Security and Compliance Audit Monitoring
Boost your SAP security & effectively respond to threats
Attacks on SAP systems are rising in frequency, sophistication, and severity. A successful breach can easily paralyze an entire organization, leak confidential information, undermine your brand authority and lead to substantial financial losses.
Use Case: Secure your Intellectual
Property Against Theft and Misuse

SAP systems store your intellectual property and govern your business secrets. A security breach to your business-critical data can have devastating consequences, crippling your competitive advantage, and threatening the entire existence of your business. Securing your SAP system against exposure is pivotal to safeguarding the foundation of your business.

Theft of confidential product information
Product Lifecycle Management stores product-specific information, technical details, and even an overview of all components comprising a product. For example, an airplane manufacturer’s details regarding their newly introduced airplane were illegally accessed and downloaded on a USB stick. If leaked or shared with competitors, this could easily have jeopardized years of research, compromised their competitive edge, and lead to unpreceded losses.
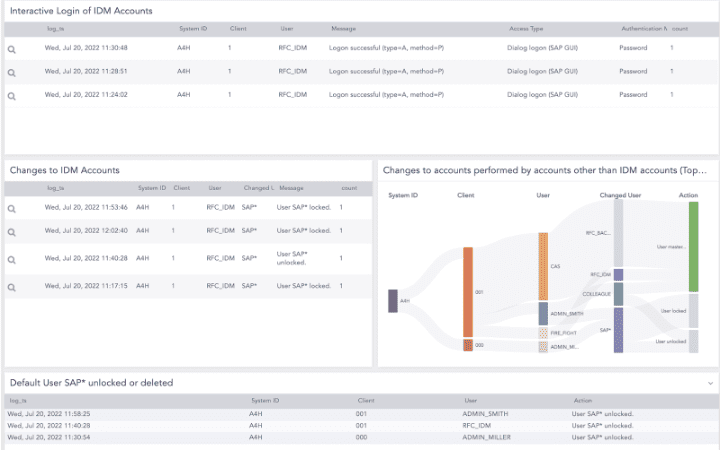
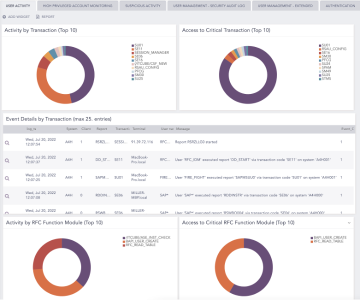
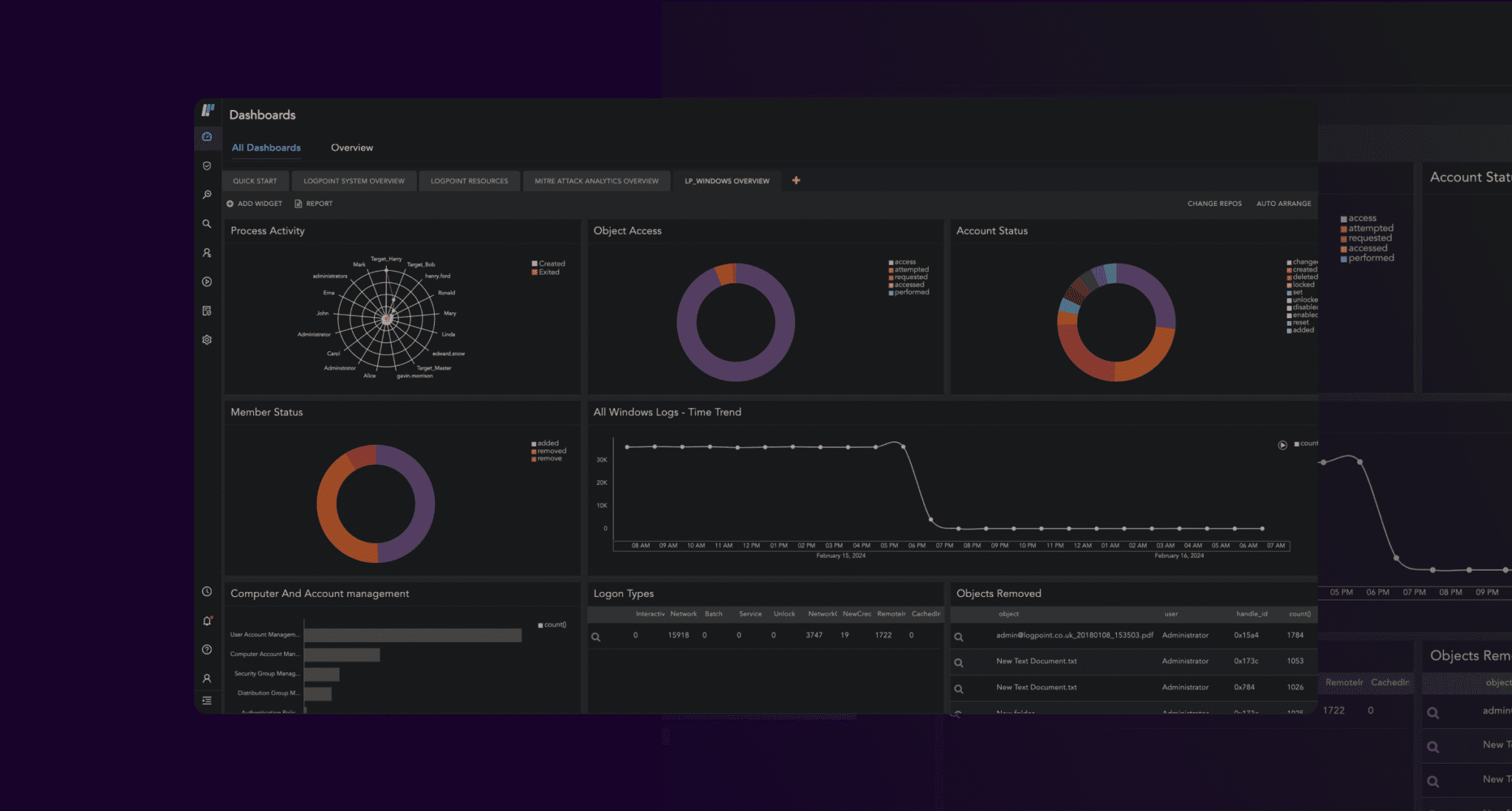
We provide monitoring and end-to-end security for your SAP system in correlation with the wider IT network, in real-time. With pre-defined alert rules and comprehensive monitoring of your logs, access controls, and changes to accounts, we can automatically detect and flag suspicious activity, so you quickly can put an end to malicious acts.
Securing your SAP system is the first step in protecting your business from existential threats.