After our blog post on Sunday regarding the WannaCry malware breakout, LogPoint today is excited to announce our turn-key application to detect and respond to WannaCry.
The application works on LogPoint and LogPoint Free, it works for all types of devices (firewalls, content security appliances, file-shares etc) and provides a simple effective tool to monitor and contain any further spread of the malware.
In addition, as research moves forward with different samples of the WannaCry, we can provide easy and fast updates to the application.
The technical details of the application are covered below:
- Monitoring the network for unusual connections to the SMB services between workstations. As the worm propagates by infecting and spreading, we will see unusual access patterns; clients should only connect to servers – in this case, we will see clients connecting to other clients.
- The malware has a very easy-to-spot pattern: encrypting files. Detecting when this happens is carried out through the use of the LogPoint agent. By monitoring for WCRY extensions we can easily detect if an infection takes place.
- The malware exploits the vulnerability identified in MS17-010. This vulnerability is detected through Qualys and by importing all Qualys scans in LogPoint, alerts will fire immediately as vulnerable hosts are discovered by Qualys.
- Certain variations of the worm will attempt to connect to a domain, which is now sinkholed. This connection is easy to detect and our analytics application will alert the second this takes place.
1. Check for SMB connections
source_address IN HOMENET destination_port= 445 | chart distinct_count(destination_address) as DC by source_address | search DC>200
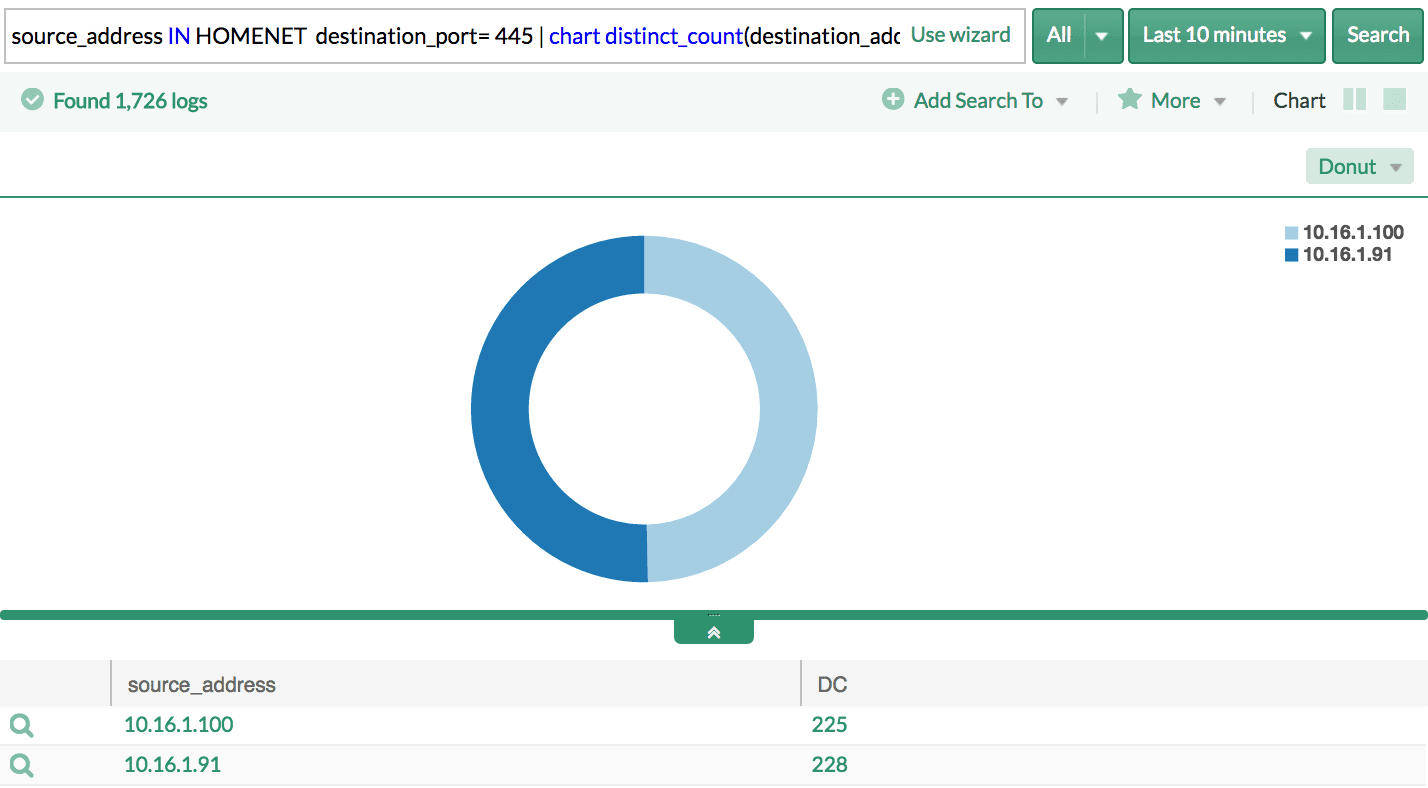
This is the case where the hosts in your infrastructure are already compromised and the malware is in the process of spreading. The first measure you should take is to apply the Microsoft security patches and disabling SMBv1 services (Guide here).
2. Identify encrypted files
norm_id=IntegrityScanner new_file IN WANNACRY_EXTENSION | chart count() by file_path, new_file order by count() desc
You can configure the LogPoint agent to monitor the integrity of your critical documents and then, if any of the hosts in your infrastructure show an evidence of change in the file formats, particularly to WCRY or similar, you might need to start looking for a quick response.
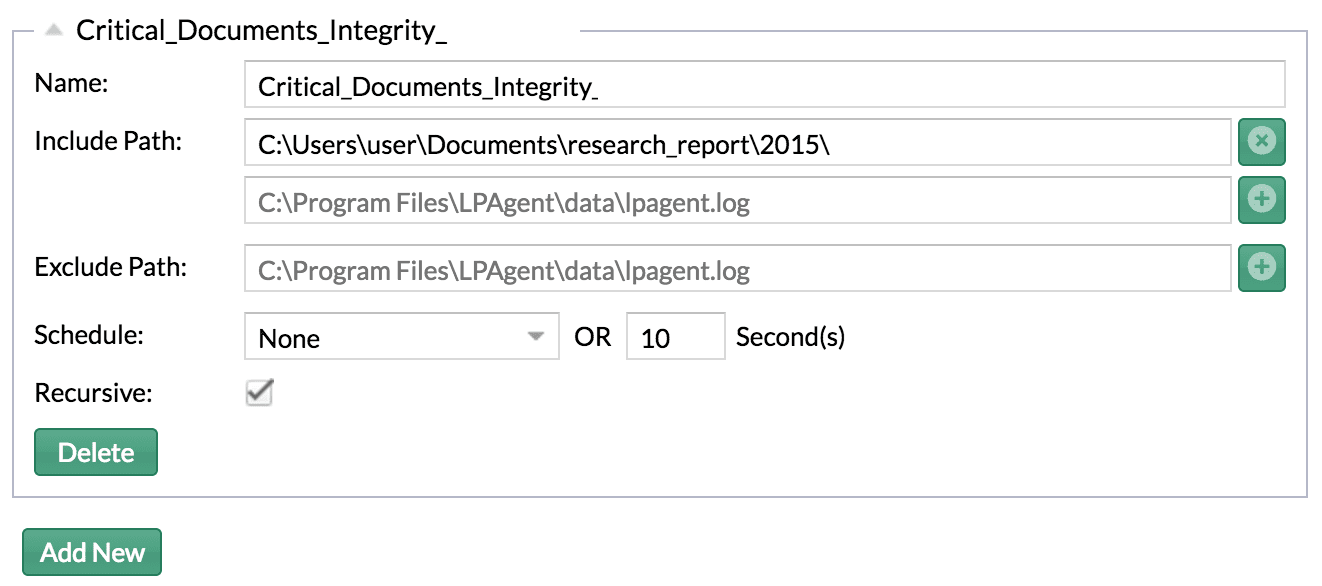
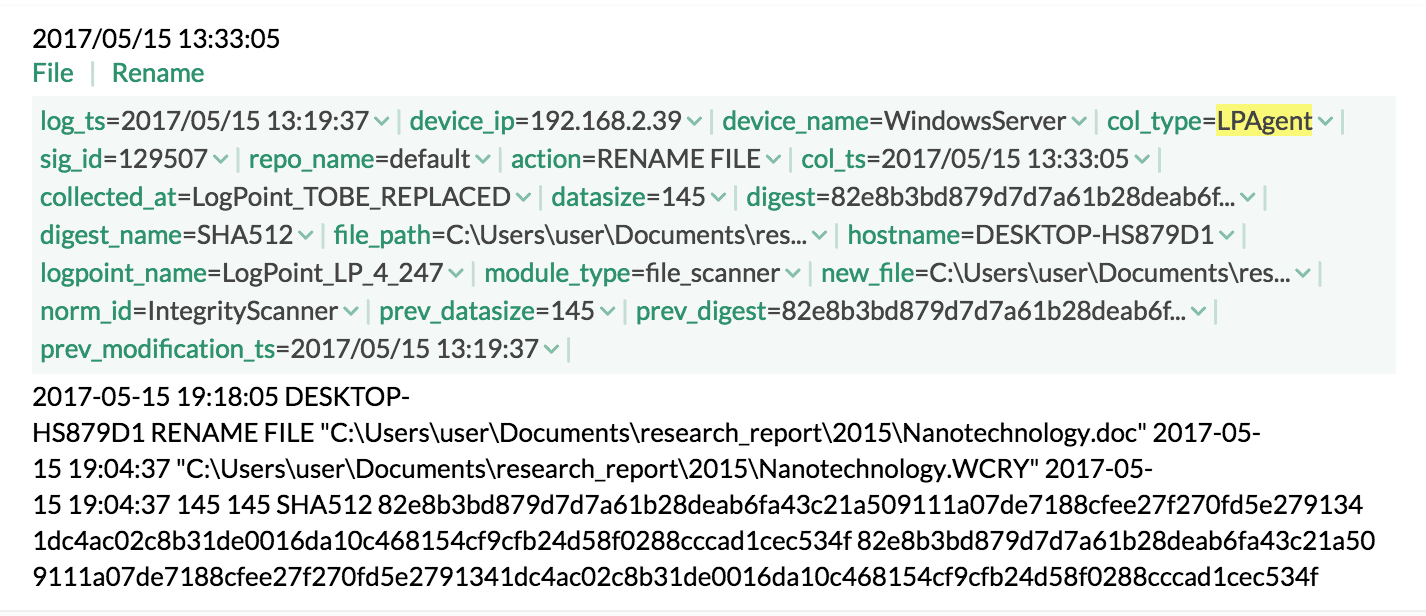
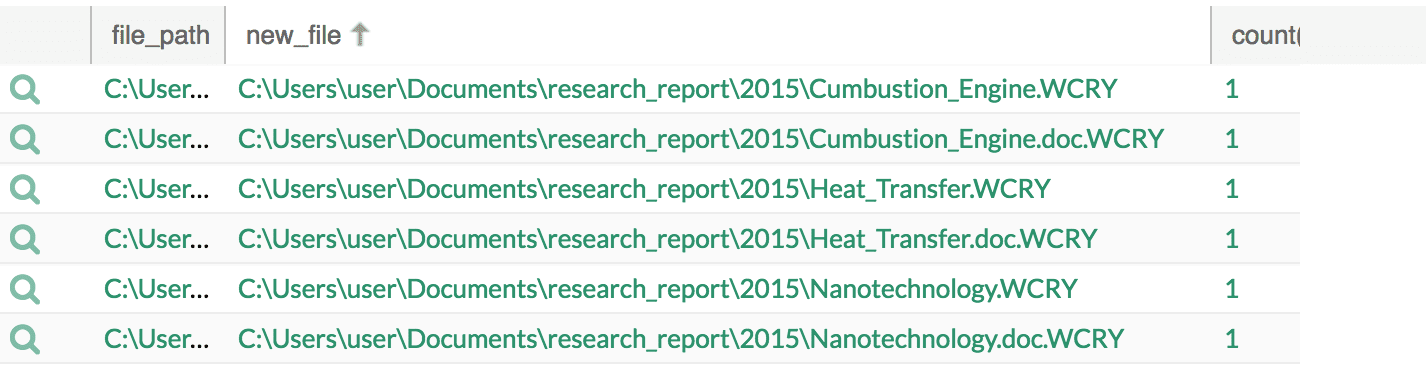
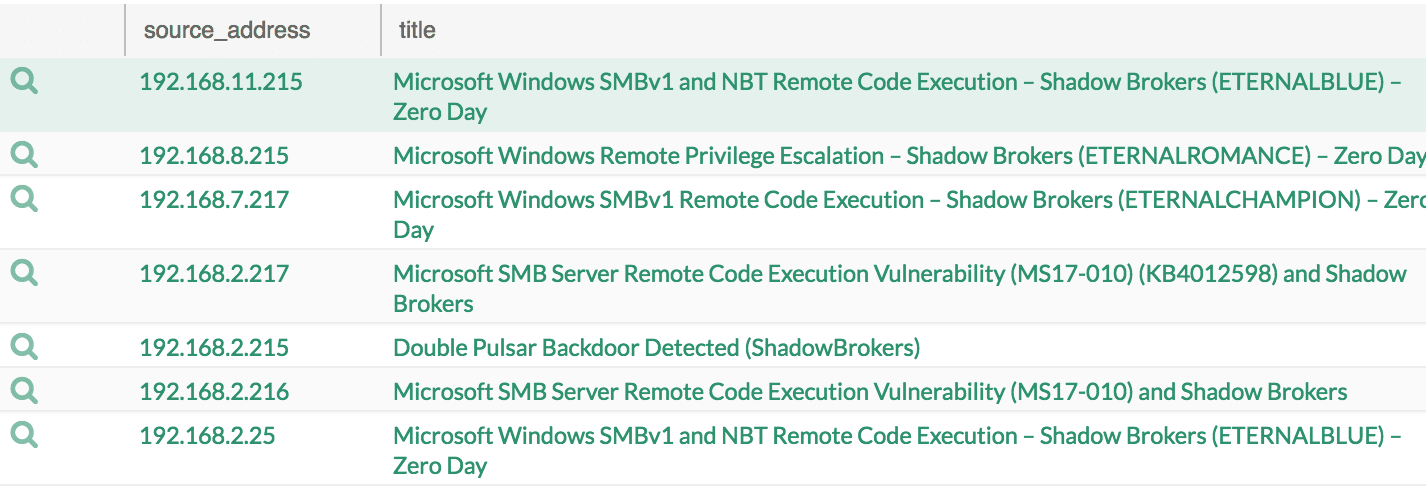
3. Check for the vulnerability
col_type=qualys* qualys_id IN [91345, 91357, 91359, 91360, 70077, 91360, 91345] | chart count() by source_address, title order by count() desc
If the vulnerability MS17-010 – Critical for SMB exists in the Windows systems, apply the following patch (here)
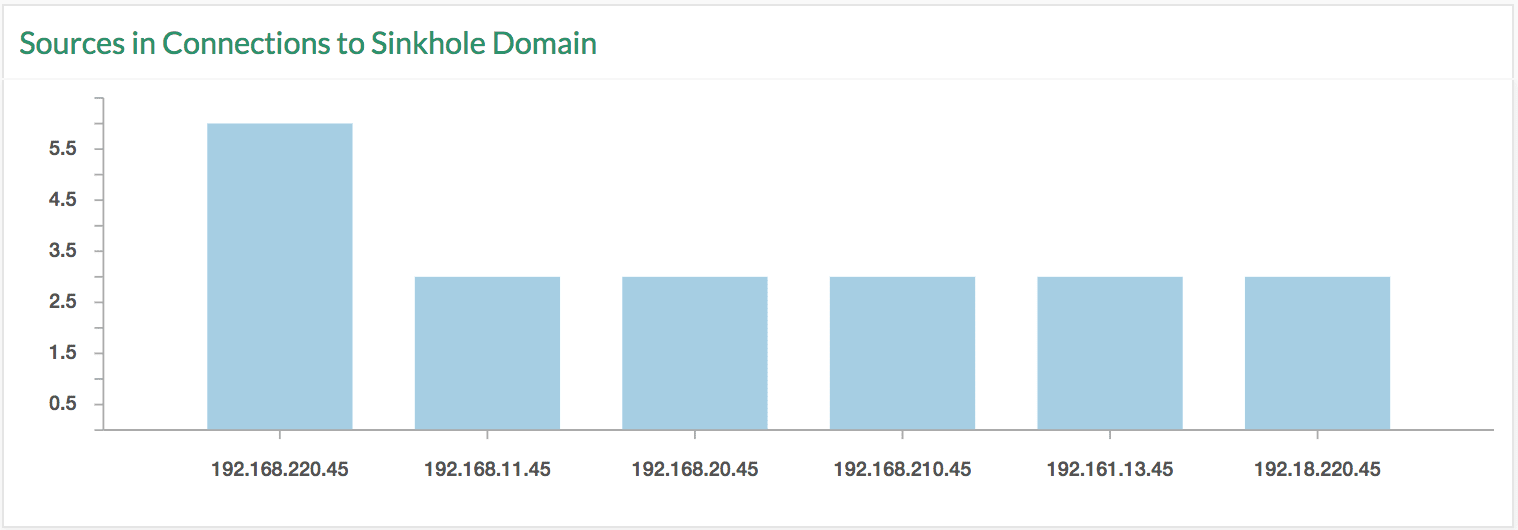
4. Check for sinkhole connections
norm_id=* url IN WANNACRY_DOMAIN or domain IN WANNACRY_DOMAIN | chart count() by source_address order by count() desc
You can see a connection to a kill switch, which seems to speed down the infection rate. You can update the WANNACRY_DOMAIN list if a new sinkhole is observed. Nevertheless, this does not mean that the attack has stopped, but the latest update on the ransomware seems to have left out the kill switch. If any connection variants from the infected hosts are identified, the list can be updated to check for such activity.
Supported Log Sources
- SMB Connections: Firewall sources
- Encrypted Files: File Integrity scanners, LogPoint Agent in this case.
- Vulnerable Sources: Penetration testing tools for a security vulnerability, Qualys in this case.
- Sinkhole Domain: Internet and Email activities identifying the visited URLs or domains, PaloAlto, Sophos UTM, IronPort, Juniper Secure Access etc.






