By Ivan Vinogradov, Solution Architect, LogPoint
The Sandworm Team, a group of known threat actors, have exploited a vulnerability in the Exim Mail Transfer Agent. Associated with the Russian GRU agency since August 2019, Sandworm introduced the vulnerability CVE-2019-10149 in version 4.87 of the Exim software.
Organizations can mitigate the vulnerability by implementing the appropriate patches, and overall, is not a significant concern if a healthy patching policy is in place. Since threat actors typically use one vulnerability as a pivot to accomplish other objectives, we will also cover the detection of relevant vulnerabilities.
Initial exploitation
The most basic way to detect the exploit in LogPoint is a query that looks for characteristic artifacts in an SMPT message. NSA recommends that the query should be an SMTP recipient field containing the combination ${run. Thus, we can imagine the most basic query being something along the lines of:
norm_id=* sender=* receiver="*${run*"
Indicators of compromise (IOCs)
Unfortunately, the current knowledge of the IOCs relating to Sandworm is limited. However, monitoring for these IOCs would reduce your risk considerably, at least until there is a better understanding of Sandworm. So far, two IPs have been associated with Sandworm that we can use in a query:source_address IN [95.216.13.196, 103.94.157.5]
Furthermore, one can use the known domain ‘hostapp[.]be’(sanitized) to run a simple search to look for the attack, for example:norm_id=Exim domain=hostapp.be
Analysts can further drill down into the query, for example, if there are multiple devices, it could be an option to replace the query with something like:label=SMTP hostapp.be
The query can be further improved based on the fact that hostapp[.]be tends to feature as the sender domain in the exploit:label = SMPT sender = *hostapp.be*
The solution requires that you have the Unix support package for LogPoint and have the relevant logs enabled – most importantly Mail Server, SSH and Command Line. The package includes a set of Linux log parsing tools. There is a wide range of solutions you can apply here by using LogPoint queries – but it depends on your Linux audit settings.
Post-exploitation
As mentioned in the NSA document, certain activities typically follow exploitation:
- Adding privileged users
- Disabling network security settings
- SSH changes
- Script execution
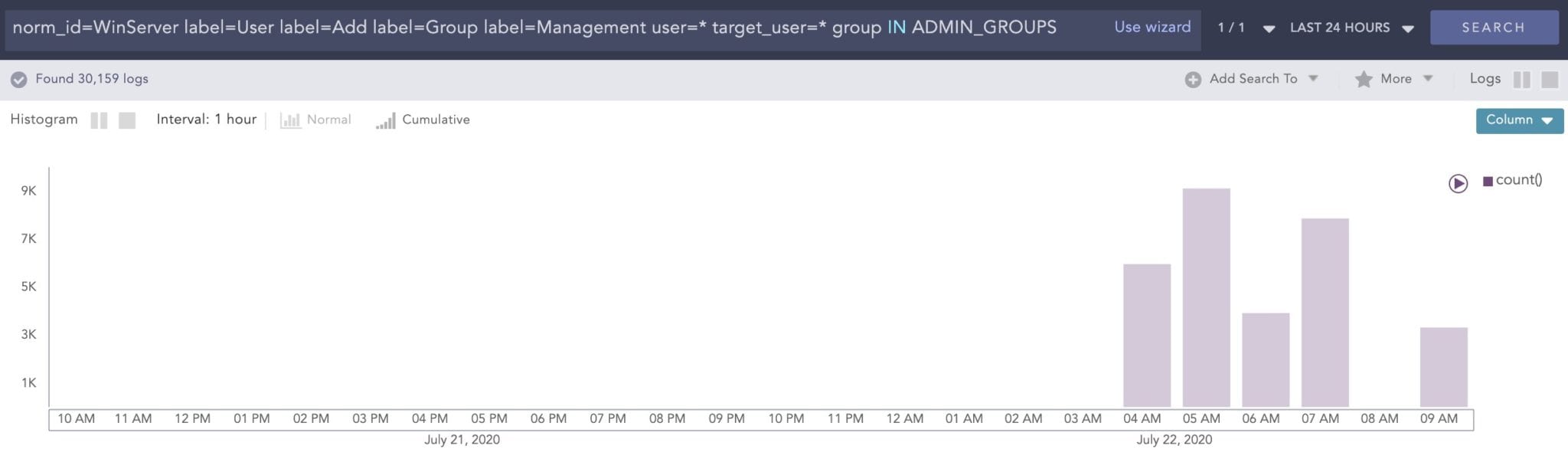
Depending on your environment, there are different ways to approach post-exploitation. In general, analysts can use the query labels such as “User” and “Add” as a wide-net detection method. For example:norm_id=WinServer label=User label=Add label=Group label=Management user=* target_user=* group IN ADMIN_GROUPS
The query is very inclusive, but it is especially useful if you have a timeframe in mind. You can use the graphical elements within the search interface to quickly see the increase in activity:
In conclusion
There is no replacement for a mature and proactive set of security policies, especially when it comes to keeping software up to date. However, one of the aims we have here at LogPoint is to optimize our solution’s potential when it comes to lowering risk, increasing transparency, and assisting mitigation – even when you may not have all the needed resources available.






