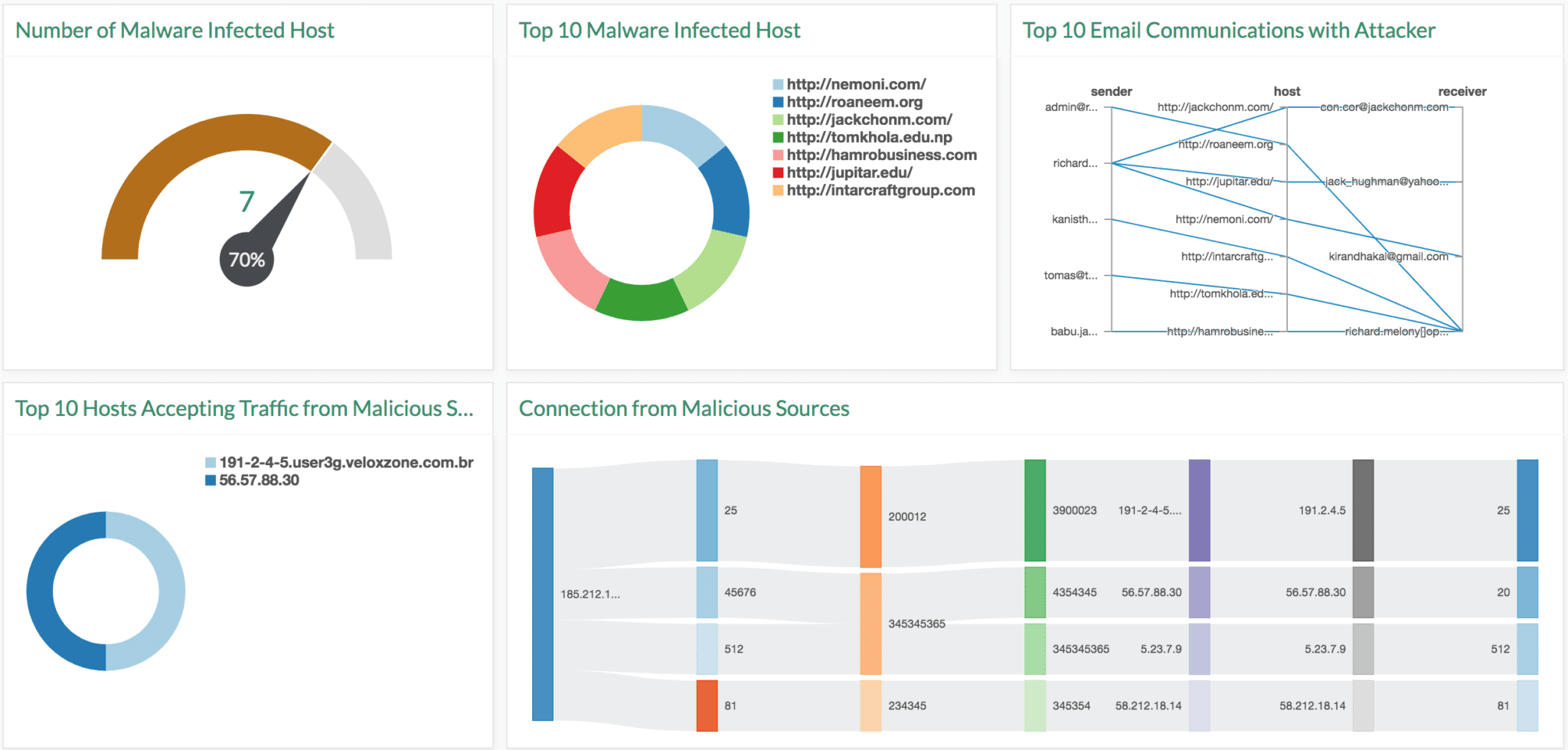
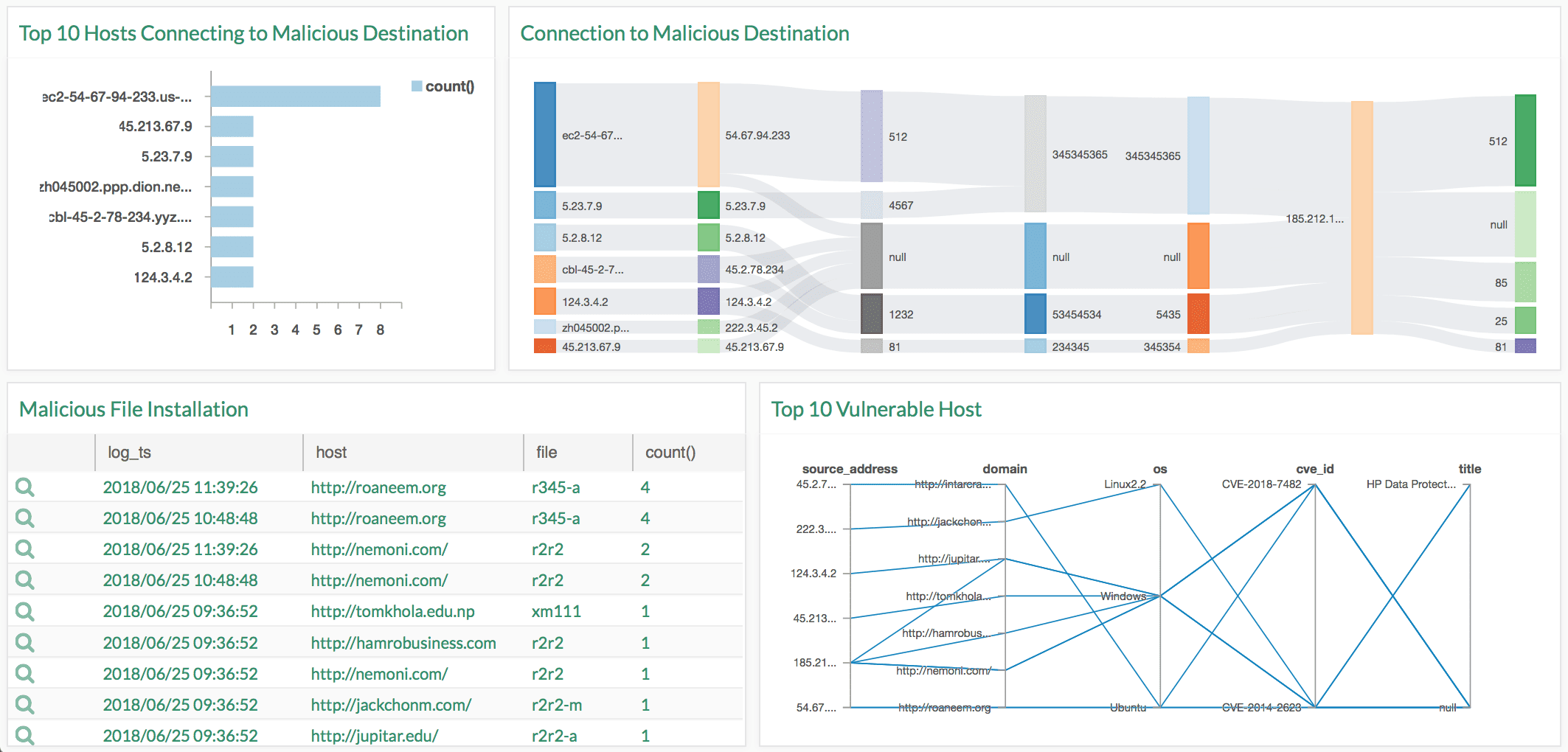
Operation Prowli, a traffic manipulation and crypto currency mining malware has infected many organizations globally. The attackers spread the malware from vulnerability exploits where brute password is forced. Once they successfully compromise a device, a self-propagating worm is installed to exploit vulnerabilities and expands the botnet by identifying and spreading to new devices.
The malware is especially harmful as it targets various platforms – CMS servers hosting popular websites, backup servers running HP data protector, DSL modems and IoT devices. The attackers gain profit using two methods, cryptocurrency mining and traffic monetization fraud.
In the first case, the malware takes over the infected devices to mine Monero, a cryptocurrency focused on privacy and anonymity to a greater degree than Bitcoin. In the second case, traffic monetizers acquire traffic from Prowli attackers and redirect it to domains on demand. Website “operators” i.e Prowli attackers profit from the traffic sent through the traffic monetizers.
LogPoint has developed an application specifically designed to detect Prowli malware. The Prowli app is available to all LogPoint users now.
Indicators of Compromise:
- Various files are downloaded in the process and they give an indication of compromise.
- r2r2 : 128582a05985d80af0c0370df565aec52627ab70dad3672702ffe9bd872f65d8
- r2r2-a : 09fa626ac488bca48d94c9774d6ae37d9d1d52256c807b6341f0a08bdd722abf
- r2r2-m : 908a91a707a3a47f9d4514ecdb9e43de861ffa79c40202f0f72b4866fb6c23a6
- r345 : 51f9b87efd00d3c12e4d73524e9626bfeed0f4948781a6f38a7301b102b8dbbd
- r345-a : cfb8f536c7019d4d04fb90b7dce8d7eefaa6a862a85c523d869912a1fbaf946a
- r345-m : 88d03f514b2c36e06fd3b7ed6e53c7525a8e8370c4df036b3b96a6da82c8b45b
- xm111 : b070d06a3615f3db67ad3beab43d6d21f3c88026aa2b4726a93df47145cd30ec
- cl1 : 7e6cadbfad7147d78fae0716cadb9dcb1de7c4a392d8d72551c5301abe11f2b2
- z.exe : a0a52dc6cf98ad9c9cb244d810a22aa9f36710f21286b5b9a9162c850212b160
- pro-wget : a09248f3a4d7e58368a1847f235f0ceb52508f29067ad27a36a590dc13df4b42
- pro-s2 : 3e5b3a11276e39821e166b5dbf6414003c1e2ecae3bdca61ab673f23db74734b
- Connections with the following domains also serve as indicators of compromise.
- startreceive[.]tk
- stats.startreceive[.]tk (traffic redirection)
- wp.startreceive[.]tk (C&C)
- roi777.com
- minexmr.com
- Another indication of compromise could be email communication from the following email address.
- richard.melony[]openmailbox[]org
- Connection with the following IP address could also be an indication of compromise:
- 185.212.128.154
Vulnerabilities:
The attackers exploit the following vulnerabilities, and immediate remediation is needed.
- CVE-2014-2623
- CVE-2018-7482
Log Source Requirements:
- Windows server/integrity scanner
- Detects malicious file installation and malware infected hosts
- Mail server
- Detects any emails sent to malicious address
- Firewall
- Detects connection to and from malicious listed sources
- Vulnerability management
- Detects hosts vulnerable to malware