation deviennent l’élément central et vital de la cyberguerre moderne, l’infrastructure IT du secteur public est plus vulnérable que jamais aux attaques inattendues. La cybersécurité publique repose sur LA bonne solution, aujourd’hui plus que jamais.
La solution Logpoint SIEM permet au secteur public de détecter immédiatement les cybermenaces sans restreindre sévèrement l’accès aux ressources numériques. Logpoint permet de surveiller, détecter et d’alerter en cas d’incidents de sécurité. Il fournit un aperçu complet et centralisé de la posture de sécurité de l’infrastructure et donne aux professionnels de la cybersécurité publique une vue détaillée des activités au sein de leur environnement IT.
Menaces
Les infrastructures IT publiques sont confrontées à un niveau de menace sans précédent, provenant d’acteurs aussi divers que les États-nations, les cybercriminels, les hacktivistes, les trill-seekers et les insiders. Pour aggraver la situation, de nombreuses organisations publiques utilisent des produits disponibles dans le commerce et connectés à Internet, exposant ainsi les nations et les organisations au cyberterrorisme et à la cybercriminalité.
Regardez notre webinaire, à la demande, dédié au secteur public : Logpoint SIEM for the Public Sector
Détection des mouvements latéraux
Détection des mouvements latéraux
Logpoint UEBA utilise un ensemble de données provenant des systèmes endpoint, d’Active Directory et des référentiels pour détecter les comportements suspects s’écartant de la norme. Ces données comprennent :
- Des tentatives de connexion qui ont échoué au niveau de comptes désactivés.
- Des activités inhabituelles en fonction du jour de la semaine ou de l’heure de la journée.
- Des accès inhabituels aux serveurs, partages de fichiers, applications ou autres ressources.
- Les accès anormalement élevés à certaines ressources.
- Une utilisation d’application anormale et des schémas d’accès au stockage atypiques.
Etant donné que Logpoint UEBA intègre une analyse NetFlow, de nouveaux modèles permettant l’analyse de volume anormalement élevé de connexions au niveau d’un système endpoint ou entre différents systèmes endpoint ainsi que des analyses de port inhabituelles seront ajoutés.
Détection du staging (stockage intermédiaire) et de l’exfiltration de données
Les comptes ou machines compromis tentent généralement de déplacer les données vers des zones de staging où elles pourront être facilement extraites du réseau de l’entreprise. Lors de la préparation des données à extraire, les attaquants utiliseront des outils tels que PSExec ou des outils de bureau à distance. Dans ce cas, l’UEBA détectera et mettra en évidence des opérations de staging et des mouvements latéraux anormaux, notamment des transferts de données importants entre postes de travail (très inhabituels), des combinaisons de protocoles/ports inhabituelles ainsi que des volumes inhabituellement élevés d’accès aux données.
Compromission de comptes privilégiés
Logpoint UEBA a été conçu pour identifier les comptes privilégiés et utilise l’apprentissage automatique (ML) pour réaliser ses autres activités. La fonctionnalité UEBA de Logpoint surveille en permanence les comptes privilégiés pour suivre et évaluer le temps d’activité, l’authentification, l’accès, l’utilisation des applications et le mouvement des données. Logpoint UEBA attribue ensuite un score de risque à tout compte qui s’écarte de la norme et si ce dernier continue à agir de manière anormale, le score de risque augmente. Pendant ce temps, les analyses réalisées par Logpoint UEBA permettent de visualiser l’activité du compte et d’alerter l’analyste en cybersécurité afin de valider l’incident et permettre qu’une action rapide soit lancée.