by Bhabesh Raj Rai, Security Research Department
On January 25, 2022, Qualys disclosed the details of a memory corruption vulnerability (CVE-2021-4034), titled PwnKit, in polkit’s pkexec utility installed by default on every major Linux distribution. PwnKit is a local privilege escalation (LPE) vulnerability that allows unprivileged users to gain root privileges on an affected system even in its default configuration.
pkexec is a SUID binary allowing the user to execute commands as another user. When a username is not specified, the program is executed as the root user in a small and safe environment. This avoids injecting the code through LD_LIBRARY_PATH or similar mechanisms.
Administrators can use pkexec as an alternative to sudo but with more fine-grained controls by defining a policy for each program. You can notice similarities in a case that affected sudo. Back in early 2021, a memory corruption LPE vulnerability (CVE-2021-3156) was found to have plagued sudo for nearly a decade.
Though Qualys did not publicly release the exploit, they provided enough technical details in their disclosure to rapidly create their exploits. Several PoCs such as [1] and [2] are already floating on the internet for anyone to use.
Log Source Requirements
- Linux
- Auditd
- Sysmon for Linux
Detecting the exploitation using LogPoint
If you do not have auditd configured to forward Linux logs to LogPoint, you can detect exploitation by searching for PwnKit artifacts in /var/log/auth.log. The LINUX_SERVERS list contains the IP addresses of all Linux systems forwarding logs to LogPoint.
device_ip IN LINUX_SERVERS
| search ("The value for the SHELL variable was not found the /etc/shells file" OR "contains suspicious content")However, administrators must remember that PwnKit can be exploited without leaving any trace in /var/log/auth.log.
To clear the blindspot, administrators can use auditd provided it has been configured to audit pkexec invocations. First, you need to look for auditd events that have “(null)” value set as their proctitle.
device_ip IN LINUX_SERVERS | search 'proctitle="(null)"'Next, you need to check for invocations of pkexec. Defenders require these indicators to further inspect the system and determine whether it was compromised using PwnKit.
norm_id=Unix "process"=audit command="pkexec"
| chart count() by log_ts, host, key, path, commandBack in October of 2021, Azure CTO Mark Russinovich announced the release of Sysmon for Linux. Administrators can use guides such as [1] and [2] to test and deploy Sysmon for Linux in their enterprise. LogPoint released Unix v5.2.0 that supports Sysmon for Linux. Administrators must note that Sysmon for Linux shares the same taxonomy as its Windows counterpart.
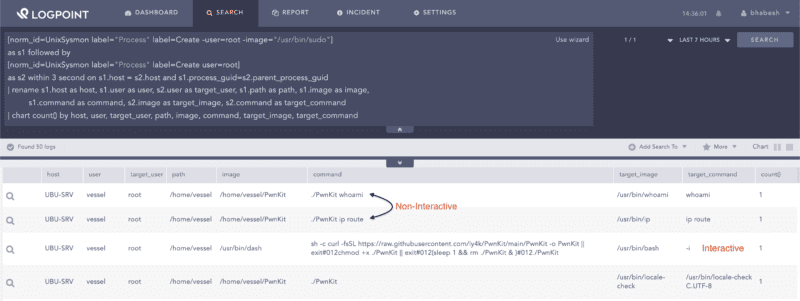
The generic LPE detection method works for detecting PwnKit. Administrators need to hunt for spawning of the privileged process by a non-privileged one with the apparent exception of sudo. PoCs, after exploitation, are either allowed to run commands directly as a command-line argument or in an interactive shell session. The screenshot below presents both of these scenarios.
[norm_id=UnixSysmon label="Process" label=Create -user=root -image="/usr/bin/sudo"]
as s1 followed by
[norm_id=UnixSysmon label="Process" label=Create user=root]
as s2 within 3 second on s1.host = s2.host and s1.process_guid=s2.parent_process_guid
| rename s1.host as host, s1.user as user, s2.user as target_user, s1.path as path, s1.image as image,
s1.command as command, s2.image as target_image, s2.command as target_command
| chart count() by host, user, target_user, path, image, command, target_image, target_commandSearching for generic local privilege escalation
Some PoCs can run as a one-liner via a simple curl command. You can monitor suspicious downloads from GitHub using process creation events.
norm_id=UnixSysmon label="Process" label=Create
image IN ["/usr/bin/curl", "/usr/bin/wget"] command="*raw.githubusercontent.com*"Post-compromise investigation
The necessary steps in investigating post-compromise activity include inspecting:
-
The creation of new users for persistence.
-
Suspicious execution of curl, wget, etc., to download payloads.
-
Installation of cron jobs for persistence.
-
Installation of an SSH backdoor for persistence.
-
Installation of coin miners.
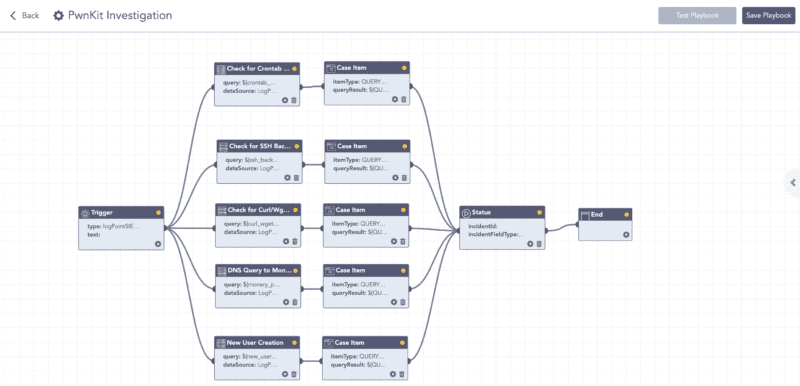
LogPoint SOAR Playbook for PwnKit Investigation
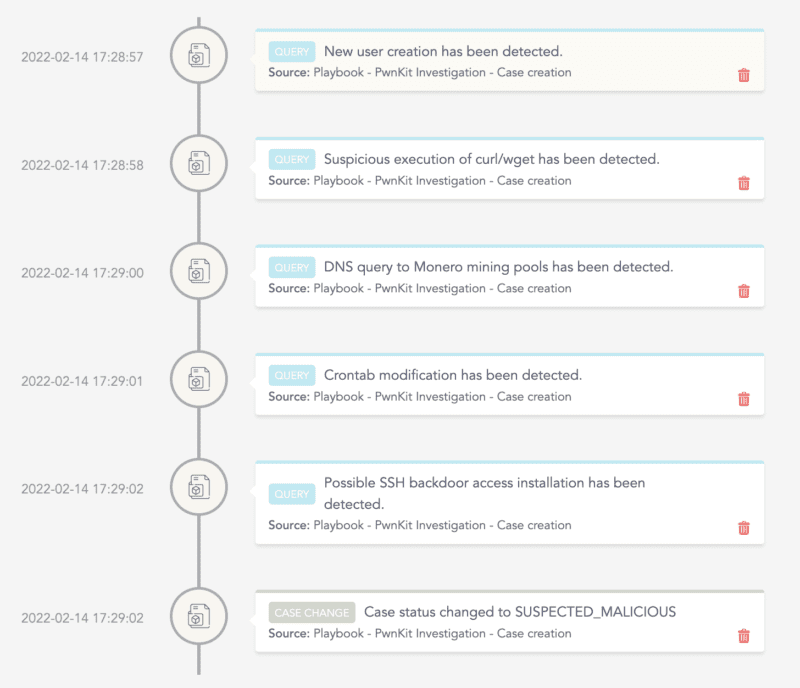
After executing the playbook in LogPoint SOAR, we can view the cases created by the playbook’s components in the investigation timeline to get a high-level overview of the investigation’s results.
LogPoint SOAR investigation timeline gathers the results of the investigation
Remediation
Finally, we stress to remind administrators to patch their Linux systems due to the flaw’s severity and the public release of several vulnerabilities POCs. Administrators can remove the SUID-bit from pkexec as temporary mitigation if patches have not been released for their Linux distribution. Enterprise defenders can expect threat actors to use PwnKit after gaining a foothold on a system.