By Ira Lisa Kristina Leino, Product Marketing Manager
SAP systems are the center of business operations, they store data related to enterprise resource planning (ERP), supply chain management (SCM), product lifecycle management (PLM), customer relationship management (CRM), and much more. Why is SAP data such a hot topic? Well, the fact that a massive 87% of global commerce is generated in SAP – These systems are a mouth-watering target for cybercriminals.
To mitigate and counter these threats Logpoint Business-Critical Security (BCS) for SAP is based on technology that extracts SAP data and connects it with any SIEM to provide full end-to-end security operations capabilities for SAP events. The relaunch of Logpoint’s SAP products divides the previous one into four solutions to better address customers’ needs and is the first Business-Critical Security solution under the Logpoint BCS umbrella.
Introducing BCS – security for business-critical systems
By onboarding SAP data into a SIEM, we deliver real-time threat detection, incident response, advanced analytics, and monitoring of the entire business-critical system in one central security operations solution.
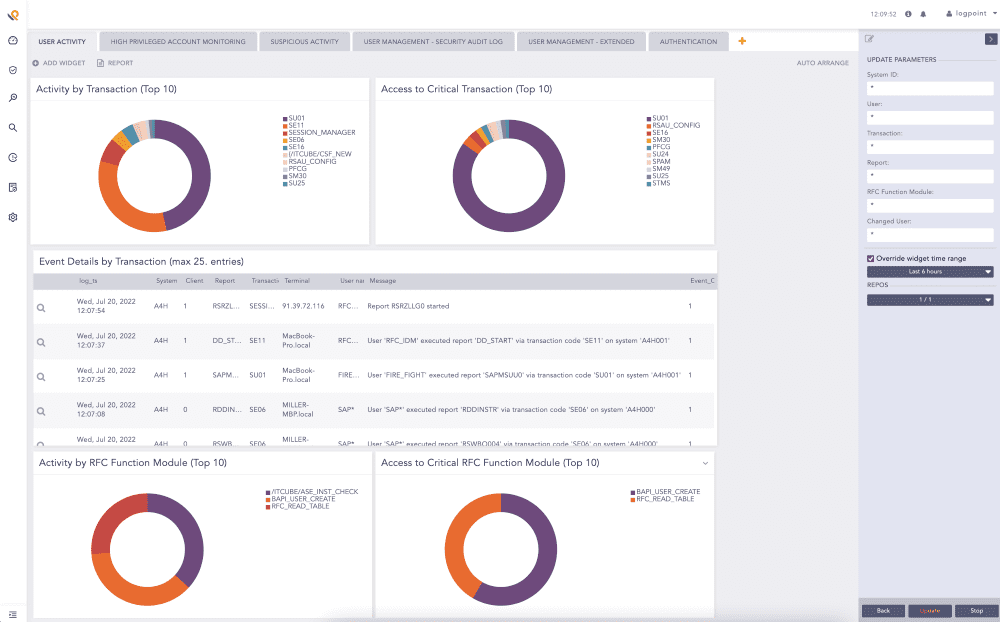
Logpoint BCS for SAP helps monitor business-critical data and act on security incidents.
The new Logpoint BCS will cover all our current and upcoming security solutions for business-critical systems.
Four solutions to meet every SAP monitoring need
With the relaunch, we are introducing four solutions, including new capabilities for monitoring business integrity – Finding the right solution for your needs is easier than ever.
With the four new solutions, customers can:
Add the missing layer of security to SAP
Security in SAP systems is limited; the SAP data does not correlate with other events in the IT network, creating a severe security gap that can only be overcome by bringing the business-critical data into a central monitoring solution, SIEM. Furthermore, logging, advanced analytics, and incident response are limited or non-existent in SAP systems.
SAP systems are under a serious threat. 64% of organizations reported a serious breach of their SAP systems in the past 24 months.
Address the security limitations of business-critical applications and elevate your SAP security to the next level with the Security & Audit Compliance Monitoring solution.
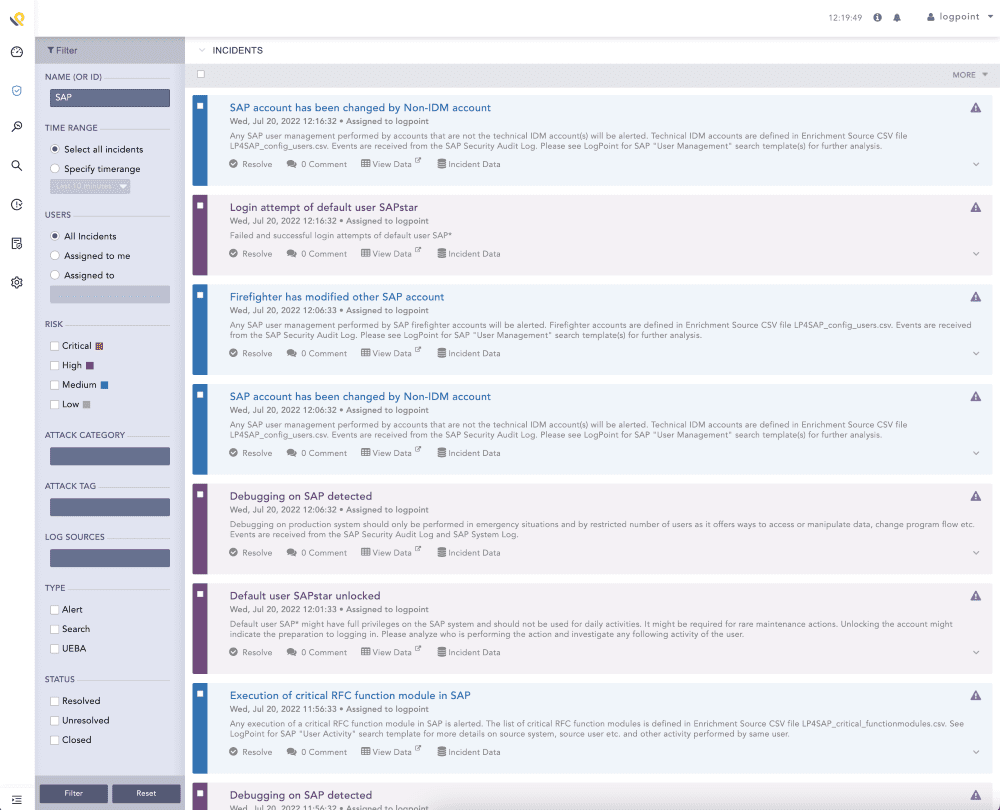
Extracting SAP data into SIEM gives a clear overview of incidents.
Minimize fraud and financial losses
Fraud (55%), monetary gain (49%), and theft of intellectual property (44%) are the major motivations behind insider threats. Our Business Integrity Monitoring solution provides continuous monitoring at the speed of the business. It detects points of deviation in your SAP business processes by comparing them to a normal flow with pre-defined use cases. Automated process controls, visual dashboards, and alerts ensure that managing cases of errors, fraud, and access violations is more efficient.
Monitor access to personal information
Personally Identifiable Information is one of the most common types of compromised information in breaches of ERP systems. Our Personal Identifiable Information (PII) Access Monitoring solution centralizes the monitoring of sensitive and personal data into one platform. This gives users a better overview and the ability to manage access violations quickly and efficiently.
Organizations may face up to €20 million or 4% of their annual turnover – whichever is greater – in penalties for non-compliance of GDPR. An easy-to-understand overview of logs related to personal data helps teams uncover unauthorized access or leakage of data and act fast to prevent the cost of non-compliance and reduce audit costs.
Identify operations problems
IT Service Intelligence works as Operations Monitoring but within SAP systems. According to an IDC report, downtime in business-critical ERP systems is costly – estimates vary from thousands of dollars up to $500,000 per hour. Moreover, many organizations experience downtime in business-critical systems every second month. Our IT-SI solution for SAP systems gives full visibility into your system’s operational capabilities, identifies operations problems, and provides early warnings to circumvent any problems before they happen.
Mix and match based on your needs
Choose the most relevant solutions to secure your systems – the solutions are available separately and can be combined with each other based on your organization’s needs. Logpoint BCS for SAP solutions work with any SIEM.







