GDPR compliance
GDPR, short for General Data Protection Regulation is Europe’s unified data protection framework which applies to any EU or non-EU organization processing personal data of individuals based in the EU. The increased data security requirements of GDPR mean that businesses have to seriously consider how to ensure compliance as the effects of non-compliance can lead to severe financial penalties. These penalties will be determined based on the extent of the data leakage, and a two-tiered sanctions system will apply. But there’s good news. Meeting the strict GDPR requirements is a lot easier with LogPoint’s out-of-the-box GDPR features for compliance monitoring and reporting.
Reporting and Audit
LogPoint offers an extensive range of pre-defined GDPR reports right out-of-the-box providing you with critical insight into how your network is performing. This information will help ensure confidentiality, integrity, and availability of your systems by monitoring your assets containing Personally Identifiable Information (PII) and allowing for the business investigation into data loss.
LogPoint currently offers the following out-of-the-box GDPR compliance reports:
Data Privacy
LogPoint’s Data Privacy Module functions under the Four Eyes Principle meaning that at least two users are required to handle critical information in an organization at all times. LogPoint by design supports the data privacy mode on normalized fields, meaning that data privacy enabled fields can’t be displayed unless access is granted by a third user. This way, we place the control back to your hands so you can:
- Grant administrative rights to deny or allow access to an obfuscated field, without the admin user viewing the data themselves
- Allow users to request access to an obfuscated field
- Limit access to the field to a predefined time range, after which the data is once again inaccessible to the user
- Document the entire process from request, hence helping you to implement Access Control mechanisms and support audit
Spotting and tracking unauthorized network or systems access
LogPoint enables you to detect any suspicious and/or unauthorized network behavior such as connection attempts on closed ports, blocked internal connections, connections made to known-bad destinations, requests initiated from untrusted zones, suspicious system access and many more.
Example: Threats in higher privilege systems
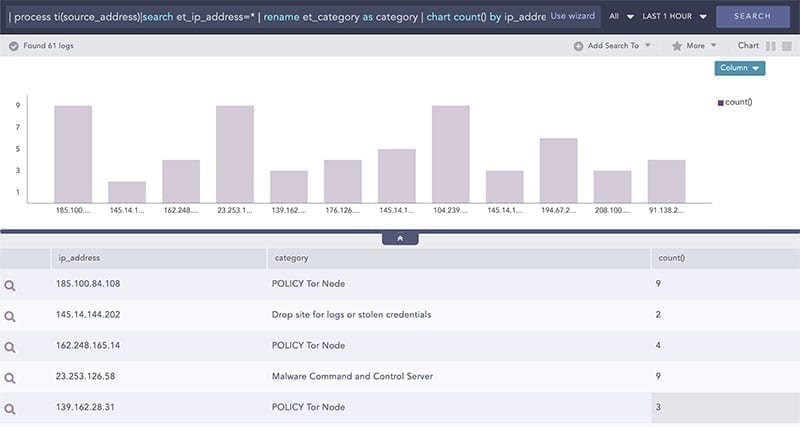
Log sources: Firewall, Threat Intelligence
Query
label=Connection label=Allow source_address IN PRIVILIGE_SYSTEMS | process ti(source_address)|search et_ip_address=* | rename et_category as category | chart count() by ip_address, category order by count() descMonitoring international data transfers
LogPoint’s intuitive visualization helps to plot data points for connection requests across the geopolitical boundaries. With an overview of top destination and source countries along with top inbound/outbound connections, LogPoint provides any organization with a detailed overview of cross-border data flow, ensuring lawful data transfer complying with the GDPR.
Example: Trend of outbound data transfer by geo location
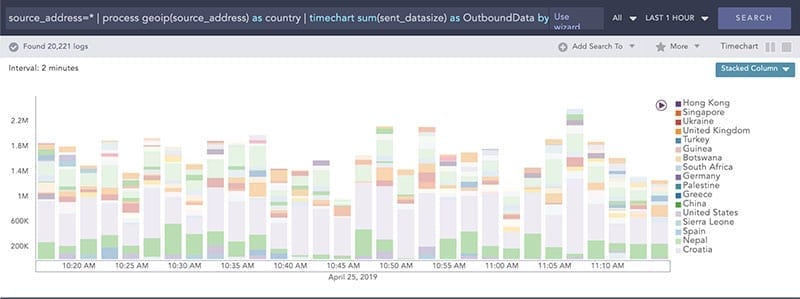
Log sources: Firewall, Geo IP process plugin
Query
source_address=* destination_address=* | process geoip(destination_address) as country | timechart sum(sent_datasize) as OutboundData by countryEnrich and route logs with sensitive data to secure repositories
Users in LogPoint by design can specify different routing policies based on different routing criteria like the type of the event, the operation to be carried out, or the specified repository. This data based on its purpose and usage can then be routed and stored in different repositories using the key-value based filters.
