UEBA: Detect Insider and Unknown Threats Quickly.
Accelerate detection and response to threats by spotting early signs of suspicious patterns and anomalous behavior with advanced User and Entity Behavior Analytics.
Get in-depth analysis on suspicious successful or failed logins, brute-force attacks, abnormal use of or first-time access to programs, transactions, and systems, plus unusual patterns in the overall activity of users.

Identify Threat Patterns Early to
Effectively Mitigate Risks
Advanced attacks and pervasive threats to your organization often rely on compromised credentials or coercing users into performing actions that damage enterprise security. To identify such attacks, you need a robust solution that enables analysts to detect abnormal activity on your network.
Converged SIEM helps you enhance investigation of unusual behavioral patterns while reducing time spent on threat hunting. Mitigate risk, damage, and data loss by detecting advanced attacks early by adding user and entity behavior analytics to your security platform.
Improved Detection
Speed up detection of incidents in your network – Converged SIEM does the heavy lifting, analyzes raw data, and enables seamless forensics to ease root cause analysis.
Spot Insider Threats
Thanks to machine learning, Converged SIEM creates baselines of normal user and entity behavior, triggering alerts whenever anything is out of the ordinary: in the cloud, on–premises, and inside business applications.
Thorough Investigations
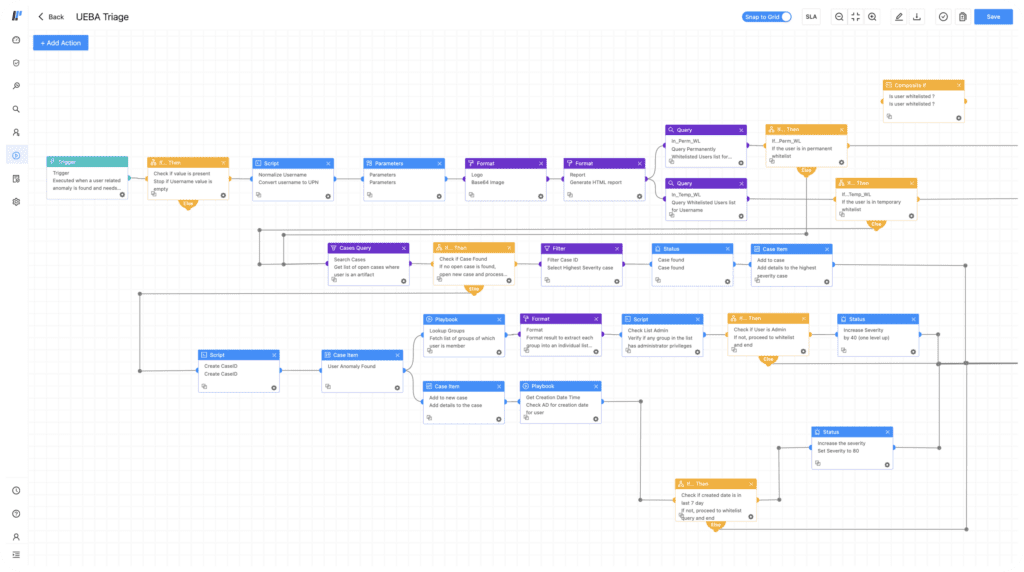
Enrich alerts with threat intel, business context, and entity risk to transform them into relevant investigations. Automate your investigation with playbooks to leave no stone unturned.
Faster Response
Limit the impact of a breach by reducing the time to respond. Out-of-the-box playbooks help rapidly investigate, contain, and remove cyber threats with automation.
From a Single Pane of Glass
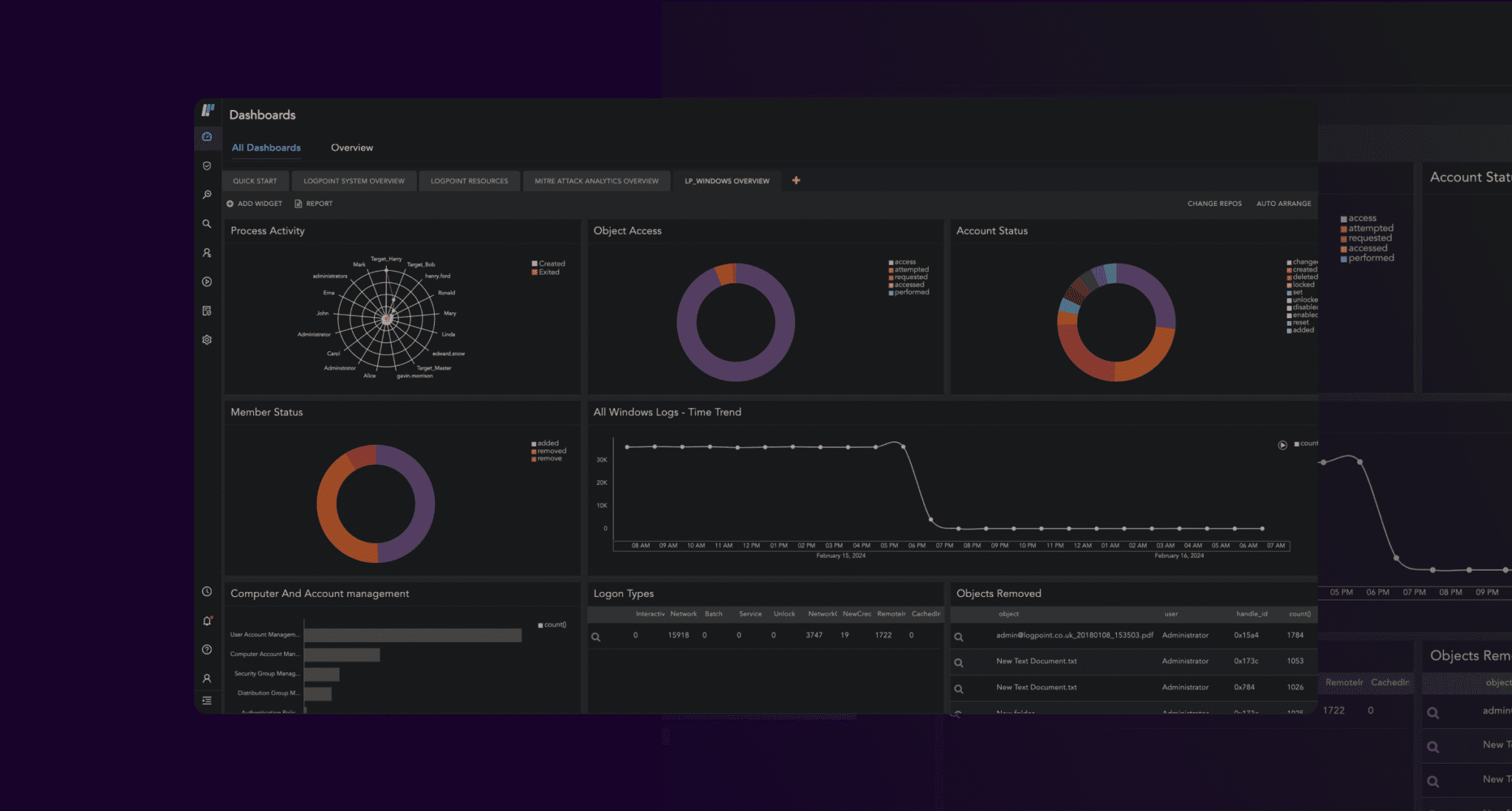
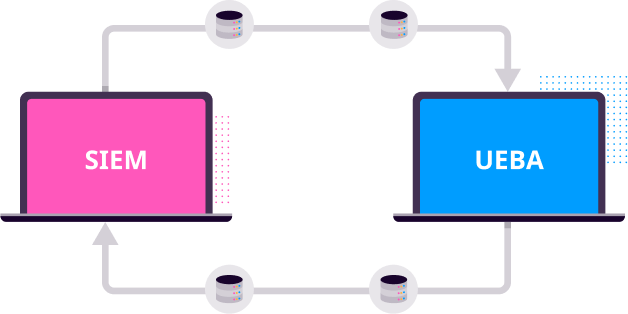
Collect and analyze logs, detect and prioritize security incidents, and respond to threats from outside and inside the organization. Combining SIEM, SOAR, and UEBA gives you all you need on one platform.
Consolidate Your Tech Stack
As all products are built on the same platform, UEBA seamlessly integrates with SIEM and SOAR, allowing them to power each other. This gives automated end-to-end security while reducing the total cost of ownership.
The UEBA module in Converged SIEM Provides you with
Comprehensive Insights and Maximizes the Value of your Data.
Enriching Your SIEM Data
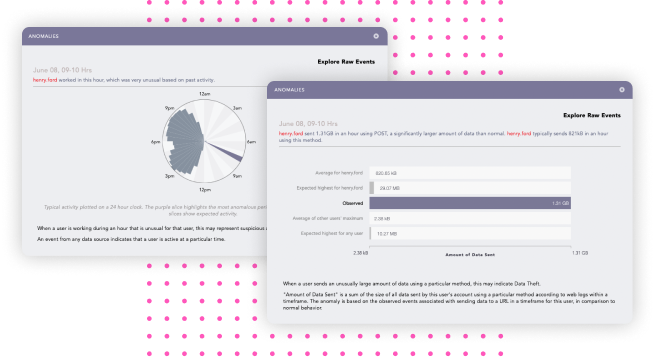
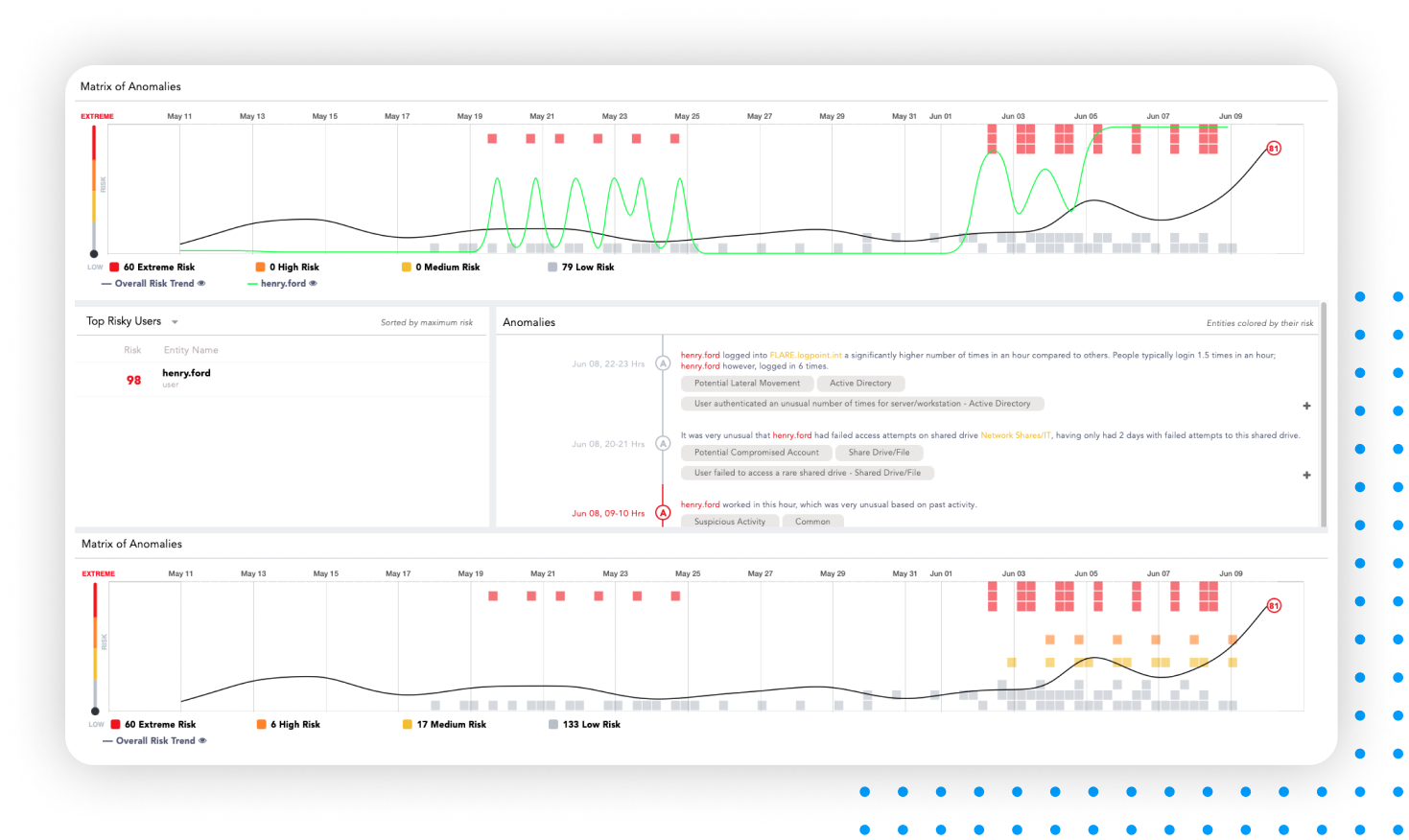
Correlating the data from UEBA with SIEM events makes the original events more insightful than ever. The original log data can be enriched using the information from UEBA’s machine learning technology, enabling you to discover suspicious user behavior. Incidents can be visualized using dashboards and search templates for faster threat hunting.
Spot Malicious Activities Early
UEBA builds baselines for normal behavior for every user, peer group, and entity in the network instead of applying predefined rules for standard behavior. By identifying deviations, UEBA detects anomalous patterns early, which are not necessarily immediately obvious and therefore often go unnoticed.
Faster and Efficient Investigation
UEBA calculates risk scores and prioritizes high-fidelity incidents. The closer the score is to 100, the riskier the behavior. Along with shorter detection times, UEBA provides more actionable evidence during investigations and higher efficacy and accuracy of the alerts and incidents generated.
Automate Your Response
Because it’s built on the same platform, UEBA is fully integrated with the automation capabilities of Converged SIEM, allowing to set up automated response processes. This improves efficiency so SOC teams can work smarter and focus on threats that matter.
As soon as UEBA detects suspicious activity in a user, Converged SIEM will create an incident. Thanks to the integration between UEBA and SOAR, it can automate the triage, check if the users are whitelisted, and block them in case of a possible threat.
Insider Threats
Insider threats are usually detected by spotting behavior that deviates from the standard baseline.
Malicious Insiders
Probably the best known and most publicized category of insider threats. These are typically entities who take advantage of their privileged access to the organization’s resources to inflict some form of harm on the organization.
Negligent Insiders
Entities who fail to practice security, follow regulations and standards, etc., or users who choose to ignore them. Often, these are unknowing, for example, if an employee misplaces their device with access to critical information or doesn’t install security updates because the company’s security policies have not been articulated. This can open the door to infiltrators, who intentionally gain insider access.

External threats
External threats are best detected by deviations in user and entity behavioral patterns. They are often a consequence of negligent insiders. If an account is being compromised, the chances are that the behavior will differ from standard baseline, such as transfer abnormal amounts of data or accessing files that they don’t normally have access to. Without UEBA, these are not easy to uncover, as they use legitimate credentials, acquired by brute force attacks or stealing.
Compromised Accounts
Compromised accounts are the result of outsiders who have gained access to an insider’s account by stealing their credentials. This often happens through phishing, when the outsider lures an employee to click on a link or open an email attachment that contains a virus.
Advanced Persistent Threats
An adversary gains unauthorized access to a computer network and remains undetected for an extended period. Once they have infiltrated the network, they will try to create backdoors, so it’s crucial to monitor any abnormal behavior in users and entities.

MITRE ATT&CK
All UEBA anomalies are mapped to the MITRE ATT&CK framework, an industry-standard classification of adversarial tactics and techniques based on real-world observations of different cyberattacks.
Logpoint UEBA matches the machine learning algorithms to actual practical scenarios rather than non-cohesive, singular items of interest. Tight integration with MITRE means analysts quickly get an overview of the threat landscape and can easily track the stages of an attack. Combined with risk scoring, the MITRE tags on anomalies help analysts prioritize their investigation and focus on the most critical incidents.
Watch our Webinar
Get insights on frequently asked questions about adding Logpoint UEBA to SIEM.
We discuss the following topics:
- The value that UEBA will bring to your current IT setup and infrastructure
- The pain points that a machine learning UEBA solution will address in your organization
- How easy is it to use and integrate with SIEM
- UEBA anomalies mapped to the MITRE ATT&CK framework
Converged SIEM
Looking to consolidate your tech stack? See how UEBA fits with SIEM, SOAR, and more. Converged SIEM helps SOC teams combine data sets from multiple sources. Instead of using multiple standalone products, they now have one single source of truth. It is the only unified platform that delivers SIEM+SOAR, UEBA, EDR capabilities and security monitoring of SAP for both enterprises and MSSPs.
- Full data integration for automated TDIR
- No integration or maintenance required
- Out-of-the-box compliance support
- Flexible deployment based on your needs