As head of product at LogPoint, I am proud of the work our engineering team continues to put into innovating our product offerings. We believe, this latest recognition in Gartner’s 2018 Magic Quadrant for SIEM, and the Critical Capabilities companion research, further emphasizes the continued efforts of our team to create modern cybersecurity solutions. by Christian Have, CPO LogPoint
About Critical Capabilities
Gartner’s Critical Capabilities report is a companion report to the Magic Quadrant research and outlines 10 different capabilities that the analyst team determines to be the most important for SIEM platforms. These capabilities are weighted in three dimensions:
- Basic Security Monitoring
- Complex Security Monitoring
- Advanced Threat Defence
The ten capabilities Gartner assesses are:
- Architecture
- Deployment, Operations, Support
- Log and Data Management
- Real-Time Monitoring
- Analytics
- Data and Application Monitoring
- Threat and Environmental Context
- User Context and Monitoring
- Incident Management
- Threat Detection Tools
Why we believe that we are better than our competitors
Per Gartner, “Critical Capabilities are attributes that differentiate products/services in a class in their terms of quality and performance. Gartner recommends that users consider the set of critical capabilities as some of the most important criteria for acquisition decisions.”
In the light of this, we believe placements in the Magic Quadrant and ranking of Critical Capabilities for SIEM validates our ability to provide industry-leading SIEM with UEBA, out-of-the-box analytics- and integration capabilities such as Threat Intelligence.
Why is this important?
We are honored to be the only new entrant to Gartner’s SIEM Magic Quadrant and Critical Capabilities this year. At LogPoint, we dedicate ourselves to build products that our customers love and feel this dedication is reflected in how we are recommended and rated in Gartner’s Peer Insights analysis.
The next level of SIEM
Attractive prices, evolution of the permanent product
Powerful tool, not only for security monitoring
Our red-team exercise has shown that your product is valuable in detecting threats as close to real time as possible
According to Gartner, SIEM technology is typically deployed to support three primary use cases: advanced threat detection, basic security monitoring, investigation, and incident response. From our perspective, these are the three main areas where a Modern SIEM solution should excel. We believe that placements in the 2018 Gartner Magic Quadrant for SIEM shows how LogPoint delivers capabilities that security analysts need to improve their defenses and act quickly in the wake of an attack.
Things to consider for your SIEM
Market leading capabilities
Among other criterias, Gartner evaluates SIEM products based on the “vendor’s ability and track record to provide product functions in areas such as real-time security monitoring, security analytics, incident management and response, reporting, and deployment simplicity. The evaluation also includes operation, administration, stability, scalability and vendor support capabilities.”
We at LogPoint take a differentiated approach to data, leveraging unique UEBA and TI capabilities, as well as seamless integrations to TIPs.
With a robust and scalable architecture—that applies a common event taxonomy to data coming in—we deliver strong UEBA and advanced analytics capabilities that are ready to deploy out of the box. We also effortlessly manage integrations for business context sources, TI and external SOAR or IR platforms by structuring data in a way that makes it readily accessible for analysis.
When a SIEM solution, enhanced with top-notch security analytics, supports threat hunting, time spent on eliminating false positives is drastically decreased. Having SIEM as a data source supported by security analytics not only provides a more valuable pool of log data, but it also enables cutting detection and response time in half.
UEBA 2.0 easily connects to LogPoint through a plugin. As a result, there is no need to do any mapping or customization which lowers time to value dramatically. The deployment architecture is easily scalable for increasing the number of entities and data volume. Our common taxonomy readily gives access to over 400 machine learning models for all devices. Detected anomalies are used as enrichment sources. Since logs and raw logs can easily be investigated based on the detected anomalies, investigation and forensics can take place immediately.
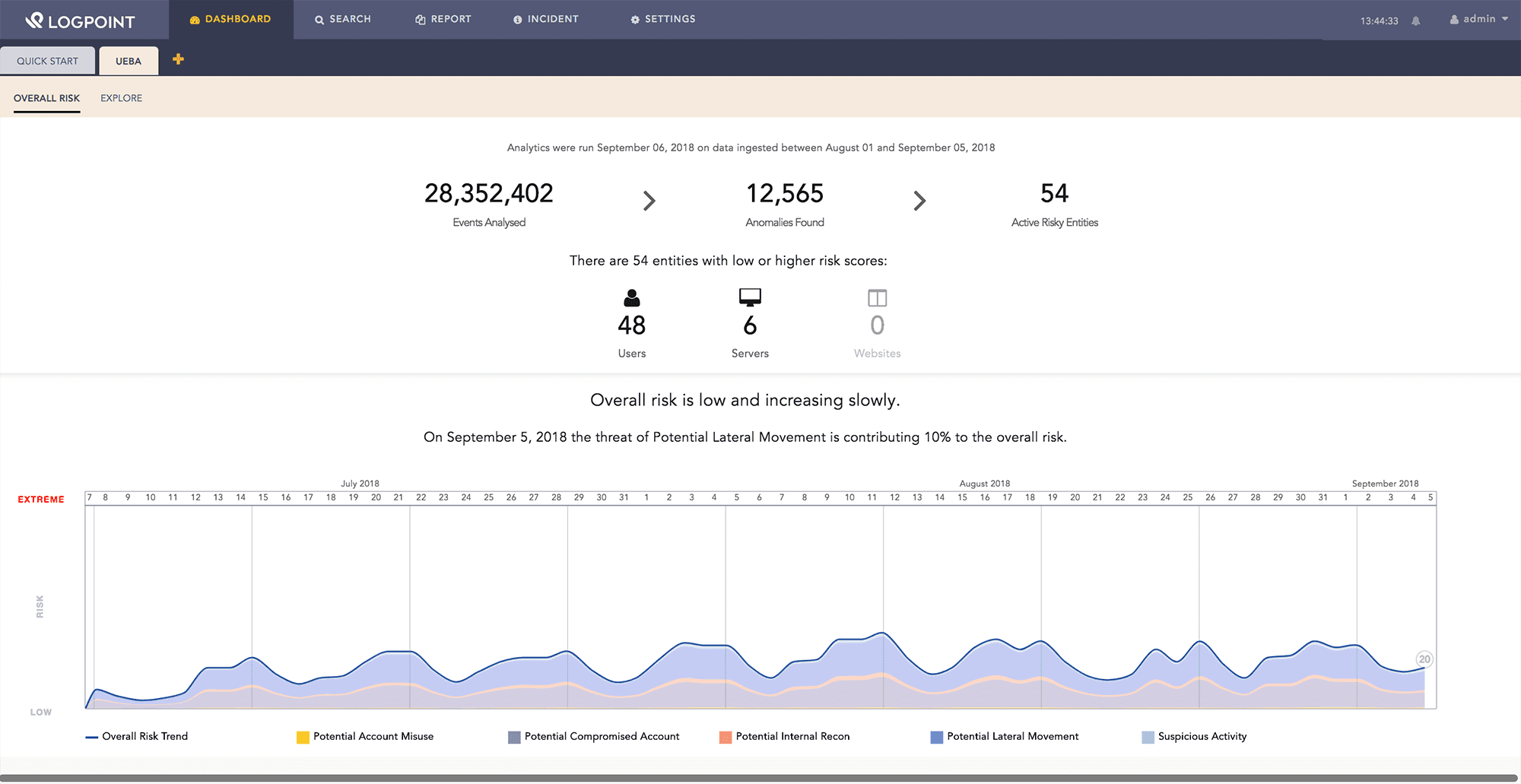
With LogPoint UEBA, we instantly provide you with the number of active risky entities, eliminating the struggle of combing trough each and every detected anomaly.
The LogPoint Threat Intelligence Application offers a simple and efficient threat intelligence platform to identify emerging threats within your infrastructure, integrating with more than 100 threat intelligence feeds. Leveraging LogPoint’s single taxonomy, the data is converted into a “common language” format, then LogPoint compares it with your enterprise log data.
By this, analysts can automate event interrogation, screening hundreds of thousands of indications of compromise to evaluate the data based on known attacks.
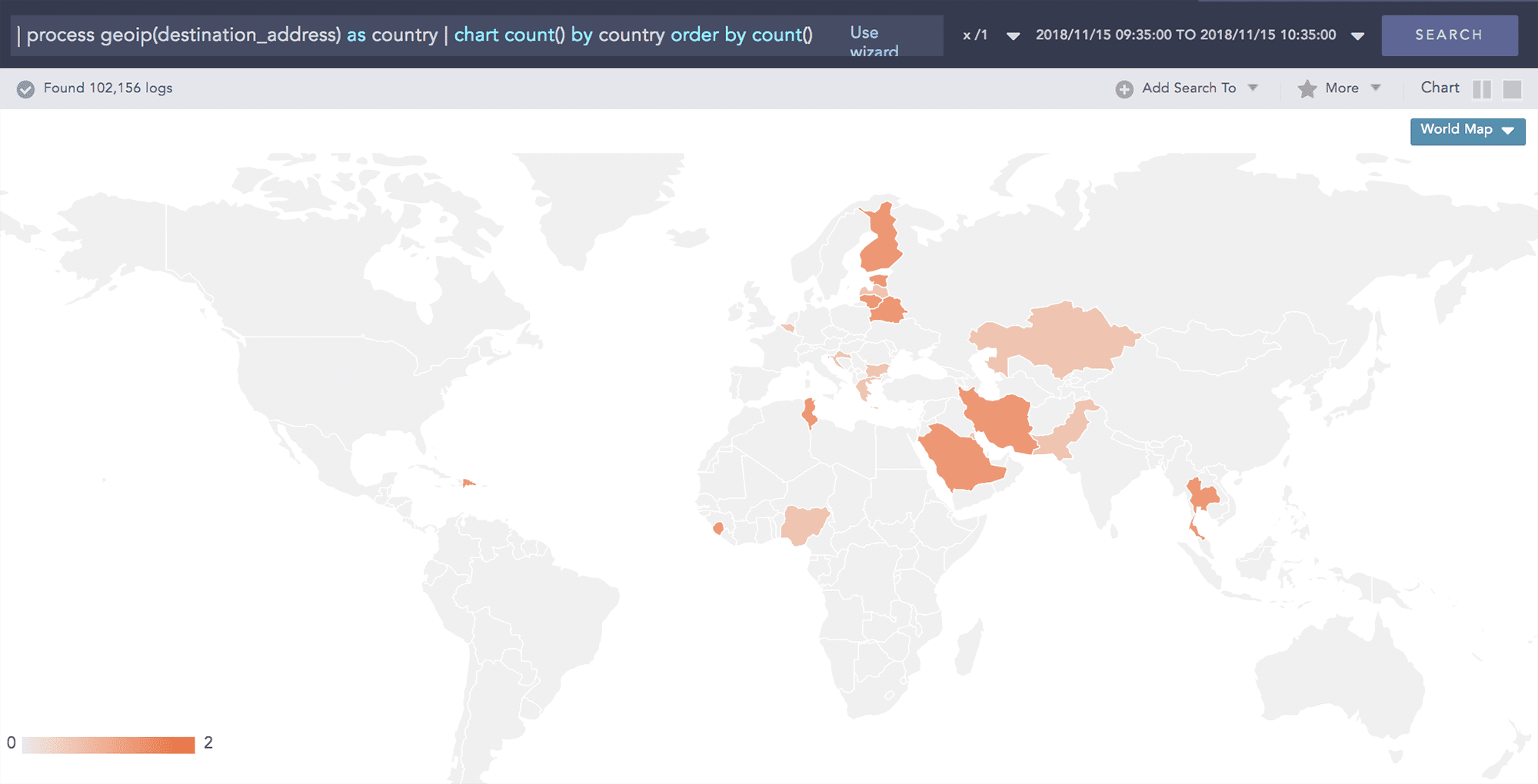
Based on the unique taxonomy for threat indicator scores, analysts can benefit from fully automated incident response mechanisms using queries for numerical comparison. Further they can understand the geographical distribution of the attack sources.
LogPoint provides full data-enrichment capabilities – which means gathered events can, for instance: raise alerts about a critical transaction in an ERP system, investigate if the user is authorized to conduct the operation in the HR system or raise alerts if a discrepancy is discovered. These capabilities increase performance and accuracy of analytics through ingest-time enrichment, without the need to import and fragment existing data.
LogPoint can help your IT operations run smoothly by delivering contextualised insights directly to your analysts. By measuring network traffic and using data comparisons, LogPoint can pinpoint when service degradation began. Comparing error messages with incidents in the network greatly reduces the time needed to resolve situations and run root-cause analyses.
With LogPoint’s SIEM tool, advanced threat detection is executed in real time and over long periods of time, allowing analysis and reporting of trends and behaviors of entities and users within the organization. LogPoint’s threat detection capabilities include enrichment with internal or external contextual information, such as threat intelligence, user names or temporal knowledge. This enables security analysts to operate faster and more efficiently.
Being an effective log management tool, LogPoint allows for basic security monitoring and is often used for compliance reporting and real-time monitoring of security controls. With flexible, convenient collection and storage of logs, LogPoint can accommodate your auditor’s needs – making compliance much easier.
LogPoint’s unique node-based pricing for SIEM, is straightforward and, unlike the models used by several competitors, encompasses all needed collectors, search and storage components. UEBA capabilities are available as an add-on, priced by users/nodes.
Scalability
Our product is built to scale. With images available for cloud deployments, virtual on-prem deployments and bare-metal, our customers can deliver security analytics to their teams regardless of their security strategy. We offer base licensing for servers through LogPoint’s Director Console to simplify network management and scaling. Customers that opt for UEBA can scale and gain value from the solution from day one.
LogPoint’s UEBA is built to leverage our unique taxonomy and delivered through the cloud. LogPoint further offers several pre-settings based on 400+ Use Cases, and organizations can thus orchestrate storage for LogPoint that is both cost effective and performance optimized.
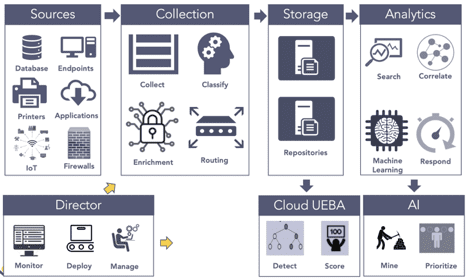
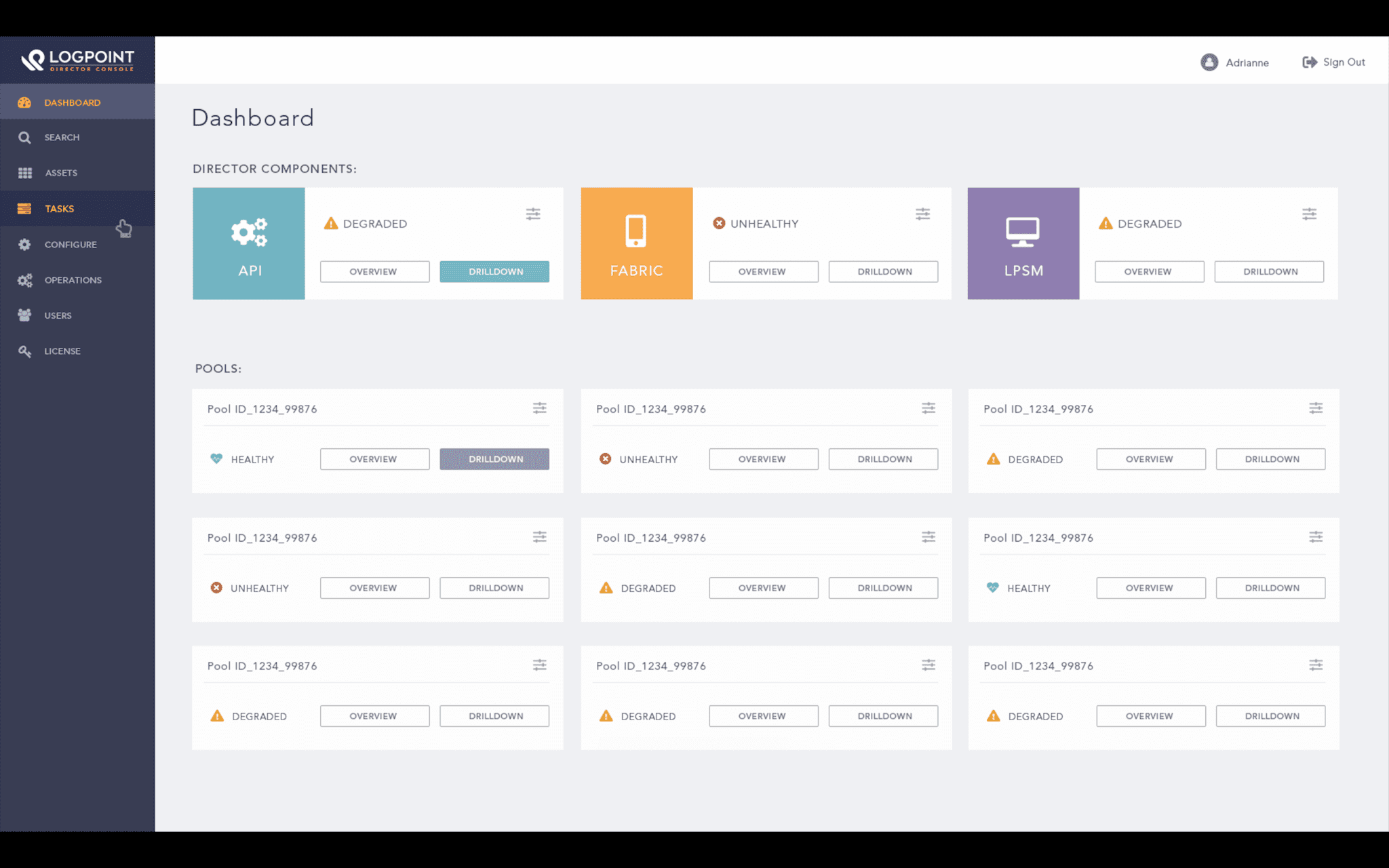
The LogPoint Director is designed for large scale and complex deployments of the LogPoint SIEM. This not only gives you the flexibility of centralized configuration and analytical capabilities but also preserves data privacy by maintaining physical isolation of system and data.
Support
Making our customers satisfied is our highest priority.
Our dedicated support team is prepared 24/7/365 to accommodate any request you might have. We go the extra mile to resolve your requests, with a satisfaction score of more than 97% on our support tickets. To ensure superior quality support, the LogPoint support team consist of certified, highly skilled engineers resulting in a decreased need of escalation and therefore faster than ever resolution.
Easy to implement and turn into something useful
Easy to use; deep protection capability; great pricing model
Vendor always willing to help. Excellent support. Our requirements are met when we have special needs
Software easy to use. Strong support of Logpoint. Customer needs oriented, additional features asked have been provided
Gartner, Magic Quadrant for Security Information and Event Management, Kelly Kavanagh, Toby Bussa, Gorka Sadowski, 3 December 2018.
Gartner, Critical Capabilities for Security Information and Event Management, Toby Bussa, Kelly Kavanagh, Gorka Sadowski, 3 December 2018
Gartner Peer Insights ‘Voice of the Customer’: Security Information and Event Management Market, Peer Contributors, 27 September 2018.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. Gartner Peer Insights reviews constitute the subjective opinions of individual end-users based on their own experiences, and do not represent the views of Gartner or its affiliates.
The Gartner Peer Insights Logo is a trademark and service mark of Gartner, Inc., and/or its affiliates, and is used herein with permission. All rights reserved.


![[🇫🇷 WEBINAIRE A LA DEMANDE] – Logpoint pour les centres hospitaliers](https://www.logpoint.com/wp-content/uploads/2025/05/logpoint-santexpo-2025-500x383.webp)

![[🇫🇷 WEBINAIRE] – Je découvre Logpoint après Forum InCyber 2025](https://www.logpoint.com/wp-content/uploads/2025/03/webinaire-forum-incyber-2025-500x383.jpg)

