ToolShell: When SharePoint Becomes a Gateway to RCE
By Ujwal Thapa and Anish Bogati; Security Research
Microsoft’s Security Response Center (MSRC) confirmed active exploitation of CVE‑2025‑53770 (dubbed “ToolShell”), a zero-day remote code execution vulnerability affecting on-premises SharePoint Server versions 2016, 2019, and Subscription Edition. Threat actors are actively exploiting this vulnerability by chaining with CVE‑2025‑53771 (path traversal vulnerability) to deploy web shells, exfiltrate cryptographic keys, and establish persistent access. Organizations are strongly advised to apply emergency patches, rotate keys, enable AMSI protections, and isolate exposed servers immediately.

Background
Microsoft confirmed active exploitation of ToolShell (CVE‑2025‑53770) after initial identification by security researcher Khoa Dinh (@_l0gg). SentinelOne observed in-the-wild exploitation activity as early as July 17, 2025 prior to Microsoft's official advisory. The attackers have been chaining this vulnerability with previously patched flaws, CVE-2025-49704 and CVE-2025-49706, both of which were addressed in the July 8 Patch Tuesday release, with public PoC code emerging by July 14.
In addition to the technical exploitation, Microsoft has attributed the attacks to two named Chinese nation-state actors: Linen Typhoon and Violet Typhoon. Additionally, another Chinese threat actor, Storm-2603, has also been linked to active exploitation. These groups have been targeting internet-exposed SharePoint servers, with confirmed compromises affecting a wide range of sectors including government agencies, critical infrastructure, universities, and private enterprises worldwide.
CVE Details
| CVE | CVSS v3.1 | Vector String |
|---|---|---|
| CVE‑2025‑53770 | 9.8–Critical | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:F/RL:W/RCC:C |
| CVE-2025-53771 | 7.1 - High | CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:L/A:N/E:P/RL:O/RC:C |
Current situation: Exploited in the wild, POC not available as of publication.
Affected Versions
Check out Microsoft Customer Guidance or CVE for updated information.
| Product Name | Version | Build/Edition | Platform |
|---|---|---|---|
| Microsoft SharePoint Enterprise Server 2016 | Affected from 16.0.0 before 16.0.5513.1001 | Enterprise Server 2016 | x64-based Systems |
| Microsoft SharePoint Server 2019 | Affected from 16.0.0 before 16.0.10417.20037 | Server 2019 | x64-based Systems |
| Microsoft SharePoint Server Subscription Edition | Affected from 16.0.0 before 16.0.18526.20508 | Subscription Edition | x64-based Systems |
Detecting CVE-2025-53770 with Logpoint
Log Sources Needed
For the hunting queries to work, you must ensure you have the appropriate event logs from specified sources. Some logs are logged by default, while others may need to be manually configured. The following log sources are required for effective detection.
-
Windows
-
Windows Sysmon
-
-
Firewall
-
IDS/IPS
Exploitation attempt
This vulnerability can be triggered by sending a specially crafted POST request to /layouts/15/ToolPane.aspx?DisplayMode=Edit. Attackers exploit a validation logic flaw in the Referer header, allowing unauthorized command execution. To detect exploitation attempts, monitor your web logs specifically for POST requests targeting this endpoint.
Post-Exploitation
Following exploitations, attackers have launched commands through their custom payloads, initiating a chain of processes. The common sequence involves the w3wp.exe web process spawning a command shell (cmd.exe) that subsequently executes PowerShell (powershell.exe) with encoded arguments. Detect this suspicious process flow by monitoring process creations originating from w3wp.exe:
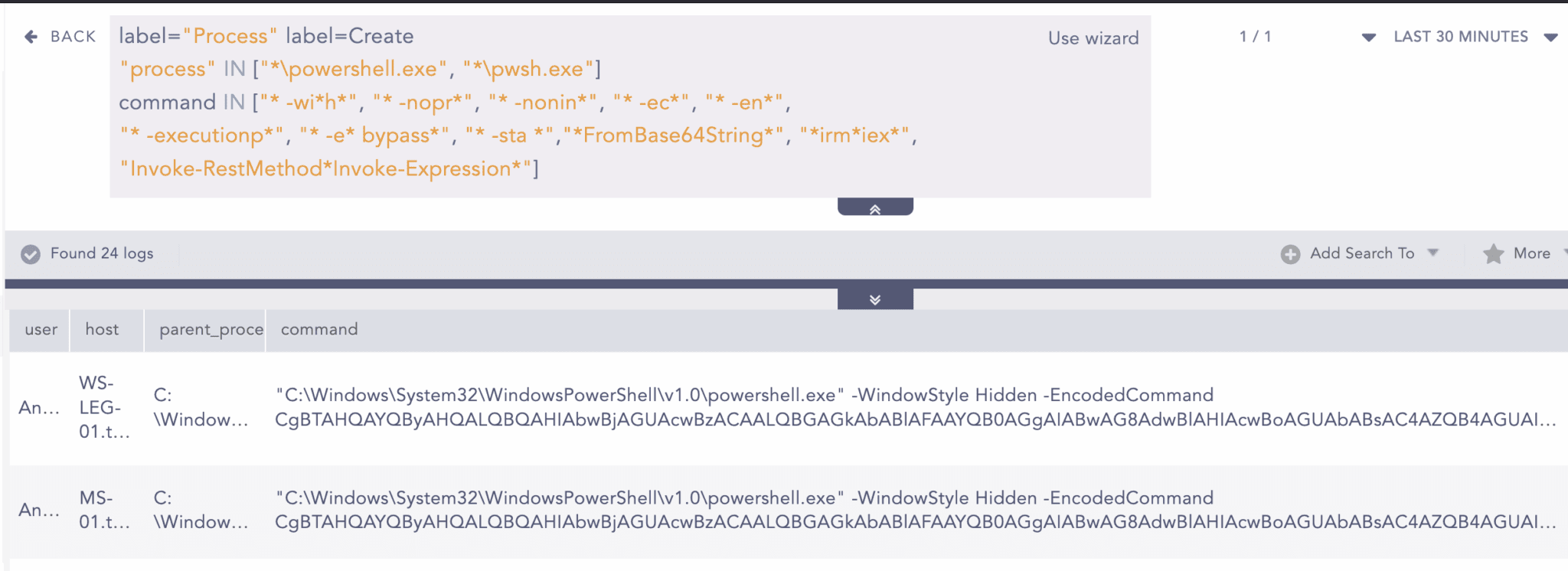
Suspicious PowerShell Parameter Substring Detected:
As discussed earlier, attackers frequently execute obfuscated or encoded PowerShell commands to conceal their activities. You can detect such suspicious activities using the following query:
Indicators of Compromise (IOC)
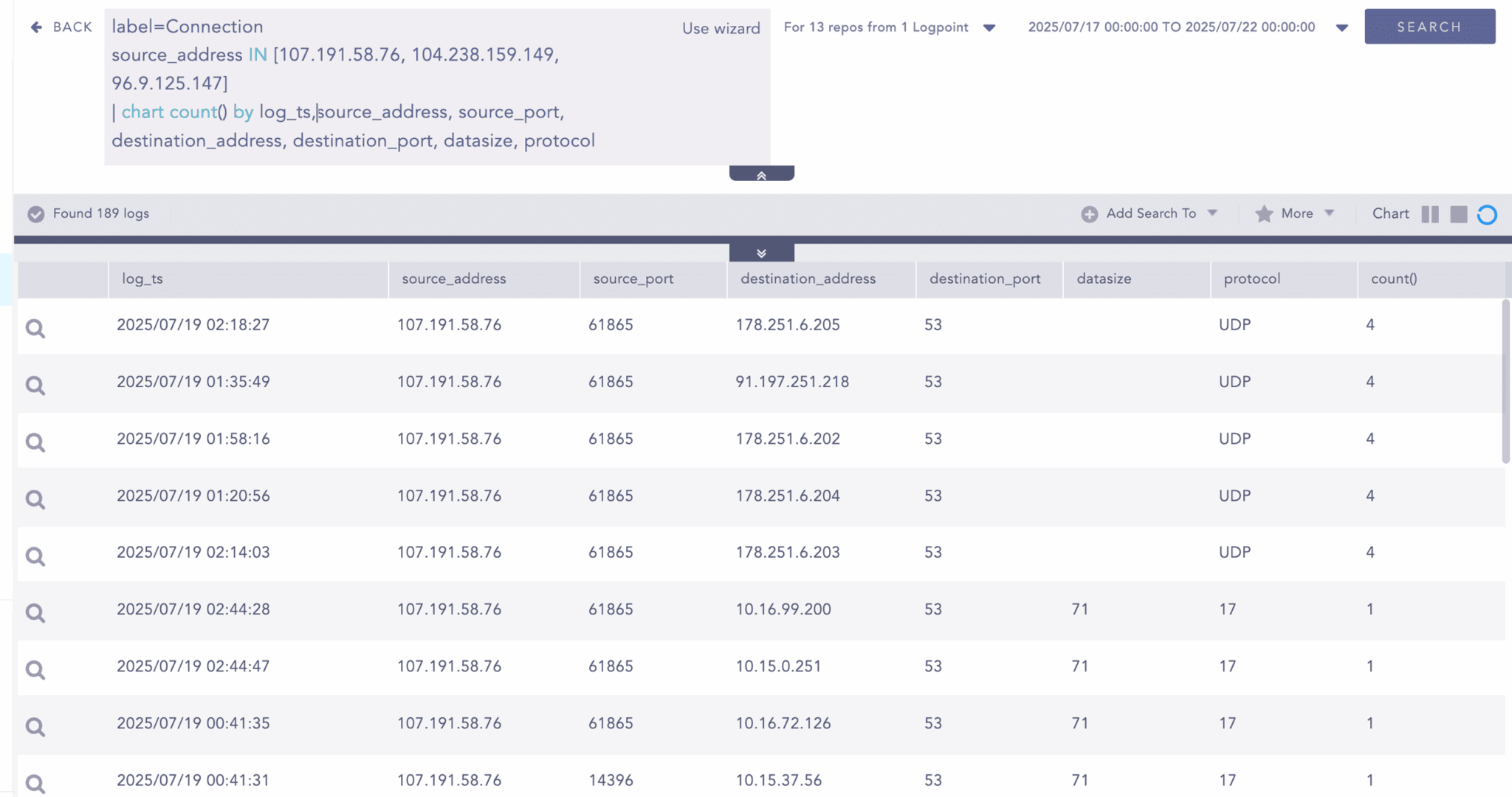
Network Scanning Attempts
Attackers have been observed performing initial reconnaissance scans to identify vulnerable SharePoint servers. According to CISA's advisory, threat actors actively conducted network scans from the IP addresses 107.191.58[.]76, 104.238.159[.]149, and 96.9.125[.]147 between July 18-19, 2025. The following hunting query will help detect network connections originating from these suspicious IP addresses.
Further Suspicious IP Addresses
Additional IP addresses linked to exploitation activity have been identified by Unit42. Include these IP addresses in your detection mechanisms to extend threat hunting coverage.
Observed User-Agent Strings
Malicious requests frequently use distinctive or spoofed User-Agent strings, as noted by Rapid7. Monitoring and identifying these unusual User-Agent strings can effectively highlight potential exploitation activities in your environment.
Webshell File Drop
Monitor SharePoint and Windows logs for suspicious file creations or downloads, especially files indicative of webshell deployments such as spinstall0.aspx.
Suspicious File Hashes
Unit42 has identified malicious payloads associated with recent attacks, sharing specific file hashes as Indicators of Compromise (IOCs). To detect the presence of these malicious payloads in your environment, use the following query:
Investigation and Response Using Logpoint
Modern security operations demand more than just alerting; they require context, automation, and precision. Logpoint delivers a comprehensive security platform that brings together SIEM, SOAR, threat intelligence, and endpoint telemetry. These capabilities empower defenders to quickly investigate threats, contain malicious activity, and respond with confidence.
CVE-2025-53770 is a critical vulnerability affecting Microsoft SharePoint. It allows attackers to bypass authentication and exploit the ToolPane.aspx endpoint to upload malicious .aspx files. By forging __VIEWSTATE payloads using extracted cryptographic keys, adversaries can achieve unauthenticated remote code execution (RCE), enabling web shell deployment, credential theft, and lateral movement across the network.
Given the strategic role SharePoint plays in business operations, timely investigation and containment are crucial. With Logpoint’s integrated SOAR playbooks, AgentX telemetry, and Osquery insights, security teams can coordinate swift detection, response, and remediation to neutralize threats before they escalate.
Osquery Investigate Host - Main Incident
This playbook utilizes Osquery to provide analysts a live, system-level view of the targeted SharePoint host. It’s especially effective during early investigation, helping to uncover abnormal processes like spinstall0.aspx, detect EDR or antivirus tampering, and verify the health of key SharePoint services and scheduled tasks.
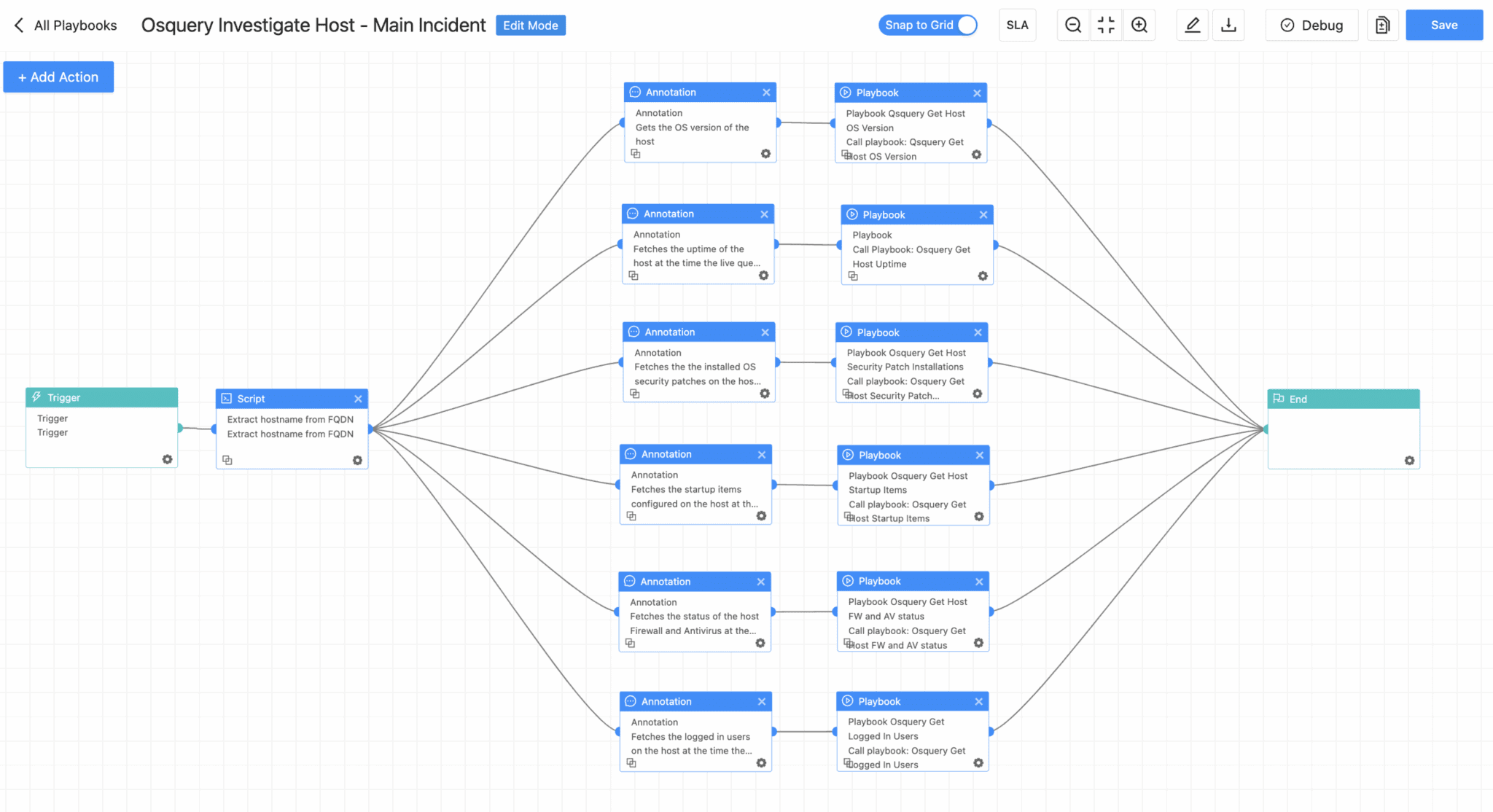
Osquery Investigate Host - Main Incident
Logpoint AgentX Process Dump
This playbook captures a real-time snapshot of all active processes on the affected SharePoint server, critical when exploitation is suspected but not yet confirmed. It is especially useful in the early compromise stage, helping analysts analyze potential in-memory payloads or obfuscated ViewState decoders that evade file-based detection. Reviewing these process dumps enables a deeper forensic understanding of what was executed.
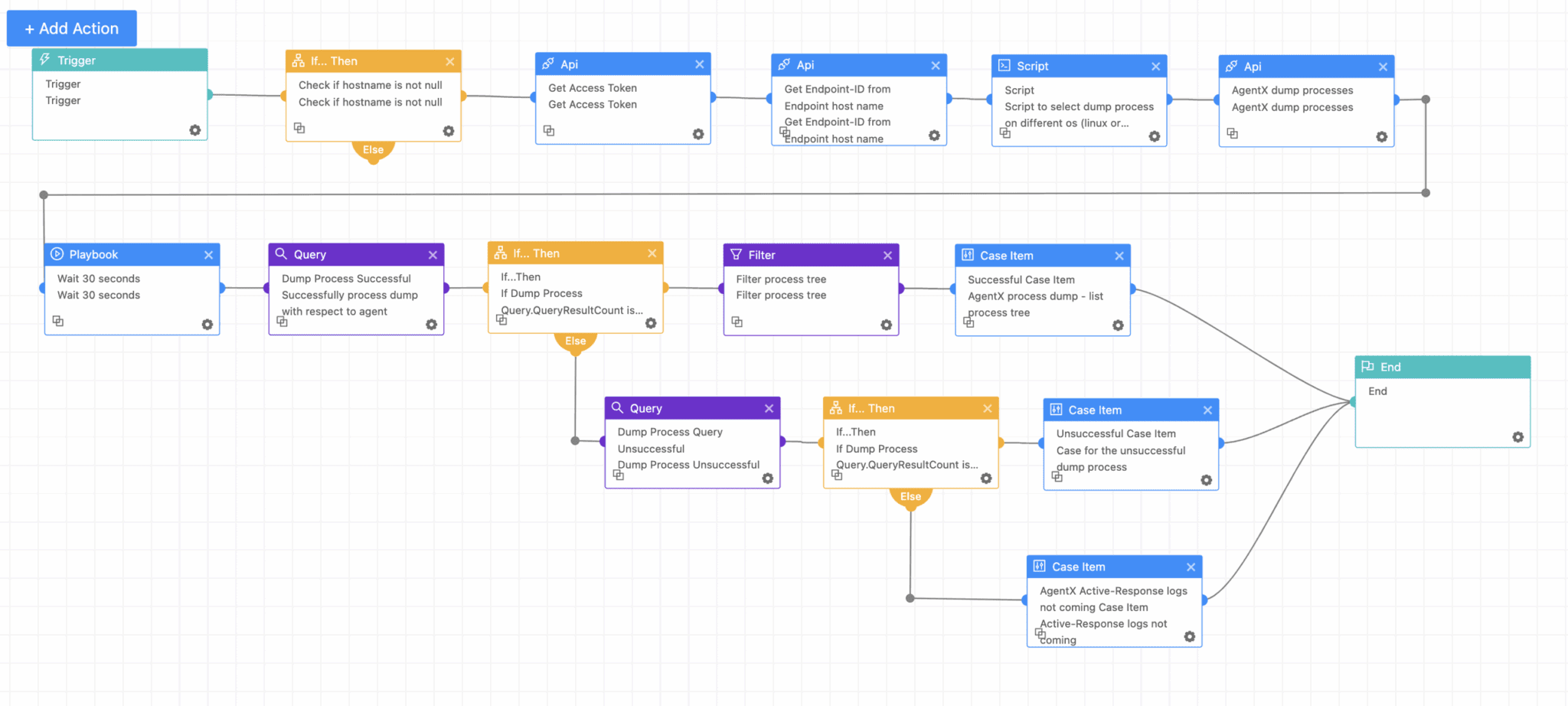
Logpoint AgentX Process Dump
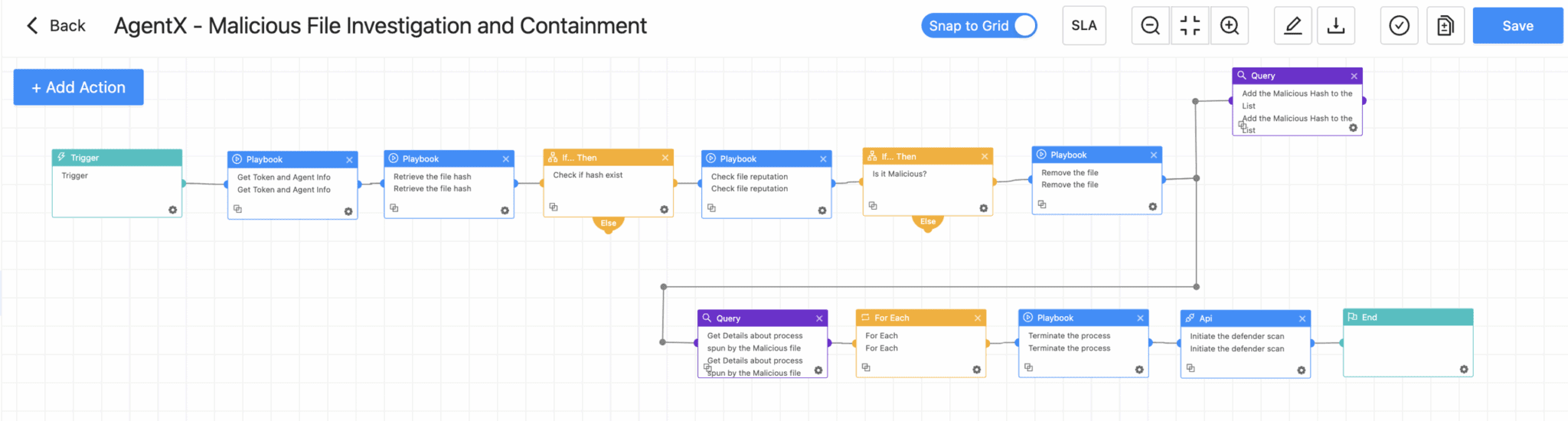
AgentX - Malicious File Investigation and Containment
This playbook enables analysts to trace and remove malicious files, like spinstall0.aspx, from SharePoint’s LAYOUTS directory by verifying file hashes, terminating associated processes, and eliminating threats identified during exploitation.
AgentX Remove Item
After detecting a threat like spinstall0.aspx, this playbook gives analysts the ability to swiftly remove malicious artifacts from critical directories like SharePoint’s LAYOUTS path. It ensures a clean wipe without leaving behind any footholds for future re-exploitation. It also deletes malicious SharePoint artifacts from the LAYOUTS directory.
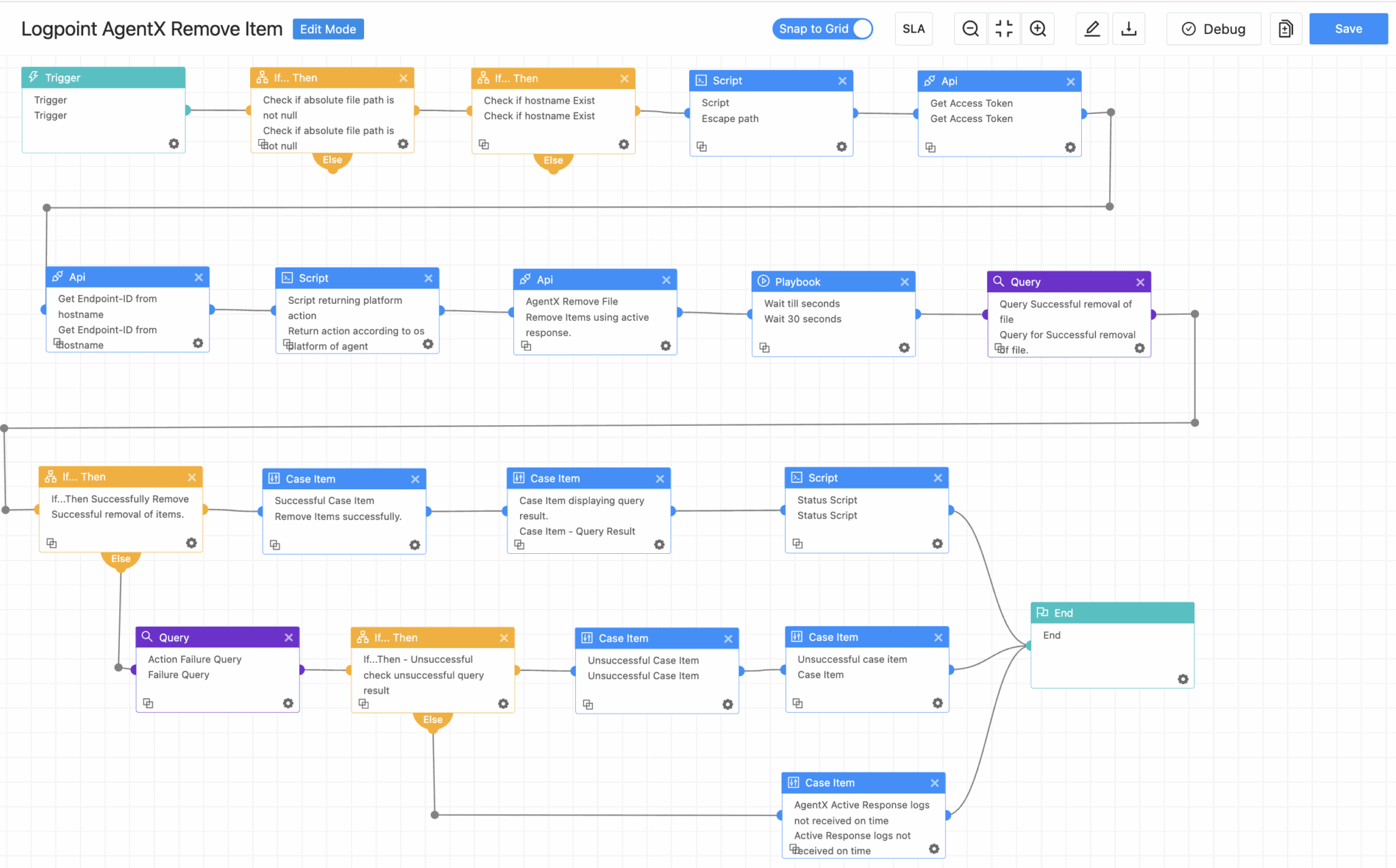
Additionally, the AgentX Terminate Process playbook empowers analysts to precisely eliminate harmful .aspx payloads such as spinstall0.aspx that operate within legitimate services like IIS (w3wp.exe). This targeted approach effectively neutralizes threats while preserving the integrity of vital SharePoint operations. After addressing the threat, the AgentX Restart Service playbook can be used to restart essential components such as IIS (via iisreset.exe), SharePoint Timer Service, Sysmon, or EDR agents. This step guarantees that monitoring and defensive capabilities are fully restored and ensures that SharePoint infrastructure returns to a secure, operational state post-remediation.
Isolate Host - Generic Playbook
Using Logpoint’s AgentX isolation playbook, security teams can immediately take a compromised SharePoint server offline, halting lateral movement and preventing attackers from pivoting or exfiltrating data, ensuring safe containment while investigation and remediation proceed.
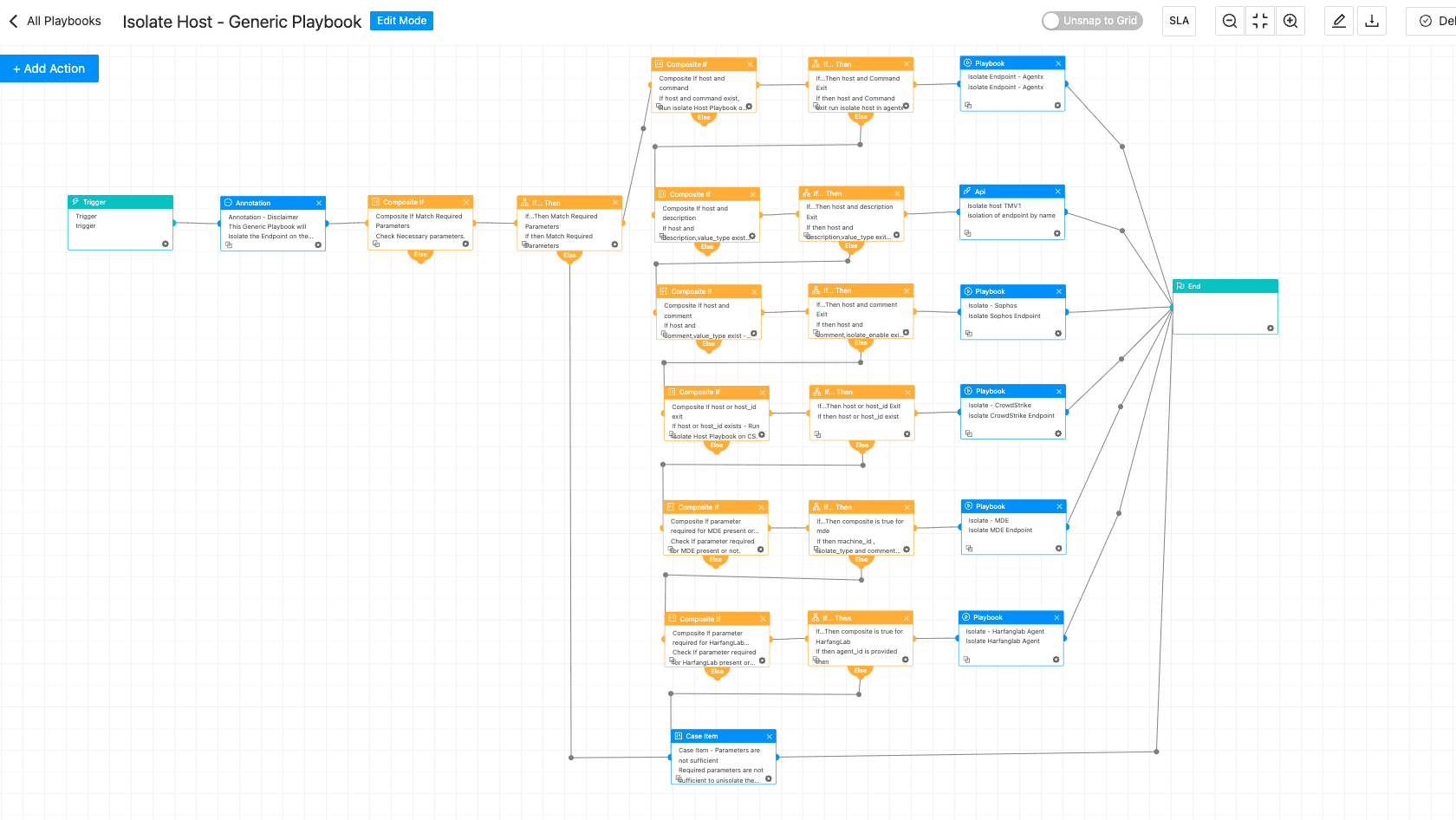
Isolate Host - Generic Playbook
Unisolate Host - Generic Playbook
Once mitigation and validation are complete, Logpoint’s unisolation playbook securely reconnects the previously isolated SharePoint server to the network, ensuring operational recovery without compromising post-incident safety.
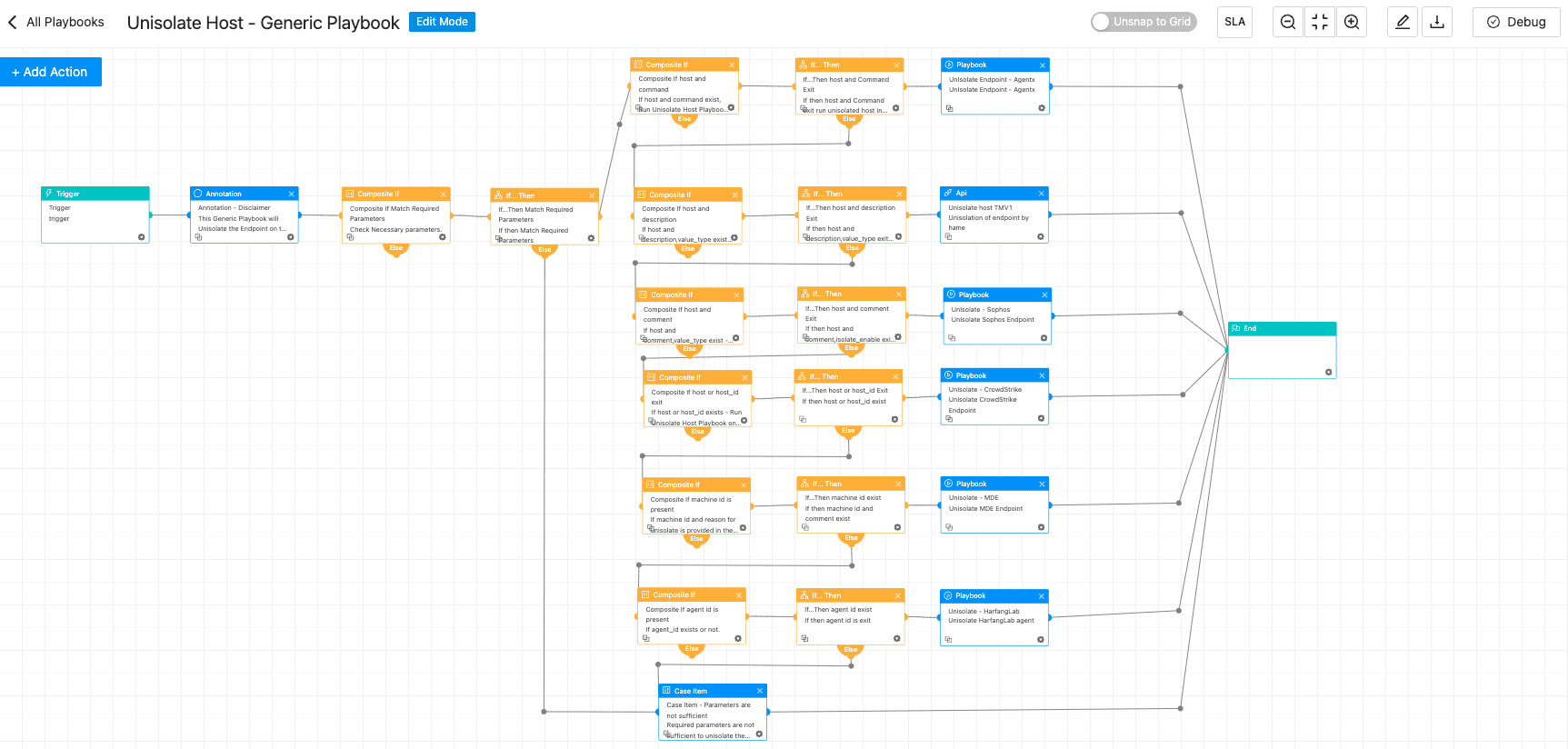
Unisolate Host - Generic Playbook
Recommendation & Mitigation
To minimize the risk of exploitation, organizations should take proactive hardening steps, leverage containment capabilities, and maintain strict endpoint visibility and control.
-
Patch all SharePoint servers to the versions that fix CVE-2025-53770.
-
Rotate machine keys using Update-SPMachineKey or via Central Administration.
-
Restart IIS using iisreset.exe to flush attacker-loaded web shells or memory-resident payloads.
-
Enable AMSI (Antimalware Scan Interface) for Microsoft SharePoint to allow detection of malicious scripts like obfuscated ViewState payloads.
-
If AMSI cannot be enabled, immediately disconnect or isolate internet-facing SharePoint servers using Logpoint’s Isolate Host – Generic Playbook to halt attacker operations and contain lateral movement.
-
Once patched and validated, use the Unisolate Host – Generic Playbook to safely bring the server back online without exposing the environment to re-compromise.
-
Auditing the SharePoint LAYOUTS directory for unauthorized .aspx scripts, and monitoring for suspicious POSTs, registry changes, and unexpected process activity (especially w3wp.exe, spinstall0.aspx, and ViewState-related behavior).
-
Update firewall and IPS rulesets to block connections to IOCs such as 107.191.58[.]76, 104.238.159[.]149, and 96.9.125[.]147, 103.186.30[.]186.
By combining these steps with Logpoint’s SOAR playbooks and AgentX telemetry, organizations can dramatically reduce the likelihood of successful exploitation and respond with speed and precision.




