Ransomware is doubtless a rising threat nowadays, putting all small, medium-sized and large businesses at risk. Our IT and security professionals at LogPoint are constantly working to help our clients withstand such attacks. When fighting ransomware, planning and forethought are crucial so you can limit the impact and quickly recover with minimal disruption. Keep in mind that ransomware variants are constantly changing, and it’s hard to thwart every attack without the help of a real power tool. After all it’s better to be safe than sorry.
The queries and examples used, assumes the environment relies on an EMC backend but works for every kind of storage solution.
Objective
Acquisition of unusual data activity on storage systems within a certain period of time often indicates ransomware activities. With the help of ransomware detection, the organization receives an alarm via email each time suspicious activity is detected. There is a wide variety of suspicious activities, however, the cases when data is deleted, created, or modified in high volumes should always be a warning sign.
Dashboards
The dashboard represents the top 30 users, that showed the highest activity during the past 10 minutes:
Query: label=EMC userSid=*|rename userSid as objectSid| chart count() by objectSid order by count() DESC limit 30| process lookup (LDAP,objectSid)|fields displayName, sAMAccountName, objectSid, count()
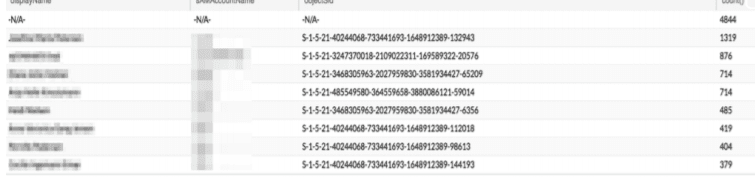
Paths, that generate high volumes of data activity by nature (e.g.: Citrix or Xen) are excluded from the search so they cannot distort the results.
Additionally, there is a list called Whitelist which consists of reliable users. The list is auto-generated based on UserSID. Furthermore, there is an in-house scale containing “normal” data activity so the system can capture any activity deviating from that.
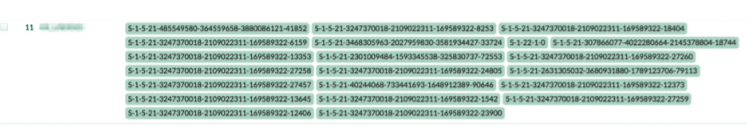
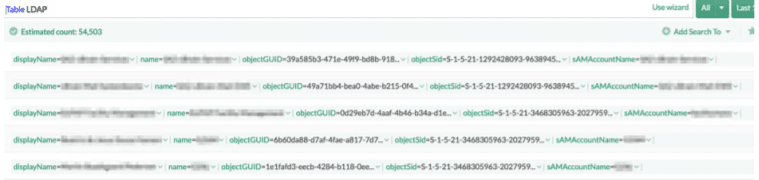
Users are assigned to userSIDs by matching with Active Directory. The results are stored in a table from where, data can be permanently used for further analysis.
Alarming
Query: label=EMC -“bytesWritten”=”0” -“bytesWritten”=”0x0″ event=”0x80” flag=0x2 userSid=*| chart count() as handle by userSid, clientIP | search handle>200
The alarm is triggered and an e-mail is sent to the person in charge, whenever a suspicious data activity, effecting more than 200 files (in-house baseline) is detected. Paths and applications which are labelled as trustworthy are excluded from this rule.
While this is just scratching the surface of how we can fight ransomware at LogPoint, this use case can serve as a great starting point for further discussions about the next steps to take in order to protect your organization.


![[🇫🇷 WEBINAIRE A LA DEMANDE] – Logpoint pour les centres hospitaliers](https://www.logpoint.com/wp-content/uploads/2025/05/logpoint-santexpo-2025-500x383.webp)

![[🇫🇷 WEBINAIRE] – Je découvre Logpoint après Forum InCyber 2025](https://www.logpoint.com/wp-content/uploads/2025/03/webinaire-forum-incyber-2025-500x383.jpg)

