By Anish Bogati and Bibek Thapa Magar; Security Research
TL;DR
Known by many names, including ALPHV, AlphaV, ALPHVM, and Noberus, BlackCat ransomware made headlines for its successive attacks on high-profile targets.
The highest ransom they have demanded so far is $14 million and it’s speculated that it has similarities with ransomware families like Darkside, Blackmatter, and REvil in regard to the tools, filenames, and techniques they use.
Despite this speculation, Recorded Future’s interview with the representative of BlackCat confirmed that, as yet, there is no connection.
So far, the ransomware has affected organizations globally, both small and large in size, and from multiple industries including critical infrastructure sectors, such as government agencies, construction, manufacturing, education, insurance, and transportation.
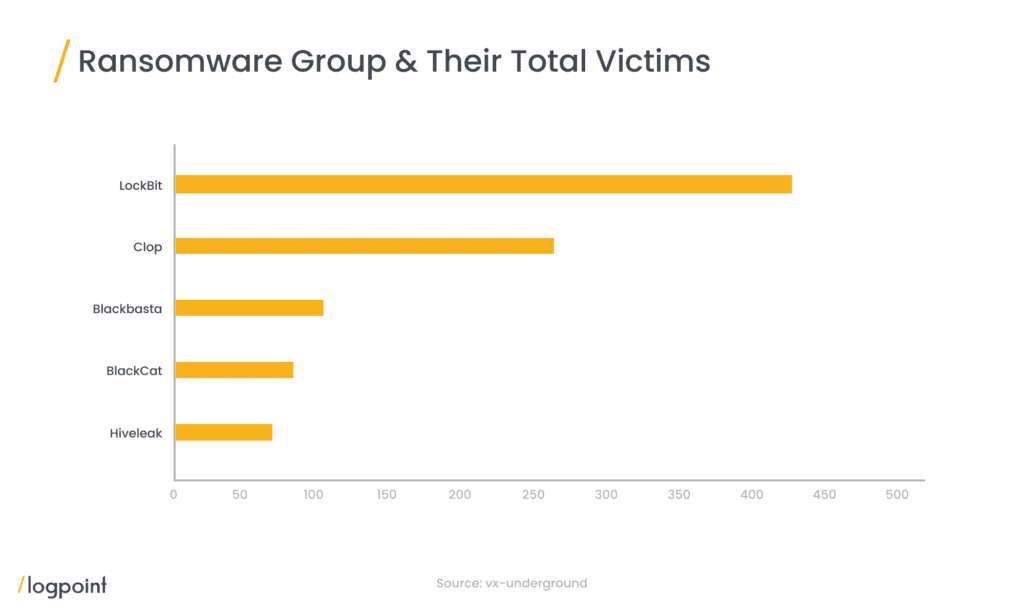
According to our research, BlackCat has the fourth highest number of victims with 90 known victims.
Analytics for the top ransomware groups are available for download in Logpoint Alert Rules.
*Blog contains detailed analysis and investigation & response via Logpoint.

Hunting and remediating BlackCat ransomware
Known by many names, including ALPHV, AlphaV, ALPHVM, and Noberus, BlackCat ransomware made headlines for its successive attacks on high-profile targets. Like Black Basta and Lockbit, it also operates under the Ransomware-as-a-Service (RaaS) model and uses double and sometimes triple extortion techniques.
BlackCat uses its public leak site to intimidate victims, where anyone can search and access the leaked victim information easily. The highest ransom they have demanded so far is $14 million and it’s speculated that it has similarities with ransomware families like Darkside, Blackmatter, and REvil in regard to the tools, filenames, and techniques they use. Despite this speculation, Recorded Future’s interview with the representative of BlackCat confirmed that, as yet, there is no connection. So far, the ransomware has affected organizations globally, both small and large in size, and from multiple industries including critical infrastructure sectors, such as government agencies, construction, manufacturing, education, insurance, and transportation.
According to our research, BlackCat has the fourth highest number of victims with 90 known victims. Analytics for the top ransomware groups are available for download in Logpoint Alert Rules.
BlackCat fast facts
-
Active since November 2021 and has a victim list of more than 140.
-
Written in Rust Programming Language and is cross-platform, supporting the entire Windows line from Windows 7 and above, ESXI, Debian, Ubuntu, ReadyNAS, and Synology.
-
Affiliates are punishing those impacted by increasing the ransom demand by publishing information from their conversations deleting the encryption keys of victims to intimidate future victims.
-
Supports multiple encryption modes along with intermittent encryption, providing speed and defense evasion capability.
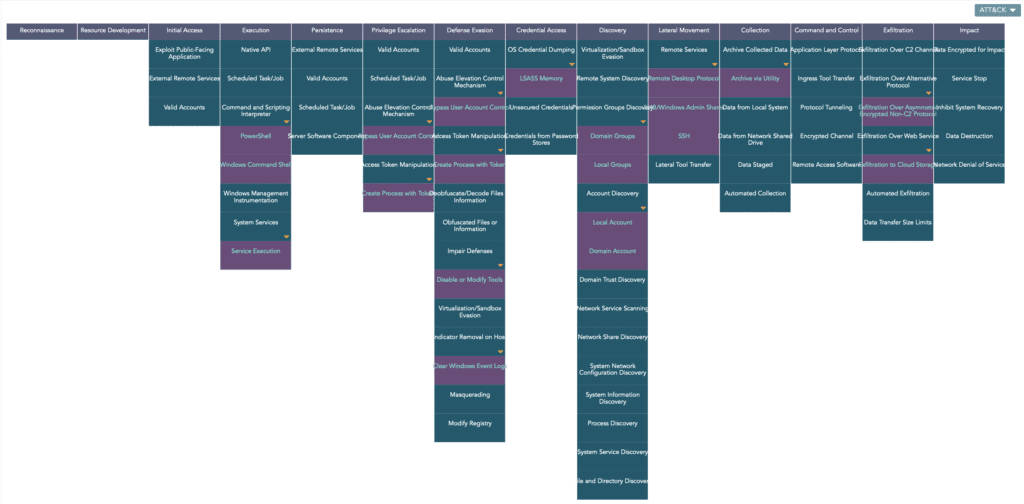
Technical analysis
BlackCat ransomware has been found to exploit compromised user credentials, unpatched or outdated firewall/VPN devices, public-facing applications, and unpatched Exchange servers to gain initial access to the system. Major initial access has been done through spearphishing and affiliates have been found buying access to the victim’s network.
We used multiple variants of the ransomware for our analysis to provide an all-encompassing detection and understanding. The samples we used were retrieved from vx-underground and for reference, we also used samples from tria.ge sandboxes. We also performed a dynamic analysis in our sandbox which is running Microsoft Windows 10 Enterprise Evaluation. The outcomes of our analysis are explained below.
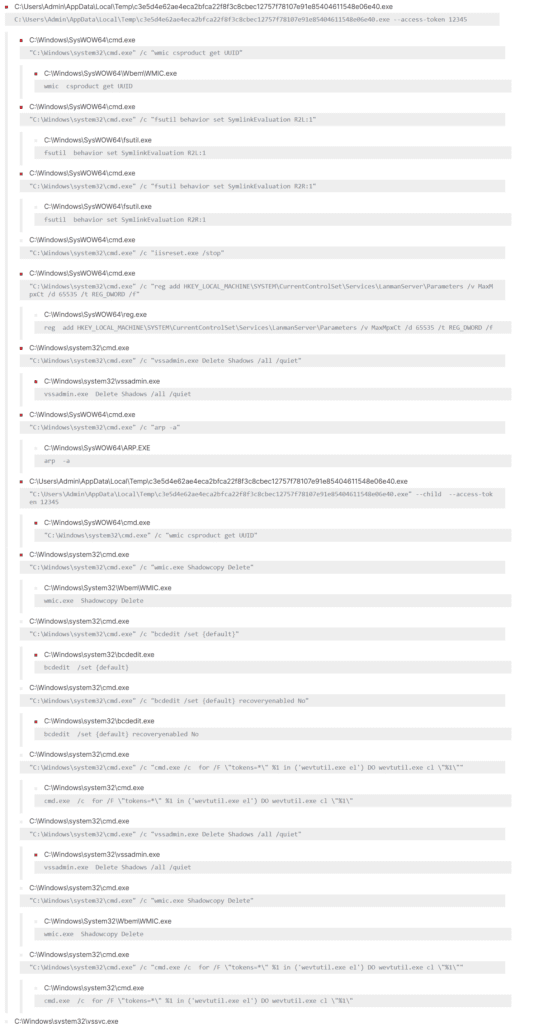
In a sample that was run on Windows 7-x64, it showed the following process tree:
Execution and Persistence
We started off assuming BlackCat already got initial access to the system. As soon as we detonated the malware, it placed itself in the startup folder to maintain persistence. Modification of “Autorun registry keys” was also observed for the same purpose. We saw execution of the following commands.
cmd.exe /c schtasks.exe /create /ru system /sc minute
/tn microsoft\windows\wininet\cachedtask /tr
C:\Users\xxx\AppData\Local\Temp\ServiceADS:cachetask /fEach time the system is booted or any user logs into the system, the malware gets executed.
We also observed that scheduled tasks were created using “schtasks.exe” as a fallback to maintain persistence and run as a predefined task, which could be seen starting from the injected explorer.exe process spawned schtasks.exe. By default, the tasks were set to run every minute.
cmd.exe /c schtasks.exe /run /tn microsoft\windows\wininet\cachedtaskIn our samples, we also saw the actors executing payloads via Image File Execution Options. Image File Execution Options are used for intercepting calls to an executable which is used for debugging, replacing, and stopping specific executables. By changing a binary, Image File Execution Options executes an arbitrary binary while executing the desired binary.
Defense Evasion
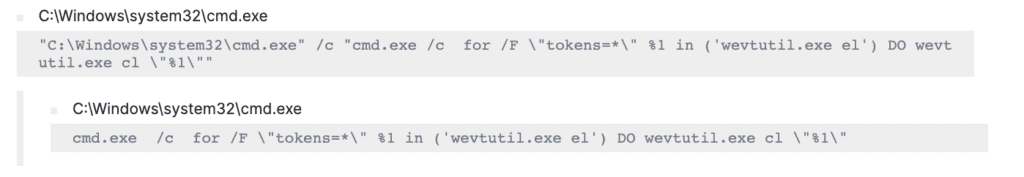
Then, we saw that to remove traces of its activities, BlackCat clears all system logs by using the “wevtutil” binary.
However, Cisco Talos Intelligence mentioned the use of Gmer.exe to disable endpoint protection systems. We also observed uninstallation of antivirus applications and disabling of Windows Defender security.
Credential Access
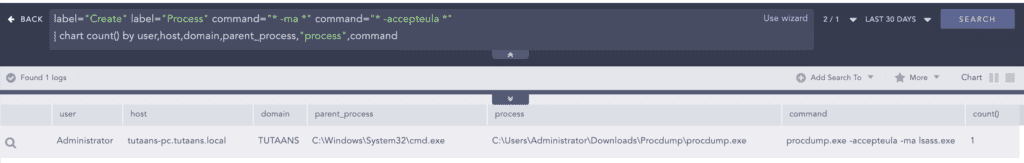
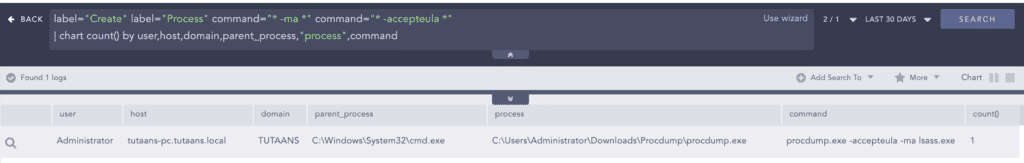
We observed the use of “ProcDump” to dump the LSASS process and obtain the user’s password hash.
cmd.exe /c C:\Users\xxx\AppData\Local\Temp\procdump.exe -accepteula
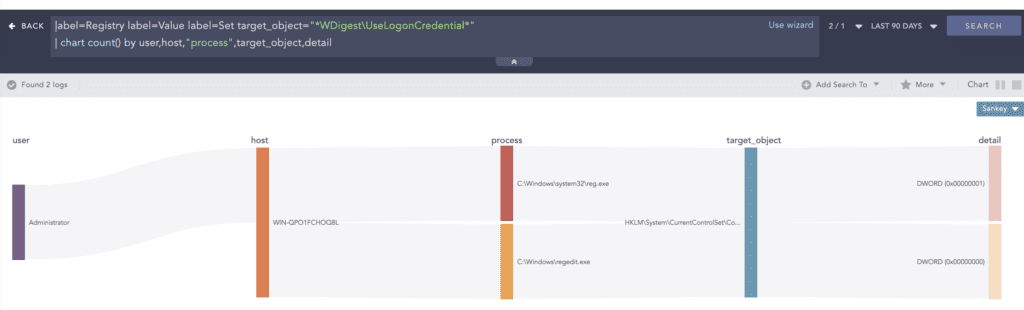
-ma lsass.exe "C:\Perflogs\lsass.dmp"To retrieve plain text credentials, the “reg.exe” binary was also used to enable the “WDigest” authentication protocol because it stores credentials in clear text.
cmd.exe /c reg.exe add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest
/v UseLogonCredential /t REG_DWORD /d 1 /fDiscovery
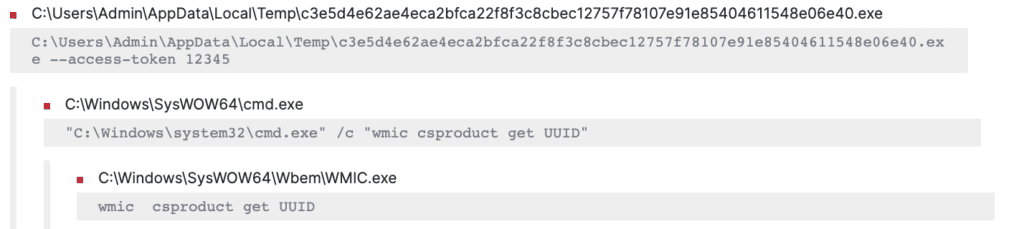
We saw that BlackCat uses “wmic.exe' to retrieve system UUID from the SMBIOS, which was used later for the recovery URL in the ransom note and also to track the compromised host and prevent re-encryption of the system.
Various system utilities and available tools like “ver” and “systeminfo” were used to discover local accounts, networks, and systems. BlackCat also set the execution policy to “Unrestricted,” which executed malicious payloads.
powershell.exe -c "$ep=Get-ExecutionPolicy;If ($ep -ne 'Unrestricted')
{Set-ExecutionPolicy Unrestricted -scope CurrentUser -Force}In some cases, the use of available system discovery PowerShell scripts like ADrecon.ps1 and Powerview.ps1 were used to collect information about Active Directory and permission groups.
powershell.exe -c "Unblock-File C:\Users\xxx\AppData\Local\Temp\ADRecon.ps1
C:\Users\xxx\AppData\Local\Temp\ADRecon.ps1; Lateral Movement
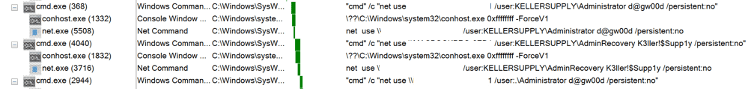
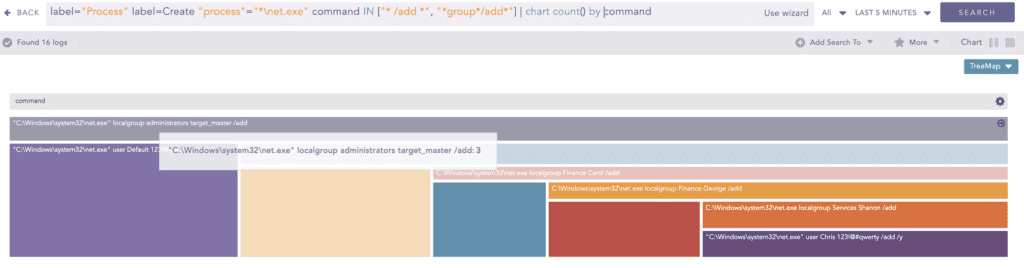
After the enumeration of the hosts, BlackCat tried to connect to discovered systems in the network and shares using the “net.exe” binary. It also tried to authenticate to the systems and shares using collected and compromised credentials.
The “net.exe” binary was further used to create a new user account and add it to the administrator group, then logoff was disabled and the password age was set to unlimited.
net.exe user LOCAL_SYSTEM 23weSD@# /add
net.exe localgroup Administrators LOCAL_SYSTEM /add
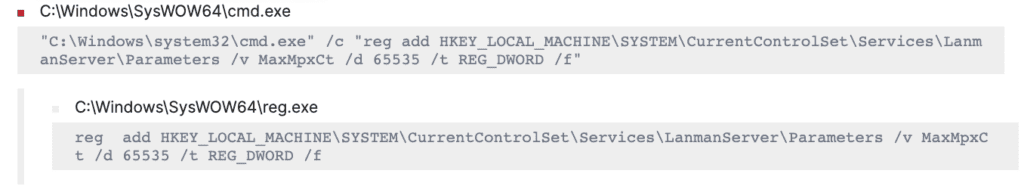
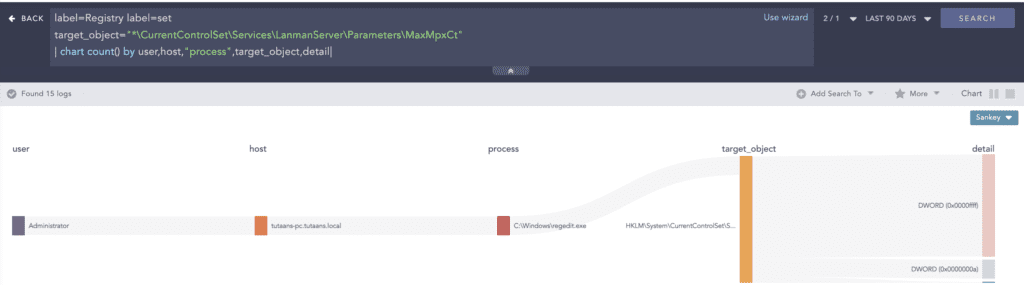
net.exe accounts /forcelogoff:no /maxpwage:unlimitedIt also used the “reg.exe” binary to modify the Lanmanserver registry key “MaxMpxCt” value which denotes the maximum number of outstanding client requests that can be maintained for each client on the server.
Exfiltration
Similar to other ransomware like conti, BlackCat used cloud storage service providers “Mega” to exfiltrate the victim’s data using tools like Rclone and FileZilla.
Impact
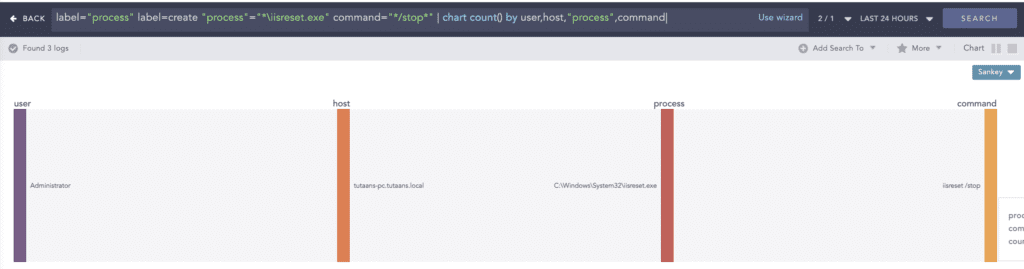
To prevent users from accessing the IIS service, BlackCat used the “iisreset” utility with “/stop” argument to stop all the IIS running services.
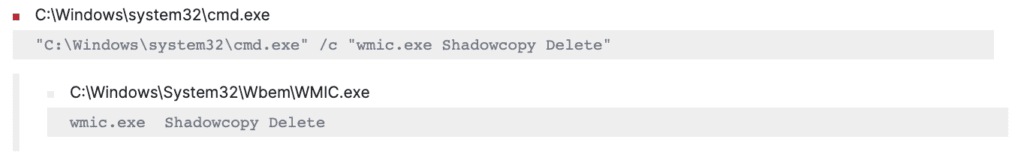
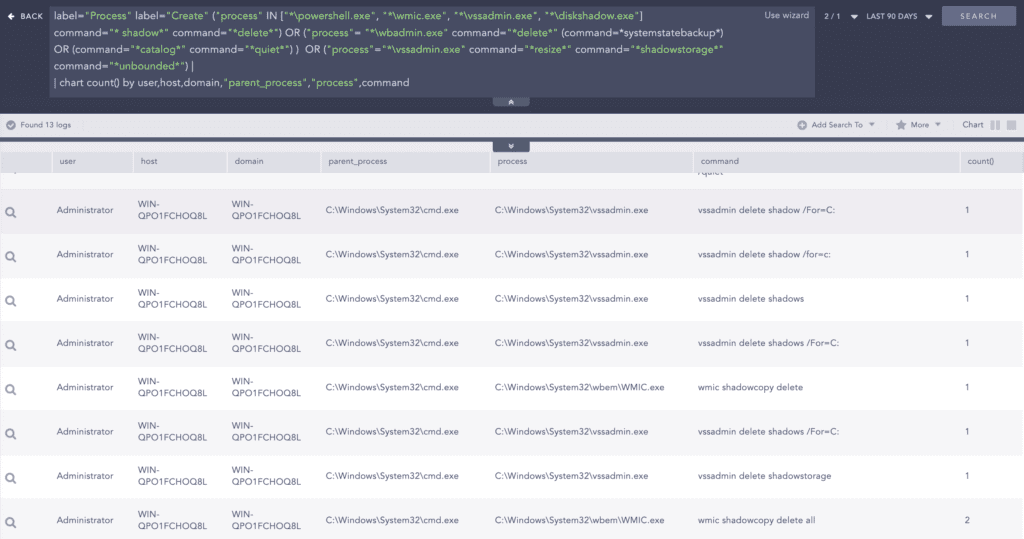
Then, it used system utilities like “wmic.exe” and “vssadmin.exe” to delete the shadow copies to prevent the administrator from recovering from the backup files.
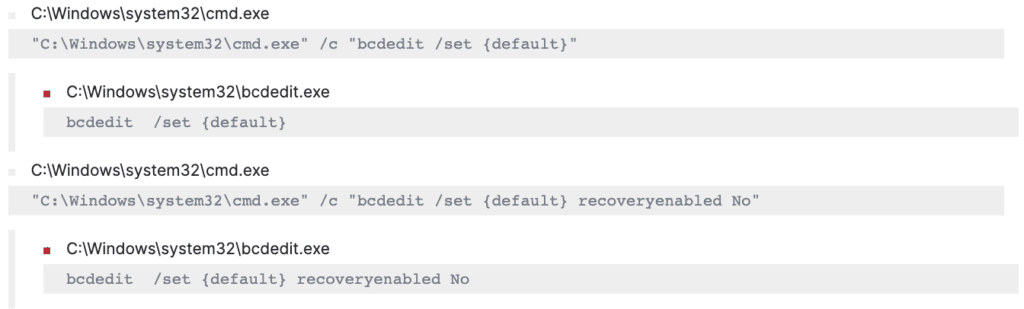
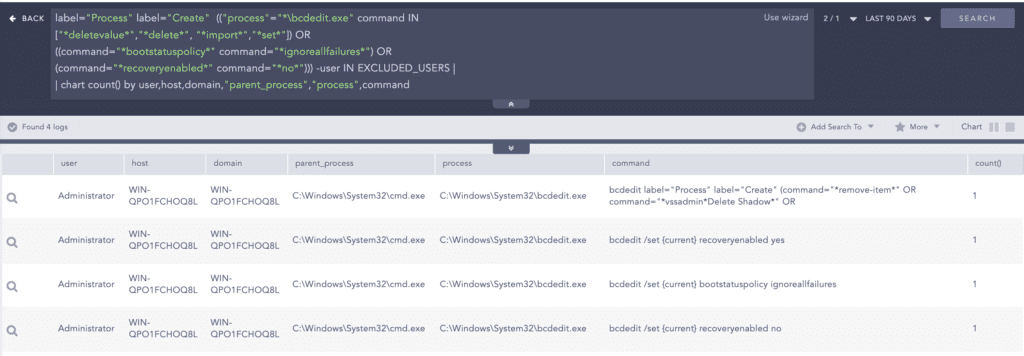
After the deletion of shadow copies, it modified the boot configuration data using “bcdedit.exe” to disable system recovery.
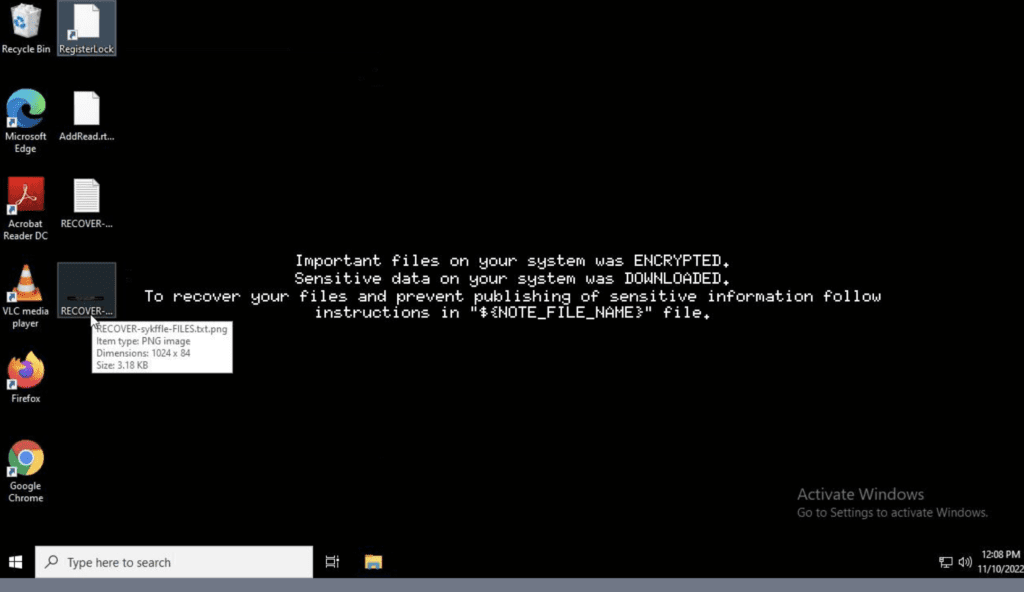
Lastly, the files were encrypted using the AES encryption algorithm (although the process can be overridden to use ChaCha20). An image along with a recovery file “RECOVER-sykffle-FILES.txt” was dropped on the desktop and the image was later used as wallpaper after completion of encryption.
Detecting BlackCat using Logpoint
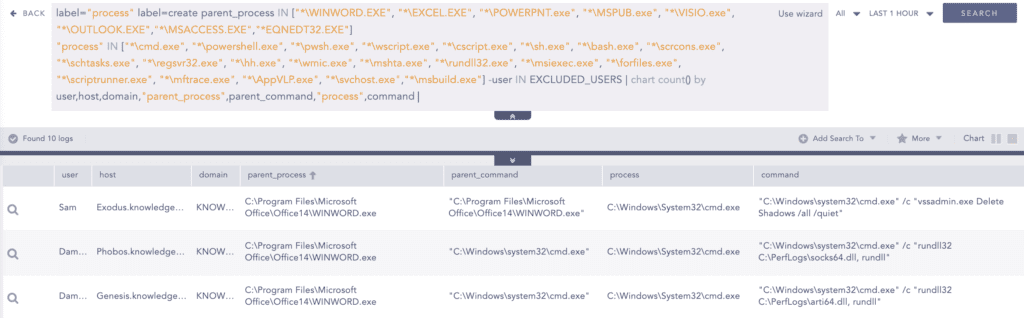
Analysts need to carefully monitor their systems for suspicious activities that can show the possibility of infection. In most cases, BlackCat achieved initial access via spearphishing. Victims were tricked into downloading macro-enabled documents. We can look for suspicious processes spawned by various Microsoft Office utilities.
label="Process" label="Create" parent_process IN ["*\WINWORD.EXE", "*\EXCEL.EXE", "*\POWERPNT.exe", "*\MSPUB.exe", "*\VISIO.exe", "*\OUTLOOK.EXE","*\MSACCESS.EXE","*EQNEDT32.EXE"]
"process" IN ["*\cmd.exe", "*\powershell.exe", "*\pwsh.exe", "*\wscript.exe", "*\cscript.exe", "*\sh.exe", "*\bash.exe", "*\scrcons.exe", "*\schtasks.exe", "*\regsvr32.exe", "*\hh.exe", "*\wmic.exe", "*\mshta.exe", "*\rundll32.exe", "*\msiexec.exe", "*\forfiles.exe", "*\scriptrunner.exe", "*\mftrace.exe", "*\AppVLP.exe", "*\svchost.exe","*\msbuild.exe"] -user IN EXCLUDED_USERS Most variants of BlackCat drop malicious payloads in trusted locations to evade detection. Defenders should look for process creation events, with corresponding images in suspicious folders. “SUSPICIOUS_FOLDER_EXE_EXECUTION" is a list that contains the list of suspicious folders most commonly used by adversaries.
label="Process" label="Create" "process" IN SUSPICIOUS_FOLDER_EXE_EXECUTION
-"process" IN ["*SpeechUXWiz.exe","*SystemSettings.exe","*TrustedInstaller.exe",
"*PrintDialog.exe","*MpSigStub.exe","*LMS.exe","*mpam-*.exe"]Analysts also need to look for “process” corresponding to wmic.exe with the respective command line arguments BlackCat uses for discovery purposes.
label="Process" label="Create" "process"="*\wmic.exe" command="*csproduct get*UUID"Powershell has been abused for different activities including the discovery of useful pieces of information and the execution of malicious codes. Analysts should look for suspicious Powershell arguments to detect BlackCat’s activities to bypass the execution policy to execute malicious commands.
label="Process" label="Create" command IN ["*-ep bypass*","*-exec*bypass*-noni*-nop*"
, "*-exec*bypass*-nop*-noni*", "*-noni*-exec*bypass*-nop", "*-noni*-nop*-exec*bypass"
, "*-nop*-exec*bypass*-noni*", "*-nop*-noni*-exec*bypass","*-noprofile*"
,"*-e* UnRestricted *"]BlackCat creates scheduled tasks for the execution of malicious binaries from non-default paths. Analysts also need to monitor the suspicious scheduled tasks from non-default paths.
(label="Process" label=Create "process"="*\schtasks.exe" command="* /create *")
OR (label="Registry" label="Key" label="Map"
"target_object"="*\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\*"
-target_object IN ["*\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\UpdateOrchestrator*"]
detail IN ["*C:\Users\Public*","*C:\PerfLogs*","*temp*"] event_type=CreateKey)Analysts can also detect the execution of scheduled tasks using the schtasks.exe binary:
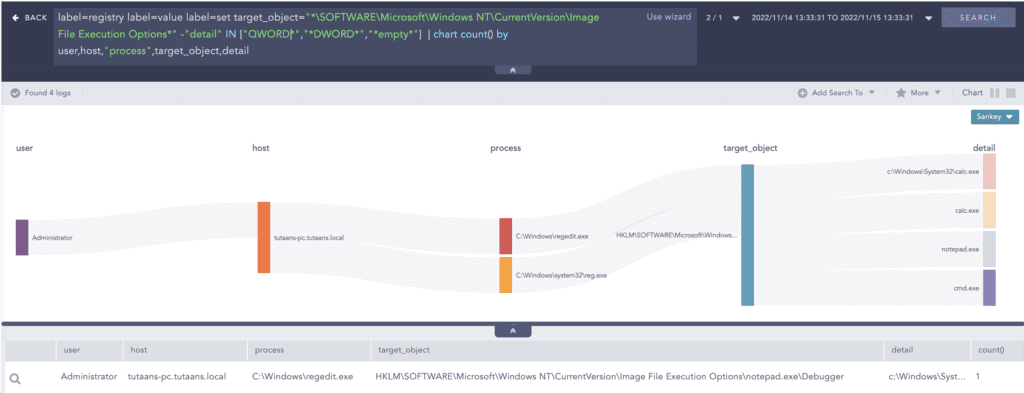
label="Process" label="Create" "process"="*\schtasks.exe" command="* /run *"BlackCat uses Image File Execution Options to maintain persistence and elevate privilege by executing malicious payloads. Registry auditing and relevant sysmon rules need to be configured properly for the detection of the Image File Execution Option modification. Defenders need to look for registry modifications indicating the use of Image File Execution Options.
label=Registry label=Value label=Set
target_object="*\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options*"Autorun Keys Modification needs to be monitored as well which indicates the malware trying to maintain persistence.
label=Registry label=Set label=Value
target_object IN ["*\software\Microsoft\Windows\CurrentVersion\Run*","*\software\Microsoft\Windows\CurrentVersion\RunOnce*",
"*\software\Microsoft\Windows\CurrentVersion\RunOnceEx*", "*\software\Microsoft\Windows\CurrentVersion\RunServices*",
"*\software\Microsoft\Windows\CurrentVersion\RunServicesOnce*", "*\software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit*",
"*\software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell*", "*\software\Microsoft\Windows NT\CurrentVersion\Windows*",
"*\software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders*"]
detail IN ["*C:\Users\Public*","*C:\PerfLogs*","*temp*"] -user IN EXCLUDED_USERSIn most cases of ransomware, file and folder permission are modified to get hands on the valuable data and also to write their payload on a specific path.
label="Process" label="Create" (("process" IN ["*\takeown.exe", "*\cacls.exe", "*\icacls.exe"] command="*/grant*")
OR ("process"="*\attrib.exe" command="*-r*")) User Access Control (UAC) bypass allows adversaries to evade detection and elevate privilege. Multiple methods are available. However, BlackCat uses ICMLuaUtil Elevated COM interface.
label="Process" label="Create" parent_process="*\dllhost.exe" parent_command IN ["*/Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}*","*/Processid:{D2E7041B-2927-42FB-8E9F-7CE93B6DC937}*"] -"process"="*\WerFault.exe" -file="WerFault.exe"It clears logs by using the system binary “wevtutil.exe” to evade detection, which should be monitored by analysts because sometimes legitimate use cases can trigger false positives.
(label="Process" label="Create" ((("process"="*\powershell.exe"
command IN ["*Clear-EventLog*", "*Remove-EventLog*", "*Limit-EventLog*"])
OR ("process"="*\wmic.exe" command="* ClearEventLog *")) OR
("process"="*\wevtutil.exe" command IN ["*clear-log*", "* cl *", "*set-log*", "* sl *"])))
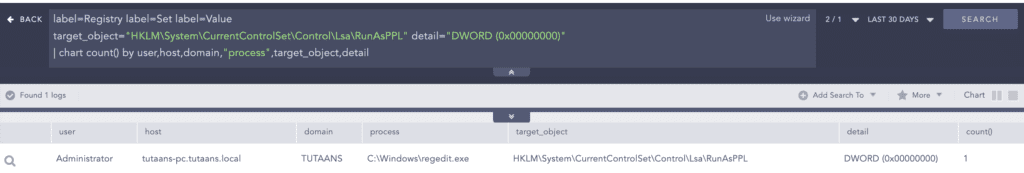
OR (norm_id=WinServer label=clear label=log)Protected Process can only be accessed by executables that are digitally signed with a special Windows Media. Protected Process Light is an extension of the protected process where the process can be assigned different levels of protection. If the Local Security Authority (LSA) process is running in protected mode, then the binary signed by Windows can only load into the process. BlackCat attempts to disable protected process light from the LSA.
label=Registry label=Set label=Value
target_object="HKLM\System\CurrentControlSet\Control\Lsa\RunAsPPL" detail="DWORD (0x00000000)" Ransomware uses various methods for LSASS process dumps. BlackCat leverages the “procdump.exe” utility to dump the LSASS process and retrieve credentials. Analysts need to look for malicious attempts to dump the LSASS process.
label="Process" label="Create" command="* -ma *" command="* -accepteula *" norm_id=WindowsSysmon label=File label=Create file="*.dmp" BlackCat also enables WDigest authentication methods for future logins to easily retrieve clear text credentials from the system. It is one of the most widely used TTPs among adversaries and thus needs to be monitored.
label=Registry label=Value label=Set target_object="*WDigest\UseLogonCredential" The use of net.exe for the creation of new users and their addition to the administrator group can also be monitored with the following query.
label="Process" label="Create" "process" IN ["*\net.exe","*\net1.exe"]
command IN ["* /add *", "*group*/add*"] Modifying the “MaxMpxCt” registry values to maximum allows the maximum number of SMB requests. BlackCat uses it while distributing ransomware to other systems via the PsExec utility. Finding logs corresponding to these events can also indicate the presence of BlackCat ramsomware.
label=Registry label=Set
target_object="*\CurrentControlSet\Services\LanmanServer\Parameters\MaxMpxCt" For exfiltration, BlackCat uploads the stolen data to cloud service provider MEGA and uses file-sharing services like the “Rclone” utility. DNS logs containing the MEGA storage server domain name can indicate exfiltration. The use of Rclone can also be monitored to look for such activities. But, legitimate use of backing data in the MEGA cloud can trigger false positives.
(label=DNS label=Query query IN ["*userstorage.mega.co.nz*","*mega.nz*","*mega.co.nz*"]) OR
(device_category IN ["Firewall","IDS","IPS"] domain IN ["*userstorage.mega.co.nz*","*mega.nz*","*mega.co.nz*"])label="Process" label="Create" "process"="*\rclone.exe"* parent_process IN ["*\PowerShell.exe","*\cmd.exe"]
command IN ["* pass *", "* user *", "* copy *", "* mega *", "* sync *", "* config *", "* lsd *", "* remote *", "* ls *"]BlackCat uses the “iisreset.exe” binary to stop all the IIS services and make them unavailable to legitimate users and analysts can look for such traces.
label="Process" label="Create" "process"="*\iisreset.exe" command="*/stop*"To inhibit system recovery, BlackCat uses “vssadmin.exe” and “wmic.exe” to delete Windows volume shadow copies.
label="Process" label="Create" ("process" IN ["*\powershell.exe", "*\wmic.exe", "*\vssadmin.exe", "*\diskshadow.exe"]
command="* shadow*" command="*delete*") OR ("process"= "*\wbadmin.exe" command="*delete*" (command=*systemstatebackup*)
OR (command="*catalog*" command="*quiet*") ) OR ("process"="*\vssadmin.exe" command="*resize*" command="*shadowstorage*" command="*unbounded*") BlackCat also disables recovery in the Windows boot menu using “bcdedit.exe” to inhibit system recovery. We can observe logs for possible modification of boot configuration.
label="Process" label="Create" (("process"="*\bcdedit.exe" command IN
["*deletevalue*","*delete*", "*import*","*set*"]) OR
((command="*bootstatuspolicy*" command="*ignoreallfailures*") OR
(command="*recoveryenabled*" command="*no*"))) -user IN EXCLUDED_USERS To maximize the impact on the victim organization, BlackCat uses the data destruction method to destroy important data or render it useless. A high volume of file modification or deletion in a short span can be an indicator and analysts should actively monitor for such cases.
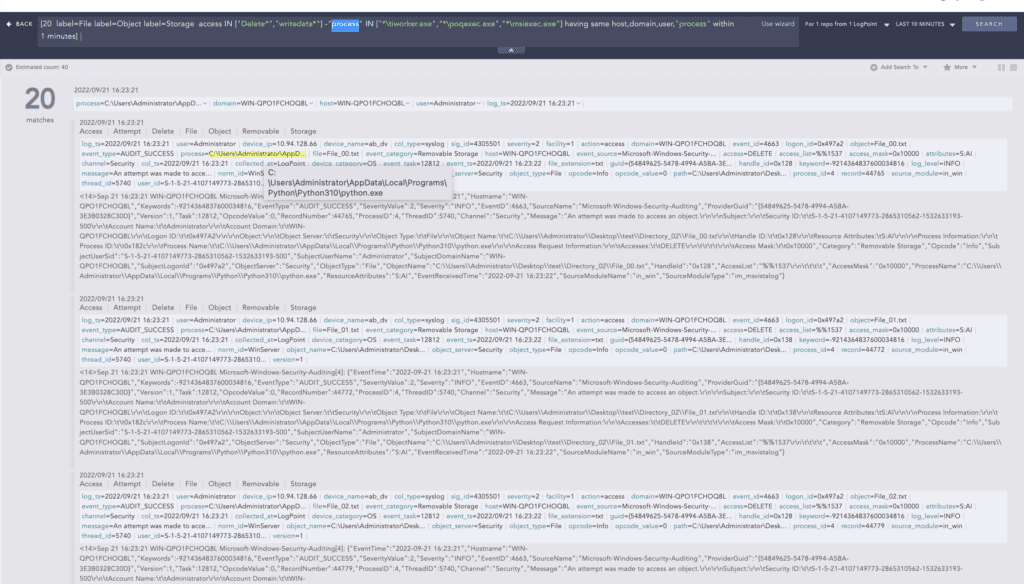
[20 label=File label=Object label=Storage access IN ["Delete*","writedata*"] -"process" IN ["*\tiworker.exe","*\poqexec.exe","*\msiexec.exe"] having same host,domain,user,"process" within 1 minutes] In the above query, the integer value “20” needs to be modified according to the use case. In our case, we have defined 20 file modifications in a minute to indicate suspicious activity.
The above-mentioned methods can be useful for hunting BlackCat ransomware with ease. Analysts can use Logpoint Alert Rules as the next line of defense for BlackCat detection and the latest version of Alert Rules is available from Logpoint.
Investigation and response using Logpoint SOAR
There is no actual silver bullet for investigation and response to ransomware. However, Logpoint SOAR can by far be the most useful tool for organizations to investigate and respond to ransomware attacks.
-
Phishing investigation and response
This playbook ensures all suspicious phishing incidents are adequately investigated and responded to, dramatically reducing the response time and human error.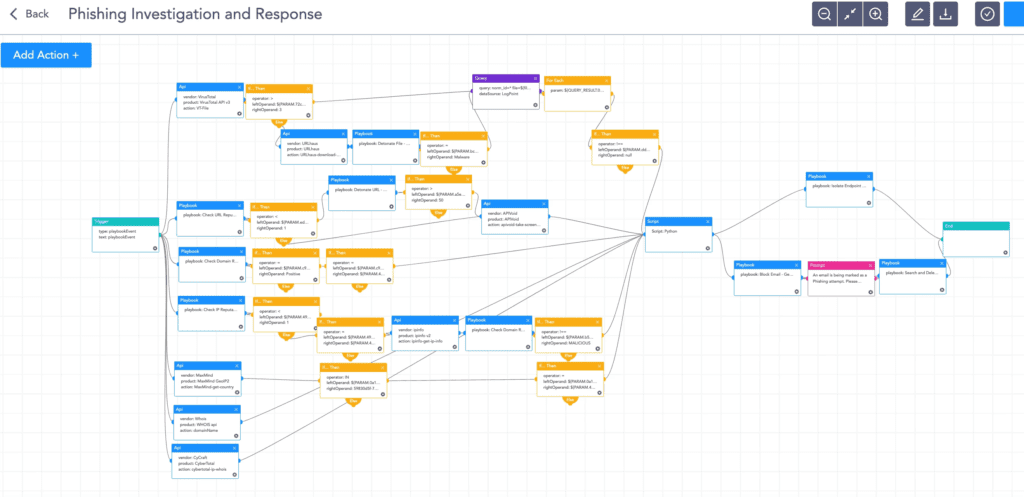
-
Ransomware investigation
This playbook thoroughly examines the IoCs and uses a sandbox to detonate the suspicious files. It also looks for the common TTPs used by the ransomware, improving the chances of detecting ransomware before it is too late. The playbook will prompt an alert message to the administrators if ransomware is identified, and will start further work to isolate the host and contain the malware.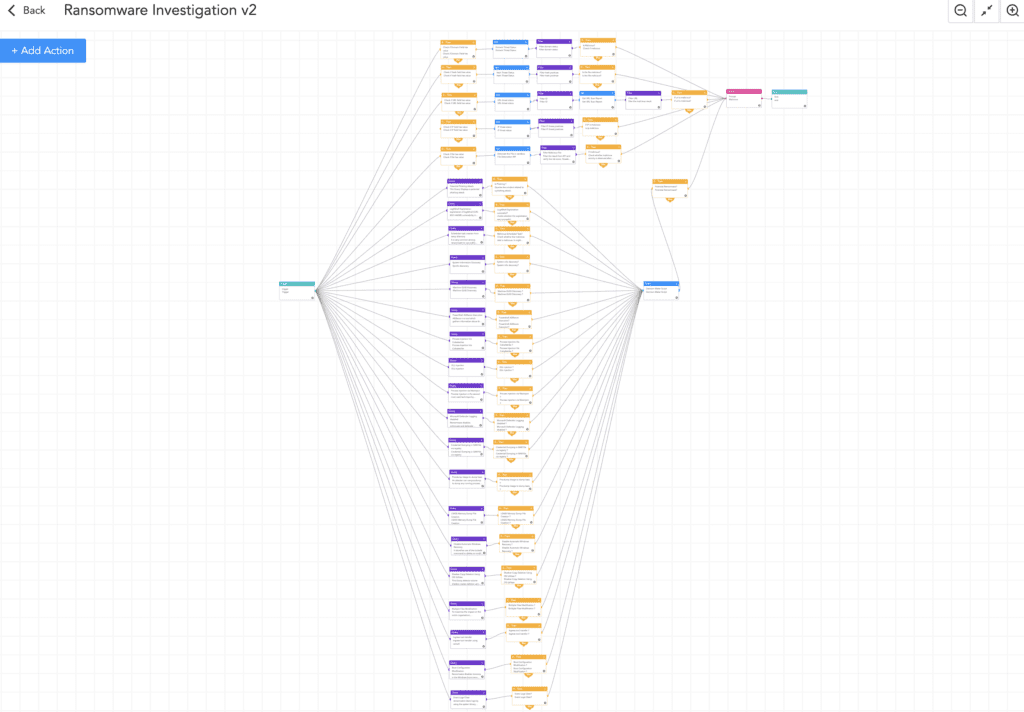
- Isolate endpoint mitigation
This playbook identifies the infected host and isolates it using the new Logpoint AgentX and also contains and quarantines it before it spreads to other machines. To get started with AgentX, a built-in response capability on endpoints, contact your Logpoint representative.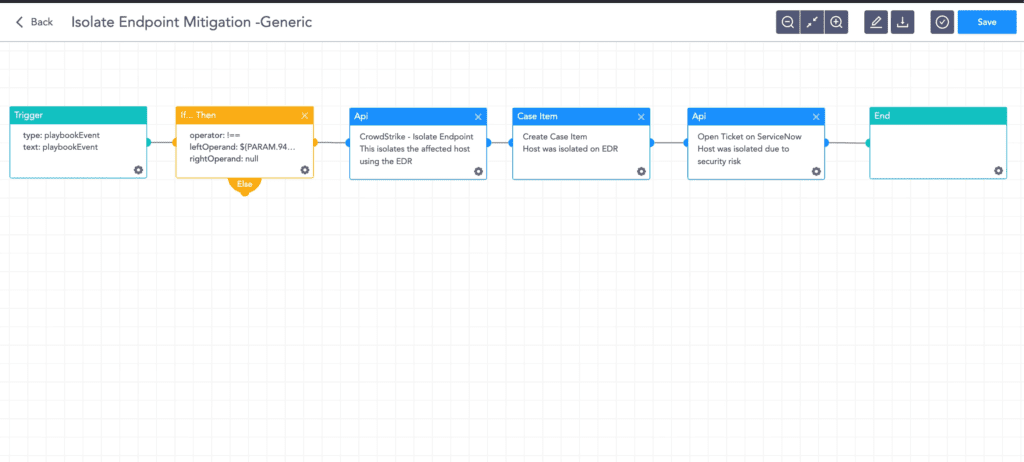
- Block indicators
This playbook checks if any IP, domain, URL, or host exists in a list of IoCs, blocks them, and adds them to the blocked list.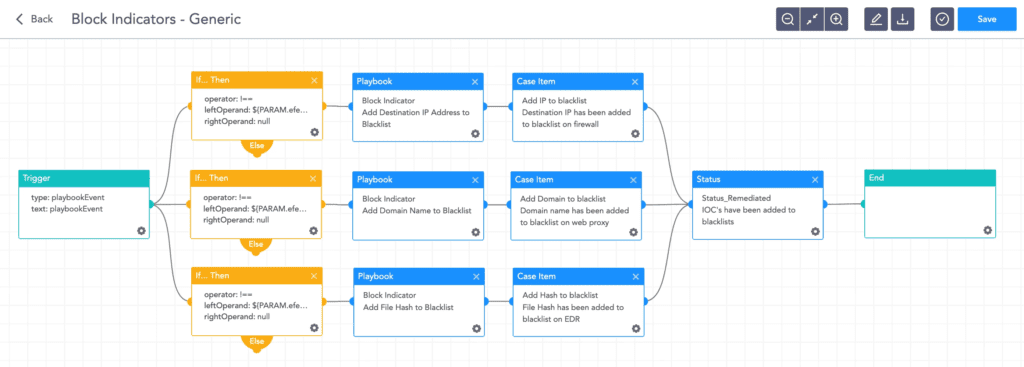
Recommended mitigation:
-
Use multi-factor authentication with high priority wherever necessary, particularly for webmail, VPNs, and privileged accounts.
-
Use segmentation or other methods to design the network in such a way as to maximize the reduction of impact.
-
Simulate real-life scenarios more often and make employees aware of phishing and other risks and also that they report the incident to the internal cybersecurity team.
-
Regularly scan and assess internet-facing devices for vulnerabilities and misconfigurations, patch them and keep operating systems, software, and firmware up-to-date.
-
Ensure the endpoint protection devices are installed, configured properly, are up-to-date, and trigger alerts if they are accidentally turned off.
-
Disabling or blocking Server Message Block (SMB) protocol outbound and removing its outdated versions can prevent threat actors from propagating malware across organizations.
-
Monitor and control privileged accounts and provide them with the least access as much as possible.
-
Maintain regular encrypted offline backups of data and also test its accessibility for change or deletion on a regular basis.
-
Simulate the worst-case scenarios regularly and make sure the incident response, playbooks, and disaster recovery plan are in place for working and continuity of business.
-
Prearranging third-party expertise in legal counsel, forensic incident response, and ransom negotiation and payment comes in handy as well.
-
Obtaining appropriate cyber insurance coverage can be useful in a worst-case scenarios.
Despite prevalence and sophistication, it’s easy to detect BlackCat
Although BlackCat has a smaller number of victims compared to its competitors, the number is likely to grow in the near future. The BlackCat ransomware group and its affiliates know the game. They launch the attack and carry out the operation with high efficiency, and each second wasted is a loss of data. Organizations need to be extra cautious and use preventive measures as much as possible and always keep contingency plans up their sleeve. The use of converged solution with powerful SIEM, SOAR, and endpoint security controls is necessary. Despite being a sophisticated ransomware, Logpoint can easily detect many of BlackCat’s tactics, techniques, and procedures and Logpoint SOAR playbooks can detect and respond to ransomware activities.